How to block Bitcoin Mining in your browser
Investment in crypto-assets is unregulated, may not be suitable for retail investors and the entire amount invested may be lost. It is important to read and understand the risks of this investment, which are explained in detail here.
Bitcoin mining can be profitable, and that is likely the reason why we have seen desktop miners and now also browser miners being pushed on to user devices.
The Piratebay experimented with running a Bitcoin miner instead of ads recently, and created quite the uproar as users started to notice that the new monetization method would yank up CPU usage to 100%.
An update of the Google Chrome extension SafeBrowse integrated a JavaScript miner as well in the extension, and led to the removal of the extension from Google's Chrome Web Store.
Any site you visit in the browser, and any browser extension, may run Bitcoin mining operations. While it seems highly unlikely that popular or user respecting sites or extensions will do that, it seems likely that these first incidents were just the first wave of mining operations to come.
Computer users have a couple of options when it comes to protecting their devices against browser-based Bitcoin mining.
While it is certainly possible to use content blocking extensions to prevent mining scripts to run in first place on sites, these usually won't block extension-based mining.
Probably the best option right now is to block known Bitcoin mining domains. One of the better options to do that is to add these to the hosts file of the operating system so that these domains redirect to localhost.
The effect is that sites and extensions won't be able to contact these domains anymore because of the redirect. Downside is that you need to add new domains and modify existing ones if the need arises manually.

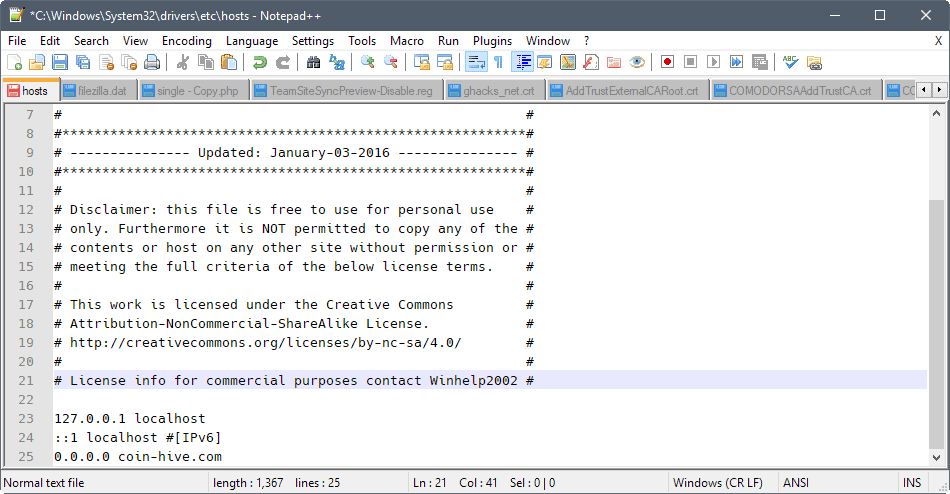
Windows users need to do the following to add Bitcoin mining domains to the hosts file:
- Open Explorer or another file manager on the system, and go to C:\Windows\System32\drivers\etc.
- Open the file hosts in a plain text editor, for instance Notepad.
- Add the line 0.0.0.0 coin-hive.com to the end of the document. Make sure you press the Tab-key after entering the IP address 0.0.0.0.
- Save the document.
What this does is redirect any request to coin-hive.com to the IP address 0.0.0.0 (the local device).
As Ghacks reader Linuxfan mentioned, the line mentioned above blocks only coin-hive.com but not any subdomain such as www.coin-hive.com. So, you may need to add these variants if they are used as well to the hosts file.
Tip: On Linux, you can run sudo nano /etc/hosts, on Mac OS X, sudo nano /private/etc/hosts. Replace nano with whatever editor you favor.
This takes care of Bitcoin mining scripts hosted by coin-hive.com, the service that both the Pirate Bay and the Chrome extension used. Note that this won't take into account self-hosted scripts. You need to add those separately to the hosts file to block them as well.
Another option that you have is to disable JavaScript on these sites. This may not be possible all the time, as sites may require JavaScript for some or all of functionality, but Bitcoin miners based on JavaScript cannot run if JavaScript is disabled.
Check out these resources for additional information on the hosts file:
Now You: Do you use the hosts file to block online resources?






















*sigh* why do people have to ruin it for everyone? I did a similar thing with javascript 5 or 6 years ago to mine bitcoins, but it was OPTIONAL and it wasn’t turned on automatically. Basically visitors could click something to donate some CPU time if they wanted to.
