Security Issues in Malwarebytes Anti-Malware disclosed
A recently disclosed vulnerability in Malwarebytes Anti-Malware (free, premium and enterprise) allows attackers to run man in the middle attacks against systems running the software.
Malwarebytes Anti-Malware is a popular second-opinion scanner, and the premium and enterprise editions of the program add real-time protection among other things to it which bring it more in line with traditional antivirus solutions.
The program is held in high regard by many for its malware detection and cleaning capabilities.
Google researcher Tavis Ormandy alerted Malwarebytes in early November 2015 to several security vulnerabilities that he found in Malwarebytes Anti-Malware.

Malwarebytes managed to patch several of these vulnerabilities server-side "within days", and is testing a new version of the client software internally which it plans to release in the next three to four weeks that patch the issue on the client side as well.
Ormandy discovered that the software fetches signature updates over http. While the data is encrypted, he discovered that it is easy enough for anyone to decrypt it using OpenSSL commands.
MalwareBytes fetches their signature updates over HTTP, permitting a man in the middle attack. The protocol involves downloading YAML files over HTTP for each update from http://data-cdn.mbamupdates.com. Although the YAML files include an MD5 checksum, as it's served over HTTP and not signed, an attacker can simply replace it.
Attackers have various options at their disposal to exploit the issue.
There are numerous simple ways to turn this into code execution, such as specifying a target file in the network configuration, writing a new TXTREPLACE rule to modify configuration files, or modifying a Registry Key with a REPLACE rule.
Malwarebytes confirmed the vulnerability publicly in a recent blog post revealing that it is working on a fix. The company announced the launch of the Malwarebytes Bug Bounty program offering cash bug bounties of up to $1000 for reported issues in the application.
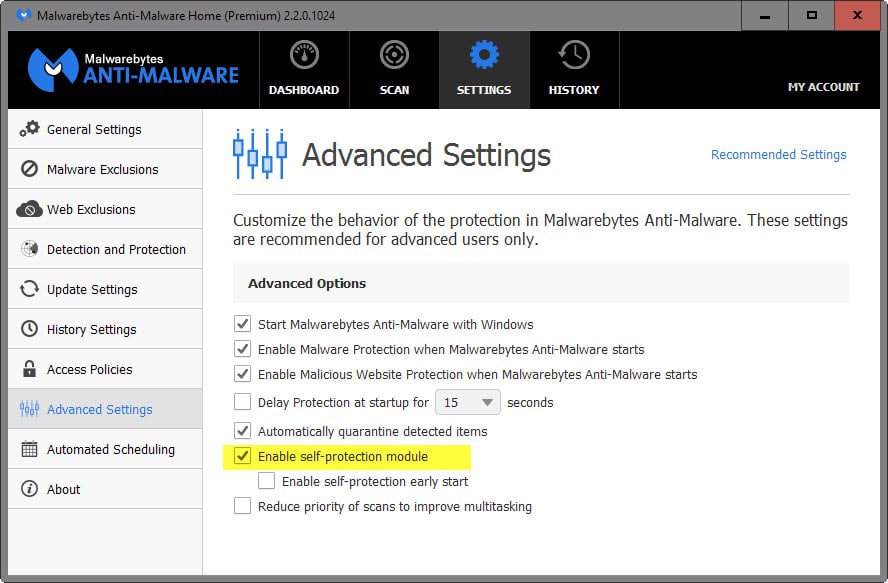
Users who run the premium or enterprise version of the application can protect it by enabling the built-in self-protect module:
- Right-click on the Malwarebytes Anti-Malware icon in the system tray and select the open option from it.
- Switch to Settings > Advanced Settings.
- Check "Enable self-protection module" if it is not enabled already.
Google's Project Zero initiative revealed vulnerabilities in products by security companies such as AVG, Kaspersky, Sophos and TrendMicro in the past.


















What on earth has self protection got to do with signature downloads being susceptible to man in the middle or similar?
Anyway I find MBAM makes my system unstable if I enable self protection.
I use this software since 2006 and have bought a license in 2008. I have been lucky enough to buy this license at a time it was a lifetime license.
