Brave 1.18 Stable launches with Brave Today, Global Privacy Control support, and more
Brave has released Brave 1.18, a new stable version of the company's web browser for desktop operating systems and Android. The new version of Brave introduces the recently reviewed Brave Today news system, support for the up-and-coming standard Global Privacy Control, and other features.
Brave installations should get updated automatically thanks to the browser's built-in updating functionality. Desktop users can select Menu > About Brave to check the version and run a check for updates. Loading brave://settings/help directly does the same thing.
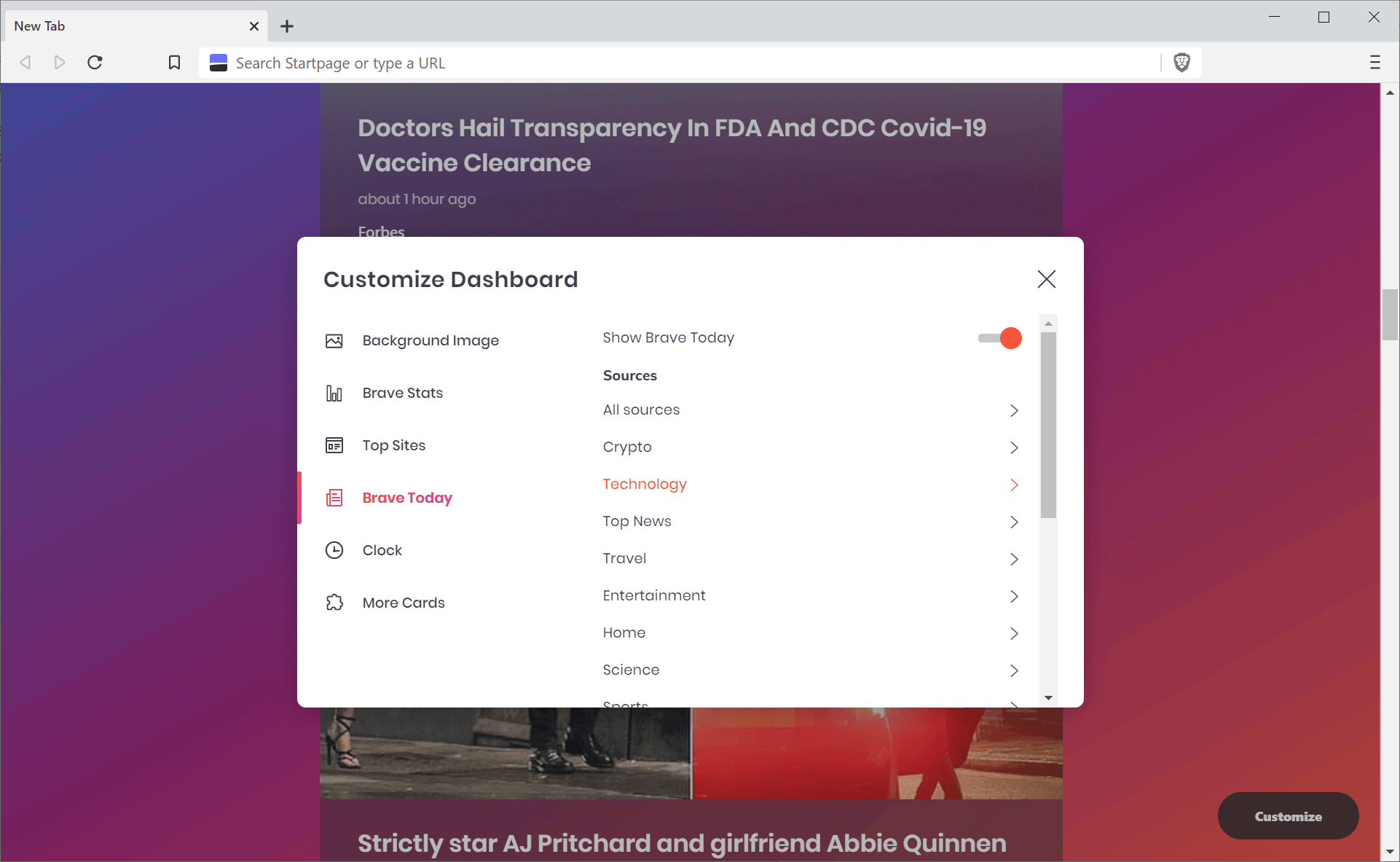
One of the first thing that users may notice, or not, is the new Brave Today addition to the browser's new tab page. It is enabled by default and all you have to do is scroll down to see a first selection of news displayed to you.

Brave Today collects news from news sources, the majority from the United States, pushes it on to its own content distribution network, to display titles and images to users. A click on customize displays options to enable or disable certain news sources in categories such as sports, finance, technology, or science.
The selection of news sources is quite good if you are from the United States, but if you are from anywhere else, you may find it lacking especially if you prefer non-English news sources. Users who don't plan on using it can turn it off easily though.
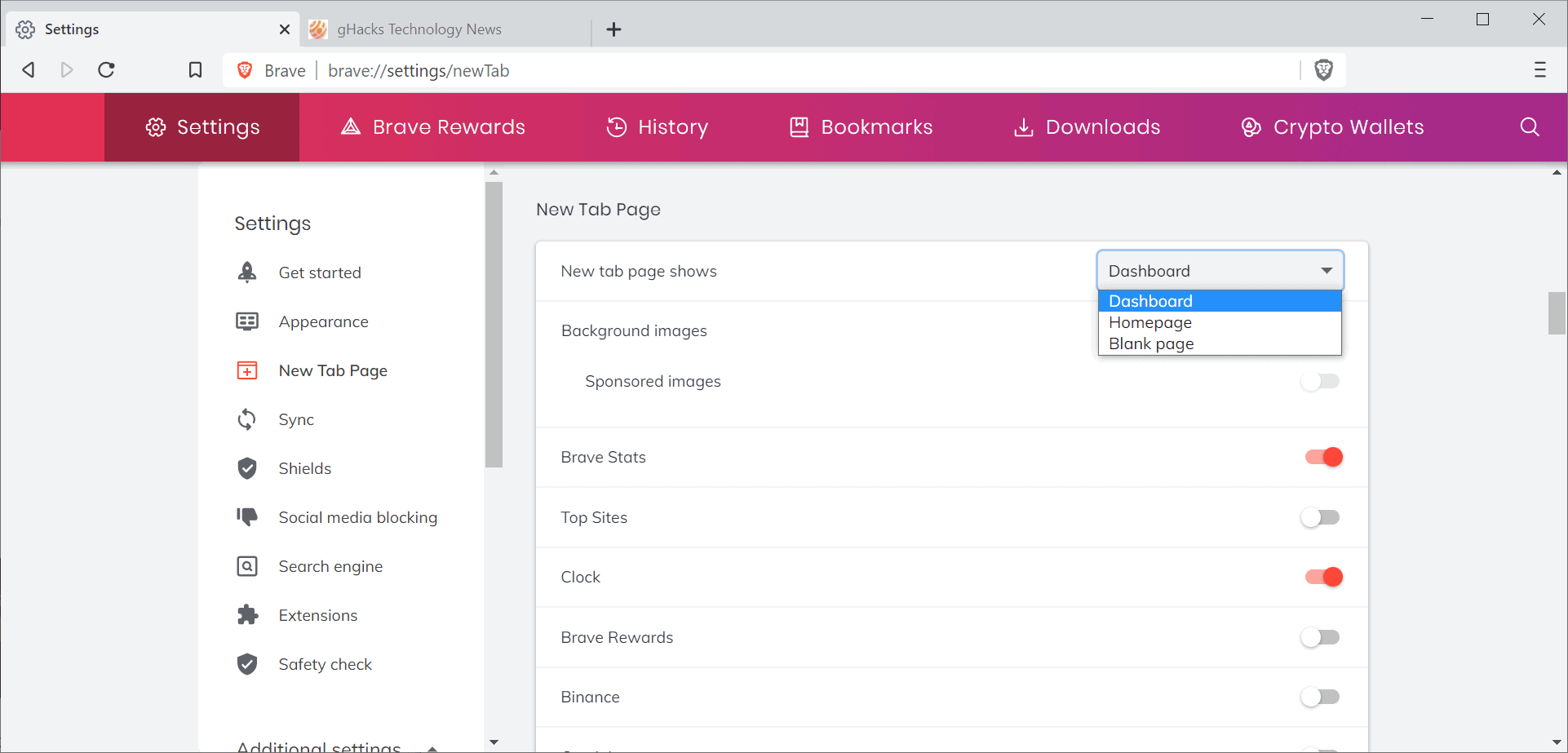
Brave 1.18 adds new controls to set what is displayed on the new tab page. Just load brave://settings/newTab (or select Settings > New Tab Page) to set the "New tab page shows" option from Dashboard to either Homepage or Blank.
Another new feature of Brave 1.18 is support for Global Privacy Control. It is a relatively new initiative to improve user privacy and rights on the Internet. Basically, what it does is inform sites that an Internet user denies sites the right to sell or share personal information to third-parties.
You can check out our Global Privacy Control summary for additional details. Global Privacy Control is enabled in Brave.
Brave 1.18 features a number of smaller additions and changes. The following ones are noteworthy:
- Protection against private browsing mode detections added to the browser.
- Contrast among tabs improved.
- Option to remove devices from Brave Sync, e.g. to remove unused devices or devices that were stolen/lost.
- Yandex is the default search engine in select regions for new installations (including Armenia, Azerbaijan, Belarus, and Russian Federation). Full list is here.
- Upgraded the core to Chromium 87.0.4280.101
- Lots of changes related to Brave Ads and Rewards.
You can check out the full release notes here.
Now You: Have you tried Brave recently? What is your take on the browser?





















@ Pants & Iron Heart:
I’d like to thank both of you for your in depth conversations on these matters on this forum as they are very important and not appreciated enough. Whether or not you 2 agree on things or get along is nowhere near as important than you 2 having the debate. I have personally learned a lot.
Thank you Pants for all of your hard work on the user.js and all that you are involved. I care that you care, never stop caring. Your readers love you.
Thank you Iron Heart for all your help on Brave and other Chromium browsers as well as advice on setting them up. Your comments are never boring thats for sure.
Also thanks to Martin for allowing you 2 to tear the place up with knowledge without much interference
Keep the debate alive and keep up the good fight.
I am likely to leave brave in the near future. It appears that Google is controlling too much of the Brave core code. I moved to Brave when I left firefox and put up with some of it in its earlier days, but the loss of blocking Autoplay either selectively or generally is a show stopper.
First autoplay blares sound out in the middle of a quiet evening, when all I want to do is read.
Second autoplay with mute is getting cumbersome since you cannot selectively turn it on and off. You can turn it off a bit then it won’t play anything unless you globally enable it. I just go to Safari in that case.
Third autoplay consumes bandwidth which the ISPs are going to make increasingly expensive. Comcast is already playing with this concept and if they are successful, the avalanche will begin.
I do not want 90% of the mediaplay that autoplays and I should be able to decide whether I want to watch talking heads, ads or whatever else, not Google, not Chromium and certainly not the news propagandists.
By continuing to use google written and driven chromium and squelching debate on the forums, I cannot long see how there is any real difference between Brave and anybody else.
I was curious about BRAVE.
I installed it, looked around and then decided to uninstall.
I used an uninstall program, so thought that everything was gone. However this was certainly not the case. I found a few remaining maps w.r.t. BRAVE, in USER even a map which looked as a full blown installation (with several sub-maps).
I then decided to look for BRAVE in the registry, I was very surprised to find a large amount of BRAVE-related registry-items.
I find this very strange, BRAVE remains secretively active after an uninstall. WHY ????
Meh, addition of another useless news feed. Most likely, the company will stop it’s development in the future in favour of other actual browser useful features and would ultimately remove it in the long run.
I was looking at something like this. Brave might be my go to News reader app.
No answer here but if you chase a portable version, be wary
https://portableapps.com/node/54119
Tried Brave in the early days. Full of issues. Slow response to reports of problems and requests for change. Hated it. It is time to try again in preparation for Manifest 3.
