How Secure is Your Password?
As part of writing my forthcoming "Windows 8 Power Users Guide" from Apress and "Troubleshoot and Optimize Windows 8 Inside Out" from Microsoft Press, there are inevitably chapters where I have to talk about security and, as a part of this, passwords.
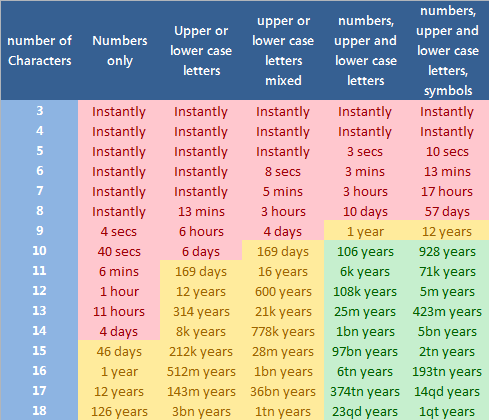
In Troubleshooting Windows 7 Inside Out I included a table showing how long it would take an average PC of the day to crack passwords of varying lengths and complexities. Obviously for the new books this table would need updating and it's a good indicator of just how quickly processing power has moved on.
As an example of this in the last book, written in 2010, an 8 character password made up of both upper and lower case letters, numbers and symbols would have taken 2.25 years to crack. The same password now would take just 57 days. I have included the data in a table for you here, heat mapped with what I consider to be safe and unsafe password combinations. Where does your password fit in the table and how secure is it?

Key:
k – Thousand (1,000 or 10-3)
m – Million (1,000,000 or 10-6)
bn – Billion (1,000,000,000 or 10-9)
tn – Trillion (1,000,000,000,000 or 10-12)
qd – Quadrillion (1,000,000,000,000,000 or 10-15)
qt – Quintillion (1,000,000,000,000,000,000 or 10-18)
Moore's law has a lot to do with the shorter times it takes to crack passwords today when compared to just a couple of years ago. This theoretical rule states that the number of transistors that can be fitted into an integrated circuit doubles approximately every two years. When you also consider new programming methods to allow any PC to use the GPU on some graphics cards and the popularity of quad core (and even higher core count) processors we can see where a password that we previously considered safe now simply isn't. Indeed a very secure password that I used fifteen years ago has now been in the "cracked instantly" category for some years now.
My advice is to make sure that your password contains both upper and lower case letters, numbers and symbols and that it is at least 10 to 14 characters long. You can use numbers and symbols instead of some letters, for example the number 0 can be used instead of an o or O, a £ can be used instead of an e and a 1 can be used instead of an i or an L. You should also always avoid dictionary words (the first things password crackers look for) and easily guessable numbers such as the year of your birth.
My own password falls comfortably in the safe zone on the chart, much as this came as a relief to me, but another password that I use less often and that I considered safe is now in th red danger zone so I'll be changing that straight away.
You'll be able to read more about in the fall when the books are released, and there will be much more on security, safety and passwords included in each. This subject is, after all, extremely important to all of us as malware increasingly tries to guess the passwords to our email and other accounts, and that the use of Internet banking means there really is something to gain from being a criminal.
So where does your password fit in the table? You can check your own password at www.howsecureismypassword.net where this data comes from or at www.grc.com/haystack.htm.
Advertisement
















SubgeniusD : I think haxor’s point was that capturing the password by compromising a system (i.e., keylogger, SQL injection, etc.), packet sniffing, or social engineering (e.g., phishing or other deception) has become the method of choice. I don’t work in security, but that sounds right to me. These days, cracking passwords with brute force is seldom heard of, except for forensic work (i.e., law enforcement, intelligence, etc.).
Just because someone YELLS IN CAPS and has a goofball ID doesn’t make everything they say automatically wrong.
No Alex, he simply ends with “anyone can hack your pass” . If that were the case PayPal would’ve been broken and the web economy shattered by script kiddies at this point.
I follow Paul dot Com and other security pros and know about the multitude of ingenious attack vectors criminals come up with. Check this guy out for a dive into the deep end of the security pool http://www.irongeek.com/
If “haxor” isn’t just a trashtalkin’ dumbass let’s see if he can “hack” my gHacks forum password lol — will never happen……
Sorry Alex, but I suspect that HAXOR is trying to sow FUD.
Social engineering is an oft-used route to gain entry to systems BUT the point is that once entry is gained, hackers are often looking for secured data because they know that it is valuable. There have been many cases in the news in the last 12 months.
So password length and possible complexity is VERY important to anyone who uses the Internet for transactions that they want kept secure.
Even things like Facebook and Twitter should be kept secure – the amount of information you put into these systems and their importance to your identity make the critical to many people. Facebook compromises would not just affect you but all of your contacts too. The higher your profile, the more critical this is of course. But then, you never know if you might become high-profile in the future! And even if you don’t, there are plenty of people who put things onto Facebook that would seriously embarrass them if they became known to a wider audience – there are a small but well documented set of people who have committed suicide over this.
