You can't block Facebook using Windows 8's hosts file
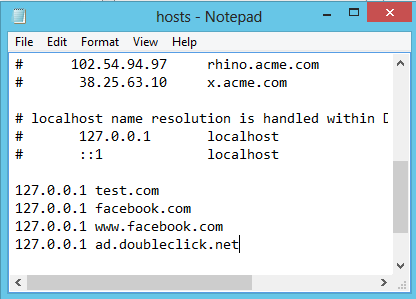
The Windows hosts file offers a great way of blocking or redirecting certain Internet hosts. I'm for instance using it whenever I move websites to a new hosting company to check the life site before the DNS has fully propagated. You can also download software like Hosts Man that allow you to add lists of known malicious sites or advertising servers to the file to block those automatically from being visited on the computer.
In theory, you can add any domain, host or website to the hosts file so that it is blocked on the system. Ghacks reader SGR just informed me that this apparently has changed in the Windows 8 RTM version.
While you can still add any host you want to the hosts file and map it to an IP, you will notice that some of the mappings will get reset once you open an Internet browser. If you only save, close and re-open the hosts file you will still see the new mappings in the the file, but once you open a web browser, some of them are removed automatically from the hosts file.
Two of the sites that you can't block using the hosts file are facebook.com and ad.doubleclick.net, the former the most popular social networking site, the second a popular ad serving domain.
The strange thing is that even write protecting the file does not have an effect on it as entries are still removed once you open a web browser. Actually, any kind of Internet connection seems to be enough for that behavior. If you open the Windows Store for instance, the entries get removed as well automatically.
This could be a bug that is affecting only some high profile sites and services, or something that has been added to Windows 8 deliberately. We have contacted Microsoft and are currently waiting for a response from a company representative. Since it is Sunday, it is not likely that this is going to happen today.
It is also in the realm of possibility that the hosts file may not accept other hosts.
Update: Tom just pointed out that turning off Windows Defender, which basically is Microsoft Security Essentials, in Windows 8 will resolve the issue. It appears that the program has been designed to protect some hosts from being added to the Windows hosts file. To turn off Windows Defender press the Windows key, type Windows Defender and hit enter. This launches the program. Switch to Settings here and select Administrator on the left. Locate Turn on Windows Defender and uncheck the preference and click save changes afterwards.
Please note that this turns off Windows Defender, and that it is recommended to have another antivirus program installed on the system to have it protected against Internet and local threats.
If you do not want to disable Windows Defender completely, you can alternatively add the hosts file to the list of excluded files and processes. You do that with a on Settings > Excluded files and locations. This basically blocks Windows Defender from scanning or manipulating the hosts file in the operating system.
Advertisement



















I am really enjoying the theme/design of your weblog. Do you ever run into any web browser compatibility problems?
A handful of my blog visitors have complained about my website not operating correctly
in Explorer but looks great in Firefox. Do
you have any ideas to help fix this issue?
I had the same problem in W7, and I solved it by adding the …/etc/ folder to “Excluded files and locations” in MSE.
It’s worth noting it’s not just Windows 8, I just noticed it done it on my PC too.
If you have Microsoft Security Essentials they changed something not too long ago so that when you edit the hosts file it triggers the AV. Because it was me editing the hosts file I just ignored it. But it also removed the Facebook.com entry in the hosts file. It left the other ones though.
The hosts file is there for web developers to be able to mimmick web addresses whilst testing development versions of websites.
But as this blog demonstrates, it can also be used for blocking Facebook, should the need arise.
That’s also happening on Windows 7 :-(
Maybe it’s not a bug, it’s a feature.
http://www.facebook.com/bug.vs.feature
I use Avira and it blocks all access to the HOST file unless I disable the real time protection. If Windows Defender is blocking the entire file then it’s just security, however, this article seems to indicate that certain websites cannot be blocked. So there is something else going on. And it’s not for our benefit.
I disabled Defender and uninstalled Security Essentials soon after trying them out. More and more, they appear to have been smart decisions.