If you’ve tried Brave in their Electron days then you should try it again. They’ve seriously upped their game in recent months.
Chromium developers are arrogant fools. I’m not using any Chromium based browsers long as there is no way to turn off that blurry DirectWrite garbage.
I use Cent Browser because its the only browser left that has the flag to turn off DirectWrite. Firefox is another alternative that still renders text clearly on any device.
Why no portable version??
also here if needed, https://portapps.io/app/brave-portable/
I’d be willing to give the Brave Browser try but I face, a priori, three barriers:
1- The install folder, which is not configurable. Create a junction?
2- The user’s profile folder, which is not configurable as well. Create a junction?
3- Less barriers than questionings : managing the cache. Is it possible to set the RAM cache, disblable the disk cache?
Once theses three points cleared, I’d have to test Brave, objectively and subjectively (might be an excellent browser which nevertheless doesn’t suit me). I have in mind the amount of user preferences available in Firefox’s about:config, I understand the equivalent in Brave is all in its ‘flags’, but do theses allow as fine tuning as in Firefox?
Brave’s audience is increasing as we’ve been told so I suppose and hope there will be more than one aficionado to bring in some answers to my wondering.
@All of you, thanks for your replies. As I understand it, at this time, Brave could be, might be — out of the box and provided @Iron Heart’s list above, most welcomed for new users — an as good or even better choice than Firefox. Could/might as from what I perceive of course and, again, in the perspective of an objective/subjective blend. But I also have the feeling (feeling is vague but unfortunately often guides choices when thorough testing/facts should prevail but are sometimes not considered should it be only for time reasons), feeling that, for a user who wishes to tailor his application, browser here, to fine-tune the browser, Firefox, with its incomparable number of settings, leads the band.
And we all have our own imperatives. or not by the way. Personally I don’t like applications which don’t offer an install location option, especially when the forced location is elsewhere — on Windows — than ‘Program Files’ / ‘Program Files (x86)’ and, when it comes to browsers, the user’s profile’s location must be available. Browsers operate so many disk accesses that having that profile on a RAMDisk is a must given the disk is not a ‘fast’ one.
So, again, facts and personal imperatives. But, above all, no credit in arguing on facts when they haven’t been experienced and to achieve that no doubt I’d have to install Brave, test it thoroughly, and see how it goes for me, less for uninstalling it than for using it as my default browser.
Thanks gain. I’ll try to consider sparing time to try Brave in a neutral state of mind.
Chromia don’t have item by item equivalents to Firefox or even nomenclature. Instead of another mini-thesis on how to play with Chromia configs, if you’re hesitant about Brave (It’s really the only OOB Chromium based browser with privacy; I see nothing wrong with it) try portable Ungoogled Chromium, it’s the second green entry at the top:
https://chromium.woolyss.com/
Has portable apps and portable versions, or just install it.
Be forewarned Ungoogled Chromium doesn’t even have access to the Web Store and so none of the usual extensions. That can be overridden but for experimentation purposes to get a feel for a private version of Chromium, use it as is. Brave looks and behaves like a “normal” browser, however, with better privacy and improved functionality over Ungoogled.
Everything you can access in Chromia, flags, settings, etc., are at
chrome://chrome-urls/
Have fun with that one!
Chromia use RAM and disk caches, depends on what kind of data is being saved, there’s some info online if you dig. Disk caches can be moved and resized, not sure about RAM caches.
Disk caches (there are a number of them) are in:
C:\Users\YourName\AppData\Local\Chromium\User Data
and
C:\Users\YourName\AppData\Local\Chromium\User Data\Default
(Default is your profile)
Chromia do not delete caches on shut down even if set to, caches are deleted at the next start up. Brave may be different, IDK, it’s easy to check, A .bat file on your desktop to delete caches when desired is what I do.
I use FF ESR with AdGuard System as my prime browser and Ungoogled Chromium with some simple extensions as a backup. AdGuard takes care of UC, also.
Brave works most similar to my FF/AdGuard setup, a browser with a privacy/anti-tracking proxy.
BTW, that site I linked above has a huge amount of info on various browsers. Most of it is current or almost, great read if you have a few hours or days.
https://chromium.woolyss.com/
Maybe that was a mini-thesis…
:)
@Tom Hawack
https://www.softperfect.com/products/cacherelocator/
Date Version Details
2020-06-29 1.5 Added: Brave Browser support.
@Tom Hawack
Add: no offline installer.
@Bob
Huh? There are standalone setups, they are even called such:
https://github.com/brave/brave-browser/releases/tag/v1.18.70
That being said, I don’t see how an offline installer has any advantage over an online installer. Both get the job done and the download size is the same.
Do you think an average user knows knows about the existance of Github?
@Bob
Fair enough, likely not, but that doesn’t mean standalone setups outright don’t exist. Anyway, what’s the point if I may ask? If your intention would be to install Brave, you could either download the standalone setup or the online installer, but the data transmitted would be just the same, both in size and in essence. Just curious, I don’t see how the distinction would even matter.
Found the standaloneversion just after me posting here. Only on github available, not on brave.com.
install mac os big sur?
@ Tom Hawack
In answer to your wondering: Don’t be “Brave.”
Simply convert to Win 10 then all of your concerns will go away. And you could even use the new Edge browser for secure web browsing…. (not! :<)
@Valborex, hi there, nice to read you :=)
Nice to read you and, as often, I suspect a pleasant sophisticated irony, especially if you remember, as i think you do, my deep feelings of unexpressed love concerning Windows10. Lol. Together, moreover, with Edge? Mama mia, you want my death? Me have woman and children, pity!
Read you later, alligator!
@Tom Hawack
Okay, I am the “aficionado” you probably expected to reply, but I’ll try to answer to the best of my abilities anyway:
> The install folder, which is not configurable. Create a junction?
Not doing that myself; but here are relevant GitHub comments:
https://github.com/brave/brave-browser/issues/598#issuecomment-451208237
https://github.com/brave/brave-browser/issues/598#issuecomment-673704663
> 2- The user’s profile folder, which is not configurable as well. Create a junction?
https://old.reddit.com/r/brave_browser/comments/j3qrnu/is_it_possible_to_move_braves_profile_to_another/g7f1qzq/
> Less barriers than questionings : managing the cache. Is it possible to set the RAM cache,
You mean limit the cache size? That’s possible, bottom of the article:
https://www.ghacks.net/2019/09/14/speed-up-brave-browser/
It’s also possible to let Brave cache to e.g. a RAM Disk, if you meant that. As for myself, I just let Brave cache normally, having set it to delete cache upon closing the browser (see my comment above). Cookie AutoDelete also deletes cache upon closing the related tab or domain change here.
> I have in mind the amount of user preferences available in Firefox’s about:config, I understand the equivalent in Brave is all in its ‘flags’, but do theses allow as fine tuning as in Firefox?
No. brave://flags allows some tuning, but it is not as extensive as about:config (although, to be fair, some things I would do in about:config was already taken care of by the Brave devs, see: https://github.com/brave/brave-browser/wiki/Deviations-from-Chromium-(features-we-disable-or-remove)#services–features-we-disable-entirely ). What you search for is startup flags: https://peter.sh/experiments/chromium-command-line-switches/
> Is it possible to set the RAM cache, disblable the disk cache?
On linux it’s enough to create brave-flags.conf in ~/.config and put the following line: ‘–disk-cache-dir=/tmp/cache’ in there.
On Windows you need third party tools for that and TBH I wouldn’t even try to do it on Windows.
This not that brave web browser has nothing more regarded to privacy than Vivaldi with its included Ads block plus uBlock Origin can do. The latest great addition to Vivaldi is that it can disable all g00gol services. Plus Vivaldi is now a fully integrated web suite with email client.
@not_that_brave
Well, not quite. Brave has fingerprinting protections and the internal adblocker is capable of CNAME uncloaking (which uBlock Origin – as an extension – can’t do in Chromium due to an API limitation):
https://github.com/brave/brave-browser/wiki/Fingerprinting-Protections
https://www.ghacks.net/2020/11/17/brave-browser-gets-cname-based-adblocking-support/
The internal adblocker of Brave IMHO also works better than the one in Vivaldi as of today.
> The latest great addition to Vivaldi is that it can disable all g00gol services.
You can do that as well in Brave, but it’s certainly a good thing that you can now do it in Vivaldi just the same.
> Plus Vivaldi is now a fully integrated web suite with email client.
Fair point, provided one is searching for a web suite.
Plus Vivaldi has unmatched configurability and features compared with any other Chromium based web browsers. Actually, compared with any current web browsers.
Those CNAME and other privacy/fingerprinting extras some are blinded of are just gimmicks. Vivaldi might just add those soon on their integrated adbsblock.
Quick tip: if you’re using latest “safe” version of Chromium based browser, you’re just in under 0.01% of uniqueness on internets combined with your device fingerprinting. Try search for any flagged buzz words and the 3-4 letter agency you’re assigned on will knock-knock on your door will all bravery browsing you’re doing…
@not_brave_only_gimmicky
Brave’s fingerprinting protections or CNAME uncloaking were not that trivial to implement from what I read on Brave’s GitHub page. Vivaldi’s team is also smaller than the Brave team. They could certainly implement it as well if they wanted to, but your predictions strike me as very optimistic indeed.
> if you’re using latest “safe†version of Chromium based browser, you’re just in under 0.01% of uniqueness on internets combined with your device fingerprinting.
Come on, no browser out there has started out with 100 million users from the get go, Brave’s uniqueness is being reduced day by day are more people adopt the browser over time. Of course you can say now: “Look, you stick out because you are using Brave!” …but this argument is bound to lose its importance on a continual basis. I’d be inclined to say that you would stick out with ANY browser aside from Chrome and Safari (and possibly Edge) at this stage.
> Try search for any flagged buzz words and the 3-4 letter agency you’re assigned on will knock-knock on your door will all bravery browsing you’re doing…
Uh, Brave is a general purpose browser providing a reasonable level of privacy (mostly from advertisers, it’s not meant to fend off three letter agencies, if that’s even possible). We are not talking about Whonix, Tails, Qubes OS, or even the Tor Browser Bundle here, by any means.
Here is my own Brave setup for anyone interested, as of December 13th, 2020. Brave 1.18.70 (desktop version – this setup is only partially applicable to the Android version of Brave). This setup is meant to strike a good balance between privacy and usability, and tries to debloat the browser.
Why do I use Brave? Basically, because Brave removes unsolicited requests to Google from Chromium, the only times it contacts Google by itself it to update extensions (if you have any) or Google SafeBrowsing (unless you disable it, see below) and Push notifications (unless you disable them, see below). This is far superior to Chrome or vanilla Chromium. You can read about the things the Brave team removed here in detail:
https://github.com/brave/brave-browser/wiki/Deviations-from-Chromium-(features-we-disable-or-remove)
It is the only Chromium-based browser with credible fingerprinting protections:
https://github.com/brave/brave-browser/wiki/Fingerprinting-Protections
It is the only Chromium-based browser that can do CNAME uncloaking:
https://www.ghacks.net/2020/11/17/brave-browser-gets-cname-based-adblocking-support/
Brave’s internal adblocker will also continue to work as it does uninterrupted. It won’t be affected by Google’s decision to cripple adblocking extensions in the near future with Manifest V3. Brave’s adblocker is not an extension, but rather implemented natively, and thus isn’t under extension restrictions, like e.g. uBlock Origin would be.
