Disguising True Crypt Volumes In MP4 Videos
I have reviewed TCHunt yesterday, a free program to scan a computer system for unmounted True Crypt containers. The program can be used to prove the existence of an encrypted container on a one of the connected storage devices. What it cannot do is to decrypt the data, but proof of existence of an encrypted volume may be enough to get you into troubles.
It was only a matter of time until someone came up with a concept to hide the existence of a True Crypt volume on the computer. A method has been described in detail in February, months before the release of the TCHunt application.
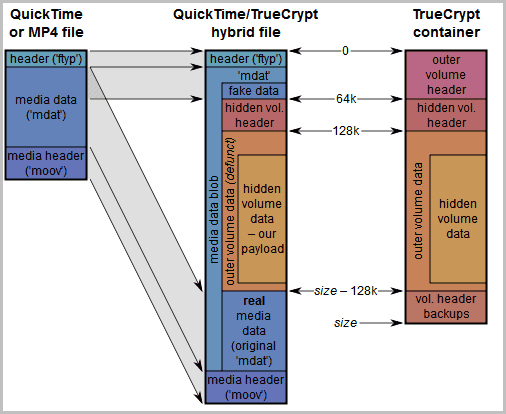
TCSteg basically hides the True Crypt container inside a MP4 video file. Even better, that mp4 video is still playable which makes it more plausible that the file is indeed just a video and not host for an encrypted True Crypt volume.
There are still some limitations though, for instance a limitation to a maximum file size of 4 Gigabytes, or the fact that someone who would monitor the bitrate of the video could identify the manipulation. The method however makes it a less likely that someone will find the hidden True Crypt container on the system, as it renders software such as TCHunt useless.
The method combines the mp4 file with the True Crypt container, or to be more precise, the hidden volume of the True Crypt container. You may remember that you can create a hidden volume inside a True Crypt container for that extra bit of security? Exactly that volume is used for the process, the outer volume will not be used at all.
A Python script has been created that handles all the file merging, you can download it from the developer website. You also need a solid quality mp4 video file that's encoded efficiently to make the combined file size more plausible.
You then create a True Crypt container and a hidden volume and give it a .mp4 name. You should follow the instructions on the developer site to the letter for maximum efficiency, for instance to select a plausible total size for the True Crypt volume and to select the maximum possible size for the hidden volume.
You run the Python script with the following command
python tcsteg.py RealVideo.mp4 TrueCryptContainer.mp4
where RealVideo.mp4 is the mp4 video that you want to use for the disguise, and TrueCryptcontainer.mp4 the encrypted True Crypt container.
Windows users need to first install Python before they can run the Python script.
The process combines the two files, and the end result should be that you can still play the resulting file in a video player and that you can mount the hidden True Crypt volume inside that video.
Additional instructions and the Python script are available at the developer's website.
Advertisement


















i get this error:
python tcsteg.py Snake.mp4 DeadSnake.mp4
SyntaxError: incorrect syntax
(This may be a duplicate: the last one hasn’t appeared)
Your first statement indicates that while TCH won’t produce false negatives (i.e. it won’t miss TC volumes), it may produce false positives (i.e. it may flag files, some or all of which aren’t TC volumes).
So how can TCH *prove* the existence of a TC volume, when some or all of its results may be false positives?
In your own example: https://www.ghacks.net/wp-content/uploads/2011/04/tchunt.png , how can TCH *prove* that one or more of those zip files are, or are not, TC volumes?
Perhaps there are then other tools for, or ways of, examining suspect files to prove if they’re TC volumes, but TCH can’t do so (or if it can, you omitted that capability in your review).
Well what I meant is that it will find all TC volumes on the system. You are right that the tool cannot differentiate between false positives and positives, but you could further analyze the file to find out. That way, you won’t miss a single TC volume on the system.
You can analyze to the ends of time with any software you might wish to employ and all you can do is prove that some file is full of seemingly completely random numbers and may or may not be a truecrypt volume.
Really cool. I like the idea to be always a step ahead or a bit smarter.
Thanks for the follow up.
I already feared that the bad guys win….
Yesterday you said about TCHunt :-
“Not all files that are found are True Crypt containers, but you can be sure that all True Crypt containers stored under the selected root folder are found during the scan.”
And today :-
“I have reviewed TCHunt yesterday, a free program to scan a computer system for unmounted True Crypt containers. The program can be used to prove the existence of an encrypted container on a one of the connected storage devices.”
Those two statements can’t both be true …
What makes you think that?
Indeed something that makes it harder to find the container. Nice tool.