First Chrome extension with JavaScript Crypto Miner detected
Google's automatic verification system for Chrome extension uploads to the official Chrome Web Store is a wreck; less than a day after the Steam Inventory Helper incident, another Chrome extension was found to abuse user trust by using user systems for crypto currency mining.
The most recent version of Steam Inventory Helper transfers any page a user visits in Chrome to a third-party server. The free browser extension SafeBrowse on the other hand runs a crypto mining module in the background while it is enabled in the browser and while the browser is open on the system.
SafeBrowse's main purpose is to skip forced intermediary advertising pages from services such as adf.ly or Linkbucks.
The most recent update of the browser extension includes a crypto miner that runs in the browser automatically. It uses the computer's processing power -- CPU -- to mine cryptocurrency.
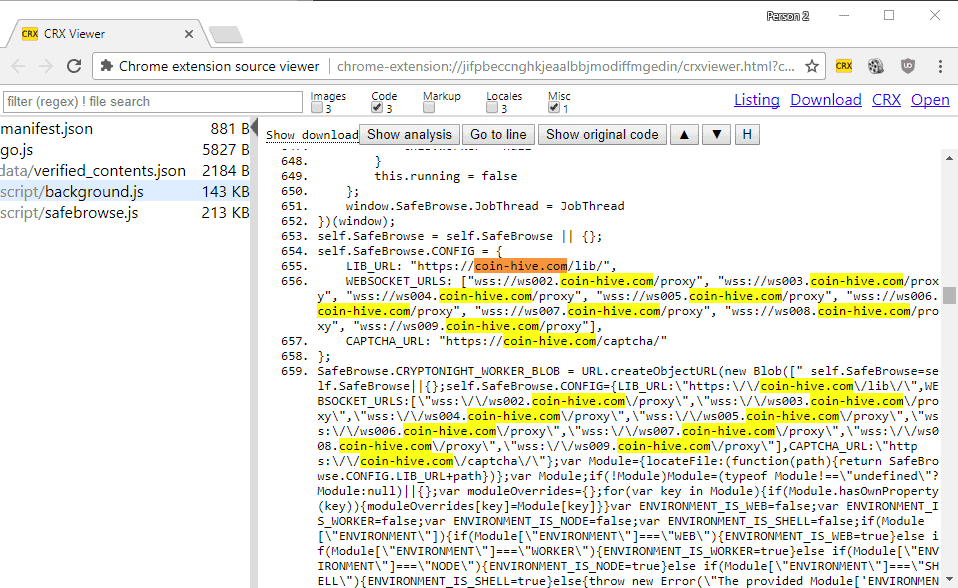
Chrome users who have installed the browser extension may have noticed that CPU usage is going up whenever Chrome is open. Those with proper firewall protection may have noticed that connections are made to the domain coin-hive.com.
A quick look at the source code of the Chrome extension SafeBrowse confirms that connections are made to the site.

The rise of in-browser crypto mining seems inevitable. One of the longest standing torrent indexing sites, The Pirate Bay, was found to run a crypto miner on its website as well this month.
Torrentfreak broke the story, and a quick analysis of the Pirate Bay's code revealed that it too used the JavaScript miner provided by Coin Hive.
Now it is the first Google Chrome extension that mines crypto currency while the extension is installed, and it seems likely that it won't be the only one that will make use of such an option.
While there is nothing wrong with crypto mining in the browser, other than that it is highly ineffective as it relies solely on the processor, it becomes a huge issue if the mining is not user initiated but enforced automatically either on visit or when an extension is installed.
The first anti-mining browser extension was released recently. No Coin is designed to block known mining domains, but it may not work properly if the mining comes from an extension and not from a website.
Anyway, if you have installed SafeBrowse for Chrome, it is probably a good idea to uninstall the browser extension at this point in time.
Google needs to change its stance on the store's verification process for new extensions and extension updates. Mozilla, a much smaller organization, does this a lot better as it has a manual review policy in place for all new and updated Firefox extensions.



