MY BRAVE SETTINGS:
Brave adblock lists:
– Go to brave://adblock/ and enable the lists there, the more the merrier. I recommend the list that matches your native language as well as the following general purpose lists: Easylist-Cookie List – Filter Obtrusive Cookie Notices, Fanboy Annoyances List, Fanboy Social List, uBlock Annoyances List
Brave’s settings menu (hamburger menu –> Settings):
1) brave://settings/appearance
– Brave suggestions in the address bar –> Disabled
– Hide Brave Rewards Button –> Enabled
– Always show full URL –> Enabled (might help in spotting phishing attempts by revealing any modification to URLs)
2) brave://settings/newTab
– If you prefer, set this to show an empty / blank page, if not:
– Sponsored Images, Brave Rewards, Brave Today, Binance, Crypto.com –> Disabled
3) brave://settings/shields
– Show number of blocked elements on Shields icon –> Enabled
– Default view –> Advanced view
– Trackers & ads blocking –> “Aggressive” (this will block 1st party ads as well as 3rd party ads, “Standard” would only block 3rd party ads – there is no reason we would want to see 1st party ads, so “Aggressive” is fine)
– Upgrade connections to HTTPS –> Enabled (equivalent of the HTTPS Everywhere extension, which is why you don’t need to install the the extension in Brave)
– Block Scripts –> Disabled (blocking scripts with a general setting like that just breaks too many websites, if you want to do it anyway, use an extension like uMatrix that can provide more granular control than the Brave setting can)
– Cookie blocking –> Only block cross-site cookies (outright blocking 1st party cookies breaks too many websites, we’ll take care of left over 1st party cookies later on with Cookie AutoDelete)
– Fingerprinting blocking –> Aggressive (if it breaks any website, play around with the “Standard” setting, „Aggressive“ has worked for me so far)
4) brave://settings/socialBlocking
– Disable all the settings there, unless you have and use a Google / Facebook / Twitter / Linkedin account, in which case leave the setting that matches your account enabled
5) brave://settings/search
– DuckDuckGo, StartPage, Qwant are privacy-respecting search engines, however, I know that Google tends to yield better results. Use whatever works for you.
6) brave://settings/extensions
– Ethereum / Web3 provider –> None
– Crypto Wallets –> Disabled
– Allow Google login for extensions –> Disabled
– Hangouts –> Disabled
– IPFS Companion –> Disabled
– Widevine –> Disabled (unless you use any commercial streaming service like Amazon Prime / Netflix / Spotify or whatever within the browser itself, if you use any of those leave it at “Enabled“)
– Media Router –> Disabled (unless you want to use Chromecast, in which case one should leave it at “Enabled”)
– Private Window with Tor –> Enabled (handy if you want to hide your IP address, do not consider it a real Tor Browser Bundle replacement though, as Brave doesn’t have Tor’s common fingerprint)
– Automatically redirect to .onion websites –> Disabled (you can still do it if necessary, Brave will offer the option to you, though I really recommend the Tor Browser for any such action)
– WebTorrent –> Disabled
BRAVE’S ADVANCED SETTINGS
7) brave://settings/privacy
– Use prediction service to help complete searches and URLs (= URL speculative autocomplete) –> Disabled
– WebRTC IP handling policy –> „Disable Non-Proxied UDP“ (will prevent WebRTC IP address leak)
– Use Google services for Push notifications –> Disabled (unless you want notifications, e.g. for chats, in this case leave it at “Enabled”)
– All Brave crash reports / usage stats / “help us to improve our product“ nonsense –> Disabled
8) brave://settings/clearBrowserData
– Set it to delete cookies and cache upon closing the browser.
9) brave://settings/cookies
– Block 3rd party cookies, set to delete cookies upon closing the browser.
– “Do not track” –> Disabled (only raises entropy, ironically making you more easy to track, and this setting is not respected by most websites anyway)
10) brave://settings/security
– Google SafeBrowsing –> Disabled (double-edged sword somewhat, Google SafeBrowsing improves security while lowering privacy, I chose to turn it off because I am convinced that uBlock’s anti-malware lists will suffice)
11) brave://settings/content
– Hard to give recommendations here, disallowing access to your location should be safe. Do not disable notifications if you use chats, do not disable microphone or camera access if you use audio / video chats. If you don’t use chats, deny access to camera, deny access to microphone, and automatically deny notifications.
12) brave://settings/payments
– Disable all settings you see there.
13) brave://settings/addresses
– Disable all settings you see there.
Extensions I use in Brave, all downloaded from the Chrome Web Store… All of these extensions are long-standing free and open source software and do not collect any kind of data themselves:
1) uBlock Origin = content blocker, for ad and tracker blocking. I use it in Brave despite Brave having its own adblocker, because contrary to Brave, uBlock Origin allows me to set custom lists that don’t come bundled with it.
– Enable the settings stopping link prefetching, hyperlink auditing, CSP reports. Don’t use the WebRTC setting as it conflicts with Brave’s own WebRTC setting and isn’t any better!
– As for the lists one should have, of the included ones: Basically all lists aside from the language-specific ones can be recommended, of the language-specific ones enable the one(s) that match your own language at least. I literally have all uBlock Origin included-by-default lists enabled without issue.
– I also value the following lists, which are not included by default (Hit “Subscribe“ at the right side of the screen in order to subscribe to them):
-> AdBlock Warning Removal List (circumvents the behavior of websites locking you out once they detect you have an adblocker): https://filterlists.com/lists/adblock-warning-removal-list
-> Fuck Fuckadblock (same reason as Adblock Warning Removal List): https://filterlists.com/lists/fuck-fuckadblock
-> I don’t care about cookies (most effective list against annoying EU cookie notices): https://filterlists.com/lists/i-dont-care-about-cookies
2) ClearURLs = primarily filters tracking elements from URLs, meaning you will be using clean links. Also does other minor stuff, e.g. eTag filtering.
– Allow domain blocking –> Enabled
– Prevent tracking via the History API –> Enabled
– Allow Referral marketing –> Disabled
– Filter eTags –> Enabled
3) LocalCDN = websites load libraries from third party sources, the providers of those libraries know which websites you’ve visited and can potentially profile you. LocalCDN provides these libraries locally for websites, intercepting requests to third party sources. Has the side effect of slightly speeding up the loading process of websites. I use LocalCDN instead of the similar Decentraleyes because the development of the latter has slowed down, and because LocalCDN supports a wider spectrum of libraries at this stage.
– You can leave everything at the default settings here. However, I recommend to disable the update notification in the settings of the extension as it’s quite annoying – the extension gets updated quite regularly.
– If you use uBlock Origin in medium mode instead of the default „easy mode“, you can integrate LocalCDN with uBlock Origin (under the “Advanced” section of LocalCDN’s settings)
4) Cookie AutoDelete = Gets rid of cookies and other kinds of local data websites store on your computer upon closing the tab or changing the domain. Remember that we didn’t block 1st party cookies because that would break too many websites? Cookie AutoDelete allows websites to set those, so that the websites can work correctly while you use them, but gets rid of them immediately once you leave the website in question, so that the cookies can’t be used for tracking purposes.
– Automatic cleaning –> Enabled
– Enable Cleanup of Discarded / Unloaded Tabs –> Enabled
– Enable Cleanup on Domain Change –> Enabled (Depends on the convenience level you want to maintain, if you are logged into an account, then change the website entirely, and then return to the website you’ve been logged into, all within the same tab, you’ll get logged out as the cookies will be removed upon domain change – normally Cookie AutoDelete would only clean cookies upon actually closing a tab).
– Clean Cookies from Open tabs on Startup –> Enabled
– Clean all Expired Cookies –> Enabled
– Enable Cache Cleanup –> Enabled
– Enable IndexedDB Cleanup –> Enabled
– Enable LocalStorage Cleanup –> Enabled
– Enable Plugin Data Cleanup –> Enabled
– Enable Service Workers Cleanup –> Enabled (may break chat notifications if you need those, so be careful if you use chats)
If you intend to use Cookie AutoDelete I recommend that you learn how to use its White- and Greylist. Sometimes, you may wish to permanently store a cookie (in which case you should also disable the setting telling Brave to delete cookies upon closing the browser, see above). A primary example would be YouTube Autoplay; the autoplay setting is stored into a cookie, so if you disable autoplay while using Cookie AutoDelete, autoplay will get re-enabled every single time you return to YouTube, because Cookie AutoDelete will always destroy the associated cookie upon you leaving YouTube. I got around whitelisting the Google cookie by using Enhancer for YouTube by MaximeRF (another highly recommended extension! – though not privacy-related, which is why it doesn’t appear here in depth), but on other websites, where there is no workaround available, you may wish to understand how whitelisting or greylisting cookies works. More info here: https://github.com/Cookie-AutoDelete/Cookie-AutoDelete/wiki/Documentation
—–
I hope this info was helpful for any interested party. I always appreciate corrections or criticism where applicable.
Thanks for the settings. I will keep cookies cause I wanna stay logged in.
@Stefano
No problem. Glad to hear that it helps you.
> Here is my own Brave setup for anyone interested
Wow, all that changing and tweaking… and it still doesn’t come close to the more comprehensive solutions built into Firefox: fluffing around with all those cookies and persistent storage and third parties when you could just use dFPI (or FPI or Temporary Containers). Do don’t even need an adblocker: but of course use one, since it removes eyesores, reduces malware attack vectors, and speeds shit up.
> CNAMES
Wow, now it’s a feature. Before Brave implemented it, it was a non-issue. The main reason Brave added it, was because it benefits their ability to replace adverts for their own monetization = their business model.
> [Brave’s fingerprinting protections] … I think the jury on this one is still out
Not to the experts
They are really only interested mostly in defeating naive scripts
– I have an email chain with the lead dev about this: it’s complicated but that’s the guts of it in a nutshell
– defeating naive scripts is all fine (RFP does it too with randomized canvas, randomized video stats per OS), but not a cure all – to those actually providing real solutions, randomizing is an oddity but useful depending on the metric: eventually scripts will become more sophisticated (and some already are) and a decent one right now can bypass most of Brave’s work
– contrast that to Tor Browser / RFP where they engineer solutions that stand up to the most rigorous tests – in other words they make them as bulletproof as possible, not short term solutions
– that’s not to say that Brave doesn’t want to make their randomizing more effective
They decided to randomize almost everything. That’s OK given that for example, canvas is subtlety randomized anyway (subtle for compat reasons) and they have to protect the random seed per session per eTLD+1 anyway. But it carries risk.
– they are so subtle with canvas that it can be bypassed and one of three real values leaked
– I alerted the lead dev to this: and his comment on how reversible canvas fingerprinting protections are: “answer, not very hard to reverse!” – given his emphasis on naive scripts, fixing this is low priority (and it’s low risk for now) – but that shows how lax IMO some of the implementations are
– randomizing is _ultimately_ no better than returning a static value, and it is trivial to return all of Brave’s attempts to confuse scripts and simply return the metrics they protect as static values: it takes about a millisecond to do
But if we actually tested each metric and tried to determine if it’s spoofed, or possibly unmask the real values or reverse the randomization, we can do that too
– e.g: the userAgent randomizing can be undone by stripping leading, trailing and multiple spaces
– e.g. the userAgent randomizing is bypassed in workers
– e.g: the randomized gibberish of returned plugins can be detected in two ways. Detecting that it’s gibberish (regex etc), or by cross checking their own object property names in mimeTypes/plugins etc
– e.g: canvas protection can be 100% completely bypassed in an iframe
– I alerted the lead dev to this as well – it was the first thing I found, within a day of installing Brave to see what it did – months (a year?) after it was implemented, so their QA is/was a bit lacking: the first fix was insufficient, and a second issue is idling: he explained to me why they missed these, and why it is hard to fix
– and while I don’t actually test Brave (I am focused on Firefox, Tor Browser, RFP), I do occasionally check it. But I don’t have to look far to be able to find weaknesses – part of that is my expectations but part of it is the problems mentioned below
Part of the problem is the solutions are inadequate. Part of it is the decision to randomize (which is not needed everywhere) and just exposes non-universal solutions fit only for naive scripts. Part of it is the implementation. But the biggest part is (and I am not a chromium engineer) that Brave is not actually engineering chromium per se: instead they have to rely on existing underlying structures and put “hacks” (for lack of a better word) on top, such as “listening” for iframes etc. In Firefox/Tor Browser, the engineers actually get right into the guts of the engine and make things happen. Brave simply can’t do that to the extent they would like to, or need to, and the lead dev on fingerprinting has said the whole thing (re-basing their patches) is delicate and fragile as it is.
