Microsoft Defender gets better at preventing Windows passwords from being stolen
Microsoft is strengthening Windows' security by adding a very important rule to its antivirus. A new ASR rule is being introduced to Microsoft Defender.
Before we get into it, let's talk about a method that hackers can use to steal a user's Windows password.
What is LSASS?
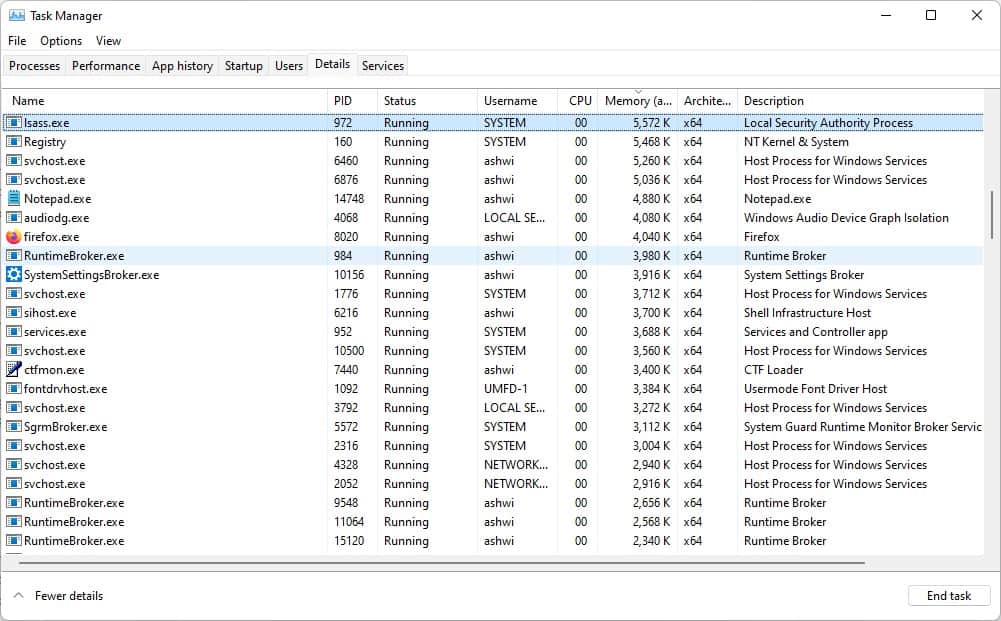
You may have noticed LSASS.exe in your Task Manager, it is related to a process called Local Authority Server Service. LSASS authenticates users who log on to a computer, and is protected by Microsoft Defender's Credential Guard. The issue with it is that Credential Guard is not compatible with all programs, e.g. custom smartcard drivers. So, it is not implemented in all environments.
When an attacker has breached a user's computer, they can easily gain access to the LSASS process via special tools like Mimikatz. The resultant file created by the tool, is a memory dump that contains the passwords and usernames of the users who were logged in to the system.
The passwords are displayed in plain-text, thus allowing the attacker to gain full access to the operating system. And all this can be done remotely, and Microsoft Defender will not block access to it because LSASS is a legitimate process and its memory dump is not harmful. It can only detect programs that are maliciously accessing the process, but can't prevent the memory dump from being created, or transmitted to steal the user's credentials.
That's pretty scary, isn't it.
Microsoft Defender gets an Attack Surface Reduction rule
The solution to this security issue is quite simple, protect LSASS from unauthorized access, and this whole mess can be avoided, right? That is precisely what the Redmond company is doing, by adding a new rule called Attack Surface Reduction (ASR). This rule will block programs from opening LSASS and in turn also prevents them from creating the memory dump. It will block access to LSASS even if a program that has elevated rights, i.e., administrator privileges, tries to open the process.
It gets better, according to Microsoft's documentation, this ASR rule will be enabled by default, while all other rules related to it will remain in their default state "Not Configured".

Is ASR a good solution? Well, if you're Microsoft Defender, this does look promising. It is not completely fool-proof though, but what is. We have to remember that malware are also evolving, and becoming complex year-after-year.
On the other hand, if you are using a third-party antivirus on your computer, the ASR rule is disabled. So, that makes the LSASS vulnerable again. Bleeping Computer reports that the ASR rule has already been bypassed by some security researchers, who exploited Microsoft Defender's exclusion paths. The exclusions apply to all ASR rules, and since this LSASS access falls in the same category, it makes it possible for hackers to bypass the restrictions. The report mentions that users running on Windows Enterprise, Windows 10 Pro and Windows 11 Pro will be protected by the new ASR rule.
That said, the new ASR rule has been welcomed by security researchers, as it makes Windows a little more secure, and that's always welcome as it will result in fewer stolen passwords.
On a side note, Microsoft Defender Preview is a new dashboard that lets you manage the security of your devices.


















Heh. “Not necessary if you know what you’re doing”. That’s cute, I’m gonna mention it during lunch today at work, everybody’ll get a kick outta it.