This software didn’t ever let me down and it is really a very good complementary security layer to any anti-virus.
I agree. This is best anti-malware program irrespective of what others say or write.
Wait until you see it pass a system as clean when it’s obvious it’s not. Then you’ll change your tune.
Just like AVG used to be the best free antivirus. Then it became bloated and possessive, and a lot of people avoid it now.
Blind faith in something being the absolute best regardless of any proof contrary is how you get screwed. I thought it was the best antimalware program, too. Until I saw it happily pass some very common malware, including a couple well-known toolbars, that I could verify with my own eyes that infected my friend’s system. And that was with an up-to-date version, with updates signatures.
But if you want to put your money where your mouth is, set up a test system, then run it thru a gamut of malware. Find as many programs that you can that use adware and spyware. Leave all the checkboxes checked. Go down the top 20 most-popular programs on download.com and use their installer. Then use Malwarebytes to scan and see what it gets. Then use the program I mentioned, and see what else it finds.
I’ll never trust Malwarebytes totally again. It ONLY gets used in conjunction with the other program I found.
I lost a crapton of respect for Malwarebytes when I saw it pass a friend’s system, twice, as being completely clear, when it was obvious even from opening a browser it was heavily infected.
Ended up trying a malware scanner called SuperAntiSpyware (I’m not affiliated) and it found 19 infections Malwarebytes missed. Some of them common spyware toolbars.
I no longer recommend Malwarebytes to people I know, and have relegated it to a second-choice when doing scans.
Here’s my “way out there” theory … MBAM is secretly working with this Google Researcher and by convincing users that there is an disclosed vulnerability, many users would jump on the “Enable Self-Protection Module.” What is actually does is reveal your Key & ID to MBAM and based on the shear massive numbers can then blacklist those key and IDs being used by pirated, non-legal users.
Hi Martin :)
Does this affect the older version 1.75.0.1300?
Seems that Google’s security researchers start testing popular security programs in the industry, e.g., Chromodo, AVG Web TuneUp, TrendMicro’s PW manager. Or, Google has its own beta build of Anti-Virus or Anti-malware program under production soon to be available. LOL
Even if they create their own AV, it’ll be a spyware, tracking, no-privacy[in reality], stealing identity and many more.
I think the same.
But how often do man in the middle attacks actually happen? Is this particular attack a red herring in most cases?
Thanks for the information, Martin.
I’ve been using MBAM for 3 years and i’ve always enabled self protection. This is the first time that there has been a warning about a vulnerability problem with MBAM. Let’s hope the fix is released asap.
“This is the first time that there has been a warning about a vulnerability problem with MBAM”
It’s probably also the first time an independent researcher has audited the MBAM code. Coincidence?
When you think about it, it’s amazing how much trust we all put in developers to build high quality, trouble-free software. This particular vulnerability seems to be rather sloppy. Downloading malware signatures over HTTP? Really? Wow. You’d think this would be one of the first things the designers of an anti-malware program would be careful not to do.
This, ladies and gentlemen, is why I favour open-source and hate DRM. The more impediments to third parties viewing and manipulating the code, the more chances for security flaws to get swept under the rug (only for some well funded spy agency to find them years before the rest of us know any better…)
Open Source also means flaws are easily found and exploited well before other people notice them and/or patched them and then release said patch for that masses. I mean, it’s not like Heartbleed vulnerability or Shellshock exploit came from Open Source and the vulnerability existed for years before….oh wait….
In truth, there is no perfect system. Open Source has a potential to be better but that is if everyone who actually views it, can understand it all and spot problems. Most people can’t spot the problems but know how to compile it (thanks to tutorials).
“Users who run the premium or enterprise version of the application can protect it by…”
Does this mean people who use the free version are vulnerable and the company intends to leave it that way?
No, the self-protection module is just a mitigation option. Malwarebytes plans to fix the issue in the software for all of its users.
Thanks for the clarification Martin =)
Malwarebytes app[iOS/Android] affected or not? If so, workarounds or patch duration?
It is unclear whether other Malwarebytes products are affected as well.