Microsoft suggests once again to disable the Print Spooler to protect against new 0-day vulnerability
Several Windows printing related vulnerabilities have been discovered, disclosed and resolved in recent time. Microsoft released an emergency update in July to address a vulnerability dubbed PrintNightmare.
This week, Microsoft disclosed yet another printing related vulnerability in Windows. The CVE reveals little information at this point as Microsoft's investigation is still ongoing.
According to the provided information, it is a remote code execution vulnerability that does affect the Windows Print Spooler.
A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
Microsoft does not list the affected versions and editions of the company's Windows operating system, as research is still ongoing. All versions of Windows were affected by PrintNightmare, and it is possible that the new 0-day vulnerability affects all versions as well.
Microsoft notes that it is working on a security patch, which it will likely release as an out-of-band patch once produced.
Workaround: disable the Print Spooler
Microsoft's workaround for protecting systems against attacks targeting the new Print Spooler vulnerability is to disable the Print Spooler. The downside to disabling the Print Spooler is that printing becomes unavailable.
One of the PrintNightmare vulnerability workarounds was to stop the Print Spooler as well.
Disable Print Spooler via PowerShell
- Open Start.
- Type PowerShell.
- Select Run as administrator.
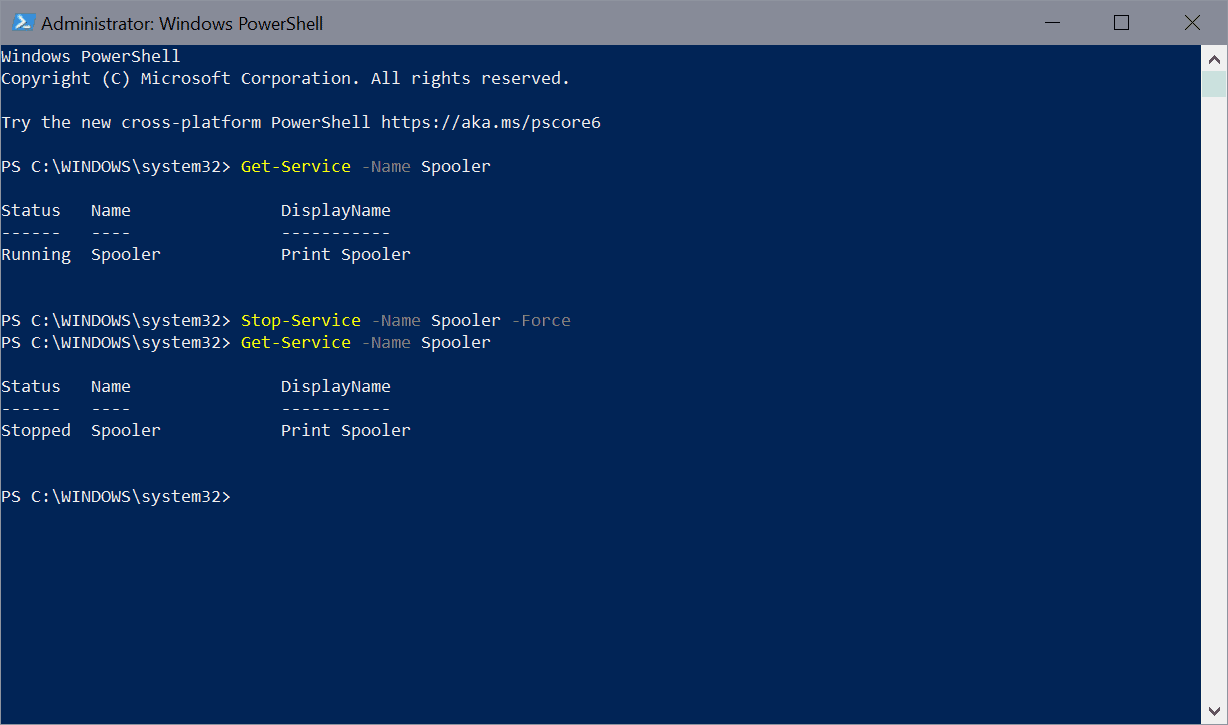
- Run Get-Service -Name Spooler to get the status of the print spooler-
- Run Stop-Service -Name Spooler -Force to stop the Print Spooler service.