Firefox Update installs Miner silently..the fucken cunts
You can also use the excellent Mineblock : https://mineblock.org
@planet42 – Tried it & Malwarebytes blocks it when it silently tries to download coinhive…
Great article,thanks a lot. Seems lately, many website’s start’s using Monero miners. Some of the sites warn’s when you visit, some not. Lazy people looking for every possible way to make some money behind screens.
upon hearing of THB running the Coin Hive script, i had much the same reaction as most of you here – i saw it as outright malware – but upon further thought and READING the docs on coin-hive.com, including their privacy policy (which is very strong) and goals, i have reached a very different conclusion
i think JS crypto-mining is potentially a huge game-changer and an excellent way to monetize a site *as long as it’s presented as an opt-IN solution*
this could be a great way to declutter the interwebs of much of the annoying ads and having to beg for donations and it costs the average visitor essentially nothing as long as you don’t hog their CPU
the problem right now is that greedy, unethical, self-serving morons are implementing such mining scripts without ever notifying the user – in the case of Coin Hive, they are working to combat this nonsense by making it difficult/impossible for their script to run unless consent is given and i like this ethic
think of this tech not as malware, but as a SOLUTION to making the web a cleaner place in many ways – think of all the garbage content, besides ads, that is written solely with monetization in mind, tracking links, affiliate links, etc., etc., etc.
wouldn’t it be great to see a lot of this garbage disappear?
some quotes from Coin Hive…
” Our goal was to offer a viable alternative to intrusive and annoying ads that litter so many websites today. These ads are not only a distraction to end users, but also provide notoriously unpredictable and non-transparent revenue numbers. We set out to change that.
[…]
We’re a bit saddened to see that some of our customers integrate Coinhive into their pages without disclosing to their users what’s going on, let alone asking for their permission. We believe there’s so much more potential for our solution, but we have to be respectful to our end users.
[…]
It’s probably too late to do anything about the adblockers that already prevent our current JavaScript from loading. Instead, we will focus on a new implementation that requires an explicit opt-in from the end user to run. We will verify this opt-in on our servers and will implement it in a way that it can not be circumvented. We will pledge to keep the opt-in in tact at all times, without exceptions.”
and from their privacy policy…
“We do not track users. We do not use cookies. We do not use any third party tracking (Google Analytics, Piwik, …).”
for more, visit coin-hive.com and read their blog, privacy policy, etc.
i also wrote a brief blog post about this here:
The Pirate Bay and its cryptocurrency mining script – why this might be the best thing since DOOM
http://12bytes.org/10227/the-pirate-bay-and-its-cryptocurrency-mining-script-why-this-might-be-the-best-thing-since-doom
I’m in trouble and would appreciate lay-language advice on digging myself out of it.
HOW UN-TECHY GHACKS FOLLOWERS CAN STRAY INTO A BOG
I download webcams with Jaksta and, for one particular type (nest.com), have to use Edge browser as no other browser (FF, Chrome, Opera, IE) will let it download. I need to auto-refresh periodically in order to keep streams going but Edge has no extension for it, so I’ve been using RefreshThing.com to do the job.
That was OK-ish until a few days ago, when Malwarebytes starting popping up blocking notices one after the other in quick succession, all of them variants of coin-hive.com, and the only way to stop them (trial and error, I have 3 browsers and loads of tabs open) was to close RefreshThing down.
A comment on Martin’s timely article led me to add this filter to AdBlockPlus in Edge: https://github.com/hoshsadiq/adblock-nocoin-list/ … since when all new tabs became unresponsive, including the AdBlock ‘disable list’, so AdBlock has been uninstalled… and now I can’t reinstall it because MS Store thinks I’m offline and I can’t fix that.
Inconvenient, to say the least, as well as embarrassing.
Hi Martin,
A quick question: I see that you’re blocking IPV6 and localhost as well…. any particular reason? My ISP doesn’t provide IPV6, however, the Apple Airport Extreme (5th Gen) gets me into some trouble now and then. :(
Thanks.
A
localhost is supposed to resolve to 127.0.0.1/::1
https://en.wikipedia.org/wiki/Localhost
https://en.wikipedia.org/wiki/Hosts_(file)
This coin-hive.com website is already included in Steven Black’s hosts file – among other 38 thousand undesirable websites: https://github.com/StevenBlack/hosts/blob/master/readme.md
Recommended! It blocks all kinds of adware, malware, ad servers, etc.
Kaspersky is detecting and blocking it as malware.
Just use this filter list with uBlock Origin (or AdBlock Plus)…
https://github.com/hoshsadiq/adblock-nocoin-list
Thank you for the link to the nocoin list. I was able to import it directly from the interweb into Opera’s built in adblocker. And so Opera will check and update it for me.
