Microsoft will integrate DNS over HTTPS in Windows 10
Microsoft revealed plans to integrate native support for DNS over HTTPS in the company's Windows 10 operating system in November 2019.
The announcement was made on Microsoft's Networking blog on November 17, 2019. DNS over HTTPS is designed to improve privacy, security and the reliability by encrypting DNS queries that are handled in plaintext currently.
DNS over HTTPS has been on the rise lately. Mozilla, Google, Opera as as well as several public DNS providers announced support for the standard. Support in programs, e.g. a web browser, means that the DNS queries that originate from that program are encrypted. Other queries, e.g. from another browser that does not support DNS over HTTPS or is configured not to use it, won't benefit from that integration however.
Microsoft's announcement brings DNS over HTTPS support to the Windows operating system. The company plans to introduce it to preview builds of Windows 10 in the future before it releases it in a final version of the operating system.

Microsoft plans to follow Google's implementation, at least initially. Google revealed some time ago that it will roll out DNS over HTTPS in Chrome, but only on systems that use a DNS service that supports DNS over HTTPS. In other words: Google won't alter the DNS provider of the system. Mozilla and Opera decided to pick a provider, at least initially, and that means that the local DNS provider may be overridden in the browser.
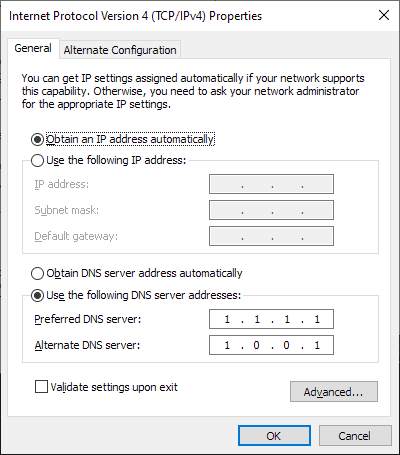
Microsoft notes that it won't be making changes to the DNS server configuration of the Windows machine. Administrators (and users) are in control when it comes to the selection of the DNS provider on Windows and the introduction of support for DNS over HTTPS on Windows won't change that.
The change may benefit users without them knowing about it. If a system is configured to use a DNS provider that supports DNS over HTTPS, that system will automatically use the new standard so that DNS data is encrypted.
The company plans to introduce "more privacy-friendly ways" for its customers to discover DNS settings in Windows and raise awareness for DNS over HTTPS in the operating system.
Microsoft revealed four guiding principles for the implementation:
- Windows DNS needs to be as private and functional as possible by default without the need for user or admin configuration because Windows DNS traffic represents a snapshot of the user’s browsing history.
- Privacy-minded Windows users and administrators need to be guided to DNS settings even if they don't know what DNS is yet.
- Windows users and administrators need to be able to improve their DNS configuration with as few simple actions as possible.
- Windows users and administrators need to explicitly allow fallback from encrypted DNS once configured.
Closing words
Microsoft did not reveal a schedule for the integration but it is clear that it will land in a future Insider build for Windows 10 first. Integration in Windows -- and other client operating systems -- makes more sense than integrating the functionality into individual programs. Users who want to use DNS over HTTPS may simply pick a DNS provider that supports it to enable the feature for all applications that run on the system.
Now You: What is your take on Microsoft's announcement? (via Winaero)


















I am using the one here https://www.digitale-gesellschaft.ch/dns/ which is a privacy and civil rights organisation in Switzerland.
The description is here https://www.digitale-gesellschaft.ch/dns/ and there is also a transparency report according to mozilla standards. They do not keep any logs.
I configured my android mobile operating system and my firefox browsers for it. Now i just wait for <m<s to do its thing.
First, I wouldn’t trust MS with a 1 character text file. But there are allot of tools out there to control dns traffic. My favorite is dnscrypt-proxy because it provides 100% user controlled privacy. It’s open source and has binaries for Linux, Windows, Android, BSD, et al. It features wildcard-blocklist, wildcard-whitelist, a hosts file ms can’t bypass, complete dns logging, etc. Note on windows, all dns request go through MS DNS Client first (aka the Dnscache service) before being routed through to the actual dns request servie. Thus, use the MS hosts file first for the fastest of blocking, then use dnscrypt-proxy for those domains in MS’ builtin whitelist or for those domains you want to block and/or monitor. Here are a few examples of a wildcard-block list…
*banner.*
*telemetry.*
*tracker*
*fbcdn*
*.amazon-adsystem.*
*google*
etc…
https://github.com/jedisct1/dnscrypt-proxy/releases
Now to remove all the spying and telemetry from windows and office…
Microsoft care about privacy of users? What hypocrits.