These ‘features’ that silently are supposed to protect us from ourselves are totally unacceptable. PC used to mean personal computer.
Any app that can change the settings that a user has made (to the Hosts file or anything else) should give the user the option of whether the change should be made or not.
Thank you Martin for publishing this information. Please keep up the excellent work that you do. I won’t be surprised if Microsoft objects to this article too.
I’m trying to block facebook through terminal on my Mac and its also not working. Every other website works, but not facebook
A better solution than relying on hosts files to block annoying sites is to use Firefox and install AdBlock Plus. It blocks sites like ad.doubleclick.net by default, as it should.
Does Microsoft Security Essentials do the same thing? It’s supposed to do everything Windows Defender will, plus more.
I agree with Brandon: a power user doesn’t need a super antivirus, because he knows not to click on crap, not to download random stuff, not to give permissions when it’s not needed and so on.
And if needs to test out fishy stuff, he does it in a VM.
Thus, for a power user MSE is more than enough for detection rate, it’s fast, it’s efficient and it’s not annoying. It has the small issue of not providing enough feedback, that’s true, but it’s compensated elsewhere.
I just tested Windows 7 and yes, it’s the MSE which removes these entries from the hosts file. As soon as I started a browser, the MSE toast window popped up to let me know that it “removed threats” which entailed removing the doubleclick domain from my hosts file. So the issue isn’t new and it’s definitely unwelcome.
Why are you redirecting to 127.0.0.1 (or ::1)?
If you want to make a site not resolve using the hosts file, use an IP of 0.0.0.0. I wonder if the hosts file “fixing” by Microsoft handles that scenario.
Windows users…
just a bunch of sheep. None will know or care. Think Linux.
Did you know that even as far back as XP windows wouldn’t let you block any of the *.microsoft.com subdomains?
XP would surely let you store those things in the hosts file, but if you ran a sniffer like SmartSniff, you would see that on occasion, when you’d least expect it, windows would phone home behind your back, contacting those same servers you had deliberately blocked.
So you see, windows isn’t being called “defective by design” for nothing.
The easier and smarter way to protect users would be to prevent the file from being edited by an automated process. You can often verify the difference between automation and human interaction by asking for a piece of information the computer cannot synthesis–such as identifying an object in a photo, writing a ‘hosts’ file application, or completing a one-way function. e.g. OS X verifies user input by requesting a faux admin password from the user that matches a stored hash. Cake.
Microsoft is either experimenting with plausible deniability in tampering with users’ browser experiences, or they are just not synchronising their goals between their various divisions. It could be the case that Windows OneCare/Defender is part of MSN, for example, and the Windows Division had no clue.
Either MS is a company that has long outlived any kind of usefulness or brand respect.
I’m not running Win 8 or MSE on Win 7 but the registry location for MSE used to be:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft Antimalware\
There might be a registry value you can change to disable this “feature”.
Well the code didn’t come through correctly because it thought I was declaring an html tag and it removed all the leading space. Missing the leading space won’t hurt.
The line that says #include should be #include less-than-symbol windows.h greater-than-symbol
See if this looks right with some SQL-fu
#include < windows.h >
Given the way the Microsoft file systems work I bet you could write a trivial app to keep the hosts file open with deny-write access. I have had to do this in the past for other reasons, but I bet it would work here too.
From memory for XP. 7 may be different. Something like this in C. Run it with the path to the hosts file after modifying (and saving) the hosts file the way you want it and before you do anything else:
// keepopen.c by Cliff
// run it in a DOS box. It takes one argument; the file you want other processes to avoid modifying
#include
main(int, argc, char *argv[])
{
HANDLE h;
if (argc == 2)
{
h = CreateFile(
argv[1],
(GENERIC_READ | GENERIC_WRITE),
FILE_SHARE_READ
NULL,
OPEN_EXISTING,
FILE_ATTRIBUTE_NORMAL,
NULL
);
Sleep(INFINITE); // never returns
Close(h);
}
}
Just read the book Nineteen Eighty Four ;)
That should be, “it is recommended to have another *piece of* antivirus software installed” — the word “software” is like “hardware” or “clothing” and you have a piece of clothing, a piece of hardware, a piece of software. You do not have “a clothing” or “a software.” Grammar check, please.
