CryptoPrevent 8: Windows malware prevention software
CryptoPrevent 8 is the latest version of the popular malware prevention software for devices running Microsoft's Windows operating system.
Windows users have quite the diverse selection of security tools at their disposal. Even if you ignore the options that Windows itself ships with, there is a variety of tools that users can install to improve their system's protection against malware threats.
CryptoPrevent falls into the supplemental category, meaning that it adds to the protection but should be used next to resident antivirus software or other protections.
We mentioned the first version of the program back in 2013 when first ransomware threats started to pick up pace.
CryptoPrevent 8
The program has come a long way since the release of its first version back in 2013. The program relies heavily on Software Restriction Policies to block malware attacks. The most recent version of CryptoPrevent ships with about 4000 rules, which is ten times the number that version 7 of the program shipped with.
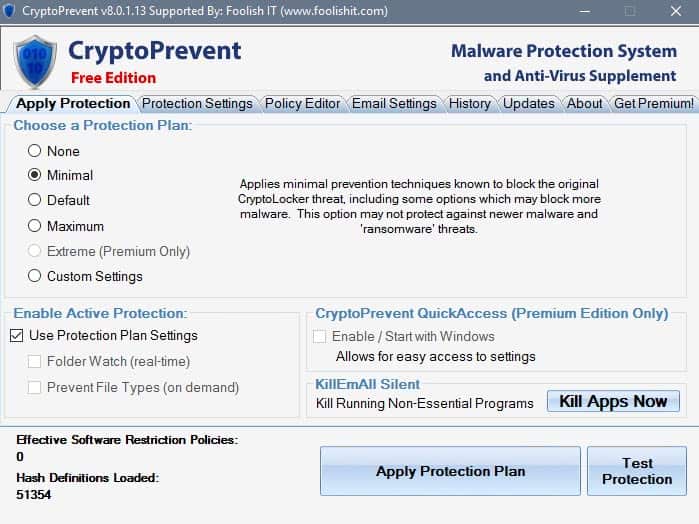
The program is relatively easy to use on first glance. The first screen that it displays prompts you to pick a protection plan. This plan determines the protection level, and goes from none at all to maximum in the free version. There is also an extreme setting that is only available for premium users, and an option to pick custom settings.
If you are unsure what to pick here, you may want to start with the default level as it is the recommended protection level.
The Protection Settings tab lists some of the protective measures that CryptoPrevent 8 will apply to the system when plans are selected.
It lists the protected areas --- the %appdata% folder for instance --, whether program naming exploits are blocked (using double file extensions for instance), and whether certain Windows programs or features are blocked as well.
The default plan makes the following security changes:
- Protects %programdata%, %userprofile%, and startup folders in the Start menu.
- Blocks vssadmin.exe, syskey.exe and cipher.exe.
- Prevents known malware from starting.
- Turns off Windows sidebar and gadgets.
Other options that the program may enable are to block file types that are often used by malware (.scr, .pif or cpl), and to watch certain folders and block programs that show malware traits.
The Policy Editor tab is quite useful, as it lists all whitelisted and blacklisted files and folders. You can check the Software Restriction Policies folders there for instance by opening the blacklist, or add folders or files to the whitelist to allow their execution.
Options are included to remove selected folders from the blacklist. This is useful in particular if you run into execution issues on the system after enabling one of CryptoPrevents plans.
One of the issues that I had personally with earlier program versions of CryptoPrevent was that it did not really reveal what it was doing, and that you had even less control over the functionality.
A CryptoPrevent monitoring service runs in the background after you apply a protection plan to the device. You can undo changes at any time by loading the program again. I suggest you set the protections to none before you uninstall the program on a device just to be on the safe side.
Closing Words
CryptoPrevent 8 improves the protection of a device running Windows through the use of software restriction policies, malware definitions, and other means. It is not designed to run as the only security program on a Windows machine, but may complement existing security programs without interfering with them.
Now You: Do you run supplemental security applications on your system?


























It’s crap… https://www.pcmag.com/review/353931/cryptoprevent-premium-8
Kz from Belgium
No-one really knows if it is good or not.
In the below review, CryptoPrevent has been reviewed as “Dismal” and not worth the hassle of installing: https://www.pcmag.com/review/353931/cryptoprevent-premium-8
In another PC magazine, it also mentioned users whose computers / laptops have crashed, froze and the fact that CryptoPrevent is difficult uninstall.
It’s really up to the user in general. Is it worth the hassle? Do you “feel” safer with CryptoPrevent installed? Does your machine still work as normal?
Not getting viruses / malware / ransomware means a lot of common sense being used, like not clicking on and opening that spam / unknown email, not downloading or opening strange email attachments, not clicking on links in strange / unknown emails, being wearey of going to strange websites, especially in a language you cannot read, and having a good ad-blocker.
