Test your web browser's cryptojacking protection
Investment in crypto-assets is unregulated, may not be suitable for retail investors and the entire amount invested may be lost. It is important to read and understand the risks of this investment, which are explained in detail here.
Cryptojacking is a relatively new threat on the Internet. It refers to websites abusing computing resources of visitors to mine cryptocurrency.
Internet users notice that something is wrong when the computer they use slows down to a crawl suddenly and when fans speed up in an attempt to cool down components of the device that get hammered.
The main issue with cryptojacking is that it is done behind the backs of users. Sites load cryptomining scripts on load to mine cryptocurrency using the resources of the computer of the user visiting the site. There is no opt-in process or information on what is going on.
Sites run these scripts to generate revenue. One of the advantages of running mining operations in the browser is that it happens in the background. It does not interfere with the site's layout or content.
Browser extensions may load crypto mining scripts as well. These work in the background just like scripts loaded by sites.
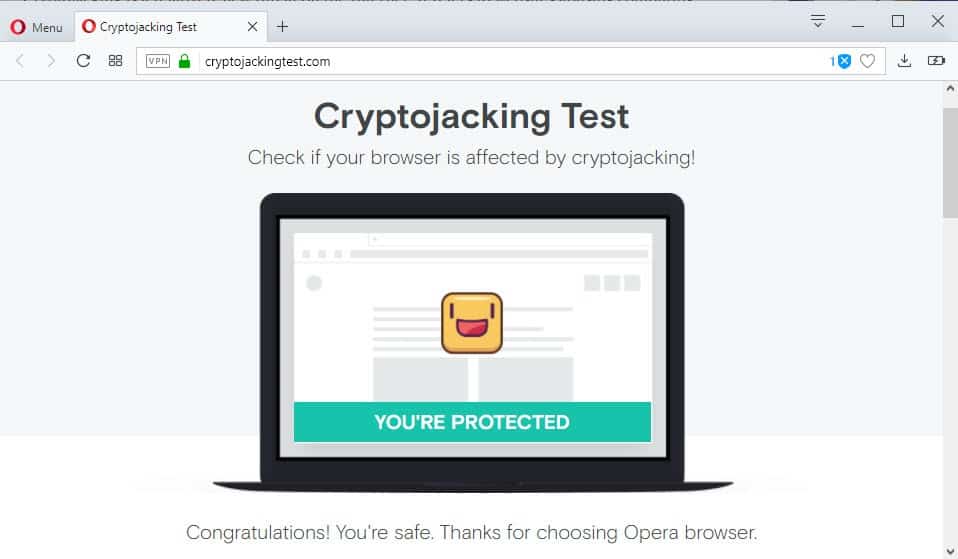
Cryptojacking Test
Opera Software was the first browser-making company that implemented anti-crypto mining protections in the browser natively.
While Opera was the first browser, content-blocking lists added cryptomining scripts before Opera did so.
Opera Software engineers created a site that you may visit to test whether you are protected against cryptojacking.
Visit the website and click on the start button on it to run the test. It won't take longer than a couple of seconds to complete and the result is either that the browser that you are using is protected or unprotected.
Opera Software displays aggregate ratings on the site as well. 73.6% of all users are protected from cryptojackingat the time of writing according to the statistics on the page.
Users who run browsers that are not protected have several options at their disposal to protect their browsers against crypto mining attacks.
- Use a browser extension that protects against JavaScript mining scripts.
- Use the Opera browser with ad-blocking enabled.
- Use a security software that protects against mining scripts.
- Install an anti-mining browser extension.
- Disable JavaScript on untrusted sites.
Closing Words
Opera tests the protection against a Coin Hive script only which leaves the possibility that the browser is vulnerable to these scripts. It is only a matter of time usually before new scripts or URLs do get blocked though.
Now You: Did you run into cryptomining sites in the past?
Related articles






















Anyone out there seeking to recover any form of crypto coins and financial assets from online scams or wallet hackers, also BTC sent to wrong addresses, I recommend this very dependable agency Spyware Cyber. This recovery specialist was fantastic in helping me recover my BTC, lost to these evil con-artists after I provided all relative information and requirements to this recovery specialist. Of the 1.4 BTC stolen from my wallet, a total of 1.2BTC was finally recovered. I was glad I was able to recover this much after losing even more to the fake platform I initially contacted before I was in contact with this excellent specialist. Go ahead, and contact Spyware Cyber by email: SPYWARE(@)CYBERGAL.COM, if you are in such a situation seeking recovery from any form of online cryptocurrency scam, tell them the incident and follow their instructions so they could help you with recuperation.