Google has to do something about this. More and more extensions are now using mining libs. It is disgusting. One of my extensions I used for years now has it too, and I was wondering why I had high CPU all the time since weeks. It is called “Archive Poster” for tumblr. Beware!
i visited the pirate bay to block coin-hive.com globally as i use uBlock Origin in Advance Mode – Medium Mode, it was already Red, but i still blocked it globally. i think i’m good.
Just a comment but it’s a shame that ghacks like many other websites now add a link in the middle of a blog (read also) (you may also like) that goes to a totally unrelated site/post/blog/url etc. Like reading a book then a commercial appears in the middle of a page. Distracting & annoying. IMHO
Calm down folks.
The PirateBay tested .. yes tested! a crypto miner to avoid ads, which is a good thing, only bad here was that this was used on the entire Browser session and that was what people complained about. But again it was a test, mining instead of ads are pretty much okay, as long it shutdown after you close the page. It’s not a big deal to fix this.
You not need any addon if you don’t like this because a simple extension like umatrix can block this, or if you not need it, just disable javascript for the page, and it does the same.
Actually mining instead of getting ads is way more secure than getting connected to unknown and possible insecure advertising hosts.
I don’t know… having my cpu cycles wasted on mining crypto currency particularly on a constant basis is vastly outstretching beyond the value of said site or software.
I am sure we here constantly tweak our browsers and systems to consume as little memory and resources as possible so having this shady kinda cloak and dagger action happening in the background is not good at all.
It’s a trend we need to squash now before it runs rampant.
Its great the umatrix blocks it but I am sure there will be a wack-a-mole situation here too with perhaps more invasive techniques and results.
@ CHEF-KOCH
“The PirateBay tested .. yes tested! a crypto miner to avoid ads, which is a good thing.”
Totally disagree. Not a good thing, especially for clueless computer dummies/non-techies.
When a website clandestinely or secretively uses the CPU and RAM resources of its visitors’ computers for crypto-currency mining, this would shorten the life-span of the visitors’ computer hardware and may even do accidental damage to the hardware.
……. Crypto-currency mining using website visitors’ computer resources is likely more harmful to the website visitors than the display of ads on web-pages. It has been an accepted business model for nearly all free-to-air TV companies to survive on ads, eg ABC, CBS and FOX. Similarly for Google and Facebook.
Malware can infiltrate through many ways, eg email attachments, downloaded files, corrupted ad scripts, OS and program vulnerabilities, etc. Does that mean we should abolish all emails, OS/programs, file downloads, ads, etc.?
@ AnorKnee Merce
No, I was replying Chef-Koch, and a rhetorical supporter of Bitcoin mining on other people’s computers, unallowed.
@ CHEF-KOCH
A freely-accessible website planting a hidden coin-mining program into visitors’ computers is not very different from it planting a hidden malware-bot-net program into visitors’ computers. Those who control bot-nets can also make money by sending millions of spam emails for seedy advertisers, eg ads for Viagra pills, penis elongation pills, dating websites, contacts for love scams, etc.
Pirate Bay is a seedy or disreputable website. It has previously been shutdown by certain governments.
@ Clairvaux
Are you replying to me.?
Notice that it is mostly seedy websites and extensions that are beginning to use crypto-currency mining hiddenware or coinware, eg Pirate Bay.
There’s a concept called property rights. My computer is mine.
You might get blue in the face explaining me how your squatting it does not really harm me, but the point is, it’s not your damn business. That’s for me to decide.
Again it was a test, in the future they use less CPU cycles and they detect if you’re on mobile phone or not. I see this as a big step forward compared to ads. The hardware also not get a damage, no matter what, each CPU has thermal sensor and the bios/mobo has a limit, when it gets reached the system normally shutdown unless you disabled the mechanism in your bios.
There is no harm in using CPU cycles at all, except that it costs for a short amount of time a little bit more energy. Ads can do much more harm here, which was several times now proven by ghacks and other pages.
No, crypto mining is not that easy to hack or infect this way as you described it, because that would require to hack the entire crypto mining page + deliver another version of the javascript to redirect the processing power, this is very easy detectable by TPB.