So my advise is don’t take your security for granted. It is VERY easy to make your passwords stronger without making them harder to remember as I said in my first comment. Additionally, use something like LastPass or KeePass to manage passwords.
Regards, Julian.
THIS ARE FAKE THINGS…WHY? CAUSE ALLMOST NO ONE CRACK PASS IN THIS DAYS. ITS SIMPLY HACKS THEM… SO NO MATTER HOW MANY ALPHANUMERIC COMBINATION YOU MAKE ANYONE CAN HACK YOUR PASS….
RAZZOR 4 EVER
You obviously have not the slightest idea what you’re yelling about “haxor” noob.
Note that the statistics published in the article only apply if the attacker has the encrypted password, or what is known as an off-line attack. Even with no password lock out, the attacker cannot perform an online attack at such speeds. Network overhead and application response time are the bottleneck for the attacker.
Why is 46 days highlighted in yellow even though 57 days is highlighted in red? Is there some sort of time-warp going on here?
I have found the best way to create a password is by using a line from your favourite song. For instance, “Amazing grace how sweet the sound” you can get 6 characters easily from: aghsts and it is very simple to remember and type in. Throw in a bit of upper and lower case, some letter -> number switching, and maybe a significant number to yourself with the shift key held down and you got yourself some special symbols too.
I get my most secure password using this method, it is 10 characters long and even I don’t know what the password actually is unless I type it out on a keyboard to look at it (because the symbols are actually numbers in my head)
Gonna have to update and increase the password length but. 900 odd years doesn’t seem enough.
You are headed in the right direction. However, 10 characters is nowhere near long enough for a secure password!! I certainly wouldn’t trust my financial data to something so short.
The good news is that you do not need to make it more complex. Keep your current password and simply add an easy to remember pattern of characters on the end as per my original comment.
Regards, Julian.
There a rule: If was made from human everything could be resolved…
There’s a slight issue with the coloring of the chart, 106 years is acceptable but 8000 years is unacceptable?
I wish people would stop referring to these as “passwords” and start referring to them as “passphrases”.
Exactly the reason why I made this simple thingy – http://gundars.me/spg
On the key for the numbers… all the power are incorrect. The powers should be positive, not negative. Negative would denote decimals.
You may want to correct the power portion of the legend;
k – Thousand (1,000 or 10^3) not k – Thousand (1,000 or 10^-3), etc
please delete this, too fast scrolling made me miss the earlier comment referring to this.
I disagree with part of your recommendations. Speaking as someone who has actually brute force hacked passwords the dictionary size and length are all that mater, not the complexity. Steve Gibson has a wonderful write up on it here. https://www.grc.com/haystack.htm
Ah yes, I meant to reference him in my original comment!
The heat map is very confusing. Why is a 10-character password with numbers and mixed case letters safer than an 18-character password with mixed case letters but no numbers? The colors are not consistent with the time required in a brute-force attack.
I find it hard to worry about hackers gaining access to a database dump. It is the bank’s responsibility to prevent that from occurring, and surely they would be held liable, not the customer. Moreover, the attacker would be attempting to crack many thousands of passwords, not just mine. The probability that an attacker would crack my moderately secure password seems to be vanishingly small.
Sorry, but this is terribly MISLEADING.
Adding punctuation and numbers does *not* magically make passwords secure. Length works just as well. Randomness (i.e., not dictionary words) is essential.
From the chart:
(a) 18 mixed-alpha (e.g., “cqmqnrbeihnejlzdml”): 1 trillion years
(b) 10 alphanumeric (e.g., “a0ohR7VdZf”): 106 years
Why do you color (a) yellow but color (b) as green when (a) is obviously more secure.
Also, all of this only matters if you’re talking about encrypting files and such on your own computers.
If you’re talking about online accounts, any reasonable system will lock you out after a few attempts, so even an 6-digit number (i.e., “302073”) will do fairly well. If the system locks you out after 10 wrong attempts, an attacker would have a 0.0001% chance of getting in before being locked out. Just make sure your password is truly random, so they have no better than random chance of guessing it.
BY FAR the bigger issue is people using the same password on every site/system in their lives. Once one gets compromised, the others are all immediately compromised or at least extremely vulnerable. Password policies about characters/length can’t guard against that.
Although you are correct in part. The actual complexity doesn’t matter, the POSSIBLE complexity IS important plus the length (which has the greatest impact).
However, I don’t agree that this applies only to local files. The problem is, as Sony and many others have discovered, remote files can become local to a hacker all too easily when a system is compromised. At that point, the hackers have time to analyse passwords at their leisure and password length and possible complexity are then very important again.
So we have to consider the problems of the normal security being bypassed.
Regards, Julian.
Since the only thing we are worrying about with this sort of analysis is when the attacker has free reign to tr as many passwords as they like, that practically means they have to have the password database. We can’t rely on users to use longer passwords (and if we force them they will write it down on a sticky note on their monitor and game the system some way to reduce the entropy of their password), so we need to make the password database more secure against brute-force attacks.