And then of course, there is so much missing (but planned) that RP does, not to mention non-Firefox APIs, but they are going to come up against the same issues they already encounter: especially given the complexity of some of them and their equivalency in so many other areas
– e.g. there is nothing yet for fonts, screen + window metrics, timezones, languages and date/time formatting, mimetypes, media capabilities, css entropy .. timing protections .. and lots more
However, all the best wishes to Brave’s anti-fingerprinting getting better and more comprehensive, because fuck fingerprinting – but stop trying to compare it to Tor Browser or RFP – it’s not even close
@Pants
You omit things as always to make Firefox (which you promote, and which you need in order for your own project to exist) look batter. Yawn, nothing new in the west. Going through some of the most egregious things in case anyone should fall for that.
> Wow, all that changing and tweaking…
…but still not as much as your own stuff “arkenfox”.
> fluffing around with all those cookies and persistent storage and third parties when you could just use dFPI (or FPI or Temporary Containers).
I can isolate stuff by using Brave’s Tor mode which is a separate profile within the main profile. I can also create separate profiles for specific tasks in order to isolate them, if I wanted to. You know that, too, but hey, omission is king, right? I just see no need for it, because there is little reason to isolate cookies and other local data that are quickly being destroyed. Containers are a meme.
> Wow, now it’s a feature.
No, CNAME cloaking is still a fairly irrelevant form of tracking, I just mentioned it for completeness, in order to differentiate from other Chromium-based browsers. Mrs. Nitpicker.
> The main reason Brave added it, was because it benefits their ability to replace adverts for their own monetization = their business model.
LOL, no. Brave Rewards existed before and after CNAME uncloaking, and are a separate part of the browser. Brave was always into adblocking, that’s kind of the point. By the way, I prefer their business model when the alternative would be getting all the money from sugar daddy Google (as is the case with Mozilla), with all the conflicts of interests associated.
> Not to the experts
Skipping the blah blah parts because fingerprinting is a meme. Like with other trackers, typically JavaScript scripts are behind it. Those scripts are more or less getting blocked by an adblocker, and thus stopped from execution. I have Brave’s fingerprinting protections enabled as a precautionary measure, but do you know how many fingerprinting scripts I have encountered in the wild that have NOT been taken care of by the adblocker already? None, zero, nada. Should tell you how high I rate the importance of this general issue.
> there is nothing yet for fonts, screen + window metrics, timezones, languages and date/time formatting, mimetypes, media capabilities, css entropy .. timing protections .. and lots more
They said themselves that their fingerprinting protections are NOT YET COMPLETE. It’s not like they are hiding it. You can read about it in the docs and on GitHub (which is where you draw your info from). I am tired of mentioning it time and time again in conversations with you.
> but stop trying to compare it to Tor Browser or RFP – it’s not even close
Huh? I make it fairly explicit in another comment here that I am not really doing this:
https://www.ghacks.net/2020/12/13/brave-1-18-stable-launches-with-brave-today-global-privacy-control-support-and-more/#comment-4480615
To quote myself:
“Uh, Brave is a general purpose browser providing a reasonable level of privacy (mostly from advertisers, it’s not meant to fend off three letter agencies, if that’s even possible). We are not talking about Whonix, Tails, Qubes OS, or even the Tor Browser Bundle here, by any means.”
GENERAL. PURPOSE. BROWSER. Much like Firefox, by the way. Stop making things up, thank you very much.
PS: I think there is no reason – despite some remarkable work they do – to treat the Tor Browser Bundle as some holy grail, however, because its base is still Firefox and if I wanted to de-anonymize you, I’d just attack its weak sandbox with a drive-by attack in order to get an exploit on your PC. Which is what three latter actually do as an anti-Tor measure. As you’ve elaborated in the case of Brave, when smaller projects have to work with code coming from someone else, there is only so much they can do without creating a maintenance hell. Tor has to live with Firefox’s weak sandboxing, for example. Not that it matters – once Gecko becomes even more irrelevant than it already is, they’ll have to create a Chromium-based Tor anyway, if only to avoid rendering errors.
As per usual: right over your head, or deliberately ignored, or twisted when confronted with FACTS
> Brave Rewards existed before and after CNAME uncloaking
Learn to read dude: Who said it was a prerequisite for Brave Rewards? I said it “benefited” it, not “enabled” it. Also, why would BR not exist afterwards? Is it a blocker? Or is it a prerequisite? Try making sense for once
> They said themselves that their fingerprinting protections are NOT YET COMPLETE. It’s not like they are hiding it
Learn to read some more dude: I didn’t say they were complete (I said the opposite) or trying to hide it. The point is that the planned additions will come up against the same problems that already plague them
> I can isolate stuff by using Brave’s Tor mode which is a separate profile within the main profile. I can also create separate profiles
So massively inferior then. Having to fluff around with profiles.Or using Tor mode with the latency (and trusting they have it right) – and please, show me the proof that while in Brave’s Tor Mode that it has anything like FPI (they don’t) – i.e multiple domains open in Tor Mode.
The point is that Firefox has first party isolation built in. Network partitioning ( https://groups.google.com/g/mozilla.dev.platform/c/uDYrtq1Ne3A ) will also soon be on by default – in Firefox 85 if all goes well (in effect it’s the networking side of what FPI does) – and it covers a lot that chromium isn’t even near to doing or considering. And dFPI (in effect the rest of FPI) will be enabled by default soon as well
> there is little reason to isolate cookies and other local data that are quickly being destroyed
So massively inferior then. While third parties exist they can be used (imagine users with dozens, hundreds of tabs open). And of course persistent local web storage is only a small part of it: what about favicons, OCSP, shared workers, SSL session caching, media caches, HSTS/HPKP, HTTPS, DNS to name a few others. Firefox can protect all those and more.
Firefox engineers actually come up with way-more-comprehensive and **real solutions**: not your namby pamby feel-good antique fuffyness
> Skipping the blah blah parts because fingerprinting is a meme
More like because you can’t understand it – understandable given your proven ignorance on how fingerprinting, entropy and linkability work
So CNAME uncloaking is a meme, and fingerprinting is a meme – except when you want to tout them as features in Brave. And now isolating/partitioning via origin attributes (like containers, FPI, dPI) are a meme – but won’t be once this concept starts to be applied to chromium. OK, got it, genius
> sandboxing
Stick to the topic dude. What does sandboxing have to do with it? “isolation” can apply to more than just processes. You’re mixing up security and privacy/tracking issues
@Pants
> favicons, OCSP, shared workers, SSL session caching, media caches, HSTS/HPKP, HTTPS, DNS
This strikes me as the only part of your post really worth discussing. The things that are immediately fixable in Brave would be:
> media caches
Set chrome://flags/#turn-off-streaming-media-caching-always to “Enabled”, this will turn the media caching off for good.
> HSTS/HPKP
HTTPS Everywhere is included and enabled by default in Brave and produces false positives, at the end of this writeup: https://zyan.scripts.mit.edu/presentations/toorcon2015.pdf
> SSL session caching
Fixable by deleting the browsing history on every shutdown of the browser:
https://serverfault.com/questions/279984/how-do-i-clear-chromes-ssl-cache
However, this strikes me as impractical for most users, a typical thing you would likely recommend to enable, but I wouldn’t. I might even include this in my next posting as a possible additional setting, but not more.
> DNS
Strikes me as an impractical form of tracking, this thread explains it: https://security.stackexchange.com/questions/83125/using-dns-to-track-browser-activity-on-a-lan
Also, do you know what DoH is? Although that would be its own can of worms, keyword being “trustworthy DoH provider” here.
> shared workers
Fair point, but very unlikely. They are not that popular with web devs.
> favicons
Same as with shared workers: Fair point, but even more unlikely. Can you show me any examples where this is actually done in the wild?
You are either totally ignorant, or being misleading (or both).
PLEASE LEARN TO READ, UNDERSTAND WHAT YOU READ, AND TO USE SOME LOGIC
Look up the meaning of the word “comprehensive”: no cares about your anecdotal usage. We’re talking about a _real solution_ for _all use cases_. I even gave an example e.g. “what about users with 100s of tabs open” and your reply was something like “doesn’t affect me”
Not all cross-domain logins break in FPI, and this is what dFPI aims to solve. “Partitioning” is not name dropping, it’s the term being used by browsers (including chromium) to basically implement what FPI is – isolation by eTLD+1 (+ scheme) – which was what was being discussed
> Huh? Massively inferior? In what way? From a usability standpoint? It’s enough to go to the hamburger menu -> “Open Private Window with Torâ€â€¦ Boom, done. From a technical point of view it’s not inferior to containers, quite the contrary.
First of all, nowhere did I say containers. I mentioned Temporary Containers in my first post. Temporary Containers (an extension) in a hardened mode is *almost* the same as FPI/dFPI – and that’s because it leverages the same underlying “Origin Attribute” infrastructure.
So I said “massively inferior” then cited FPI. And you counter than it’s no better than containers which is different thing altogether. How about you actually argue the point instead of making false statements
And now you’re confusing Tor protocol with Tor Browser’s FPI. It’s one thing to break the digital footprint of your IP address, and a completely DIFFERENT thing to break linkification of traffic.
So load up your Tor mode in Brave and you have none of that protection – let alone in one of your many profiles (isolated from each other but nothing in the profile is), and so on. Your antiquated ideas on using cookie cleaners and multiple profiles and one off tor mode windows and one off incognito windows is the way of dinosaurs, and contain many flaws and holes.
So yes, your methods when using chromium are VASTLY INFERIOR .. and technologically outdated
—
You keep saying things like “how likely is that”, or “so it won’t affect me”. So you’re relying on user behavior and the status quo. If there is a hole, then patch it. One day that hole will be exploited. e.g.just because you block most FPing scripts, so what: that’s just the first line of defence. What about when scripts mutate on demand with random names from random third parties and get super sophisticated and ultra-smart and block lists start to become ineffective. What about when all FPing scripts are first party and you can’t detect them, as they are bundled deep within needed JS files for the site to work. Actual anti-fingerprinting is the last line of defense: you don’t ignore it because it may be deemed low risk. This is what is meant by real solutions: instead of just trying to defeat naive scripts, how about defeating ALL scripts.
Again: go look up the word comprehensive
You clearly do not understand what you are talking about. For example stating that SSL session ticket IDs are cleared when you close the browser – that’s by design: FFS, that’s why they’re called SESSION ids. FPI/dFPI/OA’s/partitioning Isolates them within each session – which is nothing like what you said chromium does above
Go educate yourself or listen for once. You’ve already shown you don’t know anything about Firefox, you sure as hell don’t understand fingerprinting or entropy or how that can be used to linkify traffic. And you sure as hell don’t know how a lot of other linkifying/tracking mechanisms work: it’s not just about your stupid cookies
@Pants
As an addendum to my last reply to your last reply… My question would be: What are you trying to achieve here? I mean, really? I am giving solid advice to people who want to achieve a decent privacy level, decent as in “above average”. I never claimed that my setup is the best thing since sliced bread, and if you need to hide, then you need anonymity, not privacy. Neither my setup nor your user.js provide anonymity.
You are undermining my efforts to provide a workable setup that doesn’t break things left and right, and when I say that some of the settings you would suggest are not workable, then this is based on my own extended experience with your user.js script (yes, I’ve used it for an adequate amount of time to make such a statement), and is ultimately my opinion. Maybe my setup is not up to your expectations, to which I would reply that it is not a proof of concept, but something that can actually be used as is.
Maybe I am wrong, but you seem very annoyed by the fact that I am not promoting Firefox like some other people here, but instead use Brave, a browser you don’t seem to like because it is in direct competition with Firefox, or because you don’t like its founder, or because you don’t like the employees, or the logo, or whatever – it’s not like I care. I do wonder though how far your opposition to Brave (which you seem to transfer to me as some kind of projection) will get you. I mean, Firefox is at around 3% market share, down from 30% market share which it had at its peak. Mozilla had to give up their headquarters, and had to fire a considerable amount of its workforce already. Does that seem like a healthy company with a bright future to you, if you take the rose-colored glasses off for a moment? The future does not seem to hold much for Mozilla aside from irrelevancy and bankruptcy, if you ask me. And it’s really on them, there are enough questionable past decisions or even just wrong priorities (especially performance-related) that we could talk about and which have led to that point, but ultimately, for whatever the reasons, we are talking about a 3% market share, more or less irrelevant browser here.