I dunno, what the rest of your ‘argument’ is but you’re wrong, mining is better than ads, for sure and there is no reason to block this, we all need to pay our bills. Even today’s onboard graphic chips are powerful enough to handle it without any problem or lag. TPB just need adjustments, but that is what the test was designed for, get feedback and change things.
People never should forget that you pay for ‘free’ things with your private data or in this case with CPU cycles, well I prefer last one and support the pages I like. Maybe Ghacks also get such a feature. I would like that instead of ‘traditional’ ads.
You don’t need any extensions of any kind. This is how you permanently and simply block coin-hive;
(Windows) hosts file –
127.0.0.1 coin-hive.com
Done. No cpu usage because there is no communication.
What happened to the new ghacks theme? https://www.ghacks.net/?theme=ghacks gives me the old same lame theme
Coming, yeah I know ;)
Android and now Chrome… Google’s app store security is a joke.
Martin, Did you already notice that your hyperlink reference under the word SafeBrowse does only lead to a Error 404 (Nof foud)!!! , ?
https://chrome.google.com/webstore/detail/safebrowse/obkfjhifkbhimlocpddgamonjihinpak/support
No did not notice but thanks for letting me know. No way of knowing who pulled it though.
“Google’s automatic verification system for Chrome extension uploads to the official Chrome Web Store is a wreck”
Why should it be better than Google’s verification on new apps in Google Play ?
Automation clearly does not work, and Google needs to address this quickly in my opinion.
These “crypto-miners” are the new “browser toolbars” that nobody wanted of yesteryear
It probably won’t be long before we start seeing check-boxes to uncheck their installation in software installers.
Speaking of rogue extensions, my Avast anti-virus (please don’t shoot the pianist, thank you) has just flagged Web Storage Viewer (for Firefox), which it tars with a “very poor” reputation, and wants to remove. I mention this because it has been reviewed by Ghacks.
I was unable to find the reputation database used by Avast, or the reason why this add-on is flagged in this manner. It stays there for the time being.
I’d be curious to know about Web Storage Viewer too. Does anyone know if this a false positive or based on actual information?
>designed to block known mining domains
We need a uBlockOrigin filter list for this. ASAP
Yuliya, take a look at the discussion here: https://github.com/uBlockOrigin/uAssets/issues/690
EDIT: Martin, sometimes the page is getting stuck (eternal loading) when I try to post a comment. Have you noticed this?
Yes, I have. It seems to disappear when I allow “all this page” in No Script, instead of just allowing “Ghacks.net” (using Firefox).
As far as I can remember, this seems to be a new behaviour, and comments could be posted in the past with No Script active and just the Ghacks.net exception.
No I have not. Anyone else noticed this issue?
Yuliya, take a look at the discussion here: https://github.com/uBlockOrigin/uAssets/issues/690
No surprises here. These kinds of Crypto miners slipped in are becoming much more common lately and this google fiasco has always happened, its just coming to light more so now that more popular extensions are jumping ship.
Mozilla’s review process is slow though and is it guaranteed to catch something like this?
I don’t think it is for webextensions. They are now approved automatically. One of the reasons of dropping legacy addons was lack of manpower to review them.
Review is simplified and takes less time because what’s up is far easier to read thanks to the use of APIs. They still do occur.
Here are the up to date criteria: https://developer.mozilla.org/en-US/Add-ons/AMO/Policy/Reviews
I’ve just learned that uBlock Origin – Webextension only, legacy not concerned) is no longer able to filter other extensions,
“[…] uBO is not allowed to intercept network requests from other extensions.” dixit Gorhill himself at
[https://github.com/gorhill/uBlock/issues/3018#issuecomment-330539105] which means that extensions (legacy or WebExtensions), whatever thoroughly checked by Mozilla, have the ability to establish whatever connection independently of uBO-Webextension : better have a solid system defense as well.
*doesn’t mean can’t sneak through
Indeed, and it’s the case for all Chromium-based browsers too. But before that, a malicious legacy extension could have crippled uBlock Origin anyway.