I just recently discovered this product and just today upgraded to v 8.0.4.0 free. I (basically) understand the ‘gadget’ issue … they being insecure … supposedly. I am not a security expert, .. but there were a couple of (actually only 1) gadget(s) I am very fond of.
So .. here is the question …. is ONE gadget just as risky as several? Are some risky and some are not? If I were to properly assume my favorite is safe … how can I white list it with this version?
The primary question is can I white list … the secondary question is ‘are all gadgets risky?”
For what it’s worth, I have recently been told by a (supposedly) white hat hacker that Windows is so full of holes that typical antivirus/antimalware products are useless, that Windows has 300+ back door vulnerabilities, Linux maybe 2-3. His advice was “there is no way to make Windows secure. It is hopeless. Ya want security, go to Linux”. Sooo, in THAT sense, it seems it doesn’t really matter if one runs gadgets or not.
I would just LIKE to have my one gadget back. Comments are welcome. Thanx.
Thanks for you reply, it’s a shame that developers of programs such as Resilio Sync, Skype, Spotify, What’s App, Wire, Avira Scout, etc., etc. feel the need to install to these non-standard locations but nothing to do but accept it then.
Have I missed something? Version 8 now restricts custom Whitelist/Blacklist Policies to the premium version only, whereas the Software Restriction Policy Editor was free and open in version 7.4.21.0?
Culverton, the Software Restriction Policy Editor is available for usage in the free version, the only premium restricted ability there is to add your own custom blacklist policies. You are free to add/remove whitelist policies and remove blacklist policies as you see fit.
Normally those programs are trying to install user specific applications and make it the easiest for people to get those programs installed. It’s not what we would recommend as there are a number of ways to program user specific applications without using those locations for your program files themselves. The locations are normally “application data”, which is what those folder should be used for (data from the application) and not to circumvent the program files file permission restrictions Windows has put in place by default. Essentially those programs are trying to make it so non-admin users can install their programs and it’s basically circumventing protections that are there for good reason.
As far as dealing with them you can whitelist them in CryptoPrevent to allow them to run using the “Whitelist applications in all blocked location” button, but I would still highly recommend researching everything that gets whitelisted and removing ones you may not actually want to run. It’s unlikely that they would allow you to choose the path to install, but if they do I don’t see any reason why you wouldn’t be allowed install/run those applications from there. You may end up having to make changes to the folder permissions specific folder where you end up having them installed to, but shouldn’t be that big of an issue overall.
Thanks Brantley, I obviously didn’t look at things properly, sorry.
Do you know, I have about 20 bonafide programs that run themselves from within one of the protected locations – Resilio Sync, Skype, Spotify, What’s App, Wire, Avira Scout, etc., etc.
I’d be interested to understand why so many program developers and now setting their .exe locations to folders that are usually protected by anti-exploit programs such as CryptoPrevent and to know whether I could have installed any of these programs in the Program Files folder without problems?
What do you think?
I wish there was a way to completely disable encryption of files within Windows, although I don’t know if that is even theoretically possible. The customers that come in my shop with malware/ransomware will never have a legitimate use for it and if there was a way for windows to monitor the file system and abort any process that attempts to encrypt files it would save a lot of people.
Lucas, the FolderWatch HoneyPot Detection feature (premium only) does exactly that! You can add custom folders you want to have monitored for encryption attacks and it will kill all processes on that system and prompt to shutdown to have the system cleaned. You can see this feature demonstrated in our youtube playlist here:
https://www.youtube.com/playlist?list=PLRH8ZC4G_wWF14FQlR2_XAkTMYn4QWYTF
Once ransomware has gotten past all the layers of security it is meant as a last line of defense. In our testing it works fairly well with normally only the honeypot files getting encrypted, but there are various styles and speed of encryption with ransomware so it may get some legitimate user files. If this gets triggered and the data is important to the user, shutting down and having the system cleaned in an offline state (attaching drive to another system or using a boot environment) is the only real way to ensure you can regain access to those files or clean the system without the possibility of further encryption occurring.
The best way to avoid having to worry about ransomware entirely is a well planned and executed backup routine. Our philosophy has always been if something is important to you it should be in more than two locations.
I run Comodo D+ as a HIPS.
Basically it will (should) prevent anything from running or accessing certain folders/regkeys or memoryinjection and so on.
That is a perfectly measured response from a vendor to a criticism. It is good to see a vendor defend their position rather than treat posters as shrills.
I used this program on PCs not long after it was first introduced – as a layered security approach. I agree with Martin, I really was not sure if it was actually doing anything meaningful. Unfortunately, it messed with my backups with the highest level of protection enabled. I wanted to just temporarily disable it before I ran a backup or before I installed a new software package, but it was not easily done. I eventually uninstalled it.
