Protect Windows against Speculative Store Bypass exploits
It has become quite time consuming to stay up to date with the ever increasing threats that Spectre and Meltdown pose to computer systems around the world.
New variants pop up regularly, and manufacturers like Intel and AMD, and software developers like Microsoft, release advisories, updates, and instructions regularly for some but not all hardware or software that are affected potentially.
While you have probably done a bit of patching already to protect against some variants, you are not done yet.
Microsoft updated an advisory on today's Patch Day that includes instructions on enabling protection against Speculative Store Bypass (SSB) in Intel and AMD processors.

The update requires that microcode or firmware updates are installed on target machines running Intel processors. AMD systems don't require microcode updates according to Microsoft.
What you need to do to install the updates is the following therefor:
- Install the June 2018 security updates for your operating system (client and server supported, see chart below).
- Install the firmware or microcode update for Intel machines when released by Intel.
- Modify the Registry to enable the protection.
Question is: should you enable the protection? Microsoft did not enable it by default but revealed that it will enable the protection automatically if it notices exploits that are in the wild.
Installing the update won't affect performance according to Microsoft but enabling the protection in the the Registry will have an impact on the device's performance; this is the most likely reason why Microsoft did not enable the protection by default.
The following table shows the vulnerabilities and their default state on all supported versions of Windows.
| Operating System | CVE-2017-5715 | CV-2017-5754 | CVE-2018-3639 |
|---|---|---|---|
| Windows 10 | Enabled by default | Enabled by default | Disabled by default - see ADV180012 |
| Windows Server 2016 | Disabled by default - see KB4072698 | Disabled by default - see KB4072698 | Disabled by default - see ADV180012 |
| Windows 8.1 | Enabled by default | Enabled by default | Not applicable |
| Windows Server 2012 R2 | Disabled by default - see KB4072698 | Disabled by default - see KB4072698 | Disabled by default - see ADV180012 |
| Windows RT 8.1 | Enabled by default | Enabled by default | Not applicable |
| Windows 7 | Enabled by default | Enabled by default | Disabled by default - see ADV180012 |
| Windows Server 2008 R2 | Disabled by default - see KB4072698 | Disabled by default - see KB4072698 | Disabled by default - see ADV180012 |
| Windows Server 2008 | Enabled by default | Enabled by default | Not applicable |
To enable the Speculative Store Bypass protection in Windows, do the following:
Note: We recommend that you backup the Registry or create a system backup before you run these commands.
- Open an elevated command prompt by clicking on Start, typing cmd.exe, holding down the Shift-key and the Ctrl-key, before selecting the Command Prompt result.
- Do the following on AMD systems:
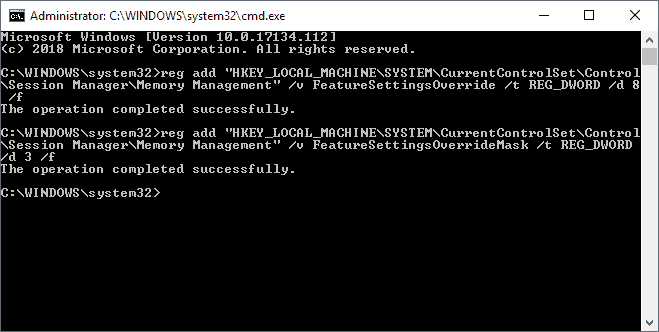
- Run reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 64 /f
- Run reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
- To protect against Speculative Store Bypass run the following commands:
- reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 8 /f
- reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
- Restart the PC.
To undo the protection outlined under 3) above run the following from an elevated command prompt:
- reg delete "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /f
- reg delete "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /f
See KB4073119 for additional information or updates.
Related articles
- New InSpectre release reveals if microcode updates are available
- Ashampoo Spectre Meltdown CPU Checker
- Check Linux for Spectre or Meltdown vulnerability
- Find out if your Windows PC is affected by Meltdown/Spectre vulnerabilities

















There are some mistakes in this article:
1) “…enabling protection against Speculative Store Bypass Disable (SSBD)” – SSBD is not the name of the vulnerability. It’s the name of the protection (it disables SSB).
2) The table is incorrect – At least Windows Server 2012 R2 is not affected by this vulnerability.