But seriously, I work with the MS 365 Defender Suite everyday as it’s our company’s primary Cyber Defense, I can offer up some non-speculative info that answers a bunch of what has been asked/claimed.
-What Defender does with your data-
We have an SLA with Microsoft for Defender, obviously, and I had the joy of trying to stay awake while our lawyers explained it to all us C-Level executives. It’s actually one of the most privacy respecting services in the Enterprise Class Security Sector. Depending on where you operate from (US, Ireland, Germany, Japan, UK, etc), your data is sent encrypted in-transit to an Azure Datalake that resides in your region and is compliant with the laws for data privacy governing said region. Data is retained, encrypted at rest, for a fixed period of 180 days, after which it is purged (of course all companies connect to Defender and have it send a copy of that data to their SIEM for long term storage and use). Businesses have the option of enabling the complete redaction of ALL Personally Identifiable employee data (strips all IPs, Hostnames, DNS queries, Servers interacted with, file names are replaced with the hash, any First or Last Names get removed, literally any data that could be used to ID a person or device and any activity performed by them is wiped locally on the client before being securely sent to the MS Intel Grid. ** Surprisingly, this is the default mode that non-business “free” Defender consumer data gets processed in. **
Defender has a small set of 20-25 IPs per region that make up the endpoints dedicated to security use and they keep it strictly segmented from all other Telemetry/Diagnostics/Similar.
All free 3rd Party AV installs, like ESET, AVAST, Symantec, Bitdefender, et al, ABSOLUTELY DO use your personal data for monetization, and they all clearly state their rights to do as such in their Terms. Sorry to dissappoint anybody fantisizing that Microsoft is spying on them with Defender, but they aren’t. Their legally binding SLA’s and Licensing Terms make this a simple fact.
-ASR, Anti-Exploit, Credential Guard-
First off, I should probably clarify and correct what Ashwin stated in this article, namely that this is NOT a new ASR Rule, or feature being added to Defender, not at all. Its been around, unchanged, for at least 3 years, probably a bit longer. The Defender Attack Surface Reduction Module/Ruleset is comprised of 20+ Mitigation Defensive Policies that are all turned off by default in Windows Pro and Ent (Pro has 10-15 I believe, Ent. has about 20, and Defender 365 has them all). All MS is doing is Configuring a Group Policy/Registry Entry to be enabled in Block Mode as the new default for that GUID/ASR Rule. This protection is NOT unique to MS, every Enterprise Class XDR/EDR solution provides their own method of guarding the LSASS process from attack. However, none do a better job than MS does, some do as well as, but complete mitigation of the threat of Credential Theft in this manner is as good as it can get.
As for the notion that it can be circumvented, that’s not really true. ASR Exclusion rules do exist, of course, but MS allows you to enable the Tamper Proof mechanism in Defender than locks down the configuration from the Cloud and completely ignores any ASR Exclusions that are created on the endpoint. I’m fairly sure that any ASR Exclusions created by end users will not apply to the Credential Guard GUID, which will guarantee protection.
Some other ASR Rules that you can (and should) enable include those such as, Prevention of All Office Apps from spawning child processes, Termination of Malicious VBA/WMI Scripts, Protection from malicious code injection into your Firmware, Blocking execution of unknown code from an attached USB device, Termination of any JS/Macro/Embedded Script execution from an opened Office Document/File Type, Blocking Adobe PDF Reader from creating a child process, to name just a few.
-Defender Uses Up too much CPU/Resources-
It used to, yes. Of course, that was only accurate if you were comparing it to 3rd Party end-user AV that’s either free or costs only $50 a year and can’t protect against ANY Next-Gen Malware, let alone an actual targeted attack on your network. I’ll compare it to CheckPoint’s Harmony Endpoint Protection (Formerly called SandBlast and SandStorm Protection), it’s inexpensive at only $40 per month per agent deployed (protects 1 OS on 1 Computer) with a minimum subscription of 50 agents. A single Full computer scan of my machine (29TB of Storage across 11 drives, 24TB of Used Space, my C:\ Volume is only 40GB Used Space on a 256GB SSD. All NON C:\ Storage is occupied by TV/Film (Video files), Photos/Images, and Music (MP3/FLAC Audio) not one binary file stored off of C:), completed scanning after 27 hours averaging a CPU load of 70%. This is only 8 months ago, it actually scanned all files despite the fact that only 40GB of the 24TB scanned was even capable of being a threat. By comparison, Defender completed a FULL Computer Scan in only 2hr 17m, while a Quick Scan clocks in at 2-3 minutes. If that high CPU use (expect 50% unthrottled) for 3 minutes or 2 hours for a Full Scan 1-2x a month is unbearable MS already addressed that in full, even on end user machines. There’s a Group Policy you can set telling Defender the most CPU it can use and what it should generally run at in a active scan. It will happily scan at 20% CPU if you desire, you won’t even notice how long it takes. They also added a defference Policy that you only have to enable. If it was about to scan or is scheduled to and is see you have 5 browsers open along with photoshop while watching Netflix or something it will defer and do the scan X hours later once you’re done for the day. It also factors GPU and Memory use to make sure it does nothing while you’re gaming, and if a attack occurs while you are, it still respects the limiters you set and offloads more mitigations to the Cloud to handle so as to deter an attack in full without causing your FPS to stutter. It’s the least intrusive and lowest maintainence offering by far. 3 years ago Defender was an hones to god Joke. As is today, they rank in the top 5, and general concensus in the CyberSec community has them on a fast track to take PaloAlto’s #1 spot 2 or so years from now.
