Microsoft Security Bulletins For April 2012 Released
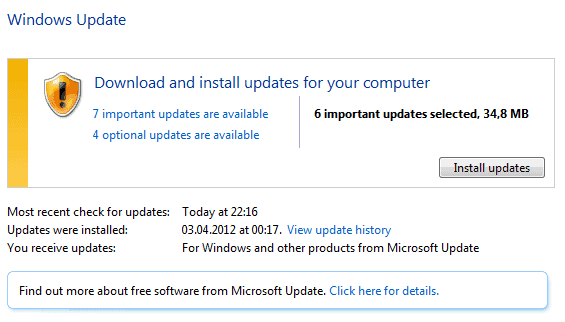
It is the second Tuesday of the month, and that means patch day over at Microsoft. Windows systems configured to automatically update should pick up the updates on the next start of the system. Users who do not want to wait that long can run a manual check for updates instead. On Windows 7, users need to click on Start, enter Windows Update in the run box and select the first entry with that name in the listing.
The Windows Update control panel applet opens, where a click on Check for updates in the sidebar runs the manual update check. If everything works out, you should see the available updates increase in the main pane of that window.
You can click on the update links to manage the updates before installation, or click on the Install updates button right away to start the downloading and installation of the selected ones on the system. Please note that you need to restart the computer after the updates have been installed to complete the process.
For more information on the process and alternatives, check out our Windows Update guide.
Microsoft has released a total of six security bulletins in April 2012 that fix vulnerabilities in a variety of Microsoft products. Products include Microsoft Office, Microsoft Server Software, SQL Server, Microsoft Windows, Internet Explorer and the Microsoft .Net Framework.
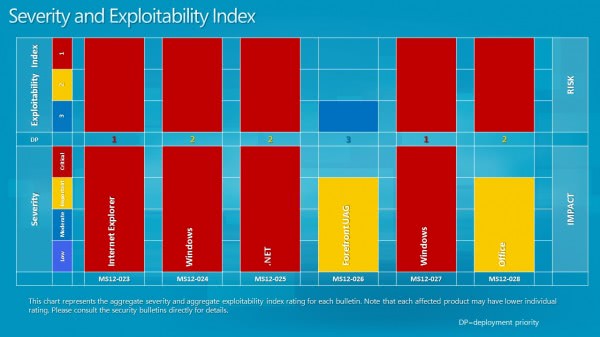
Severity and Exploitability Index
Four of the bulletins have received a maximum severity rating of critical, the highest possible rating, while the remaining two one of important, the second highest rating. The actual severity rating depends on the version of the software and the underlying operating system, and may differ as a result of this.
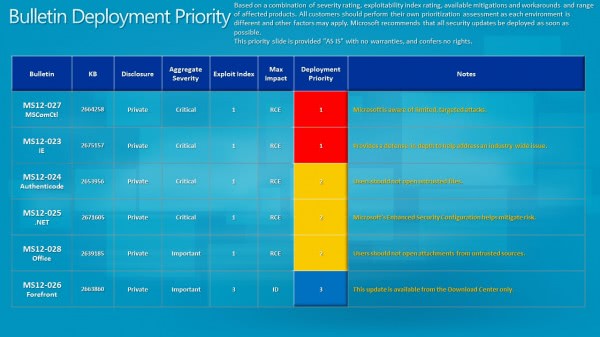
Bulletin Deployment Priority
When you look at the deployment priority, Microsoft suggests to install the bulletins MS12-027 and MS12-023 first, then Ms12-024, MS12-025 and Ms12-08, before installing MS12-026. Why those two critical vulnerabilities first? Because the vulnerability that MS12-07 addresses is actively exploited, while Ms12-023 is covering an industry-wide issue.
Microsoft Security Bulletins For April 2012
- MS12-023 - Cumulative Security Update for Internet Explorer (2675157) - This security update resolves five privately reported vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-024 - Vulnerability in Windows Could Allow Remote Code Execution (2653956) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user or application runs or installs a specially crafted, signed portable executable (PE) file on an affected system.
- MS12-025 - Vulnerability in .NET Framework Could Allow Remote Code Execution (2671605) - This security update resolves one privately reported vulnerability in Microsoft .NET Framework. The vulnerability could allow remote code execution on a client system if a user views a specially crafted webpage using a web browser that can run XAML Browser Applications (XBAPs). Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. The vulnerability could also allow remote code execution on a server system running IIS, if that server allows processing ASP.NET pages and an attacker succeeds in uploading a specially crafted ASP.NET page to that server and then executes the page, as could be the case in a web hosting scenario. This vulnerability could also be used by Windows .NET applications to bypass Code Access Security (CAS) restrictions. In a web browsing attack scenario, an attacker could host a website that contains a webpage that is used to exploit this vulnerability. In addition, compromised websites and websites that accept or host user-provided content or advertisements could contain specially crafted content that could exploit this vulnerability. In all cases, however, an attacker would have no way to force users to visit these websites. Instead, an attacker would have to convince users to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes users to the attacker's website.
- MS12-027 - Vulnerability in Windows Common Controls Could Allow Remote Code Execution (2664258) - This security update resolves a privately disclosed vulnerability in Windows common controls. The vulnerability could allow remote code execution if a user visits a website containing specially crafted content designed to exploit the vulnerability. In all cases, however, an attacker would have no way to force users to visit such a website. Instead, an attacker would have to convince users to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes them to the attacker's website. The malicious file could be sent as an email attachment as well, but the attacker would have to convince the user to open the attachment in order to exploit the vulnerability.
- MS12-026 - Vulnerabilities in Forefront Unified Access Gateway (UAG) Could Allow Information Disclosure (2663860) - This security update resolves two privately reported vulnerabilities in Microsoft Forefront Unified Access Gateway (UAG). The more severe of the vulnerabilities could allow information disclosure if an attacker sends a specially crafted query to the UAG server.
- MS12-028 - Vulnerability in Microsoft Office Could Allow Remote Code Execution (2639185) - This security update resolves a privately reported vulnerability in Microsoft Office and Microsoft Works. The vulnerability could allow remote code execution if a user opens a specially crafted Works file. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
 Alternative Download locations
The security updates have been uploaded to Microsoft's Download Center from where they can be downloaded.
Advertisement




















Sorry Martin, I can see the Silverlight/microsoft video in main outer browser.
That’s great ;)
Hoi Martin, First many thanks for this mount update explanation.
Ferry handy indeed.
I have a question for you I do not see the Silverlight video?