Its Groundhog Day at Microsoft! Vulnerability patched again

Remember the movie Groundhog Day? Bull Murray plays a rather self-centered weatherman who finds himself in a time loop on Groundhog Day.
Windows administrators may have similar feelings to Murray's in regards to vulnerability CVE-2021-43890. First patched in December 2021, Microsoft announced in December 2023 that it has detected attacks in the wild and patched the issue again.
If that sounds confusing, it is. What Microsoft failed to mention is that the first patch has somehow been undone since April 2023.
Appx installer spoofing vulnerability in Windows
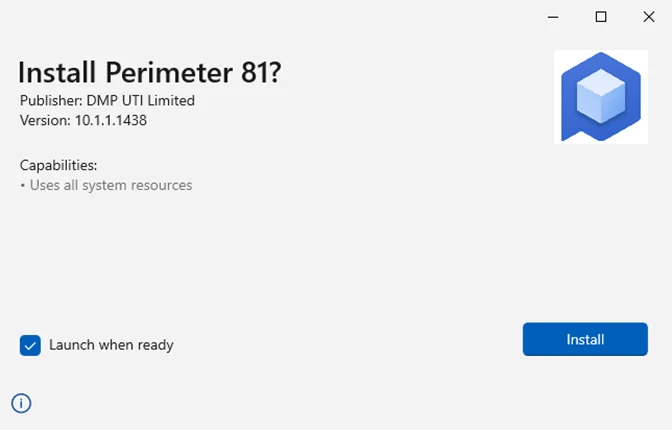
The vulnerability report refers to the issue as a spoofing vulnerability in Appx installer in Microsoft Windows. Microsoft developed the ms-appinstaller Uniform Resource Identifier to support the downloading and installation of apps directly from Internet servers.
In other words: users who clicked on ms-appinstaller links would get an installation prompt similarly to the one displayed on the screenshot above.
While it still required the user to hit the "install" button, the lack of a prominent "cancel" button led to unwanted installations. A click on the x-icon at the top of the window cancelled the process.
Activation of install would download and install the malware on the device.
Microsoft describes the process in the following way: "Users who click the links to the installers are presented with the desktop App Installer experience. If the user clicks “Install” in the desktop App Installer, the malicious application is installed and eventually runs additional processes and scripts that lead to malware installation."
Microsoft's blog post on its Security blog reveals that it observed several attacks that make use of App Installer to infect Windows devices. The functionality is disabled by default according to this Microsoft support page. Administrators may enable it, however. What Microsoft fails to mention in the post is that it disabled the functionality in December 2021 already as a reaction to abuse of the functionality.
Will Dormann was among the first to spot this missing piece of information in Microsoft's announcement.
What Microsoft also does not reveal in its announcement is when it disabled the functionality by default. Günter Born thinks that the December 2023 security updates are the most likely option, but Microsoft never revealed this. Born found a single reference on the web by a Microsoft Answers user who got the "cannot open app package" error message when trying to install an app using the ms-appinstaller protocol.
The description informs the user that the protocol has been disabled.
System administrators may want to read through Microsoft's entire post on the Security blog. It includes information about three malwares that used the vulnerability as well as a long list of recommendations.
Apart from making sure that App Installer build 1.21.3421.0 is used, Microsoft recommends the following mitigations:
- Deploy phishing resistant authentication methods.
- Implement conditional access authentication strength.
- Educate Microsoft Teams users and apply best security practices for Microsoft Teams.
- Educate users to review sign-in activity and mark attacks.
- Make users use Microsoft Edge or another browser that supports Microsoft's Defender SmartScreen technology.
- Educate users about clicking on links and verifying link targets.
- Educate users that they double-check software that is installed, e.g., to make sure the publisher is legitimate.
- Configure Microsoft Defender for Office 365 to recheck links on click.
- Enable several security features.
More than half of Microsoft's suggestions are about educating users.
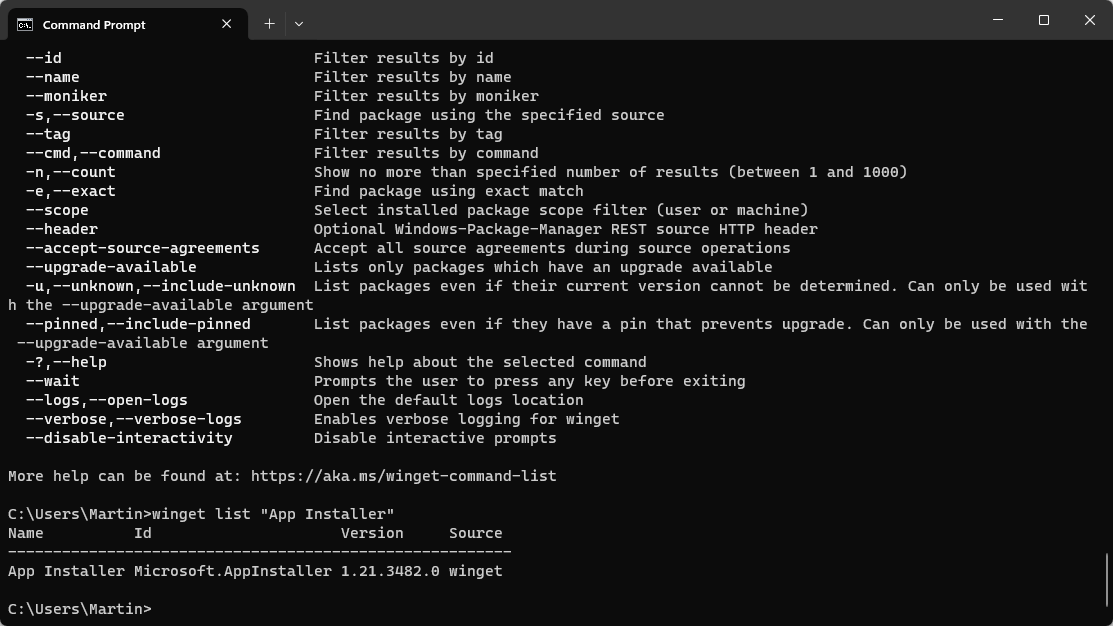
You can check the AppInstaller version in the following way:
- Open a command prompt window, e.g., by opening Start, typing cmd and selecting Command Prompt from the options.
- Type winget list "App Installer" and press the Enter-key.
Check the version that is returned. You can upgrade the application using the command winget upgrade Microsoft.AppInstaller.
Now You: have you used App Installer in the past to install apps?





















The winget tool is part of the App Installer.
You can install winget by installing the App Installer from the Microsoft Store.
If you see App Installer needing an update from the winget command, winget needs to be updated.
You can update it from winget or the MS Store.
To see which version you are running, type
winget -v
The latest version of winget/App Installer is 1.21.3482.0
@Anybody
Why do a bunch of the shortcuts on my start menu now have the word “system” added to them?
Why was this done, how was this done?? Does the underlying code in this change do other things too?
So Microsoft’s solution now is handed off to the end user. Honestly I have never seen Microsoft so degraded as they are today.
Absolutely nonsense. Microsoft’s employees are finishing this year making what they do better: nothing good. :[