Firefox 60: HTTPS upgrade for Mixed Content
Mozilla plans to launch a new feature in Firefox 60 that upgrades optionally-blockable mixed content on HTTPS sites to HTTPS if possible.
The migration to an HTTPS powered World Wide Web is in full swing. One of the byproducts of the migration is that some sites may load HTTPS and HTTP content. This is called Mixed Content and it is undesirable as it reduces security and privacy if loaded.
Mixed Content is divided into blockable and optionally-blockable content. Modern web browsers block any content that may interfere with the display of data on HTTPS web pages if it is loaded using HTTP.
Think of a script that is loaded from an HTTP resource on an HTTPS site. Browsers don't block optionally-blockable content usually on the other hand. This is static content such as images or videos that can't interfere with the web page or data directly.
Firefox displays a different lock symbol on sites with mixed content that is optionally blockable. The browser displays a green lock symbol on HTTPS sites without mixed content.
While optionally-blockable mixed content is less dangerous than blockable mixed content, it is still problematic from a privacy point of view.
HTTPS upgrade for Mixed Content in Firefox
Mozilla Firefox 60 includes a feature that changes the browser's behavior when it comes to mixed content that is optionally blockable.
Firefox attempts to load mixed content that is optionally blockable from HTTPS domains instead of the referenced HTTP domains. If the resource cannot be loaded, it is not displayed at all. This can lead to image, video or audio content not being shown correctly in the browser because of the change.
The limitation is likely the main reason why Mozilla won't activate the feature by default in Firefox 60.
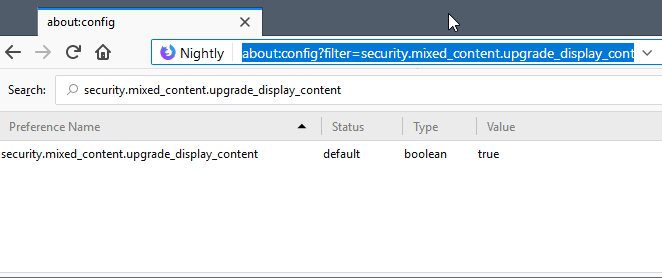
The feature won't be enabled by default in Firefox 60 but users can set it to enabled in the following way:
- Load about:config in the Firefox address bar.
- Search for security.mixed_content.upgrade_display_content.
- Set the preference to True.
You can revert the change at any time by setting the preference to false, or by right-clicking on it and selecting the reset option from the context menu.
Now You: Do you care about mixed content? (via Sören)
Related articles
- Firefox 23 to block insecure contents from being loaded on https pages
- Firefox 59: Referer Path Stripping in Private Browsing
- Firefox 60: new "not secure" indicator preferences
- Firefox 60 with new preference to disable FTP
- Mozilla makes Firefox 60 next ESR target






















Better to side with being safe and all https then mixed mode risking a lot. Browser doing right by users to force https and notify of issues or even block eventually. Let the web sites fix what’s wrong and side on security. Still cannot believe how many sites still not https even technology sites you would think would be ahead of the came and know the importance.
@John: “Better to side with being safe and all https then mixed mode risking a lot.”
Best of all is allowing users to make those sorts of decisions for themselves. Browsers shouldn’t be forcing anybody to do anything. Encouraging, sure. Making the default behavior “safe”, fine. Forcing, though, is completely unacceptable.
Hihi,
if i wouldn’t have an Interest in Anagrams, i’ like to say Tomahwack is false written.
It’s without theee C, but,…that’s only mee Opinion.
Greets, InGSoC.
I’m French, not Belgian!
Hello there,
as long as we cannot hide completely through a Stealthcap implemented in any Browser, we are visible, sooo…?
What’s the Deal? Secure? Nonsecure, what does that gonna prove, hmmm?
Thee Internet is NOT programmed to be invisible, so, i do not generally understand all that, this
and that Company plans to do this and that.
Replicants are like any other Machines, wheteher they are a Benefit or a Hazard.
If they are a Benefit, not my Problem, GG
Greets, InGSoC.