I remember a time when NoScript’s developer, in an escalating conflict with an Adblock Plus list maintainer, ended up modifying NoScript and pushing an update so that ABP couldn’t bock ads on noscript.net. That was years ago, but since this developer had a close relationship with Mozilla his add-on updates weren’t reviewed before hand (there was a security reason to this: NoScript at this time regularly took care of 0-day vulnerabilities). These rights were removed and NoScript goes through manual reviews like everyone else ever since. The author apologized and acknowledged this conflict went too far.
So, just because legacy add-ons can block each other doesn’t mean they can sneak through each other as well.
There is never a 100% guarantee, but it is less likely — by a large margin — that something slips by.
Only good news this week, huh?
Internet is becoming a uninhabitable place, I have no doubt that soon a lot of sites will start to use coin miners.
Yea my energy level to keep up with this kind of crap is in the red. We have to fight everyone these days to keep control of our own computers.
Ok I’m done. You can claim your browser is secure as shit, sandboxed and whatever, but it is all meaningless with such a crazy add-on ecosystem. Not touching Chrome with a ten feet pole.
Now I wonder, are Chromium-based browsers affected by this kind of things ? (Opera, Vivaldi, Chromium itself, Brave, …)
>are Chromium-based browsers affected by this kind of things ?
Well, this extension should work on Chromium and Opera, definitely, if you install it from Chrome Store. Regarding Opera’s Store I don’t know how/if they curate their extensions. I assume they do, it feels like their store is a lot smaller and cleaner than Chrome’s.
Chromium should be safe to use, assuming you don’t install any hack developer’s extension – going the safe route, using only stuff like uB0, uMatrix, Decentraleyes, aka only extension from well reputable devs, will almost completely eliminate this possibility of being given a malfunctioning update, as even with zero curation you know these extensions updates won’t bring you any unpleasant surprises.
Here’s a question-
Mozilla says they manually review the code of submissions to their extension store. Do they manually review each update as well?
I ask because there have been examples of a widely used trustworthy extensions that have been secretly bought out, sometimes requiring the original owner to sign a non-disclosure agreement- and then been monetized into what one might consider malware. I don’t think that’s something that’s exclusive to either Chrome or Firefox. However, if Mozilla were to manually review every update (Which they may already be doing)- that would be a huge security edge.
Ideally, there would be both manual and automated checks. An extension or extension update should have to pass both for it to be publish and sent out to the public through the official “stores”. Obviously, with side-loaded extensions, people have to take their chances to some degree- that’s part and parcel of side-loading. But it’d be nice if, to the greatest extent possible, we could be certain that official extensions from various browsers’ “walled gardens” were safe and secure.
Reading that Firefox might be more secure than Chrome is an interesting sort of positive reversion to their original reputation. One of the reasons they took off and became the leading web browser at the beginning of the century was because they were considered much more secure relative to Internet Explorer. Later, they were considered very insecure relative to other browsers- one year a big convention that buys new computers and installs all updates and updated web browsers, and gives the computers themselves out as a reward to the first person who can hack into them and gain admin level access to the operating system (All legal because the owner of the computers gives permission) actually stopped using Mozilla Firefox because it was considered too easy to hack relative to all the other major browsers. They added it back to the contest the next year, but questions kind of remained. It sounds like they may be turning that around (Although we’re only hearing about extensions).
I’d love to see a security expert really analyze where all these browsers are at relative to each other these days in a comprehensive way security wise. And include everything, so people can see where browsers rank relative to each other (Someone may not want the *most* secure browsers because it could have usability issues or something, but that same person may be willing to pick the most secure browser out of a group of three that they like or something).
Opera’s Store is curated manually like Mozilla’s AMO (don’t know about specific procedures and how they compare, but I know that updates are reviewed manually). I also know that Opera has more stringent requirements around various bits and pieces, from my past correspondence with several extension devs.
Whether you’d be willing to trust them considering the Chinese stakeholders is up to you, but I find Opera a pretty pleasant browser to use alongside FF.