The Tor project is tracking blocking Chromium bugs and if they can resolve them, you’ll have Chromium-based Tor. They will ultimately be forced into it if their Gecko engine can no longer render websites correctly in the future.
You are seemingly berating me for using a browser that you will also be using in five years time, well maybe not Brave specifically, but certainly some form of Chromium. Either that, or you say bye-bye to the Internet as a consequence of Firefox’s predictable demise. My point being – if you want to help improve the privacy of people, or in general to do something useful for society – you should be looking into ways to improve Chromium, or to at least assist people who attempt to do this. Gecko has lost the browser wars which are really just browser engine wars, and it won’t recover as long as Chromium remains open source software that anyone can take in order to create new browsers from it – it will always be the preferred option if only for web compatibility reasons.
Firefox could be much better than Brave for all I care, but let’s say that it would indeed be the case to a degree where it matters and there would be no other reasons that directly speak against using it (application security, overall trustworthiness of Mozilla), I still wouldn’t use it, because I neither use, nor will I switch to, products that will disappear in the mid term with high likelihood.
So what is your goal here? Convince me to use Firefox? Won’t happen, I would have to switch back to Chromium in less than 5 years anyway. Tell others that my setup is bad? Then the real question would be your definition of “bad”, whether that definition is compatible with real world workability and user expectations, and what things precisely could be considered bad. If you can’t name a bad thing in my setup, please, for the love of god, give it a rest.
“But, but, there are things I can toggle in about:config that would elevate Firefox beyond that!” is not something I take seriously as long as these things break websites, or have questionable overall value, I tell you that. Usability is very important to me and to others.
So again, what is your purpose here? Is it something personal? Something against me, or against Brave? Or is it some kind of superiority complex in that you want to show me that a proof of concept is more private than my own setup, a setup aimed at real world workability? What is it? All you achieve here is to a) waste my time and to b) discourage people from improving their privacy in non-breaking ways, chiefly by trying to undermine my credibility (mainly by insinuating that I compare my setup to stuff to Tor, putting it at the very same level, which is ridiculous because I don’t). Great stuff you do here. And again, it’s for naught, you’ll be using something Chromium-based in the mid-term, too. Think about it. I’ve shown you what you can do to help society (in this case: the privacy of others), which would be to improve Chromium in that area. Deep inside, unless you want to quit the web for good, you know that this is the only useful thing to do beyond any short- to mid-term clinging to Mozilla or FF. This debate will soon resolve itself before your very eyes anyway. Just saying, food for thought. You should really question what you are doing here, the purpose of it all, for your own good. You can invest your time in more useful, more long-term ways.
When you can’t logically discuss something, you attack the messenger
For about the 20th time now you keep claiming things about me that you have no way of even knowing, let alone verifying. Martin, please leave this in: I want this here as a matter of record, and also to rebut the misinformation on arkenfox user.js
Your paragraphs starting with “Dude, usually I am not this direct” and the subsequent one starting with “Your GitHub history also shows” are 100% full of incorrect statements. Here is a list of mis-truths, bad assumptions, and innuendo
ME
– You can see/find one public repo on github that by it’s very nature is not meant to be code: so therefore I am not a “coder”, so therefore I am not prolific, so therefore I am not qualified
– You seem to think being a “coder” is a prerequisite for “something”. So for example: bug reporters, testers, QA: are all invalid when they find a flaw or potential problem and report it?
– You seem to think finding a weakness is only valid if you can provide a solution
– You seem to think I’ve haven’t offered potential solutions
– You seem to think using existing tests is a weakness. Do you have something against people who test? Also, there are only so many ways to test something: why re-code the same test? If the test is there, use it. Why is this a bad thing?
– You seem to think I haven’t independently discovered any weaknesses (and provided PoCs) on my own: for example bypassing the randomization in Brave’s canvas. I have done lots of independent (and joint) research and shown new concepts and exploits
– You seem to think having a conversation with a Brave dev is a weakness. Why the hell wouldn’t I talk to them about it? If they want to explain why, that’s them being professional
– You seem to think everyone knows the inner workings of every project, and has the time to get up to speed. What’s wrong with saving time and effort and directly asking? Devs do this all the time – i.e checking in with the person assumed best qualified/knowledgeable on the matter
– You think my knowledge comes from reading “various studies”. How about literally hundreds of research papers, thousands of quality articles, tens of thousands of bug reports and reading code samples, numerous conversations (including in person) with others in the field… not to mention my own work
– You seem to think I owe you some “concrete evidence” about ME – lulz
ARKENFOX
– You seem to think I get all/most my information from Tor Browser. Strange then that the repo adds, changes, and discusses items months ahead of Tor Browser. Strange that some Tor Browser changes have been done based on arkenfox information and research. Strange that many “pre-existing Tor docs” are woefully out of date and yet they are supposedly our sources and yet we differ. Strange also that arkenfox contains items Tor Browser doesn’t. Since I moved it to github, thousands of prefs have come and gone: they’ve all been checked out in timely fashion well before most of them were referenced elsewhere outside of Mozilla code/docs/bugzilla etc – it’s all documented in the repo
– You seem to imply all the repo’s info comes from “easily” found sources and all it’s done is collect other people’s work into a single list. If you look at the repo, you will find that everything is discovered independently via diffs per release, and researched independently. And has been since it moved to github in Feb 2017 – the PROOF is in the repo
– You seem to think the arkenfox user.js is about anonymity: when it’s about really about privacy
– You seem to think you can identify recommended extensions: is this the BS about your claim that you can “trivially” grab extension IDs again? An engine bug (and chromium also has this albeit slightly different: neither are good) has nothing to do with the discussion and is out-of-scope. If you do nothing (no extensions) then you are not making anything better, but if you do something (vetted extension), then you are better off: especially when the vetted extension does not leak a UUID. Why are you recommending extensions then? Hypocritical much? You also seem to suggest these extension UUID flaws mean nothing should be done to counter fingerprinting
So you’ve searched for traces of me and can’t find anything except a github repo. Good. Why are you upset with me? Are you trying to dox me? What are you afraid of – FACTS? Why can’t you discuss technical matters without devolving into personal attacks? Why can’t you stick to a topic?
You don’t know anything about Firefox, you know nothing about arkenfox, and you most certainly don’t know anything about me.
===========
As for the rest: you just keep denying, doubling down, and deflecting
I said your setup doesn’t even come close to what can be done in Firefox: example: FPI/dFPI = i.e all about isolation of eLTD+1 (+scheme) in many areas: not just persistent web storage. side-note: I find your setup hilarious when you keep attacking Firefox as having to be tweaked so heavily in order to be “private”
You reply: to argue that isolating by first party is no big deal. If it’s no big deal then why do Tor Browser use it – answer: because it mitigates linking traffic within that session. Your answer after claiming you can counter it with cleaning cookies, is to use lots of sessions, profiles. That’s not an answer. The answer is call-it-want-you-want (partitioning, FPI, dFPI) is _the_ current best solution, and is why all browsers are building it in (to different degrees): the fact is that it’s been available in Firefox for years as FPI and is superior to what you are trying to achieve. So you want to argue against all the engineers at Firefox, Chromium etc who see a solution that fixes many “holes” – why else would they add it if it didn’t add value?
You keep replying about your experience. It’s not about you dude. Of course you can achieve the same result by opening a new profile, visit one site, close the profile (and either fully sanitize or destroy the profile). I can also do that with Firefox. What part of this confuses you: isolation WITHIN a session? Of course limiting 3rd parties helps mitigate the attack surface. Why are you bringing up basic assumptions?
Even something as simple as “what about users with 100s of tabs open” – the point being nothing is isolated between them: and instead you want to claim that having lots (100s) of tabs open is not a thing: but IT IS. Also, a tab doesn’t have to active for it’s local web storage to be used, or it’s cache checked etc
Almost everything you post is just walls of text of off-topic or incorrect statements, or basic assumptions in order to be argumentative
For example: your take on how scripts go undetected: gifraffe1, giraffe2 etc. As for “random” third party domains: that’s a real thing and cheap too – thousands of them in one case observed in the wild (from memory it was 17000+ domains). So imagine completely random js file names, even completely “random” code (i.e different obfuscation or a “signature” each time = arms race), and maybe “random” third parties. Block lists can only go so far. Of course they help: that’s not what is being argued here. But ignore all that – just imagine when they are all served by the first domain and embedded within JS files that are needed to run the website: key words: EMBEDDED and NEEDED.
I gave hypothetical examples (based on real world knowledge: and it’s an arms race, so it will only get harder) in order to demonstrate why being more-comprehensive is a better strategy, but you want to argue that it’s not. You just don’t get it, do you. A more comprehensive solution vs one that has lots of holes: it’s not about the risk factor, it’s about the strategy. In what world is a solution that covers more attack vectors the equal of one that covers less?
The point is, WHEN or IF a FPing script gets through, then you need real anti-FPing solutions (and maybe heuristics: just like anti-virus software). Instead you want to argue about 3rd parties and other crap
—
> You recommend both in your “arkenfox†setup, fingerprinting protections and uBlock Origin
First of all, I recommend Tor Browser if it suits the end user. But if the user wants to use Firefox, then here’s some info that can help them. uBO is a content blocker: thus it reduces requests and attack surfaces: both for malware and tracking, and speeds up page loads. WHY the hell wouldn’t I recommend it. You seem confused.
—
FYI: The reason I bother to very occasionally point out your BS is your hypocrisy and your continued behavior in spreading falsehoods (like falsely claiming for over a year that Firefox didn’t block any prefetching). Imagine if I did it to all your BS. I corrected your statement on IPv6-only breaking sites, because you directly referenced arkenfox. And I pointed out that your setup to mitigate tracking was inferior to the strategy of first party isolation. And that RFP is vastly superior to Brave’s anti-FPing. All those statements are true. Everything after that is you arguing bogus points mostly full of rubbish
All you had to say was
– “It’s great that all browsers are moving to partitioning everything, meanwhile my setup covers a lot of it and should be good for most people until partitioning lands, and using a one off profile/mode for one off sites solves this. Blocking most third parties also helps here” – and I would have said nothing more
– “this is true that almost all IPv6 sites fall back to IPv4, good point. I was wrong about the breakage” – and I would have said nothing more
– “RFP/Tor Browser’s anti-FP is well advanced and way more robust.. ” – actually, fuck it .. I’m dreaming you would ever admit that I said something true and provided facts
You do realize that people can read what you write, right?
That’s it from me in this thread Martin
@Pants
Oops, I forgot about some things, small addendum:
> spreading falsehoods (like falsely claiming for over a year that Firefox didn’t block any prefetching)
Ahem,
network.dns.disablePrefetch
network.prefetch-ext
network.predictor.enabled
network.http.speculative-parallel-limit
browser.urlbar.speculativeConnect.enabled
…all having the wrong – that is user-hostile – values would like to have a word with you. Please don’t lie, thank you very much.
> Imagine if I did it to all your BS.
Please do, if it has the same quality of your other replies, I have nothing to fear. If that was meant as some kind of threat, I can only laugh about it. I know your type of reply by now, and remain unimpressed.
