Privdog is Superfish all over again
Privdog is a privacy protection software that is available as a standalone product for the Google Chrome Microsoft Internet Explorer and Mozilla Firefox web browser and bundled with select Comodo products including Comodo Dragon and Internet Security.
According to Comodo's website it ships with the company's Internet browser and Internet Security products. The company did not bundle the standalone version of PrivDog with its products though.
A user on Hacker News noted that the Superfish test would return a hit even though Superfish itself was not installed on the system. After some analysis it appeared that the privacy software Privdog was the culprit in this case.
Note: I installed the latest version of Comodo Dragon on a test system and it shipped with Privdog. It did not install a root certificate on the other hand.
Privdog has been designed to block certain trackers and advertisement from showing up while you browse the Internet. It blocks all advertisement that is not hosted directly on the domain you are visiting and replaces it with AdTrustMedia advertisement.
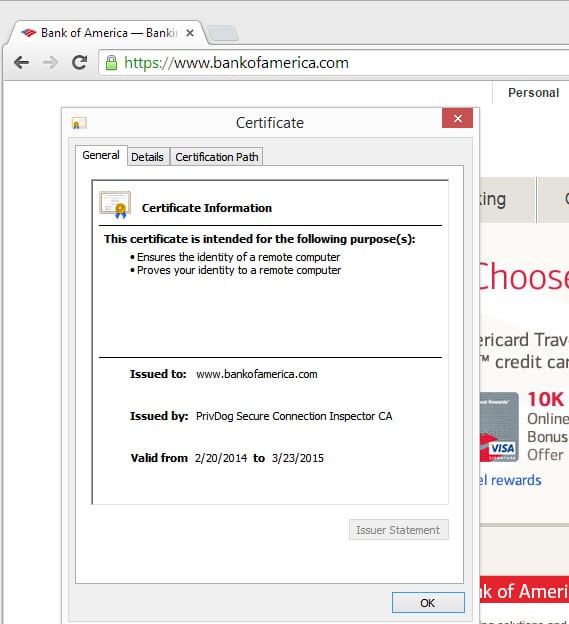
What's worse however is the fact that it installs a certificate on the system as well. While it does not share the same key on all installations, it has an arguably even bigger flaw than that: it intercepts all certificates and replaces them with one signed by its own root key.
All in this regard means valid and invalid certificates which in turn means that the browser you are using accepts any certificate regardless of whether it is valid or not.
That's bad on many levels and means basically that you are not secure while Privdog's certificate is installed on the system.
It is therefore highly suggested to remove the software from the system and make sure that its root certificate is gone too after the removal. If it is not, you need to remove it manually from your system which you can do in the following way:
- Tap on the Windows-key, type mmc.exe and hit enter.
- Go to File -> Add/Remove Snap-in
- Pick Certificates, click Add
- Pick Computer Account, click Next
- Pick Local Computer, click Finish
- Click OK
- Look under Trusted Root Certification Authorities -> Certificates
In case you are wondering what the connection between Comodo and PrivDog is: the CEO and founder of Comodo seems to be behind Privdog as well.
So why is this Superfish all over again? Both products add a root certificate to the user's computer and both make the user's computer insecure in the process and are used to earn revenue for the parent company. While they don't work the same, Privdog is arguably worse in terms of security than Superfish, they have been designed for the same purpose.

















Per the article below, the certificate replacement only occurred in the recently released stand-alone version of Comodo’s PrivDog. This does not happen in the browser extension in Comodo Dragon.
However, I have removed the PrivDog browser extension from Comodo Dragon anyway. I have AdBlock Plus installed, so why do I need PrivDog anyway?
—————–
SSL-busting adware: US cyber-plod open fire on Comodo’s PrivDog
Superfish sequel: I’m looking at the man in the middle
24 Feb 2015 at 11:01, John Leyden
http://www.theregister.co.uk/2015/02/24/comodo_ssl_privdog/
Apparently I don’t have Privdog’s certificate installed on the system and did a check from the link in the comment selection returns clean with Mozilla Firefox.
Martin can you take the Untrusted certificate and moved them to Trusted Root?
Example login.live.com certificate or is that how it even works, this was kinda where I left off with the operating system years ago before I lost my mind with the machines. Pure Administration tasks that took extreme testing and tweaking. Nonetheless thanks for the information on Privdog’s certificate.
Thanks for the Article Martin
Here’s a handy online tool that will check if your vulnerable to these recent blunders.
https://filippo.io/Badfish/
Got tired of CIS and all the problems with it recently. Like blocking Xbox. Switched to Windows Firewall Control from BiniSoft.
SSL-busting code that threatened Lenovo users found in a dozen more apps
“What all these applications have in common is that they make people less secure.”
by Dan Goodin – Feb 22, 2015 12:45pm PST
http://arstechnica.com/security/2015/02/ssl-busting-code-that-threatened-lenovo-users-found-in-a-dozen-more-apps/
Using any Comodo product is a major security risk, I would never touch a program that comes from companies like Comodo and IObit for example.
The Comodo forum discussion link on this has changed to:
https://forums.comodo.com/general-security-questions-and-comments/komodia-superfish-vulnerability-ssl-hijacker-merged-t109881.0.html
Here is the advisory from the privdog team.
http://privdog.com/advisory.html
—
Still cause for worry?
