LogoFail vulnerability affects many Windows and Linux devices

Many commercial computers are vulnerable to a set of vulnerabilities that exploit flaws in the processing of startup logos during boot.
Security researchers at Binarly have disclosed security vulnerabilities in system firmware used by computer manufacturers during the boot process. The vulnerability impacts x86 and ARM-based devices.
The set of vulnerabilities is found in BIOS software created by different companies, including the three largest independent bios vendors AMI, Insyde and Phoenix. These are widely used in the industry, for instance in computers by Intel, Acer or Lenovo. Alex Matrosov, CEO at Binarly, says that about 95% of all computers use firmware from the three bios vendors.
Binarly says that it estimates that almost any device produced by these vendors is vulnerable "in one way or another".
In simple terms, LogoFail exploits vulnerabilities in image parsers that affected devices use to display vendor logos during boot. Different image parsers are used to display different image types, and "they are rife with vulnerabilities" according to Matrosov.
A hacker needs to replace the vendor image with a specially prepared one to exploit the vulnerability and execute arbitrary code on the machine. Binarly explains that attackers may store malicious logo images on the EFI System Partition or inside unsigned sections of a firmware update. The images are then parsed during boot and this initiates the attack on the device.
The attack allows attackers to bypass security features such as Secure Boot. Binarly notes that this also affects hardware-based Verified Boot systems, including Intel Boot Guard, AMD Hardware-Validated Boot and ARM TrustZone-based Secure Boot.
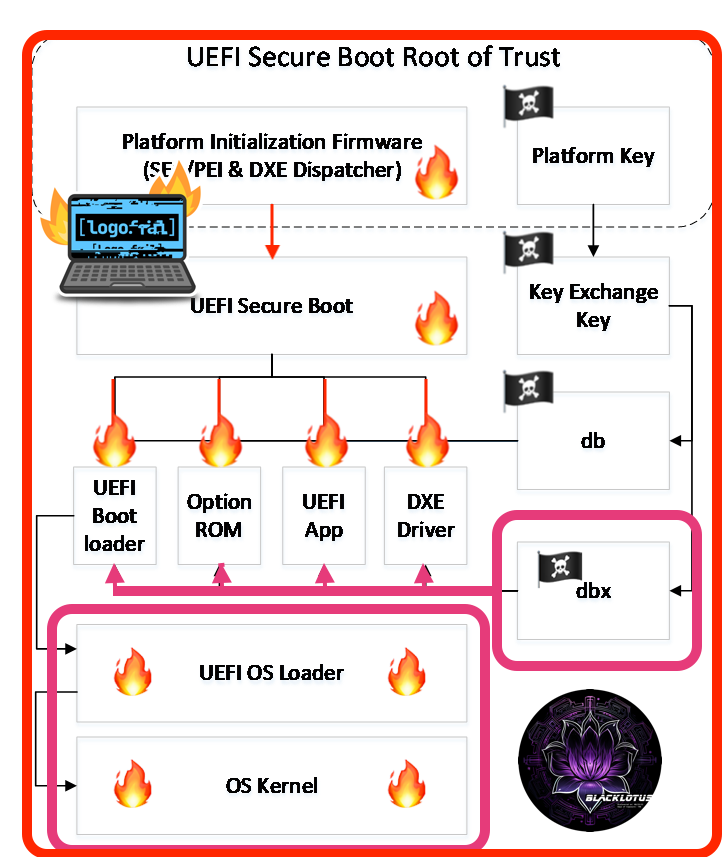
Binarly believes that the attacker may be able to bypass "most endpoint security solutions" and integrate a persistent stealth firmware bootkit on the system. In other words, attackers may exploit LogoFail to compromise the security of many computer systems.
Attacks and protection
Attackers need to gain administrative access on target devices to exploit the vulnerability. This can be achieved through malicious payloads planted on the system, for instance by getting the user to run malicious software, or through exploits.
Once access is gained, the attacker would replace the vendors boot logo with a malicious logo, which the device would then load during boot.
An attacker would be able to disable UEFI security features, such as SecureBoot, modify the boot order and execute malicious software to infect operating systems.
Firmware updates are available or will be released for some of the affected devices. Administrators may want to check for firmware updates for devices that they manage that address the vulnerabilities. Not all devices will receive firmware updates, however. Especially devices that are no longer in support may not receive them.
A search for "device name firmware update" or "device name drivers" should return the driver download website of the manufacturer of the device.
Users on devices without firmware updates need to be extra cautious and use protections to avoid the initial attack on the device (which needs administrative access).
Additional information about the vulnerability is found on the Binarly website and on the CERT database.


















Most BIOS’es have an option to disable the logo splash; I’m wondering if disabling the splash screen also disables this hack possibility.
The vectors for inserting malicious code are more numerous than you might think.
As a preventive measure, is there a tool for observing changes in UEFI memory ? (That would be the minimum…)
I don’t think it is fearmongering when researchers find vulnerabilities in any given system, such information is valuable to people who can decide to take a calculated risk or take the security update. This is why FOSS is so safer than proprietrary, even if there is more flaws found in FOSS than proprietrary, at least they are highlighted which is not the case for propietrary as they could even have more flaws.
Sometimes taking the security update can brick or slow down your system, the choice should be up to the users to weigh up.
The least risky security exploits to have in your system are the ones where a would be hacker needs physical access to the machine physically, those ones are not really critical security flaws if your machine is away from people you don’t trust.
However, close proximity attacks are a real security risk where someone can exploit a machine a few metres away, or machines where if they get the admin password they pwn you.
A good admin password should always have at least 128 bits of entropy security. Also it is good practice to never use an admin account in any OS casually. People should use a standard non-admin account as the main driver for everyday use, because if you download a malicious program, usually the damage is quite limited.
Always strive to use FOSS as much as possible, it is just safer by design.
@Bobo
Plastic keys can already be hacked.
It is possible to log a user’s keystrokes of a nearby keyboard by listening to the electrical sound that their device screen makes, all they would need is a malicious code on the target machine and a smartphone mic a few metres away.
That is old news, and is why military computers usually feature shielding in their construction materials and are much more robust and expensive than a normal consumer product.
Even an air-gapped PC is not 100% safe when turned on, if it formally had malicious code on it, it could be open to other attacks like the sound of keystrokes picked up by a smartphone mic that could steal passwords.
James bond type spying is not as far fetched as people think it is.
This fearmongering is getting ridiculous. No computer will ever be “hacked” this way in real life. What’s next, vulnerable plastic keys on the keyboard? Exploitable vulnerabilities in the laptop screen itself? Global warming?
It’s really easy to install a modified BIOS image though, you don’t need physical access to do it. It could be done all in software as you’re running your OS.
You underestimate how willing the average user is to granting admin access
So, someone must first hack and gain access to your pc before they can use this hack?
If your still using x86 hardware you shouldn’t be exposing it to the internet anyways.