- Run Set-Service -Name Spooler -StartupType Disabled to set the startup type of the service to disabled so that it is not activated on system start.
Disable Print Spooler via Services

You may also use the Services management interface to stop the Print Spooler service and set its startup type to disabled.
- Open Start.
- Type services.msc
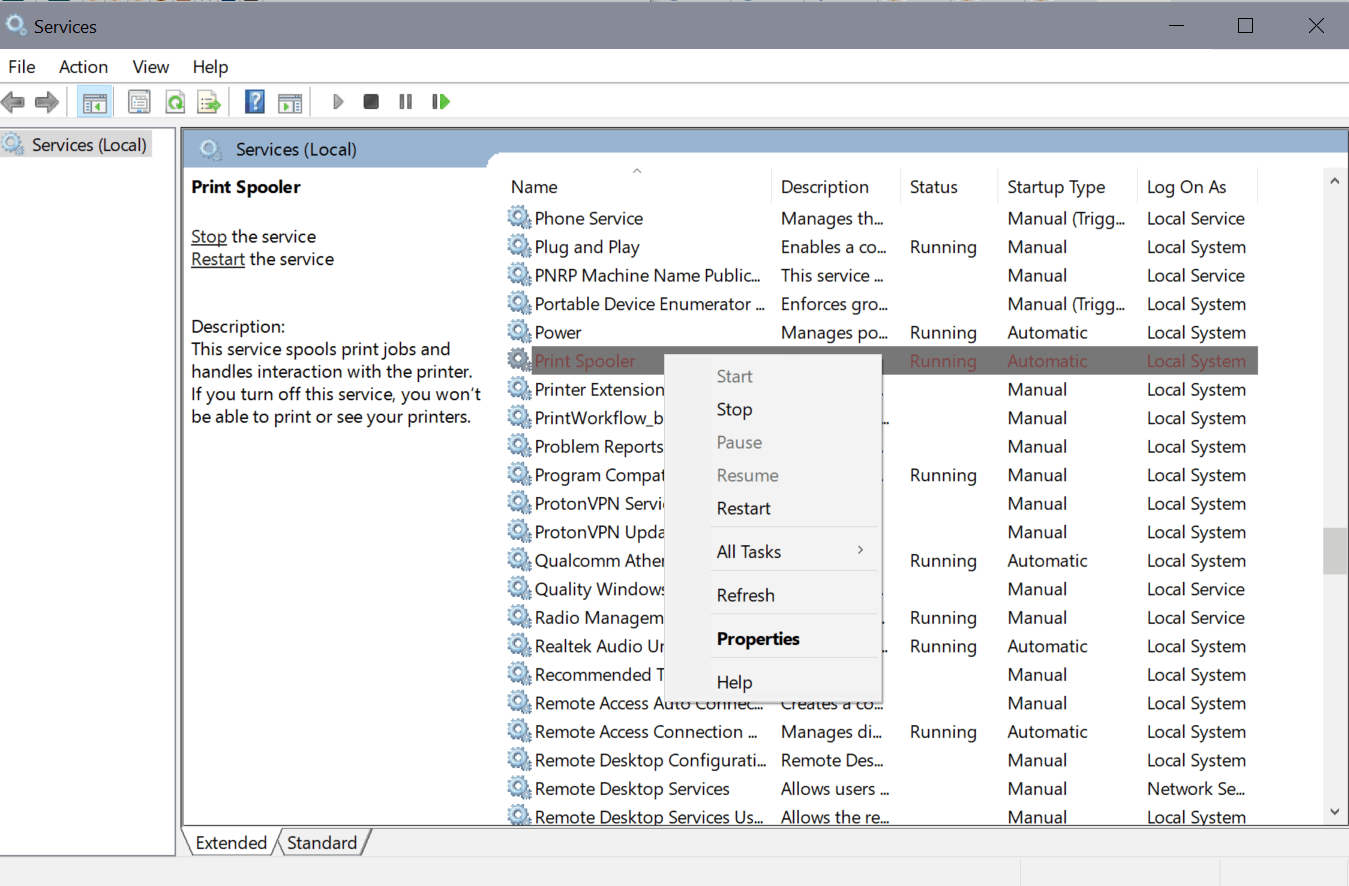
- Locate the Print Spooler service. The list is sorted alphabetically by default.