I tried Chromodo which is bee to run the Virtual Desktop (SandBox) of the Comodo security Suite.
https://www.Comodo.com/home/browsers-toolbars/chromium-secure-Internet-browser.php?key5sk0=2128&key5sk1=ffc9a67f43de786eabbabf8e05b7f5edc74bc614
If one removes the embedded privatdog extension and after the certificate, simply restart the browser and the certificate reappears
I use CIS, but during the installation of the suite, I decline the Privatdog installation that is not installed on the PC. So it is the browser itself which installs the certificate…
I did not find a Privdog cert on my machine. But there are plenty of Comodo certs. Some ar elikely added by their firewall but Comodo is considered a “trusted publisher” and I think Microsoft also adds [at least] their root cert on any Windows build.
No.
If I delete the certificate, it disappears.
If I do not run the browser integrated into the virtual desktop (Chromodo), the certificate is not in the list.
If I run the built-in browser, as soon as the certificate reappears in the list.
During the installation of the Firewall, I refuse Privatdog, it is just the launch of the browser that creates the certificate. (even if it deletes its extension)
Additional actual and potential vulnerabilities are described here – it’s not just Lenovo.
http://www.reuters.com/article/2015/02/20/us-lenovo-cybersecurity-dhs-idUSKBN0LO21U20150220?wpmm=1&wpisrc=nl_board
OK, so Comodo & Lenovo just earned a permanent slot on the consumer blacklist– do not use/buy any of their stuff. They can not be trusted. The US military banned Lenovo products about two years ago for that reason
Sony BMG earned the blacklist ten years ago with their CD DRM rootkit scheme. The temptation to go-rogue must be very strong even for nominally reputable companies. They calculate that extra profits will outweigh the risk of discovery of their schemes… and there are always more tricks to try if they get caught. Consumer boycott of all their products is the effective way to react.
Bauerston …yes, i agree…i added lg to that list as it seemed they started that “phone home” deal.
Perhaps it’s appropriate in their Feedback to tell them of additional exposures or information.
https://www.us-cert.gov/ncas/alerts/TA15-051A
For those who are interested, over at How-to-Geek, Lowell Heddings has posted a similar article today about this topic:
**Don’t use Comodo, Their Crapware Completely Breaks the Fundamental Security of the Web!
Windows**
https://discuss.howtogeek.com/t/dont-use-comodo-their-crapware-completely-breaks-the-fundamental-security-of-the-web/25410
Just for the record, it’s much easier to just:
– click Start (or tap the Windows key on a keyboard)
– type certmgr.msc (and press Enter) to get the Certificate Manager
thanks broadband…so easy
An article about Superfish said certmgr.msc displays certificates at the user level and the Superfish certificate is installed at the computer level; thus Martin’s procedure to display the computer-level certificates.
I have CIS installed and I can’t find the privdog certificates even after following your advices.
hey martin, can you check adguard for windows desktop too?
I’m using it & to me it seems, that it works in a similar manner to this: http://i.imgur.com/99uI51C.png
Did you run it against the Superfish test site?
https://filippo.io/Badfish/
acc to that site, my system seems ok?
result: https://filippo.io/Badfish/no2.png
Also no other SSL-disabling product was detected on your system.
but i still have adguard cert. on all https websites, maybe this is the way they provide adblocking on https sites?
guess i should ask the developer
Dany, that was my first thought as well. Maybe it is using the cert to protect you own https pages as well. I do think it is best to ask the developers to see what they have to say about it. I just checked the homepage briefly but could not find many information about the implementation on it.
Privdog, but not only. Self-signed certificates on the go, using evil to combat evil …
“Two more software makers have been caught adding dangerous, Superfish-style man-in-the-middle code to the applications they publish. The development is significant because it involves AV company Lavasoft and Comodo, a company that issues roughly one-third of the Internet’s Transport Layer Security certificates, making it the world’s biggest certificate authority.”
Now Lavasoft (I mean Lavasoft itself! using Komodia which self-signed its certificate in the same way as SuperFish and Privdog) is concerned with its Ad-aware Web Companion …
This is the end or the beginning, my friend?
Forgot to include the link of the quote’s source :
arstechnica.com / security / 2015 / 02 / security-software-found-using-superfish-style-code-as-attacks-get-simpler/
And the beat goes on. Lenovo & Superfish, Comodo & Privdog, what next (to be discovered)?
How can certificates be issued so easily? I ignore everything of the mechanism but at the end, that is at the user’s start : who, what to trust? Is the Internet becoming a no man’s land?
I am not surprised considering the shady nature of their CEO..
I used their firewall in the past not a bad product, but unnecessary for me today on systems newer than XP.
I used to use Comodo HIPS, then it turned to shit with a large update (version 6 if I recall)
Using Online Armor now, it’s free, and so far I’ve found it more powerful than Comodo HIPS was even.
Don’t kid yourself though that you’re secure without a HIPS defense just because you’re no longer on XP. Since I’ve started using HIPS, I won’t go back to computing without.
I have been using Armor Online for a long time and I love it . . . ’cause it works and it’s F-R-E-E!
(I did not pay anything for it but plan to upgrade to a paid version in the future – – as it is Definitely Worth IT!)
i
Online Armor is shareware (not free)
Comodo firewall was great on XP. Used Zonealarm before that, and currently use Windows Firewall Control on 7. Gotta have the pop-ups heh.
It should be “Note: I installed the latest version of Comodo Dragon on a test system” instead of “Note: I installed the latest version of Comodo Dragon on a text system”.
You are right, thanks for spotting the typo. Corrected.
Doesn’t Commodo Dragon bill itself as the chromium browser with added security and privacy features? Bit ironic isn’t it.
Here is a post in the Comodo PrivDog help forum:
https://forums.comodo.com/help-privdog/privdog-a-tool-that-hijacks-your-ssl-connections-t109892.0.html
As of right now, it has gotten 22 views but no replies.