When they announced Vers 8, I decided to give them another try using the default setting. It has not interfered with my backups or interfered with the installation of new software either.
I am mostly concerned right now with the different approaches ransomware infects systems. The bad guys have already proven that they can hit the firmware in PCs and bricked them permanently. In a small business this can be death by a thousand cuts.
LD, I haven’t seen many malware applications hit the firmware (unless they are pre-loaded by the OEM :/), but there are some very active ones that hit the Master Boot Record of the harddrive. For that type of protection there is a great opensource program called MBRFilter available. Martin did a review on it previously here:
https://www.ghacks.net/2016/10/21/mbrfilter-protects-the-master-boot-record-against-manipulation/
Past that, the layered security approach is your best methodology. Including items like user education, backup routines, appropriate permissions layering on the network and system level, active & up to date antivirus/anti-malware, firewalls on the system and network layer, as well as the use of CryptoPrevent can all add up to a very good defense against the various malware out there. Nothing will ever be 100% effective, but you can mitigate downtime and loss by staying vigilant.
CryptoPrevent by foolishit.com- has anyone really looked at the name ? ……fooliSHIT coul’d be an omen…. !
We actually have a quote from our Founder/CEO Nick Shaw on that specific topic on our About page (accessible on our site by searching for “About”):
“Some years ago, I decided to register “foolishtech.com†to start a blog for voicing some common issues and resolutions I had experienced in my years as a PC repair technician. Scrolling down the page to confirm my site purchase I saw “foolishit.com†in the registrar’s suggestion box of similar names, and I couldn’t stop laughing, I had to have it!
We realize that “FoolishIT.com†doesn’t make for a great domain name. In addition to other various issues, the major roadblocks early on were being unable get a Microsoft Application ID, and for years we couldn’t get this domain on Google Apps, all due to the last 4 characters of the 9 character domain name. It seems some automated algorithms think it’s profane! Regardless, Foolish IT is now a long established entity thanks in part to our CryptoPrevent malware prevention software, it would be FOOLISH to change the name now!”
@Brantley Strickland (Foolish IT), thanks for these explanations. It appears that only the Maximum and high plans (in which blocking of BCDEDIT.EXE is included) could be problematic given the software run by the user, that a simple switch in CryptoPrevent enables/disables a given blocking (with a nevertheless advised reboot).
Blocking SYSKEY.EXE, CIPHER.EXE, and VSSADMIN.EXE, all three in the default plan, is less likely to be problematic (hence in the default plan). I note the links you provide.
Now I know better. In case of any further questions I’ll contact the Support page of FoolishIT.com.
Hey Tom (for some reason couldn’t reply directly to you),
All four of those EXEs could be blocked and are blocked through the various plans in CryptoPrevent. However, one of the great thing about CryptoPrevent is you can enable/disable particular protections fairly easily (either through the Policy Editor as Martin pointed out, or through the Protection Settings tabs). For those particular blocks, it’s adding Software Restriction Policies in Windows so if you make changes to those to ensure they have taken place you will want to reboot (they would eventually apply on their own, but gpupdate is a bit strange on when it chooses to perform it’s tasks; where reboot would ensure it process any changes that have been made)
As for each of those programs, the Default plan will have SYSKEY.EXE, CIPHER.EXE, and VSSADMIN.EXE blocked. We’ve seen little to no “legitimate” usage outside of some specific case administrative tasks to use SYSKEY.EXE or CIPHER.EXE. Those should normally be fine being blocked in most all cases (syskey has recently been making a comeback in tech scam calls to lock the target out of their computer).
You can find more about the legitimate uses of those with these pages:
SYSKEY.EXE – https://support.microsoft.com/en-us/kb/310105
CIPHER.EXE – https://technet.microsoft.com/en-us/library/bb490878.aspx
VSSADMIN.EXE and BCDEDIT.EXE can be, and regularly are, used in more legitimate ways. Normally, VSSADMIN.EXE has a more specific case usage, but is also heavily used by ransomware to remove backup copies of targeted files – which is why it is included in the Default Plan protections. The most commonly used program we’ve come across is ShadowExplorer (great program), which makes it easy to browse the various backup versions. Generally, that is used in a specific case scenario, where disabling that protection and rebooting would not be too detrimental to accomplishing your goal. BCDEDIT.EXE is different, that is why it’s included in the Maximum and high plans. BCDEDIT.EXE is used by some backup utilities (when performing system image creation), remote access tool (when rebooting into safe mode w/ networking) and many other legitimate programs. At the same time it can be used maliciously to prevent access to booting the system. It’s fairly rare that ransomware will take this course of action, but it’s included because it has been done before. Disabling this protection can be done on a case by case basis; or left disabled depending on the software you use normally, without much fear of malicious intent.
