RockYou Hacked. Some 30 million passwords in the wild [Security]
RockYou, a service that offers applications like slideshows, games, layouts and more for social networking sites like Facebook, MySpace or Orkut was recently hacked and the service's entire database of 30+ million data sets exposed to hackers in the process.
This alone would have been problematic but the situation grew worse when it became clear that the passwords were stored in plain text in the databases.
This means that more than 30 million complete sets of emails, usernames and passwords were exposed to third parties. At least one hacker managed to get hold of all the data of which the passwords and a small sample was posted on the Internet.
RockYou users who have an account at the service should immediately change the passwords for all their services that use the password and email address to avoid that these accounts are compromised.
RockYou did not only store login information about its own service but also for third party websites like Facebook or MySpace to make it as easy as possible for users to use the data with their social networking accounts.
This means that MySpace, Bebo or Facbeook login information have also been stored on Rockyou servers if the user has entered them before on their website (see Techcrunch for additional information)
Security company Imperva got hold of the 30+ million passwords that have been selected by RockYou users to secure their accounts. Their findings are alarming:
- About 30% of users chose passwords whose length is equal or below six characters.
- Moreover, almost 60% of users chose their passwords from a limited set of alpha-numeric characters.
- Nearly 50% of users used names, slang words, dictionary words or trivial passwords (consecutive
digits, adjacent keyboard keys, and so on). The most common password among Rockyou.com
account owners is “123456â€.
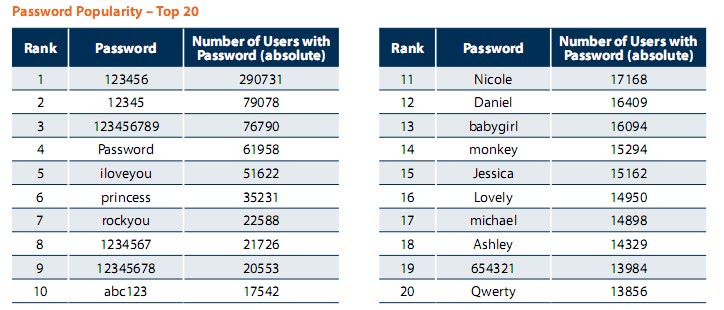
The password popularity chart is therefor dominated by easy to guess passwords just as 123456, Password, rockyou or abc123. The full report of the findings can be downloaded from the Imperva server as a pdf document.
If a hacker would have used the list of the top 5000 passwords as a dictionary for brute force attack on Rockyou. com users, it would take only one attempt (per account) to guess 0.9% of the users passwords or a rate of one success per 111 attempts. Assuming an attacker with a DSL connection of 55KBPS upload rate and that each attempt is 0.5KB in size, it means that the attacker can have 110 attempts per second. At this rate, a hacker will gain access to one new account every second or just less than 17 minutes to compromise 1000 accounts. And the problem is exponential. After the frst wave of attacks, it would only take 116 attempts per account to compromise 5% of the accounts, 683 attempts to compromise 10% of accounts and about 5000 attempts to compromise 20% of accounts.
Recommendations for users
- Choose a strong password for sites you care for the privacy of the information you store. Bruce Schneir’s advice is useful: “take a sentence and turn it into a password. Something like “This little piggy went to market†might become "tlpWENT2m". That nine-character password won't be in anyone's dictionary.â€
- Use a different password for all sites – even for the ones where privacy isn’t an issue. To help remember the passwords, again, following Bruce Schneier’s advice is recommended: “If you can't remember your passwords, write them down and put
the paper in your wallet. But just write the sentence – or better yet – a hint that will help you remember your sentence.†- Never trust a 3rd party with your important passwords (webmail, banking, medical etc.)
The easiest way to ensure all this is to use a password manager that can generate strong passwords and save them for the user. We recommend Last Pass which is available for several popular web browsers.
Advertisement















Hello to all,
pls i want to have a valid links which you can use to get millions of emails.
Thanks and looking forward to your positive reply.
Socor
O yeah. Select strong umpteen letter password, just so it can be lost with 30 milion other passwords. What’s the fucking point.
Fuck me, that’s stupid.
If you require passwords longer than 3 chars, then your system is worthless as it cannot even protect against something so trivial as brute-force attack (hint:real users do not log into their accounts with random password at rate of 10000 attempts per second).
This really isn’t surprising. We’d all be amazed how much this wouldn’t happen if people took the extra .5 seconds to add a number or two to the end of their password. Leave the door open and people will come in. Using passwords like “1234” just isn’t smart.
It is indeed a problem that many face, mainly out of ignorance on how to construct ‘nonsensical’ strings of characters as passwords ‘strong’ enough and yet to remember each one of them. The difficulty gets multiplied when one is required to change passwords often and to use unique, different passwords for each online use.
All there were problems but not any more. Here is a book (probably the only one) titled ‘SPAM 2 SCAM How 2 B e-SAFE’ that shows how this can be accomplished without any additional software. Readers will find some simple yet practical suggestions to fortify their information environment including how to construct strong passwords and remember them easily like their own names. This book also prepares readers to recognise patterns of fraud and thereby helps them not to fall victim to such schemes.
SPAM 2 SCAM How 2 B e-SAFE (ISBN: 1440424616) is available in the USA, Canada and Europe from most conventional distribution (whole sale and retail) channels and e-stores. Please feel free to pass this message around. Together, let us try to save as many vulnerable ‘netizens’ as possible and as quickly as possible.
Thank you.
This news is last year ago. Why post it again?
To me the unbelievable is not the secure bit, since I am guessing the information was stored in a more or less secure place.
The incredible thing is that a site with ANY users at all (let alone 30 million) doesn’t use any password encryption. The first ever php based site I built had password encryption and I didn’t even know what classes where, and I was hazy on what functions were as well!
“…passwords were stored in plain text in the databases…”
WHAT?! I guess I’m lucky not to use any of those sites, but what kind of web developer does this? Will this have legal consequences? Are there any laws which state you have to keep your users private information at a secure location?
Unbelievable!