“We have reached out to Microsoft”
You mean you asked them
Yeah apparently Microsoft are aliens who have colonised the moon :)
@Hellscreamgold, Actually he’s right in this case. In Windows 7, Defender was an anti-rootkit/malware tool. It was added in the days when anti-virus programs did not always scan websites for malware threats and you often needed two separate programs to protect your computer.
In Windows 8, Defender is a full blown anti-virus/malware/rootkit/etc. security suite. It’s basically a rebadged Microsoft Security Essentials built-in to the OS.
http://en.wikipedia.org/wiki/Windows_Defender#Windows_8
Bravo Microsoft!
We all know that you have a great track record with security in your Operating Systems and this new “enhancement” to security of Windows 8 will surely help rid us of millions of zombies and bots on the Web and make our (albeit now even more limited) user experience enjoyable.
Thank you!
Quit astroturfing. M$ sucks donkey dong and this is just another example.
This is not astroturfing, m’dear, it’s called sarcasm.
The author is a moron. Windows Defender isn’t an anti-virus system. It’s an anti-rootkit system.
@Hellscreamgold I’m afraid you’re the moron as under Windows 8 it _is_ anti-virus – MS renamed it. Try checking your facts first before insulting someone.
Try adding IPv6 hosts or turning off IPv6 i your network config.
Have you tried adding the hosts file to the Windows Defender exclusion list?
Windows Defender > Settings > Excluded Files and Location. Add the hosts file and see if you still have the problem.
It might be a good compromise between using the hosts file and leaving AV turned on.
..and why would you want Windows Defender anyway? Uninstall that crap and install a real AV.
Trust the yokels from redmond to come up with a completely bone-headed approach that actually causes far more grief than it resolves. It’s frankly amazing how many supposedly smart folks they have on their payroll, given the highly polished turds they so regularly turn out.
Regardless of these host file shenanigans, you can ALWAYS block any domains you don’t want on your network using DNS Redirector. This also has the advantage that you can block an endless amount of sub-domains without having list list each one individually (as you do in the HOSTS file) For example, in DNS Redirector all it takes is this…
doubleclick.net
facebook.com
facebook.net
fbcdn.
…and then every computer on your network would benefit, without having to edit the HOSTS file on each computer.
That doesnt make a whole lot of sene dude. WOw.
http://www.Privacy-News.tk
Solution http://www.reddit.com/r/technology/comments/yh2h6/bug_or_feature_you_cant_block_facebook_or/c5visq0
You can change permission on the NTFS side to prevent windows from messing with it. Read only on the file properties does not stop the system account and never has.
People still use virus protection? Interesting.
Yeah it’s all the rage these days with macs and androids ;)
Easy solution, don’t use windows.
Technet still doesn’t have an answer to this (and it was asked 31-Jul):
“hosts file – not able to block facebook.com”
http://social.technet.microsoft.com/Forums/el-GR/W8ITProPreRel/thread/cad06d70-f5a6-4661-83ba-90366a6e2380
Easy fix is to modify permissions on the system user so that it only has read and execute permissions, Works for me,
I think it’s just because those two companies resolve IPv6 before IPv4, so your blackhole doesn’t get used.
Try blackholing in IPv6 also.
I think it’s just because those two companies resolve IPv6 before IPv4, so your blackhole doesn’t get used.
Try blackholing in IPv6 also.
One of my friend running Win8 RTM just confirmed that stopping the MSE process solves the issue.
It seems to be a security feature made for ‘default’ users and looking form that way it’s not necessarily bad. Altough there’s no option on MSE settings to disable this. Serious people using 3rd party security software anyway and the presence of one automatically stops MSE afaik so it’s not a big problem.