OK then, not my last comment in this thread then
You’re still attacking the messenger, not the message. Or when you do attack the message, its to nitpick every sentence. This is a very clear sign of someone who has lost an argument. e.g. lulz, of course arkenfox has a Mozilla source: because that’s what it’s documenting
> I said that you having a conversation with him about the basic workings of the code demonstrates that you can’t read the code
First of all that is false. I said I “alerted him to the leak”. I never said that I directly asked him about the code or brave’s inner workings – he offered that up himself – because that’s what professionals do, they like to explain what happened
Even if I did directly ask him (and I didn’t), that does not mean I can’t look up the code, follow it, or whatever you’re trying to claim. You’re saying asking a question is proof of inability: I call BS. It’s almost as if you can’t do logic. I specifically mentioned time constraints and no need to do it: it’s not my job to inspect Brave’s code – that’s their job (but I’m more than happy to let them know of a bug)
> I take it from your write-up that you have never coded a line and now try to explain why that isn’t a bad thing
> I wasn’t talking about the REPO, I was talking about YOUR GITHUB ACCOUNT
Again with the not reading and understanding part. Finding a REPO (because the Thorin-Oakenpants github ACCOUNT is not used for anything else public) but none of the evidence you seek, is a false equivalency. Just because you can’t find my specific work under one handle/account, doesn’t mean it doesn’t exist. That’s not my problem. I don’t owe you anything
> > spreading falsehoods (like falsely claiming for over a year that Firefox didn’t block any prefetching)
> Ahem, network.dns.disablePrefetch
So you’re still claiming a falsehood. Look up network.dns.disablePrefetchFromHTTPS: it’s been default true since FF70, which was released almost 14 months ago. There, proof that Firefox blocks some prefetching by default. The claim that Firefox doesn’t block any prefetching is false Once IPv6 becomes even more relevant, you’ll be doing a 180° and recommend enabling that…
Your claim is that disabling it breaks 5% (now 8%) of websites – I call you out on that as utter BS, and now what? You’re still arguing about it for some reason
> proof
go google it. I’m sick of giving you proof as I have in the past, because you then ignore it and go off on something else. Try this: recently a handful (100 or so) of malicious chrome extensions were found to be using over 15 thousand Galcomm domains – go google that
If you looked hard enough you would see that the holes in Brave’s anti-fingerprinting that I mentioned are documented by Brave now (but my canvas PoC isn’t because I asked Peter not to link to it). Search harder.
You seem to think I have to give you, of all people, proof of everything. Every time I do, you don’t learn from it and revert to the same falsehoods
> What bothers me about your argument is not the basic quality, but the lack of plausibility
Now that is much better and clearer statement that may clear some of your confusion. Although I’m not sure what part of “when”, “evolve”, “arms race” or “imagine” etc you couldn’t follow
Demonstrating some scenarios to illustrate that better solutions are, well, better: i.e. more comprehensive covering more attack surface etc. They are plausible, and doable: just not likely for the average user (e.g corporate surveillance has no need). Take for example in FPing: a targeted script by a three-letter agency. Good to see you finally agree that a more comprehensive solution is better than a less comprehensive one
> What would be the actual benefit here
You seem fixated on number of clicks. No-one cares. We’re talking about linkability implications, not how you got there. If you don’t understand this, or the threat/chance/no-matter-how-small of linkifying traffic that you want to specifically be unlinkable, then go read a book or something. PS: Good to see you finally agree that a more comprehensive solution is better than a less comprehensive one
> WALLS OF TEXT
This is an unfortunate side affect of having to trying to deal with your posts and so much off-topic/side-tangents and misinformation. I’m not even pointing it all out. Do you really want me to address all your BS? Really?
* [Editor: Removed last paragraph, please keep the discussion on point]
@Pants
> You’re still attacking the messenger, not the message.
You really shouldn’t criticize it when you are doing it yourself. It’s a severe case of hypocrisy.
> This is a very clear sign of someone who has lost an argument. e.g. lulz
I don’t gain or lose anything by “winning” here. Is this some horse race where my bets are at stake, or something? Anyway, once you come up with a plausible threat not covered by my setup, I’ll be happy to discuss it.
> of course arkenfox has a Mozilla source: because that’s what it’s documenting
What kind of achievement is that? Anyone can compile a more extensive source into a user.js…
> You’re saying asking a question is proof of inability: I call BS. It’s almost as if you can’t do logic.
Wrong. I say that the type of question you ask are proof of YOUR inability.
> I specifically mentioned time constraints and no need to do it: it’s not my job to inspect Brave’s code – that’s their job (but I’m more than happy to let them know of a bug)
Let’s be real here, even if your job you couldn’t do it.
> So you’re still claiming a falsehood. Look up network.dns.disablePrefetchFromHTTPS: it’s been default true since FF70, which was released almost 14 months ago. There, proof that Firefox blocks some prefetching by default.
Uh oh, it blocks one single form of prefetching now, that renders my arguments totally invalid… Wait, it doesn’t! They could disable the other forms of prefetching as well but don’t, the only question is why…
> I don’t owe you anything
OK, what’s wrong with providing proof of your coding abilities? That’s something to be proud of!
People can read that I am asking for proof and that you fail to come up with proof, people also know that “I don’t owe you anything” is a cheap excuse meant to hide the fact that you haven’t coded a single line of code in your life. Rest assured, I’ll continue to call you out on it, unless you tune down on the arrogance. Your choice.
> Your claim is that disabling it breaks 5% (now 8%) of websites – I call you out on that as utter BS, and now what? You’re still arguing about it for some reason
It’s OK, mate. I am content with waiting for your 180° turn once the setting causes even more problems than it does now.
> Try this: recently a handful (100 or so) of malicious chrome extensions were found to be using over 15 thousand Galcomm domains – go google that
So it was an extension… Weren’t we talking about website tracking? What has malware to do with it? Also, they were likely not dynamically generated from what I read. Stop spreading bullshit, this has little to nothing to with tracking.
> If you looked hard enough you would see that the holes in Brave’s anti-fingerprinting that I mentioned are documented by Brave now (but my canvas PoC isn’t because I asked Peter not to link to it). Search harder.
So they’ve responded to you using a testing suite successfully, that’s good to hear. Why can’t you provide a bugfix after you have identified the issue? Of course, it’s not your job, time constraints, nothing at all to do with your lack of skill… Oops, did I spoil your reply?
> You seem to think I have to give you, of all people, proof of everything.
Isn’t your skill level something to be proud of? Come on, don’t do it for me. Pretend that I wasn’t there calling you out. Pretend that it is for the wider audience of gHacks, surely someone else here is interested in your expertise.
> They are plausible, and doable: just not likely for the average user (e.g corporate surveillance has no need).
If an encounter with them is unlikely in the wild, this is what I call an implausible scenario. Nobody denies the theoretical possibility (even though some of the things you claim Brave doesn’t protect against are actually covered by it, but hey, who am I to judge). But the whole “mountain out of a molehill” stuff is just ridiculous if that is meant to show that my setup is supposedly bad. My suggestions cover all scenarios with medium to high likelihood.
> PS: Good to see you finally agree that a more comprehensive solution is better than a less comprehensive one
Huh? I never specifically denied that comprehensive solutions are a good thing (that would be utterly idiotic), I am still saying that the first line of defense usually suffices and that I do not really care about 1% obscure scripts or something. “Thank you for agreeing with me!” after you putting idiotic claims in my mouth, claims I have never actually made, from which I have now supposedly backtracked (Dafuq? How messed up are you?) is an old trick of yours… Again, in no comment of mine you will find a quote that states that defense in depth is a bad thing, its overall usefulness in the wild notwithstanding, because effectively 90% of the fingerprinting can and will be covered by the adblocker. It’s always the same, lame, old scripts.
> Take for example in FPing: a targeted script by a three-letter agency.
Hahahahahahaha, targeted by a three latter agency? Seriously? Dude, neither your setup nor mine protects against targeted survaillance by three letter agencies. These guys would probably use malware to break into your systems, or do sybil attacks at the network level even if Tor is being used.
> We’re talking about linkability implications, not how you got there.
Yes, and traffic from other Brave profiles IS ISOLATED. Not any better or worse than Firefox Containers. Yes, containers operate within the same session, but there is no benefit to that. Seriously, you can’t bring yourself to admit that containers bring in no advantage whatsoever over separate profiles. Me trying to explain that separate profiles can be easily handled from a usability standpoint goes a long way to show that the only benefit you could possibly claim for containers (ease of use), isn’t one.
> This is an unfortunate side affect of having to trying to deal with your posts and so much off-topic/side-tangents and misinformation. I’m not even pointing it all out.
I was about to say the same thing. Some things you claim do not hold much water.
* [Editor: removed, stay on point please.]
You also once claimed out of nowhere that I supposedly had a Reddit account that earned me a high downvote count (Why would I go there to earn downvotes and get banned? Dafuq?), and when I asked you to point me to the exact Reddit account, thinking that someone is trolling me by impersonating me or something along those lines, in order to verify your claims, you again FAILED TO SHOW ME PROOF. Such proof would have shown gHacks that I am the complete troll you claim that I am, so why didn’t you go through with it? You literally didn’t want to point me to a Reddit account that was supposedly mine anyway… Why shouldn’t I know about my own Reddit account, pretty please? You make up lies of thin air, for all to see.
* Editor [removed last paragraphs, stay on point please]
@Iron Heart
> Yes, and traffic from other Brave profiles IS ISOLATED. Not any better or worse than Firefox Containers.
Containers alone, yeah I can agree
> Yes, containers operate within the same session, but there is no benefit to that.
I hope he’s only talking about isolation
> Me trying to explain that separate profiles can be easily handled from a usability standpoint goes a long way to show that the only benefit you could possibly claim for containers (ease of use), isn’t one.
Are you serious?
They might not be useful to you but…. Dude, you really don’t like Firefox :P
Cheers
@Rnk
Has little to do with me liking or disliking Firefox (To be frank, I wouldn’t even care about FF, if I wasn’t forced to discuss it by people hijacking my posts – the reality out there is that you hardly see it in use anymore.). It should be fairly obvious that I was talking about the isolation aspect, and ease of use to some degree. Different profiles can also isolate just fine, if you only use them for one specific task. Containers, however, also tend to break some stuff (can be circumvented with different full profiles), one example would be cross-site logins. Not sure why that is even a point of contention.
Use whatever suits your needs. If it’s Firefox, which I personally avoid because it can’t even get its own security right…
https://madaidans-insecurities.github.io/firefox-chromium.html
…then that’s great for you!
On a semi-unrelated note, color me surprised that anyone actually follows the back and forth tainted-by-personal-dislike bickering above, you Sir or Madame, deserve a gold medal for your perseverance.
@Iron Heart
Cross-site logins are not an issue with containers, they’re not like FPI, they are actually a good alternative if the later gives issues (Temporary containers).
Considering that with a new profile you have to set everything up again, I don’t see them as a good alternative even for a one-off thing, I would just open an incognito window in that case, or well, if on Firefox, do nothing extra since a couple of extensions handle all the permanent/temporary container switching/deleting. Would like to see an alternative land on chromium desktop, for when I eventually switch if Mozilla keeps messing up, very unlikely thought.
> On a semi-unrelated note, color me surprised that anyone actually follows the back and forth tainted-by-personal-dislike bickering above, you Sir or Madame, deserve a gold medal for your perseverance.
At the beginning I thought I would learn some stuff, I didn’t…
@Pants
I take it from your write-up that you have never coded a line and now try to explain why that isn’t a bad thing.
> You can see/find one public repo on github that by it’s very nature is not meant to be code: so therefore I am not a “coderâ€, so therefore I am not prolific, so therefore I am not qualified.
Misinformation. I wasn’t talking about the REPO, I was talking about YOUR GITHUB ACCOUNT. Those are different things and anybody who uses GitHub knows that. Your ACCOUNT shows no coding history.
> You seem to think being a “coder†is a prerequisite for “somethingâ€. So for example: bug reporters, testers, QA: are all invalid when they find a flaw or potential problem and report it?
Misinformation. I never claimed those were INVALID. This is about your arrogance, not about the fact that lesser achievements are also achievements. Your arrogance doesn’t match your achievements, that’s all.
> You seem to think finding a weakness is only valid if you can provide a solution
Misinformation. I never said that. Again, this is about your arrogance level, not about the worthiness of objectively lesser achievements.
> You seem to think I’ve haven’t offered potential solutions
Not at the coding level. Your coding history is non-existent.
> You seem to think using existing tests is a weakness. Do you have something against people who test? Also, there are only so many ways to test something: why re-code the same test? If the test is there, use it. Why is this a bad thing?
Misinformation. I never said testing was a bad thing. I also never talked about rewriting test suites (dafuq?). I said that if testing is your only qualification, something literally anyone can do, you shouldn’t be arrogant. This is not about the validity of testing, this is about your self-perception, or lack thereof.
> You seem to think I haven’t independently discovered any weaknesses (and provided PoCs) on my own: for example bypassing the randomization in Brave’s canvas. I have done lots of independent (and joint) research and shown new concepts and exploits
You found the Canvas weakness with the usual testing suites, for anything else I would want to see PROOF.
