Zero-Click Bluetooth Attack: A Growing Threat for Unpatched Android Phones

A security researcher, known as 'Mobile Hacker', has shown how vulnerable unpatched Android phones are. In their demonstration, they revealed a potentially devastating zero-click attack that exploits newly uncovered Bluetooth vulnerabilities to install intrusive payloads via Metasploit, a popular penetration testing framework, onto devices that haven't received their latest patches.
'Mobile Hacker' used proof-of-concept (PoC) exploitation scripts which were released by Marc Newlin earlier this month. These scripts are freely accessible on GitHub and take advantage of the weaknesses tracked as CVE-2023-45866, CVE-2024-21306, and CVE-2024-0230 (more info). They effectively force-pair emulated keyboards through Bluetooth to different OS architectures, thereby enabling keystroke injection.
What's truly alarming about these scripts is they work on devices where Bluetooth is enabled and active, meaning they're in an unlocked state. The attack can spring from another mobile device within Bluetooth range without requiring any interaction with the victim or leaving any noticeable signs of a breach. This vulnerability highlights the importance of keeping our devices updated and vigilant against potential threats lurking in our digital space.
These attacks are as stealthy as they sound and can impact unpatched Android phones. Let's dive deeper to understand this modern menace.
Zero-click attacks, for those who may not know, are cyber threats that don't require any interaction from the victim - no clicking on suspicious links or downloading rogue applications. The hacker needs proximity to execute these nefarious actions via Bluetooth. The vulnerability in question impacts a range of operating systems across different devices but it's especially concerning for older Android versions.
Why is this so? Well, consider the fact that most Android vendors stop supporting devices after only two years and follow infrequent updating circles (quarterly at best). This means security updates get delayed sometimes for months making these devices ripe targets for hackers exploiting Bluetooth vulnerabilities.
To give you a clearer picture, all Android devices running version 10 and older are vulnerable to these Bluetooth flaws. They're essentially sitting ducks for zero-click attacks unless patched immediately. As for newer versions like Android 11 to 14 which have active support, the flaws were addressed in the December 2023 patch.
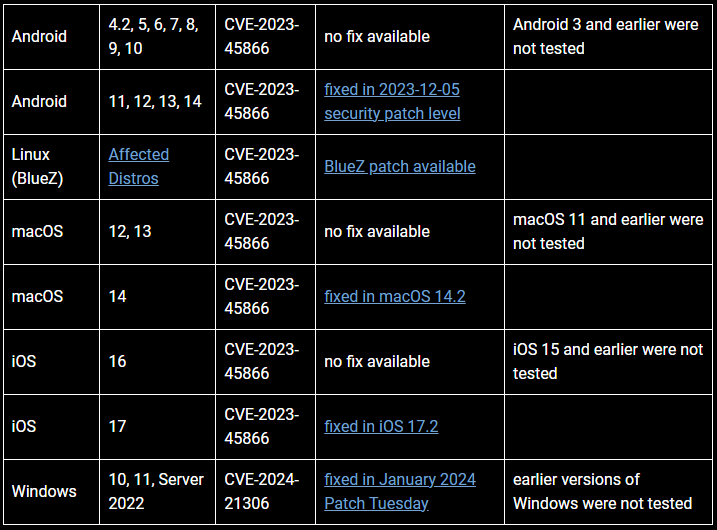
Unlike their Android counterparts though Apple's iPhones had their flaws fixed by iOS update 17.2 but left previous versions used by older models exposed. MacOS fixed its flaw in version 14.2 while Microsoft issued fixes for Windows 10,11 and Server 2022 in their January 'Patch Tuesday' release of updates in 2024. Older macOS versions like 12 and 13 are vulnerable, and no fixes will be made available.
If you are unable to upgrade to a safe version I recommend either disabling Bluetooth or keeping their phones locked when in public spaces with many people nearby.
Advertisement



















No worries for me. I have a Google Pixel 8 Pro that gets the latest security updates monthly. My Samsung tablet that I have may see a security update in a few months from now but it hardly gets used.
This is why I only buy the cheapest of Android devices. $150 or $1,000 — Either way the manufacturer isn’t going to give a damn about patching them two years from now.
“As for newer versions like Android 11 to 14 which have active support, the flaws were addressed in the December 2023 patch.”
Active support by who? Does Google push critical security patches for all Android devices?
I have an Android 12 device which has long been abandoned. They don’t even release security patches and that December 2023 patch will never happen.
Google provides patches for supported Android versions. It’s on your device manufacturer to actually incorporate them into new ROMs and give them to you. At least, this is the way it works for system-level vulnerabilities, like in the kernel.
But vulnerabilities in apps, on the other hand, can be automatically addressed via Google Play.
Note the important bit, that just because Google is patching still-supported versions of the underlying Android platform, does not guarantee that your device manufacturer will provide them to you in a timely manor, or even at all.
Mike, I know. The vast majority of Android phones will remain unpatched, contrary to what the article implies. For Android 11-12 devices, at least.
Google should focus on installing Android in such a way, that these patches would apply for most, if not all devices. A solid, tight OS core or something like that. The device-manufacturer part of the OS should be kept as separate as possible.
Don’t know how feasible it is, but things need to improve here. 2/3-year support is ridiculous.
Samsung and Google’s own devices. That’s it.
I use a 2023 OnePlus android running OS 14. How do I know if it’s been patched? The article didn’t give any recommendations other than keep your device up-to-date.
I have s10e and did not get the patch. it says my phone is up to date. (last update march 10 2023). I generally turn off wifi and bluetooth to conserve battery and because my phone still has a 3.5mm audio jack.
Apparently samsung ended support sometime last year. too bad because it seems they did not even do QA testing.
Unlike pc where you can run decade old hardware with new update software (except windows apparently). these wanker phone manufactures are doing their damnest to force people into buying new hardware. Despite google “supporting” these older versions, it does not even matter when manufactures have the ultimate say. I loath mobile manufactures.
I rarely use Bluetooth, but when I do, I always turn it off after I’m done with it.