Privacy and security. Upgrading “optionally-blockable mixed content on HTTPS sites to HTTPS if possible” concerns security. I understand your opinion regarding privacy on the Web but security is maybe a less controversial topic.
I went through my bookmarks again and found some that use mixed content and they are: Feedly and MIT Technology Review. Oh, and the link posted by @Jessica led me to Google Assistant.
The new preference is working like it should on the three websites mentioned above and they all show that they are secure. If I didn’t open the browser console I would never be able to tell that the insecure content was upgraded and the page load times seem to be unaffected. I’m kind of impressed by how well it works on my end.
Looks to me like the default for the preference is true which is what I’m seeing in my Nightly install. Also, in the screenshot it looks like the text is not in bold.
Anyway, I wanted to test the preference and can’t find a website that uses mixed content. Instead of the new option being ahead of its time maybe it’s day late and two dollars short? LoL
@Richard, I have two linnks which you may find interesting:
Mixed content Test (Bennish) [https://www.bennish.net/mixed-content.html]
Mixed Content Test (Mozilla) [https://people.mozilla.org/~mkelly/mixed_test.html]
– -> [People.mozilla.org] was DOWN at ~2018-02-24-12:30 GMT
Thank you sir! I bookmarked the first link and the second one was down for me also.
Is mixed content even a thing anymore? I opened dozens of my bookmarks and am yet to see a website that uses mixed content.
https://www.ghacks.net/2013/04/09/firefox-23-to-block-insecure-contents-from-being-loaded-on-https-pages/
Has this not always been present on firefox.?
Martin, I’m afraid I don’t quite understand the implications of,
“Mozilla plans to launch a new feature in Firefox 60 that upgrades optionally-blockable mixed content on HTTPS sites to HTTPS if possible.”
Upgrade? Does this mean that Firefox will attempt to switch to https mixed-content originally called with http? And if that fails, will it block the mixed content or revert to http?
Here, concerning mixed-content, default Firefox settings (except one modification,
// MIXED CONTENT
// disable insecure active content on https pages – mixed content
user_pref(“security.mixed_content.block_active_content”, true); // Default = true
// disable insecure passive content (such as images) on https pages – mixed context
user_pref(“security.mixed_content.block_display_content”, false); // Default = false
// enable Mixed-Content-Blocker to use the HSTS cache but disable the HSTS Priming requests (FF51+)
// user_pref(“security.mixed_content.use_hsts”, true); // Default = false, I leave it false
user_pref(“security.mixed_content.send_hsts_priming”, false); // Default = true
As always I refer to Pants’ Ghacks-userjs settings.
Thanks @Jessica @Martin.
I’ll have a look at the the Google Groups link.
Note that this is an experiment and the setting is enabled only in Nightly by default temporarily to gather some feedback, as per the thread I linked to.
Tom, yes, it attempts to load the resource from HTTPS instead of the referenced HTTP. If that does not work, it blocks the resource. Not sure why they don’t fall back to HTTP in that case though.
Here you go:
https://groups.google.com/forum/#!msg/mozilla.dev.platform/xjZQq0kEauM/w8OKXv7EAQAJ
Google’s Group indeed states “If the resource doesn’t exist over HTTPS, it will
fail to load. [regarding mixed passive content unavailable via https after testing]”
I remain a bit surprised as I’ve always considered that if non-secured Mixed Active Content should be blocked (and it is by default on Firefox), on the other hand non-secured Mixed Passive Content had no serious reason to be blocked (and it isn’t on Firefox at this time).
That Firefox 60 plans to start Mixed Passive Content with https is great, but blocking it in case it fails to load via https surprises me. At this time much passive content transits only through http…
This way of approaching problem is wrong. Admins should fix this themselves on their website.
Be realistic. A lot of admins don’t do that and HTTPS is important for the security and privacy of the user. So it’s the right approach because resources are very often also available via HTTPS even if referenced via HTTP. So good move from Mozilla from the user’s point of view.
They wouldn’t, that has never happened. The move to HTTPS has been browser-driven from the start. Certificate authorities themselves have to answer to major browsers when they mess up security wise.