- Right-click on Print Spooler and select Stop.
- Double-click on Print Spooler.
- Set the Startup Type to disabled.
- Select Ok.
Effect of the workaround
You won't be able to print anymore on the device if the Print Spooler service is not running. You could enable it on demand, e.g. just the moment before you start a new print job on the device, and turn it off afterwards again.


















It’s time for Microsoft to release a big, red hard-coded desktop on/off toggle/shortcut for the Print Spooler service.
LOL LOL LOL
If you want to disable the Print Spooler with just one click you can use “Fix Print Spooler v1.2” – it is portable freeware.
https://www.sordum.org/9199/fix-print-spooler-v1-2/
Setting the service to manual instead of disabled allows you to ‘conveniently’ start and stop it from the task manager when you need to print and should be just as safe otherwise.
Makes you wonder how many more holes many more holes hackers will find in the print spooler. As with most problems, big users are most likely the target ahead of home users but probably not worth the risk of ignoring it when spooler is so easy to shut down and turn off.
There’s 10,000 other vulnerabilities in Windows still left to find and new ones created with each update. So get to work on those bug bounties you can make a fortune from all the bugs in Windows.
Vulnerable via the internet/browser, or through a local network? I can’t find the details. Elevated privileges but how are they accessed?
I miss my printer cable, Star SG-10 printer and those nice DB25 ports ‘n plugs…
“An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges.” I read somewhere that it is difficult enough to exploit this vulnerability, however thanks for the useful workaround @Martin! :]
I disabled it…I only use printing once in a while so no problem. Next time I go to print I’ll either have to remember its disabled or maybe a notice will appear that its off? Exciting!
Despite the fact that everyone my age is older than me…(LOL ) that said, since I’ve retired, I’m
more homely than ever, so,no need for a networked printer, especially wi-fi…. it’s USB direct from source.
Very minimal print jobs these days. Printer can go weeks w/out use so……
Win 8.1 – task mgr-services tab, I disable Print spooler and Printer extensions and notifications, I’m a bit over vigilant, that’s me. Of course only takes seconds to reverse
the process.
You can still print. The print job will go straight to your printer. Most printers have onboard RAM to spool the print job too. The windows print spooler is meant to take some of the load off of your printer and spool it locally. Too many print jobs all at once without the local windows print spooler can cause your printer to stall or not print. But if it is just you printing an occasional average size print job you should be fine. Just make sure your print drivers are working and installed.
That would work for me, but not for my wife. Per previous recommendations, I have disabled the print spooler “accept client connections” capability with the RegisterSpoolerRemoteRpcEndPoint registry item. This disables printer sharing capabilities, which are unnecessary if you have a networked printer. I suspect that the latest vulnerability also depends on the print spooler accepting client connections, so I’ll wait until there are more details before making additional changes.
What is the CVE?
Here it is: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36958
I went to this site and see, “Update: September 14, 2021 – We have completed the investigation and have released the September 2021 security updates to address this vulnerability.” OK, that’s good.
For about the last month, every time I reboot, the print and index services show “Disabled”. I have to manually enable them to “Automatic”, then start them. They work fine.
Is there a way to get these two services to start automatically every time I reboot?
Thanks Martin.
This is fantastic, especially in an office or a hospital. Printing is sooooo overrated anyway! Think of all the TREES you are saving!!!
Would setting the print spooler to Manual mitigate the services option Martin?
I think so, but it won’t help when it comes to printing. If you set the service to manual, no printers are recognized by Windows.
Imagine this at the times of Win3x, Win95, XP, 7, 8 … ‘would have initiated a planetary revolution! People then, especially before XP, were not addicted as they are nowadays, and at present, combined to the fact there is no alternative to Win10 accessible to the masses, people endure day after day Microsoft’s technical incompetence, together with their OS’ inquisition at every level.. more even: the very concept, architecture of Win10/11 is unhealthy : the OS is not correctly thought.
LOL! Poor, poor, MS. If only their code were open. Too bad, so sad.
Poor Poor user, if only you knew that development in malware for an operating system is proportionate to its popularity. And your open source OS is barely 2% of the Operating system market share with Mac 4 times more popular. I wonder which one of them is the actual poor poor OS ????