Why are People still selecting Weak Passwords?
If you have followed security news in the past days you have surely noticed that several sites had been hacked in one way or the other. One of them, the Yahoo Voices service, even saved user passwords and information in plain text, which is one of the biggest no-nos in the development world.
The reason for this is simple. Lets imagine an attacker manages to get hold of two user databases. One were the passwords are encrypted in one form or the other, and one where they are listed in plain text.
To gain access to user accounts, the attacker would have to decrypt the passwords in the first. In the second, nothing would have to be done because all the data is already there in plain sight in the database.
A plain text database on the other hand provides security experts with insight to the password selection process. And in the case of Yahoo Voices, they have discovered that the top passwords are exactly what they would have been ten or even fifteen years ago. Passwords like "password", "123456" or "qwerty" are considered weak passwords for a variety of reasons, including being always in the top selection when passwords databases are analyzed. Some are even used in movies to get into a computer.
In the case of Yahoo Voices, it would not really have mattered if you would have selected "princess" as your user password, or "gGwPywfzNjPOnlKE98J,", as both would have been listed in plain text in the database.
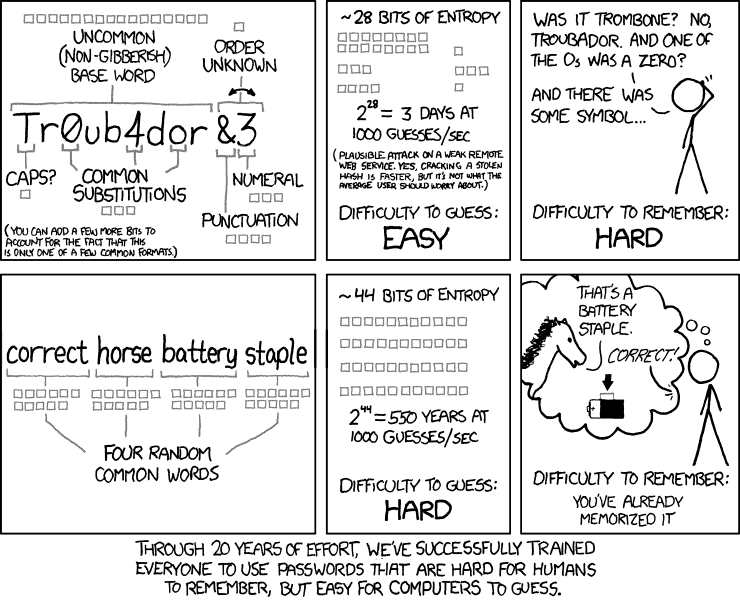
What people should however ask is why users are still selecting these weak passwords and not secure ones. In times where password managers are available free of charge, it does not really make much sense that these passwords are still topping the password popularity lists.
There are two parts to the answer to the question. First, these passwords are selected by users because they can.
And second, because site operators let them. If you operate a website or service, you should obviously make sure not to save your passwords in plain text.
But next to that, you could also come up with password rules that make it impossible for users to select weak passwords. How those could look like? You could for instance raise the minimum password length to ten characters and require users to pick at least a number and a special char in the password.
If you think that is turning away some users who try to register but fail, then you are probably right about that. But it is very likely that the majority will simply select a secure password instead if they really like to join the service.
In turn, their passwords are better protected from attackers who try to brute force their way in either via the web front end or by getting hold of a database that stores the password information.
Another option would be to display suggestions on the sign-up page. You could suggest to users signing up to pick passwords of a certain minimum length without enforcing those rules. While that would certainly get some to pick secure passwords, other's would possible ignore the suggestions to select the easy to remember "qwerty" instead.
What's your answer to the question? Do we need stricter password guidelines to improve password security? Or different systems that replace traditional passwords? Lets discuss in the comment section below.
















the reason why people use weak passwords is probably because they do not care if their account is hacked or if they are just a average user
One phrase says it all…”Nobody expects the Spanish Inquisition!” :)
I deliberately use 1234 (or 123456 or some such variation) on sites where I don’t CARE if the password is hacked. By doing this, I don’t have to worry about remembering something, AND I don’t have to worry about the password I use being common with somewhere I do care, like my bank.