Regards,
Marvin Cecil
I usually don’t share my story with people online and those I don’t know, not only because it put me at the lowest point ever but because it made me a person of ridicule among family and some of my friends. I put all I had into Binary Options ($190,000) after hearing great testimonies about this new investment strategy. I was made to believe my investment would be triple, it started good and I got returns (not up to what I had invested). Gathered more and involved a couple family members, but I didn’t know I was setting myself up for the kill, in less than no time all we had put ($420,000) was gone. It almost seem I had set them up, they came at me strong and hard. After searching and looking for how to make those scums pay back, I got introduced to Mr Hang a recovery agent who helped recover about 85% of my lost funds within 3 days and I was very happy with is good service and honest review catch him up for your lost funds with Email address: Bitcoinitspecialist @gmail.com ) or via phone. (281) 784-0586)
Blockchain and Cryptocurrency Email List for B2B Marketing
Never mind Opera’s fantasies, does Opera pass Panopticlick’s test?
https://panopticlick.eff.org/
Nobody does out of the box except for this browser…
http://theclassictools.com/
https://cryptojackingtest.com/
fake on chrome as mineblock recognizes that its running while you testing
opera pretty fooling people to check while they mine lol
Interestingly, Avast detects that cryptojackingtest.com leaves a js:miner-c in my browser’s cache.
I add this:
https://www.grahamcluley.com/stop-dilly-dallying-block-ads-youtube/
Brave passes with its default configuration.
“Opera Software was the first browser-making company that implemented anti-crypto mining protections in the browser natively.”
But I’m pretty sure Brave Browser is the first browser that implemented it. https://twitter.com/brianbondy/status/909867392750297090 :)
I’m pretty sure my install of Firefox came with uBO which had filters for bitcoin miners when it was updated to version 56 so it definitely beat Opera and Brave. ;)
Just to be clear, that was a joke. :)
Protected – using the Brave browser.
I ran the test with NoScript disabled because it would not run otherwise.
Kaspersky (KIS 2017) immediately caught the crypto script testing code and flagged it as malware ;-)
Then the test page reported that I wasn’t protected… but I’m sure I am; I just think the test page does not account for protection software doing its thing. Its not a thorough test on the part of Opera.
If someone’s interested, here’s a blocklist that looks more comprehensive than NoCoin:
https://github.com/ZeroDot1/CoinBlockerLists
Thanks
I’m always amused when I visit test sites like this and they say “Oops! It seems you have JavaScript disabled in your browser”. Yes, that’s why I use the NoScript extension, silly billies!
Protected here on Firefox 58 even with ‘uBlock Origin’ disabled for the testing page.
Firefox’s native tracking protection option is disabled. No dedicated anti-cryptojacking Firefox extension.
No idea though if the protection is that of Firefox or of my system-wide defense which I’ve fed with cryptojacking addresses and domains. I could find out but I’d have to start logging. No problem, thanks to God or the army or the cops or my settings, as long as I’m safe …
It seems that Firefox with Tracking Protection enabled (a built-in feature) passes the test (I disabled Ghostery during the test, and it still passed). This would make sense, since cryptojacking is performed by third parties, which are probably identified as trackers by Mozilla.
Nice find!
Didn’t think of running that test. I disabled uBlock Origin, ran the test, and saw the same results. I’ve been using Tracking Protection for a while now and I’m a big fan. It’s very light on resources and when it’s working on a site, if anything, it lowers ram usage, from what I’ve seen. I’ve always been of the opinion that a lot of people aren’t aware of how aggressive “Tracking Protection” actually is.
I just looked on github and Disconnect added bitcoin miners back on Nov 15, 2017. If someone is not using uBlock Origin which has the default “Resource abuse” filter I would recommend using the No Coin Filter list, the list in Disconnect isn’t as comprehensive as the other two. Still, it’s pretty nice that Tracking Protection includes what it does.
All this methods won’t protect you against custom made mining scripts. In the end tou run someones code in you browser all the time.
I just monitor my CPU usage by Process Explorer tray icon graph constantly so if my CPU usage spikes on page I will notice that immediately.
“All this methods won’t protect you against custom made mining scripts”
If you aren’t allowing scripts to run in your browser, then you’re protected from all scripts, custom or otherwise. That’s one of the reasons why I haven’t allowed scripts to run in my browser for years (aside from hand-picked exceptions). It’s too risky.
I added the NoCoin filter list to Adblock Plus = my browser is protected, according to the test.
link for the lazy: https://cryptojackingtest.com/
I’m not seeing a link for the test Martin.
I’m curious how it would fare against the “Resource abuse” filter list in uBlock Origin, which is now bigger than the No Coin filter list.
As it turns out, with uBO’s Resource abuse filter and without No
Coin the browser passed the test
Sorry for that, link is here: https://cryptojackingtest.com/
Thank you sir. ;)
This is just a ploy to entice people to use opera browser.Opera is a good browser but an adblocking extension can be installed on any browser not just opera.
This is a test to see if you have an adblock installed and is not browser specific.
I take it we just type “cryptojackingtest.com”? I can’t find a link anywhere to the test.
Yes, link added.
Thank you.
My setup at Firefox and Edge browser (no Opera for me):
– uBlock origin with No Coin Filter list installed
– Malwarebytes with all protections enabled
That’s it! No slowdown and no coin miners until now.