I fully expect that there will be an update of group policy templates that include managing features like this. Their corporate customers wouldn’t demand anything less, and I don’t see Microsoft biting that hand, especially when it’s such an easy gesture for them to make.
why do you say that serious people use 3rd party security programs? I think mse is probably the best av for windows and it’s free
Brandon
MSE is the worse ever Anti virus software whether free or paid. There has never been any thing worse than MSE.
Well there are several things people can take account deciding the best AV product, for me the detection and protection rate is the first and speed is close second. Searching for “virus scanner detection rates” gives you tons of results of product comparsion.
Eg. http://www.av-comparatives.org/comparativesreviews/detection-test looks a comprehensive one.
MSE is told to be a basic protection even by the author. Plus it’s not a suprise that its results are not comparable to products that are in the market for 20+ years. Though it’s not a sole reason to be good product, either.
IIRC you should find one or more articles about this topic here in Ghacks as well….
Tom thanks for the confirmation. I find it strange that MSE under Windows 7 does not do the same though.
Well,you can keep using Windows Defender but you need to exclude hosts file from scanning.
btw. servedby.advertising.com disappears too.
Best Regards
Yeah I thought about the same, to check it in W7. So appearently it’s a feature for Win8 only or the MSE version currently available for download is not the same as the one integrated to Win8. We might expect this ‘feature’ later with an MSE update… though the above thought fits for Win7 users as well. Power users who know what is the hosts file are usually running more serious 3rd party protection and not MSE.
Would be curious to know if locking yourself out of the file using NTFS permissions would make the changes persist.
Make yourself owner, remove all permissions, give yourself only read access.
Microsoft : All your HOSTS file are belong to us .
That’s not a bug. Microsoft wants to make sure their “tiles” (which include facebook, twitter, linkedin and a few more) work flawlessly. That’s why they “override” your settings.
To achieve the same blocking-effect you’re used to, you’ll have to use your own local DNS proxy. For Windows, there’s (besides Bind and derivates) a tiny tool called “Acrylic DNS Proxy” which is availaible via sourceforge.net/projects/acrylic/ and this little thingy also supports regex and wildcards (so you can catch all those subdomains with just 1 line).
As this is only one of the many things Windows8 will bring us. Check out their new “billing” ideas at their live.com website for more of what’s coming. If anything, Windows8 will drive more people towards Linux (incl. Apple) than Microsoft might wish for.
Anyway: it’s not a bug, it’s a “feature” to be aware of as it can and will have an impact on your privacy… just like the “lock-machine-to-personal-data” thing that Microsoft has implemented.
I guess the days of “enjoying a slim and working operating system” are over in the Windows corner of the world. Up next: “enjoy your online-shop interface called *Windows8* and forget about not being tracked all together”.
I mean, I know where they’re coming from: they will be able to identify “stolen” OS installs easier than ever… but they will be “knowing” users better than ever too. And that’s where they’re losing my trust. I rather keep my privates private and I’m pretty sure I’m not the only one. ;)
+1
After losing $7B on their advertisement agency, Microsoft want Windows 8 users to be forced
to see advertisement and spam and on the way collect some $$$. Look at Windows 8 store where Metro apps display advertisements.
“own local DNS proxy for Windows” -best one is powerful Peerblock
(win successor of Privoxy ) – similiar in using/maintaining as HostsMan .Use both.
the most stubborn to block even in W7 without any WinDef, MSE
seems CDN akamaitechnologies.com ,some content is sent by it -I see in TCPView
,even being blocked in many ways.
So U can suspect for whom they really work….
Doubleclick is owned by google…
Did anybody try to run a procmon trace to see which process edit’s the host file, it could very well be a trick of MSE and not the OS.
Yeah, this’ll *really* make Windows 8 popular with the IT crowd. How the heck are we supposed to do our jobs if the OS itself counters this?
No “need” to upgrade to Windows 8.
I block facebook using tinyFilter in Chrome.
I reserve editing the hosts file for DNS specific propagation.
If it turns out to just be some HOSTS entries than I’m probably not going to care too much if the software is doing it’s job. However Windows Security Essentials should explicitly tell the user that the hosts file has changed and will revert/edit it. Otherwise many system admins are going to be left scratching their heads.