Most often these are garbage forums where I just want to post a quick reply, or even READ the thread, but the stupid forum insists I create an account first. Ghacks does not fall into this category of course because it lets me comment with just a name and email. I always honor such openness by using my full real name and my genuine email. I often don’t for garbage forums: nobody@nowhere.com is the most polite one I use in such cases.
Ross,
You make a valuable distinction between the levels of security required to operate safely on the Web and the fact that ones passwords can be adjusted in strength accordingly. Can I add an intermediate level to your differentiation of the passwords used?
Low Security ……. websites that contain little or no personal information that could be used adversely if the website is hacked ……. simple passwords that are easy to remember and have low entropy e.g. 123456 or test123 or princess or password
Medium Security ……. websites or user logins on computers where some personal information is stored that you would not want to have compromised such as correct name, DOB, address, credit card number …… medium strength password or passphrase that utilises the 92 printable characters available on the keyboard eg (4wIndydAyZ) or fun@HOME2day. This will give you a moderate entropy value and make your password less easy to crack
Strong Security …… websites that relate to financial matters or administrator logins on your computer where the password being hacked would lead to the disclosure of private, confidential and/or financial details …….. strong password or passphrase that utilises the 92 printable characters and the use of user defined rules to manipulate the characters in the expression to form a pseudo random set of characters e.g. this is a bit more difficult to demonstrate but one could use a rule such as letters on the middle row of the keyboard are transposed up one row and one key to the right so “thisiwouldbehot” becomes “tiirwouqtbeiot” The more rules you apply the more random the phrase appears. The trick is that after a few goes of typing this you think of the plain text password but your fingers type the encrypted phrase. You end up with a pseudo random password that has a high entropy value and will take ages to crack.
Note: with the strong password when you switch from a QWERTy to an AZERTY keyboard you have to think of and type the encrypted password which does require some hunting on the keyboard since the transition rules no longer operate correctly, or conversely you reset the password to work with the layout of the new keyboard.
Note: if working in a team make sure everyone knows the rules by heart, otherwise much time can be lost when a team member transposes to the right instead of to the left when altering an administration password. Because what you type on the keyboard has little resemblance to the original passphrase the original could be stored in plain text with little security risk. However the rules for transforming the password should never be written down, since you will remember them.
The same levels of security can also be applied to email accounts and for much the same reasons, from the fluffyduck account for rubbish to the general hotmail account you use for general mail to the private account you use for personal and professional reasons.
A user has to have some idea of where they are strolling on the Web and to take the appropriate precautions in terms of being prepared and secure. The time taken to work out a secure password now is much better than the time and angst required to resolve the after-effects of an inappropriately week password.
Michael,
I’m a pretty average user – not a techie. I began to read about Keepass and LastPass but in the end I was overwhelmed by the documentation of the software that is supposed to make my life in the world of passwords so much easier and safer. So I did not install any password manager. Dumb? Probably, but – as I said – I’m an average user and I gave up without doing anything. I bet most people do what I did (or even less).
I have just discovered that there is a current version of NIST Electronic Authentication Guideline, which was published in December 2011. For those who are interest the link is
http://csrc.nist.gov/publications/nistpubs/800-63-1/SP-800-63-1.pdf
The Computer Security Division of NIST has a Computer Security Resource Centre in which you can have a look at all their various publications. This page groups the publications by Topic Cluster
http://csrc.nist.gov/publications/PubsTC.html
There are some interesting, if somewhat technical documents,.over a wide range of security topics
Michael
I use a combination of Keepass and Lastpass to manage my passwords. All “proper” accounts use pseudo-random computer-generated password which I can’t even try to remember. But I also keep a few “disposable” accounts which I use for my Android phone. These accounts have simpler passwords to make them easier to recall and type in a small keypad.
I will admit that I knew little about the concept of password entropy, so the cartoon from XKCD always rather confused and possibly annoyed me. The higher entropy of the pass phrase of random words compared to that of the more random single phrase seemed counter intuitive until I looked at the mathematics and the underlying assumptions for assigning values of entropy bits.
Appendix A “Estimating Password Entropy and Strength” of the NIST Publication on Electronic Authentication Guidelines
http://csrc.nist.gov/publications/nistpubs/800-63/SP800-63V1_0_2.pdf
gives a good description of how to calculate the entropies of different types of passwords and perhaps more importantly gives a table of the values of bit entropy for different types of password.
