Thunderspy: find out whether your device is vulnerable to (local) Thunderbolt security issues
Security researcher Björn Ruytenberg published a security analysis of the Thunderbolt protocol on April 17, 2020 entitled "Breaking Thunderbolt Protocol Security: Vulnerability Report". He discovered several security vulnerabilities in the Thunderbolt protocol that may be exploited by local attackers to access all data even on systems with encrypted drives and if the computer is locked or in sleep mode.
A total of seven vulnerabilities are revealed in the analysis; these affect "all laptop and desktop systems equipped with a Thunderbolt 2 and/or Thunderbolt 3 family host controller employing Security Levels". All Microsoft operating systems from Windows 7 to Windows 10 and all Linux kernel releases from kernel 4.13 are affected. Apple Macintosh systems are affected partially only because of additional security measures that are in place by default.
Update: Intel responded to Thunderspy stating that newer versions of Windows 10, Mac OS X and Linux supported a feature called Kernel Direct Memory Access (DMA) protection which mitigated against attacks outlined in the research paper. Microsoft published an article about this here on its Docs website. On systems running at least Windows 10 version 1803, administrators may go to Start > Settings > Update & Security > Windows Security > Open Windows Security > Device security > Core isolation details > Memory access protection to verify that memory access protection is enabled; this requires a UEFI firmware support and is not compatible with other BitLocker DMA attacks countermeasures. End
All attacks require brief local access to the system but the system itself may be locked or in sleep state. The paper describes several exploitation scenarios which all require local access to the device.
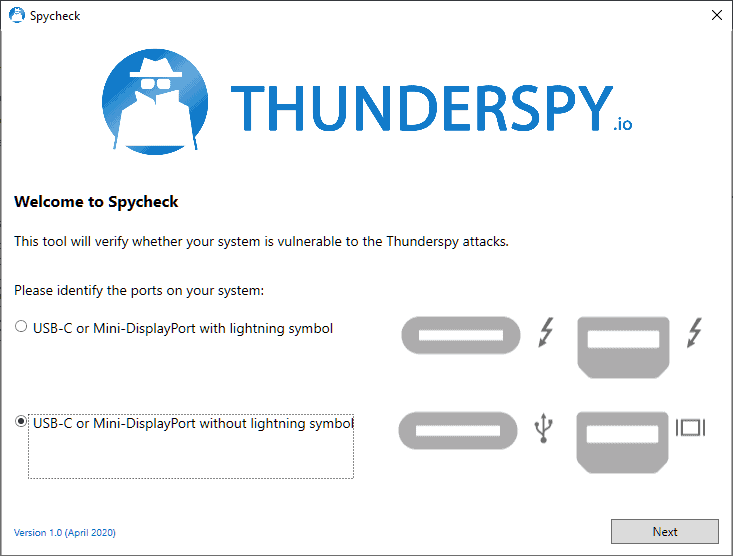
A program has been created by the researcher that checks devices with Thunderbolt ports. The application is available for Windows and Linux; the Windows version may be downloaded from the Thunderspy website. It is compatible with Windows 7 and newer versions of Windows, and with Linux kernel 3.16 and Pyton 3.4 and later on Linux devices.
Spycheck prompts you to identify the ports on the device which can either be USB-C or Mini-DisplayPort with lightning symbol or without lightning symbol. Hit the next button once you have identified the correct port to have it check that port. Devices without Thunderbolt ports will show up as "not vulnerable" automatically. Suggestions are displayed on how to address the issue if a device is found to be vulnerable by the application.
The researcher created demonstration videos; the first demonstrates how to unlock Windows PCs in 5 minutes by exploiting vulnerabilities.
The second video shows how to disable all Thunderbolt security on a Windows PC permanently.
Now You: do you use devices with Thunderbolt ports? Are your devices vulnerable? (via Deskmodder)






















Due to Windows 7 End of Support, Laplink has developed a new “Windows 7 Migration Kitâ€. It eases the transition to Windows 10 and reduces the effort of manual PC migrations. The kit includes PCmover, the only migration software of its kind recommended by Microsoft®, Intel® and all major PC manufacturers. Learn more and get special pricing at windows7migrationkit.com/comment-learn-more.html.
Sorry, I believe there’s a typo in the quote in paragraph two. The research paper says “All laptop and desktop systems equipped with a Thunderbolt 2 and/or Thunderbolt 3 family host controller employing Security Levels.” Thus, “Thunderbird” would seem innocent, this time at least. :-)
Quoting the the Thunderspy website,
“If your computer has such a port [Thunderbolt], an attacker who gets brief physical access to it can read and copy all your data, even if your drive is encrypted and your computer is locked or set to sleep.”
“All the attacker needs is 5 minutes alone with the computer, a screwdriver, and some easily portable hardware.”
No one gets physical access to my PC in my absence anyway. Most valuable article but requiring technical literacy I lack.
1) check via msinfo32 if your device support Kernel DMA Protection
2) enable “Disable new DMA devices when this computer is locked” group policy setting (applicable only when the system partition is encrypted using Bitlocker)
I don’t know if there is such protection exists in Linux.
P.S. if your device supports Kernel DMA Protection, it’s better to use it, not a policy setting.
https://docs.microsoft.com/windows/security/information-protection/kernel-dma-protection-for-thunderbolt
I use a MacBook Air that only has 2 Thunderbolt ports. Is my laptop vulnerable? No idea. How big is the risk? No idea, though I suspect small.
https://i.imgur.com/eEA8eM9.png
I tried attatching a HDMI monitor and/or an external SSD. Nothing, and I’m not installing their driver. This program doesn’t function properly.