> You seem to think having a conversation with a Brave dev is a weakness. Why the hell wouldn’t I talk to them about it? If they want to explain why, that’s them being professional
Misinformation. I said that you having a conversation with him about the basic workings of the code demonstrates that you can’t read the code, for all to see. Discussions between people who can read code usually leads to viable solutions (in which case talks are useful), you just want to know how it works, and show some testing results anyone else who cared could also have shown, and that demonstrates your skill level. You are able to operate a testing suite. Wow. Reporting test results is good but you also wanted to know how the code works that actually produces those results, and this has me a bit concerned. For deeper insight you need outside info, even if the code is right before your nose.
> You seem to think everyone knows the inner workings of every project, and has the time to get up to speed. What’s wrong with saving time and effort and directly asking? Devs do this all the time – i.e checking in with the person assumed best qualified/knowledgeable on the matter
How stupid do you think gHacks readers are? Looking at the fingerprinting defenses does IN NO WAY require you to look at the ENTIRE code of the browser, this is laughable. That you have to ask about the basic functionality shows that you don’t understand it beyond the results of testing suites. That was my point, you just choose to deliberately misread it.
> You seem to think I owe you some “concrete evidence†about ME – lulz
There is nothing wrong with showing me some evidence that you can code (could just be a link to some repo you maintain or something), which would clearly be something positive about you. You refuse to show it because it literally doesn’t exist.
> You seem to think I get all/most my information from Tor Browser. Strange then that the repo adds, changes, and discusses items months ahead of Tor Browser. (…)
Wow, so you made some config changes ahead of Tor? That’s insane skill levels right there. OK, fair enough, I correct myself: You also use the Mozilla docs as a source! How could I have overseen that!? … Feel better now? I don’t believe for a second that you ever contributed anything that exceeded config changes or the results of testing suites, until you show me otherwise (which, again, would be a good thing about you, nothing wrong with showing me proof – don’t be so shy).
> You seem to imply all the repo’s info comes from “easily†found sources and all it’s done is collect other people’s work into a single list. If you look at the repo, you will find that everything is discovered independently via diffs per release, and researched independently. And has been since it moved to github in Feb 2017 – the PROOF is in the repo
The changes are being documented by Mozilla and that you were able to find the diffs is not an achievement, if I had the time to spare, I could do that as well. Or anyone else for that matter. Of course your work is based on pre-existing documentation, that’s how you get to know about config changes in the first place. And then again, please don’t outright deceive people, I didn’t ask for proof that you can read pre-existing docs, I wanted to know something about your coding skills. Showing me that you can toggle about:config settings after you’ve read Mozilla’s documentation doesn’t quite achieve that yet.
> You seem to think the arkenfox user.js is about anonymity: when it’s about really about privacy
You can’t seem to make up your own mind on that one, for you recommend fingerprinting defenses but also advocate the installation of extensions at the same time. Fingerprinting protections enhance anonymity, the installation of extensions lowers it. If this is about privacy, then you don’t become any more private by fingerprinting protections if your extensions already expose you so much, and are a fingerprinting vector themselves that is easily exploited. So, which is it, privacy or anonymity?
> You seem to think you can identify recommended extensions: is this the BS about your claim that you can “trivially†grab extension IDs again?
I let that bug speak for itself (trivial): https://bugzilla.mozilla.org/show_bug.cgi?id=1372288
That you refuse to acknowledge the issue either shows that you don’t understand it (which is likely considering…) or that you want to gloss over weaknesses of Firefox, neither would be a good thing.
> and chromium also has this albeit slightly different: neither are good
A Chromium extension leak can be non-unique due to non-unique extension IDs, a Firefox extension leak is always unique due to unique extension IDs.
> You also seem to suggest these extension UUID flaws mean nothing should be done to counter fingerprinting
The extensions you suggest shouldn’t be in a setup that is about anonymity, but fingerprinting protections are anonymity-enhancing. So while you can do something against fingerprinting while running extensions, it is snake oil if anonymity is the explicit goal (which defense in depth fingerprinting suggestions seems to imply), because I can already use the extensions to identify you, in case of Firefox even identify you uniquely. Again, anonymity vs. privacy, you can’t seem to grasp the difference and randomly suggest things enhancing both, when sometimes there is direct conflict. Your setup can only support one OR the other, ultimately.
> So you’ve searched for traces of me and can’t find anything except a github repo. Good. Why are you upset with me? Are you trying to dox me? What are you afraid of – FACTS? Why can’t you discuss technical matters without devolving into personal attacks? Why can’t you stick to a topic?
Dude, this is hilarious. First things first, getting to the GitHub commit history of your account takes me ONE(!) single click from your arkenfox repo. So much for “doxing”. As for personal attacks, it was you who said that I have no clue, implying a lack of skill. So I thought to myself: “Wow, this guy claims to be more knowledgeable than I am, let’s take a quick look at his GitHub commit history utilizing one single click. Surely her coding skills ill back that one up.” And… nothing. about:config changes that anyone can do, yes, but not a single code commit by you, on GitHub, where most open source devs would at least have a small commit history… That you can’t get yourself to say that you are a coder shows to me that I was guessing correctly here. And off-topic, Pants, how are your not-so-polite comments about my skill level (while having a fairly laughable skill level yourself, that is), “on-topic”? That’s going off-topic as well, I merely responded by exposing your own skill level. You asked for it, so here it is.
> You don’t know anything about Firefox, you know nothing about arkenfox, and you most certainly don’t know anything about me.
All three couldn’t be more wrong. I have used Firefox, I have used arkenfox including its functional deficiencies and funny recommendations, I know that you have no GitHub commit history (as if that was a secret, your GitHub account is public and accessible from the arkenfox repo). And honestly, you are not that important to me, to any degree where I would want to know more. Again, I am merely replying to your own personal attacks by exposing your non-skills. If you had any, I am sure you would have proudly put them in show by now, judging by your character. Shame that they don’t actually exist. Tune down the arrogance to bearable levels, and I won’t have to hint at you not being very prolific in the coding area again.
> I find your setup hilarious when you keep attacking Firefox as having to be tweaked so heavily in order to be “privateâ€
You know that some of the settings I suggest are already the default, i.e. don’t need to be toggled, right? Your setup list is much longer than mine and more or less only considers the entries that need to be changed, with very few exceptions.
> So you want to argue against all the engineers at Firefox, Chromium etc who see a solution that fixes many “holes†– why else would they add it if it didn’t add value?
Again, don’t put words in my mouth (your favorite hobby, and your favorite comeback it seems). Show me where I said that isolation is useless, I am looking forward to it! I said that Firefox’s current solution is buggy and doesn’t work in the real world, which is also true. I don’t use things that are not workable (yet), and neither do others who need to actually work with their browsers.
> What part of this confuses you: isolation WITHIN a session?
What would be the actual benefit here? Opening a new Brave profile and a new Firefox container tab takes roughly the same amount of clicks. In Brave that would technically be a different session, I agree, but that’s totally irrelevant in this context, where I was merely talking about usability(!). Firefox’s approach is also buggy in comparison, please acknowledge it, or do I have to point at Bugzilla bugs again to show that you are wrong?
> and instead you want to claim that having lots (100s) of tabs open is not a thing: but IT IS.
That would lead to a kernel panic with high likelihood, haha. I doubt that Chromium remains very stable with hundreds of tabs, unless you have insane amounts of RAM. You come up with things that are totally implausible in real life to prove a point. Color me surprised.
> Almost everything you post is just walls of text of off-topic or incorrect statements, or basic assumptions in order to be argumentative
You sometimes seem to lose sight of basic assumptions in favor of showing me proofs of concept that are very much implausible in any real world situation. And I think your OWN walls of text deserve no further comment, or do they? Don’t hypocritically criticize me for things you are doing yourself.
> As for “random†third party domains: that’s a real thing and cheap too – thousands of them in one case observed in the wild (from memory it was 17000+ domains). So imagine completely random js file names, even completely “random†code (i.e different obfuscation or a “signature†each time = arms race)
Proof…? Also, that being undetectable seems implausible to me when it was detected (otherwise how would you know about it?).
> just imagine when they are all served by the first domain and embedded within JS files that are needed to run the website: key words: EMBEDDED and NEEDED.
If something is NEEDED you better EMBED IT YOURSELF, because if you get it from third parties and depend on their updates, you have to update your website too most of the time in order to react to changes. Nobody ever does this, at least not voluntarily and not in places where it can be avoided, which is why scripts are still easily separable from websites for the most part.
> I gave hypothetical examples (based on real world knowledge: and it’s an arms race, so it will only get harder) in order to demonstrate why being more-comprehensive is a better strategy, but you want to argue that it’s not. You just don’t get it, do you. A more comprehensive solution vs one that has lots of holes: it’s not about the risk factor, it’s about the strategy. In what world is a solution that covers more attack vectors the equal of one that covers less?
The stuff you suggest is fairly implausible and I strongly doubt that whatever you propose is widely being used by advertisers. Ads are usually served in conjunction with tracking scripts (although there is a number of tracking scripts without ads being served), if it were such a big problem as you make it out to be, people would be seeing much more ads while using uBO already. Again: The things you propose, who really does this in the wild? Show me examples, show me proof that exceeds studies or testing suites. Again, nothing wrong with showing me proof, so don’t be shy.
I never said that defense in depth was a bad thing (thank you for putting words in my mouth, again), I questioned whether or not I should care about a minor number of obscure scripts that could potentially get past the initial line of defense (assuming they even target Brave, which is pretty laughable in its own right considering the market share…). It’s not worth it considering the fuss you make around it. It’s good that it’s there, but that’s it, and that should be true for most users out there.
> The point is, WHEN or IF a FPing script gets through,
Never happened here, not even on GAFAM websites. Again, show me some real world script not out of a testing utility that is not already on the EasyList or EasyPrivacy list. What bothers me about your argument is not the basic quality, but the lack of plausibility. Why should I feel threatened by some obscure script that is likely first party, never to been again on other websites? Give me a reason to care about “It’s great that all browsers are moving to partitioning everything, meanwhile my setup covers a lot of it and should be good for most people until partitioning lands, and using a one off profile/mode for one off sites solves this. Blocking most third parties also helps here†– and I would have said nothing more
But you said lots more… Because this is exactly what I myself said. I also said that the name dropping you do is not very impressive considering that all browsers are implementing some form of partitioning, Chromium engineers are currently working on cache partitioning, for example. You make that sound like a Firefox ad when it’s really a cross-browser effort. It seems you deliberately want to misunderstand me for – at times – cheap comebacks und gotcha moments, or worse to make me look worse than I am. Please stop, I assume you have the ability to read, and there usually isn’t much vagueness to the things I say. If you misunderstand them, you WANT to misunderstand them.
> “this is true that almost all IPv6 sites fall back to IPv4, good point. I was wrong about the breakage†– and I would have said nothing more
Dude, IPv6 is meant to replace IPv4 and is on the way of doing so, you recommend disabling it, which is an insanely bad usability choice even now. Once IPv6 becomes even more relevant, you’ll be doing a 180° and recommend enabling that… Of course you will be saying that you only do that to improve usability, but what you fail to see is that this recommendation is hampering usability even now. And that’s not even considering the entire container mess, I sincerely hope people never need any cross-site login with those active…
> “RFP/Tor Browser’s anti-FP is well advanced and way more robust.. †– actually, fuck it .. I’m dreaming you would ever admit that I said something true and provided facts
Where did I say that Tor’s anti-fingerprinting mechanisms are inadequate, where did I say that Brave was a Tor replacement? Please show me, I am quite curious. If you can’t demonstrate where I said it, because it once more doesn’t exist, would you be so kind to NO LONGER PUT WORDS IN MY MOUTH, thank you very much. You insinuate that I said it in the hopes that it will make me look stupid, and then feign sorrow about me apparently not admitting I was wrong about things I have never claimed in the first place(?). Is that how it works? This is some A+ manipulation technique, but it’s also quite f*qed up if you think about it. I mean, what I kind of logic is that? I can’t admit that I was wrong about things I never claimed, of which you only say that I claimed them, in order to make me look stupid and / or worse than I am. Sorry, I really can’t admit that I was wrong about things you put in mouth.