3) Step 2 to enable SSBD is incorrect – This setting activates Indirect Branch Prediction Barrier (IBPB) which is an alternative protection against Spectre 2 for AMD. In fact it’s OK, because you will rewrite the value in step 3 :-)
4) Steps to disable the SSBD protection are “a way to hell” – There is no reason to delete registry key FeatureSettingsOverrideMask as it just defines the bit mask. You should not delete the FeatureSettingsOverride either, because you will disable the protection against ALL vulnerabilities. You should change the (bit-based) value according to the desired state (0 = protection against Variant 2 and Variant 3 activated, protection againt Variant 4 deactivated). You can use InSpectre to (de)activate the protections individually.
Thank you for your input. The table comes from Microsoft, has the company updated it?
Their article was created on June 12, but it’s possible that they updated it later. Source: https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/7d4489d6-573f-e811-a96f-000d3a33c573
” Why bother ? The Spectre/Meltdown has been around since many, many, years back. Still i haven’t heard anything that these exploits are (ab)used.”…………….totally agree !
We are always toooo late , when new malware arrives , while security-updates never speed-up your OS !
Only real working solution is making backups regulary ………….!!!
I disabled spectre and meltdown , it made my system slower , while the checker “said” performance ; good !
Still lost few seconds with booting into Windows , wit spectre/meltdown enabled…………
Why bother ? The Spectre/Meltdown has been around since many, many, years back. Still i haven’t heard anything that these exploits are (ab)used. To me this is quite ridicilous news…. If patches affect computers negative i don’t bother install them.
I am still on XP x64 and 7 x64 plus some Linux dists.
Martin,
Would it be a generation of Intel or AMD microprocessors that don’t “include” these Meltdown and Spectre weaknesses?
You mean if new processors that got released after Spectre/Meltdown reveal exist? I’m not 100% sure on this but you probably have to wait a bit longer before you can buy Intel processors that are not vulnerable.
I run Windows 8.1. I uninstalled a previous Windows update which provided Meltdowh protection as it slowed my computer too much (my computer is 5 years old). As there is not a single Meltdown or Spectre exploit in the wild, AFAIK, I prefer to take my chances. I have backups.
I won’t be making further modifications to my system for this malware.
I still think Intel and amd should have owned this bullshit and given everyone a new mb and processor, sure it would cost billions, boohoo. These companies need to learn real pain instead of doing whatever the hell they want
Are there any performance impacts?
Yes if this is enabled performance will drop but Microsoft did not reveal by how much.
The registry for Speculative Store Bypass are only for IT and servers? home computers no?
Microsoft’s description and instructions are really bad. I understood it that it is for all client and server versions, not only for server.
Hmm….not sure if the image is photoshopped but if the claim in by the user is true…..https://rog.asus.com/forum/showthread.php?103044-New-Microcode-for-Skylake-X-02000049-found-in-lastest-Windows-10-Insider-Preview
Quoting the asus user ” Maybe Intel will sending next microcode update to Microsoft before motherboard manufactures. “
Dear Martin, please don’t spread fake news. The registry for Speculative Store Bypass ( ADV180012 CVE-2018-3639 ) in your post doesn’t do anything. Even if you enable it, the protection is not enabled at all.
One will need microcode update from Intel/AMD for the protection to be enabled.
Note: for ADV180013 Rogue System Register Read CVE-2018-3640, a microcode update is required as well.
Now, Intel hasn’t officially release microcode update with SSBD MSR yet.
So, even with the registry being enabled, there is NO PROTECTION against CVE-2018-3639 and CVE-2018-3640.
Yep. You are right. Have just tried this and nothing. Using the powershell commands to check if speculative store bypass vulnerability protection is enabled and it still says vulnerable so. Got a ryzen 5 1600x. Guess we gotta wait for new microcode/bios updates again xD.
To be honest, I’m concerned about protecting Windows against Microsoft’s incompetence.
Martin,
You have made it clear what is required for AMD but not Intel, can you please clarify?
Otherwise great article so many thanks
You need to run the commands under 3) on Intel systems.
Thanks!
As MSI hasn’t released a new bios for my MOBO (and probably nerver will) does any of this spectre/Meltdown mitigation even apply to my hardware?
I am running an i5-4670 on a MSI Z87-G43 Gaming and an i7-4790K on a MSI Z87-GD65 Gaming.
Is this W10?
This is all supported versions of Windows.
Thanks a lot Martin !