What does it mean for average user? I could think of a few things, but that’s just me thinking too much. There’s some controversy surrounding cloud flare, but time will tell.
Getting a VPN would be a good idea, since I like to research hot topics, it might get me in hot water.
@Barry “some controversy surrounding cloud flare”
There has been no wrongdoing by Cloudflare or been found guilty of anything.
No one cares using Googles dns yet everyone makes out Cloudflare to be the worse company ever.
@Barry, do use Tails and Tor Browser and your pretty safe.
The tech companies are all run by the CIA. As Trump closes in on their trafficking and laundering crimes, they are going to increase surveillance, censorship, and user harassment. DNS over HTTPS is a non-starter and it will be used to track political dissidents. Reject it outright. Do not comply.
I don’t know if any of you follow Q but it was mentioned that XBox game servers were being used by high-level criminals to communicate outside of the NSA. When it was exposed, Satya Nadella took the servers offline to wipe the evidence.
Do not trust Silicon Valley.
Q from Star Trek?
@Stan:
I think he was referring to this: https://en.wikipedia.org/wiki/QAnon
I have to agree with Fenderson on this one.
Governments employ intelligence (spying) agencies.
Tech companies are NOT run by the CIA (it’s a very disingenuous argument).
Corporations are run for profit (money).
Corporations spy on users to SELL their information for profit (money), except Microsoft who gives the NSA free access for who knows what reason(s).
Silicon Valley does have a leftist agenda, but that’s a political bias, not evidence of collaboration with Five Eyes (except Microsoft, of course, who has been proven to provide access to the NSA).
@Johnson Kane: “I don’t know if any of you follow Q”
I don’t, because I’m not that nutty.
for professional you can disable it or mount a DOH server with pihole and filter dns with it (and filter Other doh and dns with the firewall)
@Bevode:
Yes, but that won’t stop applications from using DoH on their own.
Its good to see a genuine improvement for the OS forecast.
Is CloudFlare worth trusting? What DNS servers do you recommend?
Cloudflare has never been found guilty of wrongdoing. No one (except Goolag shills) has even accused them of anything.
Goolag sells user information.
Microsoft helps the NSA spy on everyone.
Of all the potential DNS providers, Mozilla chose Cloudflare.
DNS-Over-HTTP is needed for security/privacy.
@notanon:
“Microsoft helps the NSA spy on everyone.”
You mean like that mozilla emloyee did, in efforts to backdoor crypto standards? Wasnt it the same who worked with your goolag pals to push through the shady WebRTC standard? Hope there arent experts like that tasked with maintaining certs or anything… oops.
DNS over TLS is a way better solution than DNS over HTTP will ever be.
Because there is still so much more data available to the ISP/government about where you visit, the whole DNS over HTTP crap is just a toy to keep the illiterate happy.
It really will take your ISP/government no time at all to logically determine what information you are looking up, when you do it and in what order too. DNS over HTTP doesn’t safeguard you against that in any way or form.
@metro87:
I have no serious security concerns with Cloudflare at this time, personally. However, whenever a single company is in a position where they have access to so much information, it’s always something that people should be cautious and vigilant about.
That a company is OK today doesn’t mean they’ll be OK tomorrow. Remember when Google was a good guy? I do.
Cloudflare is fine, some here are totaly paranoid …
Bevode, Why don’t you use the DNS of your Internet service provider? Paranoid?
Ah no, i have selected cloudflare for it’s speed twice more fast than my isp and my isp don’t use dnssec.
But some people here, tell other cloudflare take personal data of the dns data, or cloudflare don’t do it, it’s clearly paranoid people.
Cloudflare is indeed collecting data and sharing with APNIC (registrant of the IP addresses used by Cloudflare DNS). Just read their privacy policy. And if you care about DNSSEC and privacy, run your own DNS resolver.