While rules for content blockers are fine if websites include undesirable third-party scripts, things work differently if that code is included in an extension. No content blocker will be able to affect this, at least once you’re past the point of using a legacy Firefox extension.
You’re left with doing this on an OS scale and not a browser scale. However, there are no easy built-in tools for this purpose, as both the hosts file and the Windows Firewall do not allow wildcards as you would want to use them. The best you can do is block whole IP subnets in the firewall, but that’s unlikely to be a good solution.
In the end my suggestion would be to run a local DNS server, which makes blocking this kind of thing child’s play (but also a lot more work to set up and maintain). In case you’re using the default DHCP settings when connected to your local network, you’re often already using a local DNS server courtesy of your router without even knowing it. To get the most out of a local DNS server you will need more than that however, my suggestion would be OpenDNS which uses an “implied wildcard” system, where a blocked entry “domain.net” would work as *.domain.net and thus block both domain.net itself but also any subdomain. Like mentioned, this takes time, experience and opportunity to set up, but a local DNS server can have some minor performance advantages and in this case it would also allow you to block certain domains for the entire local network.
I checked uBlock and it blocked thosed url by default. No need to use Adblock Plus
NoScript blocks coin-hive.com. However it certainly won’t hurt to add it to the host file.
Here is another way to do it.
Add this to your Adblock or uBlock filter.
||coin-hive.com^$third-party
||jsecoin.com^$third-party
||miner.pr0gramm.com^
||gus.host/coins.js$script
||cnhv.co^
in uBlock, should these be added to the tab My filters or to the tab My rules?
You can subscribe to this list with ublock or adblock.
https://github.com/hoshsadiq/adblock-nocoin-list/
Has all the above urls.
uBlock blocked them by default. No need to add
Martin –
There was an article posted on BetaNews last night regarding how to add a filter to the Adblock Plus extension in your browser to protect against the Bitcoin hijack as well.
https://betanews.com/2017/09/21/adblock-plus-block-cryptocurrency-miners/
I followed the simple instructions and added the filter. I’d be interested to see what you and the ghacks community thinks about this.
Martin,
it’s not a bitcoin miner, but a monero one instead.
you never mentioned it in the article.
monero is based on cryptonote whose proof-of-work algorithm is designed to be suitable for ordinary PC CPUs
Just use Easyprivacy tracking list, it’s currently blocking this domain.
Thank You! Very much appreciate what you do!!!!!!!!!!
Actually saw two entries for mining domains.
||coin-hive.com^$third-party
||jsecoin.com^$third-party
And…people got to TPB with javascript enabled? That’s friggin scary! What with the miner, redirects and God knows what else. Will not be saddened when they get shut down, next time, again. SMH!
Martin, this rule works. However, one should be aware of the shortcomings of using a hosts file: It only blocks *exactly* what’s added in that file. Hence, a rule like
0.0.0.0 coin-hive.com
does *not* block, e.g.,
http://www.coin-hive.com
mining.coin-hive.com
… etc. …
This is exactly the reason why a rule like
0.0.0.0 doubleclick.net
is not sufficient but literally hundreds of rules are necessary to cover all variants of doubleclick. And wildcards or placeholders are not allowed in a hosts file! See also the remarks on https://wiki.ubuntuusers.de/hosts/#IP-Adressen-umleiten.
So a better solution is definitely using uBlock Origin’s Dynamic Filtering or uMatrix as they make sure that all relevant sub-domains are also blocked.
You are right, thanks. I add that to the guide to make it clearer
I only use the long-established free host file (http://winhelp2002.mvps.org/hosts.htm) which has entries like,
0.0.0.0 coin-hive.com
0.0.0.0 ws017.coin-hive.com
0.0.0.0 ws022.coin-hive.com
0.0.0.0 ws023.coin-hive.com
0.0.0.0 ws024.coin-hive.com
0.0.0.0 ws025.coin-hive.com
0.0.0.0 ws026.coin-hive.com
0.0.0.0 ws027.coin-hive.com
0.0.0.0 ws028.coin-hive.com
0.0.0.0 ws032.coin-hive.com
And https://cryptojackingtest.com/ says I am protected (running Firefox). Thank God for those who provide such helps.
Done. CPU says “Thanks” and I agree.
“Make sure you press the Tab-key after entering the IP address 0.0.0.0.” : a simple space is enough.
Nice tip thx!
I haven’t though of using host file to block this nasty thing, I mainly use host file to be able to use Photoshop^^,mainly Ublock Origin+Umatrix.
Sad to see Piratebay using miner too ;'(
Host files can only block fixed ip addresses. Some websites are sneaky and generate random script names from multiple random domain names. To block this, you need a blocker that analyse mining patterns in scripts, not just block the host. I use Mineblock which does just that https://mineblock.org