Firefox 23 to block insecure contents from being loaded on https pages
If you are a veteran Firefox user you may remember that Mozilla implemented options to block insecure contents from being loaded on https pages in Firefox 18. The feature has been disabled by default in the version of the browser and users who wanted to increase the security of it had to change the values of its parameters manually to do so.
So what does it do if enabled? Whenever you connect the browser to a secure webpage using SSL - you can confirm that by making sure the web address starts with https - only contents that use SSL should be loaded for security purposes. Websites sometimes load insecure contents, say a script using an http connection on secure sites. That's a security issue right there and the setting introduced in Firefox 18 prevents this from happening if enabled.
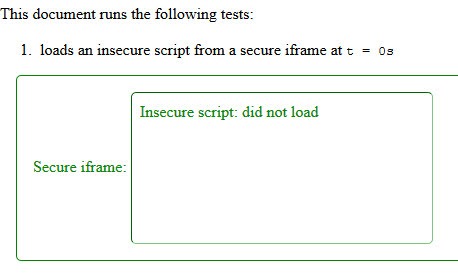
Here is a visualization of how this looks like. The insecure script that is loaded inside the secure iframe is not loaded when the feature is enabled.
After rigorous testing Mozilla decided to enable one of the two mixed content preferences in Firefox 23 by default. Firefox 23 is currently the version of the Nightly channel and it will take months before stable users of the browser will be upgraded to that version. Still, it is important to know that this is going to happen eventually.
The developers have integrated two mixed content preferences into the browser:
- security.mixed_content.block_active_content - This preferences blocks active contents including scripts, plug-in contents, inline frames, Web fonts and WebSockets from being loaded on secure websites if they are offered via insecure connections.
- security.mixed_content.block_display_content - The second preference adds static display related contents to the blocked content list. This includes image, audio and video files
If you are running Firefox 18 or newer, you may modify the preferences at any time. Let me show you how to do so.
- Type about:config into the browser's address bar and hit the enter key.
- Confirm that you will be careful if this is the first time you are opening the page.
- Use the search form at the top to filter for security.mixed which should display only the two parameters above.
- A value of True means they are active, while False indicates that they are not enabled.
- To modify the value double-click the parameter.
So, if you want to improve the security of your browser right away, set the active content parameter to true right away.
Advertisement



















I will never trust firefox again no matter how good the plugin are because you won’t find one to stop firefox from spying on all your DLNA devices.
I found that the android version of FF without any plugins is listening in to DLNA broacast messages from devices like XBoxes and Samsung Smart TVs and then making a UPNP request to the devices to recive XML data back from these devices.
In my case this not only includes the make and model of the TV but also the serial number and its not like my simple android device can stream to the TV or play XBox games.
I know Google pays Firefox $50m a year and they don’t do that without getting something in return as you can see if you type About:config into the URL and search for Google but I will not put up with Firefox hacking my local area network to then upload all the device data back to central server.
Shown below is both the request and reply I captured with some of the data replaced using XXX and I also had to tweak the HTML tags in the XML so it would post.
GET /smp_24_ hxxp/1.1
Host: X.X.X.40:7676
User-Agent: Mozilla/5.0 (Android; Tablet; rv:36.0) Gecko/36.0 Firefox/36.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
hxxp/1.1 200 OK
CONTENT-LANGUAGE: UTF-8
CONTENT-TYPE: text/xml; charset=”utf-8″
CONTENT-LENGTH: 1167
Date: Thu, 01 Jan 1970 03:59:18 GMT
connection: close
Application-URL: hxxp://X.XX.40:80/ws/app/
SERVER: SHP, UPnP/1.0, Samsung UPnP SDK/1.0
[?xml version=”1.0″?][root xmlns=’urn:schemas-upnp-org:device-1-0′ xmlns:sec=’hxxp://www.sec.co.kr/dlna’ xmlns:dlna=’urn:schemas-dlna-org:device-1-0′] [specVersion] [major]1[/major] [minor]0[/minor] [/specVersion] [device] [deviceType]urn:dial-multiscreen-org:device:dialreceiver:1[/deviceType] [friendlyName][TV]Samsung50[/friendlyName] [manufacturer]Samsung Electronics[/manufacturer] [manufacturerURL]hxxp://www.samsung.com/sec[/manufacturerURL] [modelDescription]Samsung TV NS[/modelDescription] [modelName]XXX9200[/modelName] [modelNumber]1.0[/modelNumber] [modelURL]hxxp://www.samsung.com/sec[/modelURL] [serialNumber]XXXXXXXXXX[/serialNumber] [UDN]uuid:0dbXXXXXXXXXXXX[/UDN] [sec:deviceID]XXXXXXOMKVUK[/sec:deviceID] [sec:ProductCap]Resolution:1280X720,Y2013[/sec:ProductCap] [serviceList] [service] [serviceType]urn:dial-multiscreen-org:service:dial:1[/serviceType] [serviceId]urn:dial-multiscreen-org:serviceId:dial[/serviceId] [controlURL]/smp_26_[/controlURL] [eventSubURL]/smp_27_[/eventSubURL] [SCPDURL]/smp_25_[/SCPDURL] [/service] [/serviceList] [/device][/root]
Everything is good except that it blocks youtube videos from playing if you use youtube with https.
Did you enable security.mixed_content.block_display_content as well? They aren’t turning that one on for Firefox 23 and it does appear to break youtube (and they know about it)
Same issue as Hmm, with only security.mixed_content.block_active_content set to true.
Reported as well with “Https Everywhere” (though due to the fact ‘Https Everywhere’ calls Youtube with https) here : https://trac.torproject.org/projects/tor/ticket/8674
Many sites are not ready, which is why starting with Firefox 21 there should be a Mixed Content Blocker UI allowing an on/off switch on a per-site basis ( https://blog.mozilla.org/tanvi/2013/04/10/mixed-content-blocking-enabled-in-firefox-23/ )
Will FIrefox display a warning if this is enabled, and it blocks something? In Chrome you get a little silver shield in the address bar at the far right where you have the bookmark star. When you click on it you get info of what was blocked.
I don’t see any warning anymore. But, I guess this feature is still preliminary.
Thanks for this Martin. For some weird reason the Plugin forums at WordPress.org deliver CSS files over http instead of https and Firefox Nightly has been driving me wild by blocking these!