Salted hashes (and making the salt longer) only really prevents building large password->hash tables, such as rainbow tables. If we instead make the hashing algorithm more complicated and slower, that will work for now, but it means we have to constantly update the algorithm and we can’t simply re-hash the old passwords, we have to wait for them to login before updating it. It also isn’t clear that the common ways of extending the hash, such as more rounds or running the same hash with different salts, aren’t vulnerable to cyptanalysis to reduce the space that has to be searched.
So, my conclusion is that we simply need to stop relying on such passwords in a central location. There seem to be two possible solutions:
1) digital signatures, with the private key protected locally by a password, so there is no central password cache to be broken. Individual users are still vulnerable to having their password and certificate stolen, but there are ways around that such as using the TPM for signing operations.
2) 2-factor authentication. Google Authenticator is open source and widely available on smartphones (there are probably other options as well), supports multiple accounts, and avoids this problem by making the password insufficient for account access — you also need a code generated by the authenticator.
Any other ideas?
I agree with you. You cannot force users to be sensible!!
2-factor is an excellent choice when you need to enforce the best (but still reasonably easy to use) security. For example, online banking and PayPal.
I love the fact that you can use 2-factor on PayPal.
Regards, Julian
It is the POSSIBILITY of using non-alpha characters that is important not necessarily actually using them. Length is the most critical factor by far. If you have the ability to use complex pass does, you can actually use well known dictionary words as long as they don’t make up the whole pass code. A password such as:
My.code.1234—-
Is actually both very strong and easy to remember, you don’t ever need to have “random” character strings. Steve Gibson on grc.com has an excellent write-up of this.
What you need to remember is that the WHOLE password has to be decoded at once, you can’t decode it in stages so it doesn’t matter how simple each part of your password is as long as the whole has complexity.
Regards, Julian Knight,
Depends on which password we are talking about. The windows login password for instance is utterly weak.
I don’t understand the heat map. A 8 char password can be cracked in 57 days at most and is red. A 15 char password can be cracked in 46 days, but it’s yellow. It’s not based on the time an attacker needs. 106 years is green, but 126 years is yellow.
I consider a larger pool of available characters more secure, so that seems to be reflected in the heat map as well.
I have a 38 character password mixed everything and upper and lower case for a hidden TrueCrypt volume. How long to crack that?
Didn’t you read the article? He gives a couple links at the end, the second one will answer your question.
btw you’ll see why a 30+ character pwd is ridiculous overkill, with so much easy to crack low hanging fruit available no criminal’s going to bother with even a 10 character non-dictionary pwd.
Who in there right mind would trust a research center with their secret password after testing it out o their site? Especially with java scripts running rampant.
I simple, practical question :
Suppose an online banking customer
uses a pwd of 8 chars,
(mix of # and letters).
Your Table above ,
shows:
3 hours to solve (red bkg).
I’m ALL for secure pwds,
but, _in practical terms_ :
the hacker would have to try
all combinations in those 3 hours,
until he found and entered “the right one”,
in the Bank’s login form.
How many chances do you think,
he’ll have to try each new test pwd,
before the Bank (or trading house)
blocks the Client online acct. access?
For my Bank, it’s only 3 (three) times…
At that point, the real Client (in most Banks),
has to voice-call the Bank to “unblock the access”, again.
This, after a series of grueling authentication questions…
for ex:
– ” so…where were you on April 7, 1942 ? ” , or
– “what is the mass of a photon at rest?
etc.
You get the idea…
Am I missing something basic here?
SFdude
There are more ways to crack a password than using an online form. Hackers could get hold of a user database dump from that bank, in which case your eight digit passwords would be cracked in no time.
Ah, yes Martin.
I see your point…thank you.
Thanks good article it let’s me take hard look to main password’s and its imprinted now that I have to do that every year.
Main request to you Mike is will you be so kind to do a follow-up next year around the same time, or maybe when there will be one unexpected development?
He – http://www.xkcd.com/936/ – encapsulates the subject with his trademark humor and satire…..
Sorry to bother you with this not-so-relevant stuff, but all the negative powers of 10 should be positive.
Somebody had to say it, very true… I was like WTF ?!
I can’t think of any site I’m registered on that allows symbols.
These calculations assume that the attacker knows whether you’re using letters only or letters with numbers, symbols, etc. In the real world the cracker has to try all valid characters, so the length is far more important. For a better perspective, I refer you to Randall Munroe:
https://xkcd.com/936/
… I need another table…my password is 20 characters and has everything except for upercase letters
More often than not, services post password restriction rules on their site, e.g. that you are not allowed to use special chars, or that you can only use some and not all. Those information are used by attackers to speed up the brute forcing. But you are right, if you do not know if there are limitations, or if there are none, you need to use all possible characters if you want to hack into a specific account, or all accounts.
If you have a large user database, you may prefer to limit the characters to speed up the cracking. While you may reveal all passwords then, chance is great that you will reveal the majority (up to a reasonable amount of characters that is).
@S True, but this also depends on the resources and time the hacker has available. It can be assumed that they’ll start with dictionary words and names and then start adding two digit years to the ends of those.
I completely agree that long passwords are the way forward, but it’s still important to highlight the differences in security between alphabetic and truly random long passwords.