Create encrypted mirror copies of folders on Windows
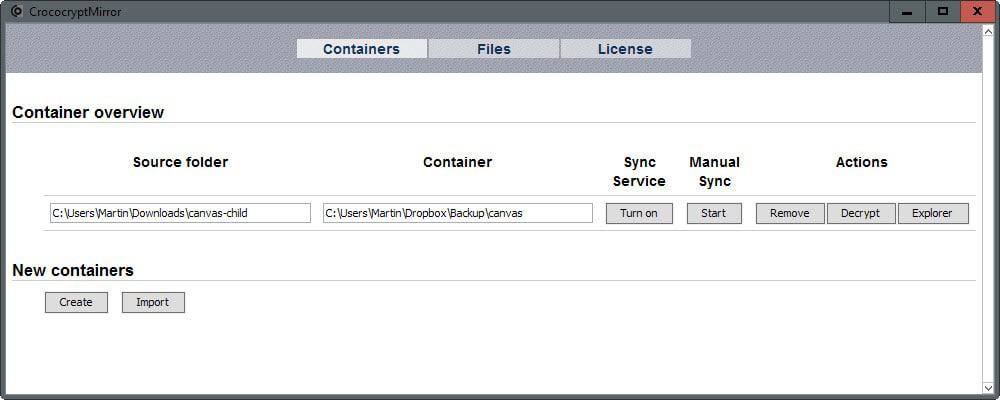
CrococryptMirror is a free program for Windows that you can use to create encrypted mirror copies of folders in Windows. It furthermore allows you to keep the folders in sync automatically if that is required.
Encrypted folders can be useful in several use cases, for instance to park data in the cloud without making it accessible directly to third-parties or to create secure backups to store them remotely or locally.
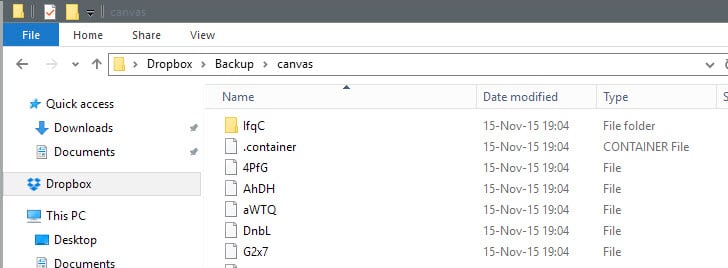
The program creates folder by folder and file by file copies of the data, and encrypts not only contents but also file and folder names.
In addition to that, it uses a headerless design to prevent attackers from identifying the program used to encrypt the data in first place.
Using the program is dead easy. It is provided as a portable version that you can download and run from any location, and as an installer.
You have to select a password on first start and the program will generate keys based on it as well at that time. Please note that the keys are needed to encrypt the data. It is recommended to back them up in safe location.
You may then import existing containers into the program or create new ones. The creation of new containers is simple:
- Select the source folder that contains the data.
- Pick a name for the folder (this is the root folder of the destination, and the only folder that is not named with random characters).
- Select the destination folder.
- Decide whether you want real-time syncing, and if you want the program to start the first copy process right away.
That's all there is to it. CrococryptMirror supports network drives as source and destination folders besides local folder locations.
It may take a moment to encrypt the data on the first run, and you can check that everything is encrypted properly by visiting the selected destination folder.
Synchronization means one-way sync only meaning that the source folder is not modified by the program. The destination folder is kept in sync however if automatic synchronization is enabled, or if manual syncing is triggered.
The program lists a couple of options that are useful besides that. You may turn syncing on or off, or start a manual syncing of the folder instead at any time.
There is also an option to decrypt the folder, to open a special Explorer window with all files decrypted, or to remove it again.
Decryption becomes useful if a folder needs to be decrypted in bulk while Explorer view is useful to restore individual files instead.
The program uses AES and Twofish, and if you are interested in details I suggest you check out the documentation as it is provided there.
Closing Words
CrococryptMirror is a useful program for Windows. It is especially handy for users who want to store data in the cloud but prefer to do so in encrypted form, and for users who want to encrypt data before backing it up.

























CrococryptMirror is very similar to another free program that Martin highlighted some time back: CryptSync https://www.ghacks.net/2013/03/27/cryptsync-upload-only-encrypted-files-to-online-storage-services/
By comparison, that program is open source, uses standard 7-zip compression and encryption, but unfortunately is not portable.
Question: if I set My Documents as ‘source folder’ and [external usb HDD]:\Backup\ as the container, am I not creating an encrypted backup of that folder in my external drive?
