Driver Radar Pro: kernel mode driver security
Driver Radar Pro is a free application for Microsoft Windows devices that notifies you about programs that try to load kernel drivers.
Windows' kernel mode is used by core operating system components and trusted programs to provide them with the necessary privileges that only this mode offers.
Kernel mode is not restricted however, and any program can request kernel mode access, and the feature is sometimes exploited by sophisticated malware, for instance rootkits.
All modern versions of Windows ship with the User Account Control, a feature designed to block programs from executing high privilege tasks such as modifying the Registry, loading device drivers or modifying protected directories.
UAC prompts when a program tries to load a kernel mode driver but it won't reveal why a program requests access.
Driver Radar Pro

That's when Driver Radar Pro comes into play. The program notifies you about any program requesting kernel mode driver access while Windows is running.
Note: make sure that running security software is whitelisted, as you may get a bluescreen or other crash otherwise.
It does not interfere with core Windows applications or drovers, and ships with a whitelist of programs that it won't warn you about either.
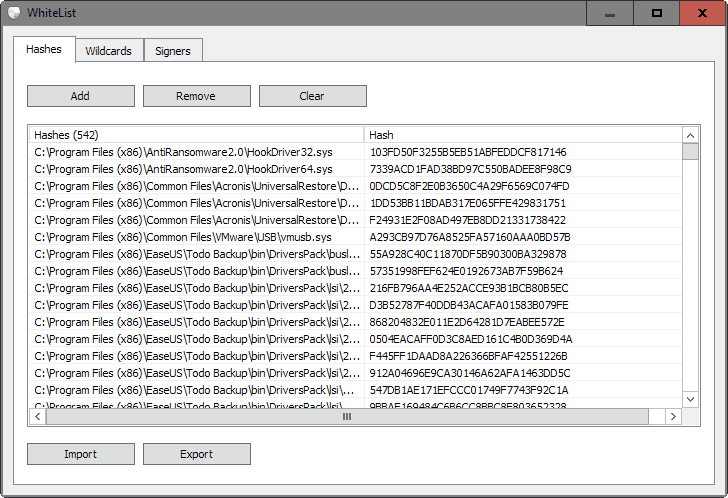
Driver Radar Pro ships with management options for that whitelist. You may remove any file hash, wildcard or signer from the whitelist, and use import and export features to make things more comfortable if you want to run the program on multiple devices.
The clear button is especially handy there as it removes all items to start with a blank slate.
Notifications
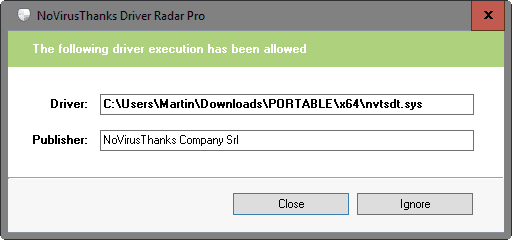
The program itself displays a notification on the desktop whenever it notices a request for kernel mode driver access.
This happens for all requests, even from whitelist programs. The text and color of the notification is different though.
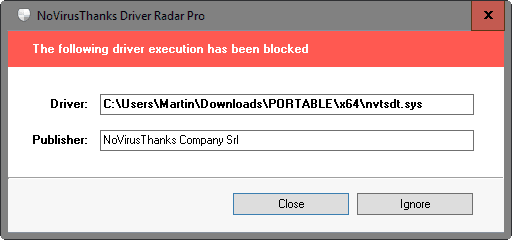
The program offers no option to reload a driver when it is blocked initially. This means that you will have to add it manually to the whitelist which is not as convenient as a button would be to do so right from the prompt.
The ignore button displayed on the prompts add the driver to the list of exclusions. This will only block the notification from being displayed, but won't change the driver's actual state (allowed or blocked).
Settings
You may disable notifications in the program settings, and manage the list of exclusions there as well.
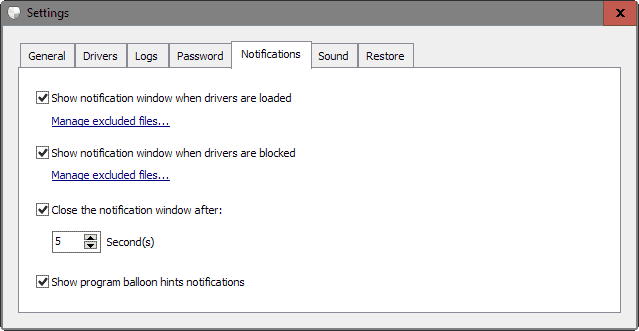
The preferences of Driver Radar Pro are quite extensive. You may disable the program's autostart with Windows there, configure the logging of events, copy drivers to a specific folder, password protect the program, or enable sound notifications.