You can find more about the legitimate uses of those with these pages:
VSSADMIN.EXE – https://technet.microsoft.com/en-us/library/cc754968(v=ws.11).aspx
BCDEDIT.EXE – https://msdn.microsoft.com/en-us/windows/hardware/commercialize/manufacture/desktop/bcdedit-command-line-options
Furthermore, the Maximum and higher plans can also cause some programs to have issues with installation and updating. This is mainly due to the “%localappdata%\*” and “blocking executables from temporarily extracted archives” protections. %localappdata%\* will block the user’s %temp% folder, where some programs will extract to the root of and execute from there to perform their install/update tasks. Similarly with the executables temporarily extracted from archives, however, more people seem to have trouble when they open a executable and then want to double click an executable from directly within the archive instead of extracting and then executing.
For any of the protections in the Maximum or higher protection plans, when you come to these specific tasks, you can lower the protection settings or disable the particular ones prior to performing these operations; and then re-enable them after you have completed. Just note that it will normally require a reboot to ensure you see the desired effects when removing or adding protections.
Hope that helps some and always feel free to reach out to our support staff through our various means described here: https://www.foolishit.com/support/ if you ever have any questions or would like recommendations. We even have a live stream (details on that support page) every weekday where you can chat directly with us directly and get demos/examples and discussions.
There’s worse : http://hpics.li/cfe8986
Funny anecdote. Choosing such a domain name with “FoolishIT.com†in mind and keeping it with a perceived “Foolishit.com†signs a most valuable sens of humor. Unfortunately as always, and whatever the quality of the site/blog/software, it will always be that some opponents grab a funny name as an argument for condemning an application. That’s life :)
More seriously I read in the article here that CryptoPrevent’s default plan “blocks vssadmin.exe, syskey.exe and cipher.exe”. I read elwewhare (I believe on FoolishIT itself) that,
“This option prevents SYSKEY.EXE, CIPHER.EXE, BCDEDIT.EXE, and VSSADMIN.EXE from running (in any location,) as it is being exploited by recent malware. NOTE: any software requiring an automated special reboot sequence (e.g. booting AUTOMATICALLY into safe mode, recovery mode, a recovery partition, etc. etc.) may fail with this protection option enabled!”
Would you be as so kind, Brantley, to confirm if the four above EXEs are blocked, or are they less or more to be blocked?
For the time being I’ve searched info about vssadmin.exe and found several sites advising to disable it. I haven’t searched for info regarding the three other EXEs mentioned above, but I did do the following as for other EXEs already concerned in order to order Win7 to not tun those files :
In the Reg under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun I’ve added “10”=”vssadmin.exe” (already 9 other String values in the list). Also, since my system backupper is AOMEI I’ve changed its setting regarding VSS so that AOMEI uses its “built-in technique to backup without interrupting” rather than Microsoft’s VSS….
If I detail all this it is to come up to asking you if, for the EXEs CryptoPrevent blocks what are the implications, what should the user be aware of?
Thanks :)
Thanks for the review of CryptoPrevent!
We actually discussed RanSim on our show last Friday 1601-06. Long story short, the company KnowBe4 seems to be focused on what we (Foolish IT) believe is one of the most important aspects of security layering “User Education”, however their tests are non-malicious and do not behave like any other ransomware or malware we’ve come across in our testing. We could focus on blocking and passing those tests specifically but honestly it won’t be providing any additional security overall for your systems in general. We have a number of other features and functionality we are currently implementing that will provide additional security to the system overall, so our focus on passing those tests will be low on our list of things to do.
Testing anything with RanSim will fail or give inadequate results.
Tried cryptoprevent 8 a few days ago and tested it using RanSim, failed all 10 tests…
https://www.ghacks.net/2016/12/28/ransim-test-ransomware-attacks-windows-pc/
RanSim is total shit! CryptoPrevent ftw
RanSim test failed by design.
It only check for read+write rights in the folder RanSim start.
Of course the folder need read rights, other the programm cant start.
So if you block that stuff, then your safe. This programm doesnt test this well.
RanSim is total crapware IMO.
I think that RanSim’s tests only work with certain protective measures, but ignore others completely due to the way they are designed.
foolishit.com
mouhaha
Speak English, you sorry Bast^%.
it’s foolish IT, snowflake!
this guy knows his stuff and responds to any and all support q’s.
you’re welcome.
shouldn’t you be in school at this time of the day?
i see what you did there, being first is very important to you, eh?
Read below from Brantley Strickland (Foolish IT) “…and I couldn’t stop laughing”.
What is going wrong when you try to laugh Elliot hum?