Cloudfare blocks archive sites. If you’re politically active at all and use cloudfare DNS, you’ll notice you won’t be able to connect to archive sites anymore.
Cloudfare does not block Archive site. Archive.is does not want to publish their IP addresses to Cloudflare DNS resolvers. They treat Cloudflare different than other resolvers. Archive.is wants Cloudflare to pass ECS data (IP address subnet) from queuing client and Cloudflare refuses due to privacy concern.
This will be a problem if Windows no longer uses the hosts file when it uses DNS over HTTPS.
So I hope they stick to their words and let admins disable it.
Mozilla uses the wire protocol in their doH implementation, and local host is indeed bypassed. However, the chromium implemtation of doH uses json. From what I can tell, the local hosts file is not bypassed with chromium/edgeium/vivaldi implementation. You should test it yourself, however.
I doubt that the Microsoft system wide implementation of doH would bypass the local hosts file.
When using cloudflare use 1.1.1.1/help or http://www.cloudflare.com/ssl/encrypted-sni/ to see where your browser stands.
How will I know if Microsoft is spying on me, wont this prevent wireshark from collecting data?
Microsoft has a history of helping the NSA spy on users, so you can be assured that Microsoft will give your information to the NSA.
Why do you think Microsoft won the $10 billion JEDI defence contract over Amazon AWS (who was providing the services already)? Microsoft has proven it’s loyalty to the government with it’s voluntary assistance to the NSA.
“wont this prevent wireshark from collecting data?”
Yes, it will.
This is my most serious objection to DoH — it makes it impossible to monitor and manage this aspect of your network communications. DoH is a hole that weakens your privacy in a particular way: it prevents you from being able to monitor and selectively block DNS requests (think pi-hole, for instance).
The only way to mitigate this is to install a man-in-the-middle proxy that can decrypt your HTTPS traffic to allow examination and modification before reencrypting it for transmission to/from the internet. This is what I’ve done in my own LAN. However, doing this is well beyond the ability of most people.
“Google won’t alter the DNS provider of the system.”
“Microsoft notes that it won’t be making changes to the DNS server configuration of the Windows machine.”
“If a system is configured to use a DNS provider that supports DNS over HTTPS, that system will automatically use the new standard so that DNS data is encrypted.”
“Mozilla and Opera decided to pick a provider”
What Google and Microsoft do now is the user respecting way to do it. Mozilla proved that they can be an even worse data whore than Google with their Cloudflare deal, because they thought they could get away with it more easily than the big G. Until maybe in the future their anti-privacy pioneering work on the DNS hijacking sector for surveillance capitalists and the US government dragnet will make other big and small companies confident enough to do it too, including Google and Microsoft.
Goolag sells user information.
Microsoft VOLUNTARY helps the NSA spy on it’s users (as opposed to requiring a court order for every request).
Cloudflare does NONE of that, yet you want to paint Goolag and Microsoft as the “good guys” and Mozilla as the “bad guy”?
SMH.
Cognitive dissonance.
@notanon
Cognitive dissonance indeed lad. Mozilla, for their noise about google have been taking the time to make a firefox lite, embedded with trackers and based on chrome. There was a story on here some days ago about it.
You sure want everyone to accept Cloudflare into firefox dont you. Blab about microsoft+NSA when Mozilla ejects their NSA goons. Too bad for their efforts that we keep things like WebRTC, Serviceworkers, Pocket, DoH etc in the public eye isnt it.
“What is your take on Microsoft’s announcement?”
I like Microsoft’s approach (use the system settings) much better than Mozilla’s approach.
That said, I really hate that DoH is a thing that exists. It does cover one privacy hole (which could be covered in other ways), but in exchange it opens a different one. For me, this is a net loss and mitigating that requires me to set up my network in a less-than-ideal way, security-wise.
That’s a battle that was lost as soon as Mozilla filed their RFC, though. I doubt I’ll ever be able to forgive Mozilla for this.
Federson, do you know that Microsoft has collaborated with the NSA to spy on it’s users?
Microsoft gave the NSA access to Outlook e-mails BEFORE the encryption process, which they voluntarily handed over to the government without any notification to their users/customers.