PS. The “Hosts” file was never designed as a whitelist/blacklist, it was designed as a way to give local machines on the network logical names without DNS (so logically this file shouldn’t contain any REAL names resolvable by working DNS.) If you really need this type of function, your home router may also have URL blocking functionality.
PS. The “Hosts†file predates DNS so your PS is erroneous. Host files were designed to map a name to an IP. Breaking that IS a bug
If you’re relying on a hosts file to prevent your users from going places you don’t want them to, you don’t deserve to be working in IT.
Go sell flowers or something.
hahahaha! Well Said!!!
Sorry, do you actually work in IT?
Because it doesn’t sound like you do.
The hosts file has a number of perfectly valid uses – one of the main ones is to keep test/live/dev environments etc separate.
Please, before you start spouting off, make sure you know what you’re on about.
That is not why people do this. You edit the host file in order to prevent, say, doubleclick from loading ads. You basically tell your computer that doubleclick.com exists locally so when a web page tries to connect to it the browser will display a 404 instead of the ad.
This is neither true nor the point. There are scenarios where controlling user access to websites via the hosts file is appropriate, and even if there weren’t, it is not ok for an operating system to pick and choose which sites administrators can block based on who is popular or willing to pay.
HACK THE PLANET!!!!
This must be some security “feature” and I wouldn’t be suprised if a bunch of other domains are also protected. Done for any reason it’s implemented stupidly if it removes entries pointing to the localhost.
Martin, it would be interesting to see what happens if you temporarily disable the security services like SmartScreen, Windows Defender, MSE, etc… would answer that is this a part of the security system or the domains are hard coded somewhere in the DNS resolving part.
Microsoft (c) “Deciding for you since 2012”
That’s obvious hacking protection. M$ don’t want theirs users to be deprived of joys of Facebook, or adds.
definitely sticking with windows 7 :|
Hahaha! That’s just hilarious. The locked OS is trying to control your browsing experience. Here’s to hoping Win 8 crashes and burns with no chance of recovery.
Maybe Microsoft will get their act together with the next OS.
Does the HOSTS file remove all the added entries¿ Or does it only remove the facebook and advert domains¿ So glad I also block those domains from my router and network.
I don’t care about “high profile sites and services”, I block what I want, WHEN I want. If some OS will try to force me to do something I don’t want, let it burn.
Same reason I despise DRM on stuff I’ve paid for. It just makes me avoid things that have them.
Wow, you’re an idiot. I love people who are completely clueless about network security and make ridiculous statements about something they have no understanding about or have even put any effort in researching. How about you channel this hateful effort towards Microsoft and focus it on understanding the security impacts that an editable host file has.
The end user is always right, so if the end user wants to override it’s local DNS resolution, it should be able to do so.
If you want to cut off attack vectors like this, you might as well block incoming E-mail.
There is no reason to assume that a request rerouted to localhost is malicious, just because it’s rerouting to localhost.
There’s better ways of detecting local web server presence. And malware could of course make a request to 127.0.0.1 itself, bypassing the hosts file alltogether.
If you’re really such a wise guy, please elaborate and enlighten the readers, instead of being aggresive to the writer of the (either way informative!) article.
I am with you. This clearly a piece of software behaving in the way it was intended.
I have seen LOTS of malware that installs local services and then redirects websites back to the local machine. In fact HOSTS redirection is a common attack vector, so go Microsoft for including this protection in their included security suite.
this isn’t actually windows doing this its security essentials no big conspiracy just an anti phishing program doing what it was designed to do
Some malware programs run a local webserver on your pc that traffic is redirected to.
Then they should have accepted a redirect to localhost as a legitimate change a user might want to make. Phishing expeditions will redirect to a malicious -external- site.
May be this is some sort of phishing protection from Microsoft, so that malware programs wouldn’t be able to edit hosts file.
Thanks mate,seems you know what you talking about so I take that as a important lesson.
Btw. I’m using hosts file just to block advertising and since I have no FB account don’t want to waste my bandwidth for connection to FB as they are everywhere these days.
Best Regards.