For example, one of the secure sites I use requires a maximum of a 12 character password with lower and upper case, numerics and special characters. If one choose a pass phrase of 12 characters that met these criterion then the password would have an entropy of 34 bits. Using the example in the cartoon of 1000 guesses/minute, then it could take 5.5 years to correctly guess the password or some 17 billion attempts ( 2^34 attempts).
This assumes the absence of a couple of important features that I would have thought would be built into any secure website. These rules would be mandatory for any secure computer system. The first would be password ageing, which would force the user to change their password after a set period of time. In this case, a change is forced every six months, which is well within the guessable time of the password, assuming that we don’t have an infinite number of monkeys doing the attempt of course.
The other feature is that the account is locked after a set number of failed attempts at the password. The account is either locked for a set period of time e.g. a day and then frees up again, or the account can only be unlocked by contacting the organisation running the web-site, and by verifying yourself via a number of security questions. On secure computer systems, we would set the limit to five failed attempts and then lock out, which would allow for bad Monday mornings.
Having said that, may I also comment that it is a bad idea to change the administrator password for a major system late on a Friday evening and then to rely on the fact that you can remember it correctly on a Monday morning after a heavy weekend. There is a lot to be said at times for the existence of back-doors.
To get back to the question you asked at the end of the article, constructing a strong password that can be remembered is extremely important and it is actually not that difficult to do. But it is also possible for site administrators to improve the security of their sites by adopting a number of security measures that will limit the vulnerability of their users to attack. The onus cannot be simply put on the users to look after their own security. If we are competent at what we are doing then we, as administrators should be able to put in place the measures that will help protect the systems.
Michael
Good advice about not changing a password on Friday. I once changed a password before going on a two-week holiday trip, and yes, could not remember it when I came back.
I agree to you we need a more stricter password guidelines, the fault lies in both
1. Webmaster
2. Users
There should be a password implementation guideline for webmaster and software makers and should reject any weak password. . Mozilla has tried to implement it through Browser ID, a unique method to avoid remembering multiple passwords. It uses asymmetric cryptography and digital signatures to allow browsers to create signed assertions about the user’s identity, and by identity providers to vouch (via signing of a key-email pair) for a user’s identity in a disconnected fashion. its implementation is done by mozilla, wonder whether it will pass to through community and get adapted.
I never store passwords in notepad, emails or even in mozilla firefox database. I dont know how many people use password manager, but it really takes out the hassle for remembering passwords. I use keepass and it makes password stronger, its database is encrypted and it follows the password implementation guideline. The only thing is to keep the back up of database.
If its interest to you martin, i am sharing this guideline with you
http://doit.sfsu.edu/node/628
I was once really disappointed when I forgot the password of one of my emails just because of its complexity, and never tried another difficult password again. After that, when signing up on some websites I was asked to choose a strong password. This time I used the “notepad” of one of my email addresses to write down those cumbersome passwords in case I forget them. This way you have access to your passwords wherever you go but keep in mind this is also very dangerous, cause that one email address could be hacked.
Another technique is to write down only the website (and not your account) and the difficult part of the password, i.e. : “uppercorner!777,34” to “!777,34”.
> Do we need stricter password guidelines to improve password security?
Advices are great, but enforcing 12 character alphanumeric passwords might not be accepted by users and attackers can ignore anything below 12 characters. Since “aaaaaaaaaaaaa” or “1111111111111” are not allowed an attacker can ignore those as well.
People don’t want to use passwords that they can’t remember. So, they don’t. Many (most?) people would avoid using a site or an application if they found it demanded a secure password AND if that password was hard to remember. Unless they absolutely had to use the site, they’d avoid it.
We need something better, easier, and more secure. I have no idea what that might be,
Finger print login, my laptop has a finger print scanner already.
Answering you question “Why people still use week passwords” I think it has to do with not wanting to store difficult long passwords who they cant remember, because there afraid that will lose them ore getting hacked.
The other thing to keep in mind is that free websites such as Yahoo are often used for ‘disposable’ email accounts. With a disposable account, they’re not interested in security when signing up, so will often use any old password.
So, I wonder how many of the accounts using the passwords ‘password’ or ‘12345’ were actually proper accounts?
You can make your passwords short but simple. For example you can make it your name and four numbers for example myname4356
Good point Tim.