They also helped the NSA spy and collect Skype video calls (in the United States, you can’t wiretap a phone call without a warrant, but apparently Microsoft gave carte blanc to the NSA to spy on all it’s users).
This has been known for years, if you’re too lazy to do an internet search, here’s a story done by the Guardian (years ago).
Microsoft handed the NSA access to encrypted messages
https://www.theguardian.com/world/2013/jul/11/microsoft-nsa-collaboration-user-data
Microsoft is a known and verified collaborator with the NSA.
I don’t want what happened to this New York family to happen to me –
New York woman visited by police after researching pressure cookers online
https://www.theguardian.com/world/2013/aug/01/new-york-police-terrorism-pressure-cooker
@notanon:
Yes, I’m aware of all of that. I’m not entirely sure what your point is, though.
This shold be the only way if a user needs such a feature. Browsers should under no circumstance attempt to bypass/override the operating system’s behaviour. What Mozilla is doing is pure evil, selling all their userbase browsing history to CloudFlare.
Firefox only uses DNS over HTTPS if you explicitly enable it. It’s not “selling all their userbase browsing history to CloudFlare”.
The only users who enable the feature are clearly able to see that Cloudflare is the provider.
Fucking hell the amount of shills around here is outstanding!!
They all bad Morons!
Like it or not the lesser evil so far is Mozilla, you can still tune the settings.
Google don’t and i bet you won’t allow you to change those settings.
MS can any any point overwrite/bypass those settings as they do now when you block their spying ips on the Host file.
Stopped the moronic shilling and if you are getting pay to so, please let me in i need the money.
Yuliya has been an anti-Firefox *** [Editor: please be polite] without much proof for a long time already. No surprise honestly.
Using Cloudflare as provider = selling info to Cloudflare…that’s Yuliya’s literal thought process without actual proof.
Yuliya = lying.
Cloudflare does not sell information (where’s your proof???).
Firefox was never going to choose Goolag as a DNS provider for it’s DNS-over-HTTPS, because Goolag DOES SELL USER INFORMATION.
And the the “anonymous” post clearly doesn’t even understand why DNS-over-HTTPS is needed for privacy. Everyone can read Martin’s DNS-over-HTTPS articles to learn why DNS-over-HTTPS is needed for privacy/security.
Posting blatant lies, like Anonymous posting that the EFF called Cloudflare evil is what shilling is all about.
Just wondering what you think you’re adding to the discussion by using juvenile name-calling (“Goolag”).
There are a boatload of DoH providers out there and one can choose from any of them to have them sell all his/her browsing history to one of them instead of the one they were already using.
“There are a boatload of DoH providers out there”
A systematic dishonest Mozilla argument.
Defaults matter. A lot.
“one can choose from any of them to have them sell all his/her browsing history to one of them instead of the one they were already using.”
Not clear what is intended here but I suspect that this is the other systematic dishonest Mozilla argument: all ISP sell your data now, so there’s nothing wrong with giving the data to Cloudflare instead of your ISP.
First, it is not really “instead of your ISP”, it is actually “in addition to your ISP”.
Second, in many places the ISP are more trustworthy than Cloudflare, they cannot legally sell this data, and beyond that can be trusted more than a Silicon Valley giant that is owned by Google and co and cannot credibly be considered not to partner with the NSA.
Third, even in USA in places where ISP are legally allowed to sell this DNS data, I think that they aren’t even doing it yet, as I heard from an exchange between a PowerDNS and a Cloudflare employee. They may in the future, but so may Cloudflare, surveillance capitalism privacy policies are known to be changed at will and USA has no legal protection against that. And don’t trust Mozilla’s promises to object to that when it happens, they are also extending the reach of their data collection all the time without consent.
Fourth, the EFF agrees that this DNS centralization at Cloudflare is evil.
Granted, I should have stated “instead of the one they might already be using.”
“First, it is not really ‘instead of your ISP’, it is actually ‘in addition to your ISP’ ”
No. One will be able configure the DNS IP addresses to any ones that aren’t DoH.
Second, third: when I stated “one can choose,” it has everything to do with CHOICE. Prior to DoH and DoT, we had none.
Fourth: the EFF is entitled to its opinion. And again, choice.