Main interface
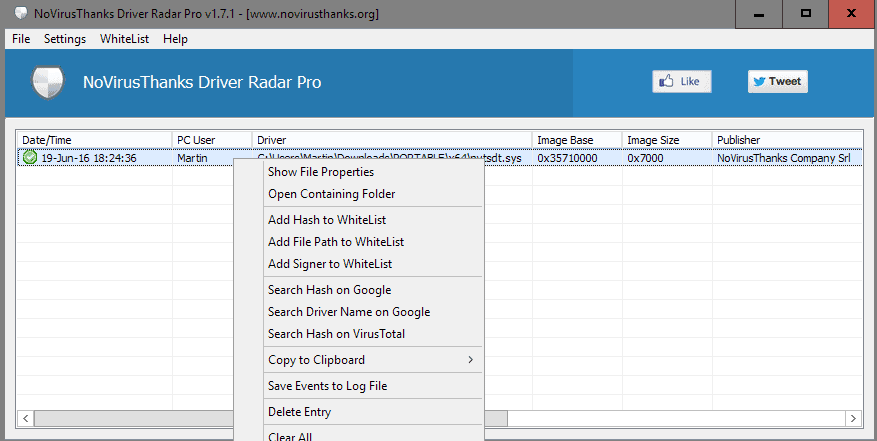
The main program interface lists all events sorted by date. Each event is listed with the date and time, the user account it was executed under, the path and file name of the driver, publisher of the driver, and other information.
Red and green icons in front of each line indicate whether a driver was loaded on the device, or blocked on it instead.
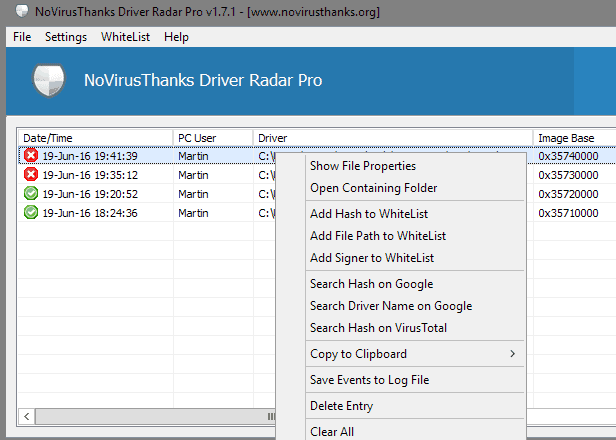
A right-click on a line opens a long list of options. You may run searches for the hash or driver name on Google or VirusTotal, add the hash, file path or signer to the program's whitelist to allow its execution, or open the file properties or the containing folder instead.
Verdict
Driver Radar Pro is a sophisticated program that is easy to use. It adds another layer of protection to Windows by blocking unknown drivers from being loaded with kernel mode privileges.
It ships with a handful of research options to find out more about drivers before deciding whether to add new ones to the whitelist.


























Process Hacker can do the same, inform about started/stopped .exe/.dll/drivers. Other software then a taskmanager is normally not necessary, because Windows protect against unsigned drivers by default. This not adds anything to existent windows mechanism, even if a driver or modul was signed it can be faked anyway, imho it confused the beginner more as it helps because who really knows what is necessary and what not?
On Enterprise versions there is also already AppGuard and even under Home editions an AV already do more or less the same, the thing is none of them really helps if you’re a target. Imo ProcessExplorer or ProcessHacker with EMET/Anti-Exploit is more as enough, because even if a infected file is loaded it can’t touch kernel elements anyway. And to prevent from loading it not really helps, since (as mentioned) signatures can be faked.
Allowed Notification in Green
Blocked Notification in Red
It’s up there.
I was expecting a screenshot of the notification.
There are two, or what do you mean?
Oh OK. I thought those dialogs were settings for notifications. I was expecting more like a balloon or a toast. Also, how much memory does it consume if it runs all the time monitoring for the occasional kernel mode driver install?
Memory use is quite ok, when I checked it used less than 10 Megabyte. May go up though but have not verified that.