Same question goes for [other computer in network]:\Backup\
That’s correct: there’s usually a very thin line between programs labeled as “backup” versus “sync”. The difference is usually either compression or the ability to save multiple versions of one file.
I’m with Nebulus and others. Open Source is the only thing I would trust with anything I put in the cloud. Having said that I have my own DDNS cloud using encrypted RAID1 drives.
I mean Frank no disrespect, but with ANY closed source encryption system there can be no guarantees to security.
Personally, Truecrypt (7.1a) and/or Veracrypt are not that hard to manage Containers. I laud Frank’s attempt to encourage and make it easy for the home user to back-up daily or at least weakly. (Spelling intended) So, for ease of use and the “better than nothing” approach, this sounds like a good enough plan for a lot of people. But, I suspect Martin’s audience is of the more techy nature and therefore more likely to be already backing up regularly.
I’d also like to state that: RAID, any RAID, is NOT backupping. Why? Again, it lacks versioning.
Since BACKUP is mentioned in the article, I’d like to point out the one thing that too many don’t know/understand: syncing is NOT backupping! Versioning is paramount in backups, syncing does not do that.
This is true. But it really depends on the circumstances – if you are talking about enterprise level or home user. I know too many home users who do not backup a thing. I always hope they do at least a one-to-one backup, in these cases that’s an accomplishement…
In general, I’d be very clear whether talking about backupping or mirroring/syncing. Currently there are LOTS and LOTS of people who don’t understand the difference and think that it’s the same thing. It’s not, and the confusion is spread by many internet writers (even with some tech know-how) (Martin, I’m not talking about you). My personal experience (in real-life and net circles I’m active) is that about 6-7 out of 10 people has this thing confused. The amount of confusion really baffles me constantly. People are using various cloud services that do only sync/mirror (or have very limited fail-safes, e.g. versions stored only for x days) and think it’s about backupping. Until human error (deleting files), virus, etc. incident comes up and they are screwed.
Martin, maybe you should do an article about backupping, what it is and what it is not?
Can you elaborate what you mean by “one-to-one backup”?
That’s correct. It becomes backing up again however if you back up the synced encrypted data regularly.
I agree that open-source can enhance the trust in software. However, this is only a necessary and not a sufficient condition for trust. Look at TrueCrypt for instance. Being open-source does not mean that any of what you do is secure.
I tried to point that out in an article a couple of month ago:
http://frankhissen.de/open-source-and-security-why-open-source-is-not-insecure-frank-hissen-it-blog.html
Please note that with CrococryptFile, we offer an open-source encryption tool based on the same technology CMirror is based on. CMirror has a couple of Windows hacks included, we are planning to remove these and make CMirror open-source as well. But this takes time, time requires some money and all this software is free. The common problem of free projects, I guess…
@Martin: Thanks for the nice and fair review. One remark:
“In addition to that, it uses a headerless design to prevent attackers from identifying the program used to encrypt the data in first place.”
This is not correct. There is a headerless mode in CrococryptFile, but CrococryptMirror will always require a header because of the sync/mirroring option. A first glance you might not identify the header, but when you know where to look at, you will identify CrococryptMirror encrypted containers.
> However, this is only a necessary and not a sufficient condition for trust
While true that it doesn’t mean automatic security and requires someone to analyze the code, at least it is possible, as with the TrueCrypt example you mentioned. With closed source software there is no such route. Quoting someone a bit better about security:
“As a cryptography and computer security expert, I have never understood the current fuss about the open source software movement. In the cryptography world, we consider open source necessary for good security; we have for decades.”
Bruce Schneier – http://www.schneier.com/crypto-gram-9909.html
Frank, I agree that open-source is not enough for security, but it is a definite step forward. The lack of it, however raises questions… And for an encryption tool that is freeware, I don’t see a real reason for not being open source as well.
As I said, CMirror contains some (ugly) Windows Hacks. So the reason is simple: Code quality. Again, open-source is planned, lack of time is the reason it’s not ready, yet…
Thanks Frank, I have corrected it in the article.
Encryption tools need to be open source so they can be peer reviewed, else there can be no inherent trust that the application is doing what it claims. It’s pretty much a requirement that the source code be open in order for it to be taken seriously and used in any sort of crucially dependable capacity. I have to agree with other posts here that this is especially true for newcomers to the encryption market, given the state of things these days.
They need to make it open source, otherwise there is no way I would trust them with my files. This is especially true for newcomers in the encryption programs dev world…
This is just as bad as most of the other encryption tools for cloud backup. It will actually create an encrypted copy of your files and thereby waste precious space on your drive. What is really needed is a tool that creates virtual encrypted files that can be backup-ed to your cloud drive. Something like the “Reverse mode” of encFS. For example encfs –reverse provides an encrypted view of an unencrypted folder.