-No Harm in Mentioning It-
In January, MS put into closed preview a solution for Small (Self-Employed) to Medium (20-50 employees) businesses as well as High Value Home Networks called “Microsoft Defender for Business (Preview)” which falls somewhere between their Defender E3 and E5 tier offerings and they’re looking for users to fill up the Preview slots for at least 90-days minimum, 100% free of course, it’s not a secret or anything, you can find it in MS Docs as of like 2 weeks ago with a link to apply for a free invite code to participate – its intent is for a person with little to no IT expertise to have no issues setting up and deploying and using it on a few or few dozen machines without need of a dedicated IT department or SOC (Security Ops Center) which not every business can afford. Dunno how many solts there are, but it’s first come first serve, as stated in the MS Docs for it. Maybe that could fit someones need here.
Windows Defender is a backdoor just like CSAM. Its scanning all your files and fingerprinting.
I haven’t used any antivirus application since Windows 7. Its really not necessary if you know what you are doing.
Do third-party AVs also have similar ASR and anti-exploit protections in place, or is this some sort of unique Microsoft feature?
Using Defender since 2015, no single problem observed here. I was a former user of Norton, Avast, McAffe and Panda, no one of them beats Defender at least imho. However I like it the more because it’s free, the only AV I would pay for it’s Kaspersky. :]
Let us see the source code.
No?
Then begone, proprietary software! And take your convicted monopoly to hell down with you.
Do you know many good AVs that are open source? Unreasonable demands.
If you already run Windows Security (currently at 1.359.210.0), right clicking the WS taskbar icon “View security options” gives you clickable links to more information than most people would ever need or understand.
“View security options” should have read “View security dashboard”.
AV? No need, thanks to Linux for saving me from spyware Windoze
Windows Defender has been disabled on my computer. Very pesky and annoying software – deletes files without any notification.
The typical “no clue what i am doing” user. The typical noob that reads somewhere “I dont use Windows AV, i use some 3rd party one. It is far better…” and decides to do that also. Knowledge about it? None at all. So tired of these guys…
No AV running here at all. Haven’t ran one since like 2013 when they all started becoming cloud-based spyware. Defender spies even more than Avast, or anyone, and yet people still trust Microsoft. Who knows where your data is going? Read the EULA, your data belongs to Microsoft and you do not ask what they’re doing it with it, who it is being given to and sold to. It comes down to trusting Microsoft. You might trust Microsoft, I do not.
Read the independent anti-malware comparisons (not the sponsored ones). Defender performs well. So do a lot of others. This seems to give Defender an edge (no pun intended). It is a competitive world. You have to think 3rd party vendors will want to match the new Defender feature.
What I don’t like about Defender is the way it updates. I like to switch off Windows update until I am ready and more confident I wont introduce a “whoops” update into the OS (usually late in the month up to a day or two before Patch Tuesday).
I bought a PC in the fond hope it would work when I want, not just times other than when Microsoft decides they need to take up bandwidth at a time they want, “don’t shut down” at a time of maximum inconvenience, etc. Hence, I run a 3rd party AV.
@Anonymous (the one who wrote “Read the independent anti-malware comparisons”) Securitywise, Windows Defender is definitely competitive. Where it’s sadly not competitive yet is performance. Even today I still find it using 50% of all CPU for seconds when scrolling through folders with exe files. Icons still load at the speed of a diashow. Its performance is still among the worst in tests like on av-comparatives, which I can personally confirm too. Definitely a shame, because Windows Defender is the least annoying otherwise. But even in terms of RAM usage, Defender has gotten quite ugly in the past year. Meanwhile I can’t believe that Avast got even lighter, its only bloat being the excess UI processes. Avast Free is definitely very usable when doing multiple precautions: Only install the file module, tick off literally everything else. Forbid Internet access to everything except Instup.exe. Disable all data collection options in the options that you can find, also disable stuff like the virtualization and the cyber capture.
To give you a hint for Windows Defender and updates though, it does not strictly require Windows Update. You can either download a signature file from Microsoft by hand, or you can run this command:
“%programfiles%\windows defender\mpcmdrun.exe” -signatureupdate -http
I used Defender that way, before I became sick of its massive performance impact.
Windows Security is the least annoying AV, whatever you’re doing with your PC is definitely the issue here, buddy.
Microsoft doesn’t like what he’s doing with his PC. It’s not about viruses.
Nice improvement indeed, so long waiting for this. Thanks @Ashwin! :]