Microsoft Teams vulnerability discovered to bypass file sending restrictions

A newly discovered vulnerability in Microsoft Teams allows attackers to push malware onto the devices of other Microsoft Teams users, even if they are considered external.
IT security researchers at Jumpsec have discovered a new vulnerability in Microsoft Teams. The vulnerability may be exploited to bypass traditional security protections, e.g., against phishing or malware, to push malicious files to the devices of Microsoft Teams users.
Microsoft Teams allows communication requests from external tenants in its default configuration. Microsoft Teams distinguishes between internal and external users. Users from an organization are considered internal, while users from outside of the organization external. External users may contact internal users through Teams by default, but Microsoft implemented protections to prevent attacks.
It is, for example, not possible to send files from an external account to an internal account. Messages may be sent however and Microsoft Teams informs users if a request comes from an external source. Messages may not contain files when they come from external sources.
Jumpsec discovered a vulnerability in Microsoft Teams that allows external users to send files directly to internal users. The files are displayed alongside the message, which can be a specially crafted message to get the target to open the file on the machine.
The researchers explain: "Exploitation of the vulnerability was straightforward using a traditional IDOR technique of switching the internal and external recipient ID on the POST request [..]".
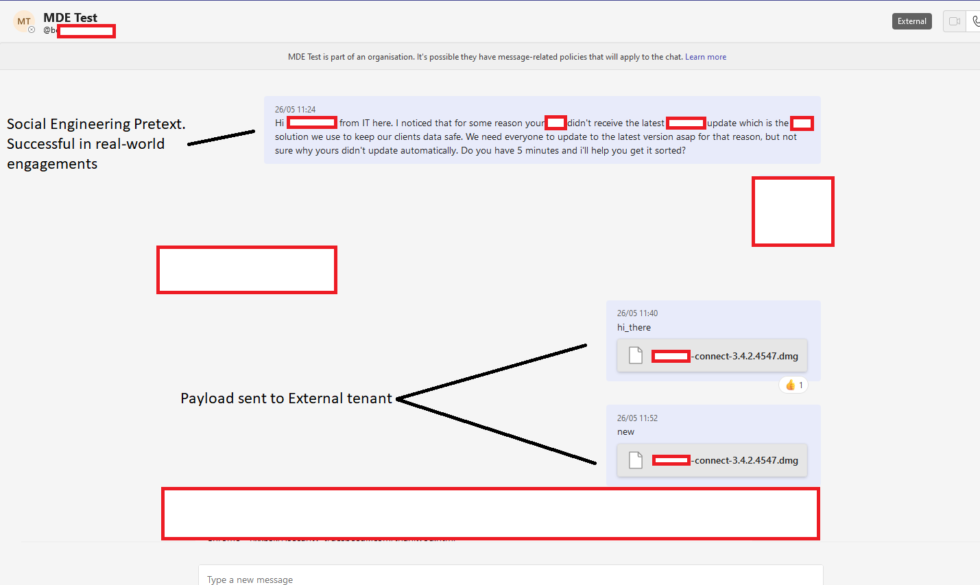
The file that gets delivered is hosted on a Sharepoint domain, but the inbox of the target displays it as a file, not a link. The file is downloaded when the user activates it.
Jumpsec notes that the vulnerability is a " potentially lucrative avenue for threat actors to deliver payloads" as it bypasses anti-phishing security controls. An attacker would have to buy a domain and register it with M365, but they would not have to use "mature domains, with web servers, landing pages, CAPTCHAs, domain categorisation, and URL filtering".
Impact of the Microsoft Teams vulnerability
The vulnerability affects all organizations that use Microsoft Teams in the default configuration. Organizations may mitigate the issue by disallowing external users from sending messages to staff members.
This is found under Microsoft Teams Admin Center > External Access. Not all organizations may be able to disable this option, as they may require communication with external tenants. These organizations may use the allow-list to add domains from these organizations so that communication from all other domains is blocked.
Monitoring of external message requests is limited currently. The researches have detected an URI that may be monitored to detect when a Teams user accepts a request from an external source: /api/mt/emea/beta/userSettings/acceptlist/manage
Jumpsec reported the vulnerability to Microsoft prior to releasing the information. Microsoft confirmed its existence, but told Jumpsec that it "did not meet the bar for immediate servicing" according to Jumpsec.
Closing Words
System administrators may want to limit external communication options in the Microsoft Teams administrative interface to mitigate the vulnerability.


















@Martin, please look at this report by Cloudflare:
https://radar.cloudflare.com/quality
It’s quite interesting, Spain #1 in speed!
1. Spain 276.9 Mbps
2. Hungary 245.6 Mbps
3. Israel 244.7 Mbps
4. Chile 240.1 Mbps
5. South Korea 236.1 Mbps
6. Vietnam 219.3 Mbps
7. Portugal 212 Mbps
8. Denmark 211.2 Mbps
9. Romania 209.4 Mbps
10. Canada 200.3 Mbps
11. Brazil 199.2 Mbps
12. New Zealand 197.5 Mbps
13. United States 194.1 Mbps
14. Norway 186.9 Mbps
15. Netherlands 179.5 Mbps
How is the UK’s infrastructure so shitty? 100 Mbps on average, wtf…
> These types of exploitations should be mitigated through MS Defender as well.
This issue is a vulnerability specific to “Teams”, so it is a matter of concern when using Teams (especially when organizations such as companies, schools, and associations share tools).
Malicious intrusions through specific programs (such as Teams) are a difficult class to detect with anti-malware solutions (MS Defender or third-party anti-malware programs).
Rather, it is a vulnerability that “administrators of systems in organizations” must be pay attention and take action, and it is a vulnerability that is far from home users at the individual level.
These types of exploitations should be mitigated through MS Defender as well.