> You do realize that people can read what you write, right?
I am GLAD about that, you know. I have nothing to hide, and don’t utilize trickery, or feign misunderstandings, or put words in other people’s mouth, or mount personal attacks so that I can then complain about the comeback (even claiming the comeback was the initial personal attack), or… You seem to forget that people can also read your stuff, Pants, and the duplicity is showing. I think the way you conduct things here hurts your reputation more than it helps it, unfortunately. You also ignore my last comment where I tried to talk some sense into you (In retrospect: Why dud I even try?), and made it clear to you that this argument is utterly pointless.
> That’s it from me in this thread Martin
Why are you talking about the moderator who is more or less in the “off” here, so to speak? What do you expect? A pat on the back? What a joke…
In Pants’ manner of talking, without expecting a pat on the back:
That’s it from me in this thread Martin.
> That would lead to a kernel panic with high likelihood, haha [snip] You come up with things that are totally implausible in real life
Number of tabs
– go to https://telemetry.mozilla.org/
– click of Measurement Dashboard
– select FX_SESSION_RESTORE_NUMBER_OF_TABS_RESTORED
That’s at a quick count about 20% of users who use session restore do so with more more than 20 tabs, there’s even about 2% with more than 500 tabs the number “100s” actually doesn’t matter, and the tabs don’t have to all be fully loaded and active: the point was that with multiple 1st parties the chances of cross site tracking increases. First party isolation (partitioning whatever) solves that
Brave + canvas
– https://github.com/brave/brave-browser/issues/12069 : this is the brave issue where I let Peter know (and I showed him the PoC) that can bypass the canvas randomization and still get useful entropy (this is not the same as bypassing it completely). If I didn’t show him a PoC then why did he agree it was an issue and say “the concern is about how reversable canvas fingerprinting protections are (answer, not very hard to reverse!)”
– In the same ticket later on (Oct 21st) I alerted him to the fact that canvas was completely by-passable in iframes: you’ll find that I was the first to report this (there is no separate ticket), and he did a patch (Oct 28th)
– https://github.com/brave/brave-browser/issues/12453 : after his initial patch, someone else reported that it was still leaking and this will give you a link to the patch on Oct 28th
—
You keep claiming that I make things up
You keep demanding proof that I “code”? WTF is even meant by that? Do you mean that I have to have contributed code to gecko, or to chromium in order to be valid? That’s what the gecko/chromium/brave engineers are there for.
Here: be happy: I have not ever committed any of patches to Gecko or any other browser: I actually declined when given the opportunity, as I am on focused on other areas, it’s not my job, and I don’t NEED to. Does that make anything else I have said untrue? Of course not. Does that mean I don’t know how to “code”? Of course not. Does that mean that I didn’t make suggestions for solutions or that one or two weren’t even used? Of course not. Your logic and assumptions are just insane.
I do not make things up. I don’t even need to give you anything: it’s right there: go look up how brave randomizes the user agent and you can see that it can be undone. Go look at the brave issues where Peter acknowledges that canvas can be bypassed in iframes, and that randomizing only one of three channels can also be bypassed (therefore it can be reduced to one of three possible real results: and there are other ways to bypass this even further and leverage entropy across all domains which I’m not going to discuss with you)
@Pants
Uh oh, a whopping 2% with 500 tabs open? That’s totally rebuking my argument, absolute mainstream numbers… At that point, either the browser or the entire OS would become unstable considering the hardware configurations most people buy. Just saying.
Not sure why you are showing me the GitHub issues where you presented the results of your testing. Anyone can run Brave through a testing website. Proof of that assumption? The other guy that reported the issue not too long after you… Some people care, which is good, but again, anyone, I mean literally anyone, can go to a testing website and report the results.
That you do not understand the browsers at the code level is a big problem, because the testing websites do not tell you the whole story. A protection that ostensibly works during your testing can fail in other circumstances (other approaches to circumvent it, for example), and you are neither able to predict the failure nor to fully understand the failure without being able to interpret the code. It’s just what it is. Now, that doesn’t make anything you say untrue by itself, but it shows that you have limited insight, limited insight that in no way matches your claimed level of expertise (and / or how you apparently perceive yourself).
Do you know whom I would consider “real” experts, so to speak? M.C. Straver, developer of Pale Moon, has deep insights into the inner workings of the code and has developed canvas poisoning for Pale Moon himself. Has also written support for various web standards in his browser. An expert. Daniel Micay, currently working on one of the most secure Android variants – GrapheneOS – hardened the memory allocator / higher exploit mitigation of Chromium considerably and has proposed similar code to Mozilla devs. An expert. Just two examples, to give you an idea…
Now you: You are informed about the current state of privacy infringements on the web from having read various studies and presumably other material, you have proven that you are able to read the Mozilla docs and you give recommendations for settings on a continual basis more or less based on that.
See the difference? I understand that you want to be respected for your efforts, but you can’t force it. I told you now which level of expertise I would have considerable respect for (and for good reason), and you just fall short. That’s not an insult, mind you, it’s a fact. Doesn’t mean your work is worthless, but it’s not fantastic (or any other lofty attribute you might imagine), either. It’s an abbreviated version of what I can find in more detail in Tor’s documentation. As for myself, I do not explicitly claim any(!) kind of higher expertise and do not expect people to grovel at my feet (i.e. to consider me an expert), so there you go. But, suffice to say, if I were in your shoes, if I had your limited level of insight, I would NOT consider myself an expert. Not even close.
Usually I am not comfortable with talking to people like this, but your attitude, lack of realistic self-perception, and aggressive tone force the issue. I am done here.
IH: tens of thousands of domains… i call BS
Me: here’s an example of how tens of thousands of domains were used
IH: so it was extensions .. not relevant blah blah
Me (if I could be bothered): this guy must be thick, he misses the domains part and focuses on that particular case’s delivery mechanism instead. Also there are other ways to very quickly accrue thousand of “random” domains
IH: 100s of tabs is NOT a thing
Me: here is some telemetry that PROVES otherwise: also it’s not about the 100’s, it about multiple tabs + multiple first parties
IH: OMG 2% have more than 500 tabs … computers explode at that point
Me (if I could be bothered): um, telemetry says the computers didn’t explode, and I even mentioned earlier to help you out, that not all tabs are active or loaded, and going even further back … the WHOLE point was that REAL solutions cover ALL use cases. 20% of users with 20+ tabs or whatever is a use case. 5% of users with 50+ tabs is a real world use case – and so is, clearly 2% with 500+ tabs
Me: points out IH claimed erroneously for over a year that Firefox doesn’t block any prefetching
IH: lists some prefs and doubles down
Me: lists a pref that has blocked HTTPS prefetching for the last 14 months PROVING IH wrong
IH: wha wha wha
If you’re going to make statements, qualify them. Saying “Firefox doesn’t block prefetching” is false. Anyway, you’re such a hero, and super knowledgeable about Firefox, flip the extra pref then. Big deal. It’s not even that much of a concern considering the amount of HTTPS traffic and that the prefetching is isolated (with FPI.. and now partitioning). You’re always so concerned with such trivial minor things.
IH: IPv6 disabled breaks 5% of sites
Me: not true, sites fall back to IPv4
IH: changes attack starts babbling about when IPv6 usage increases
Me (if I could be bothered): just because usage may grow doesn’t mean they don’t continue to support fallback to IPv4. All prefs are always being re-evaluated. WTF does this have to do with anything? Oh I get it, keep arguing about pointless things.
Me: facts
IH: bash arkenfox, wha wha
Me: more facts
IH: wha wha bash pants .. where’s your coding? wha wha
Me: what an idiot!
IH: proof or I call BS
Me: here’s the brave issue which shows I gave Peter a PoC that analyzed and detected the randomized channel in canvas, and bypassed it, as confirmed by Peter
IH: don’t know why you’re showing me that issue, and anyone can run brave thru a test suite
Me (if I could be bothered): I’m not fucking using a test suite, I’m not fucking testing brave
Me: I don’t actually test Brave, but happy to let them know I see something
IH: anyone can do that, someone else even listed the bug after you, you’re not special, you can’t code wha wha
Me: OK fine, maybe i WONT FUCKING EVER TELL BRAVE ABOUT A LEAK AGAIN (and I’m not even looking)
Me: your setup isn’t as good as Firefox can be e.g. FPI/RFP
IH: whaa whaa FPI isn’t superior
Me: shows it handles far more items and far more use cases: same with RFP
IH: well I’m happy with 90%
There’s just so much more, but that last one sums it up – that’s it right there
EVERYONE .. IRONHEART IS HAPPY WITH 90% EFFECTIVE SOLUTIONS. So you’re happy with 90% – good for you, go enjoy that.
I’m into REAL and more comprehensive solutions – for ALL users, for ALL use cases. Not your shitty sanitizing extension. Or your currently massively inadequate over-hyped “farbling”
Oh, and IF cross-login is a problem on some sites for some users with FPI in Firefox (you seem to think this is some fatal flaw: when it’s behaving exactly as designed), they could, you know, like you said, it’s so easy, just use another profile (or secondary browser). Meanwhile, in TB it fits just fine, no one has really complained much, if at all: so no-one has bothered to look too much more into it. FPI is NOT front facing in Firefox and for some people it’s fine, for others that may mean a couple of site login problems. That’s what dFPI aims to solve to make it front-facing for Firefox users, who have different expectations
There’s just so much insanity in your logic. Not to mention all the other crap you bring up that isn’t even relevant. You go stick to your 90% solution and let the grown ups talk.
@Pants
One minor thing…
> Or your currently massively inadequate over-hyped “farblingâ€
You can’t seem to understand the difference between privacy and anonymity. Still. After all the explanations I offered. Jeez, here we go again.
You have to make your mind up: Are you trying to become some wannabe Tor configuration where you aim to provide anonymity, knowing that you can’t provide it at the network level (at which point the quest for anonymity already becomes a total farce, but that’s besides the point)? If so, you should scrap all extension recommendations from your repo, because those are already a fingerprinting vector with which you are uniquely identifiable, even if all the other fingerprinting vectors are being covered in an A++ manner.
If your setup is about privacy (like mine), perhaps you shouldn’t rave on and on about Brave’s fingerprinting protections being supposedly ineffective*, because it doesn’t matter. An obscure fingerprinting script that is not covered by the adblocker will be able to use extensions as a vector, on Firefox even more so than on Chrome.
Don’t you consider it a bit absurd to tell me that Brave’s fingerprinting protections are supposedly inadequate* when it totally doesn’t matter as long as I have extensions installed? I repeat: THAT’S ABSURD!
If anonymity was the goal, both you and I have FAILED and should point to tools like Tor. It’s clear to me that anonymity can’t be the goal when discussing any(!) Brave or Firefox setup (= general use browsers that fail to cover the network aspect of anonymity), but it seems to be unclear to you.
*This needs a qualifier, I think. There are studies which show that farbling is effective for a range of fingerprinting vectors, here is one:
https://hal.inria.fr/hal-01527580/document
Writing the following well in advance to deflect any insinuations you happen to come up with now and then when discussing Brave (not that this would stop you, I know):
Does farbling work for all fingerprinting vectors? No.
Does Brave Software claim to have invented it? No.
Is it the only anti-fingerprinting method Brave uses? No.
Did Brave Software ever claim it was the only anti-fingerprinting method Brave uses? No.
Now that this is out of the way, it should be obvious to any coder that BUGS HAPPEN. If you can demonstrate to me that the anti-fingerprinting method fails because it was designed that way(= fail by design), I’ll be happy to call it “inadequate” even though it hardly matters in a setup that never was about anonymity (see above). If Brave Software had no opportunity to tackle the issue yet, or if an ordinary bug is the reason for fingerprinting protections failing to work as expected, one should treat them like any other software project – report the issue, let them fix it. I don’t really expect you to understand the difference between fail by design and fail by bug, though, because to differentiate the latter from the former you’d have to have the ability to read code.
If you call something “inadequate”, perhaps you should be clarifying whether you talk about the specific method for a specific fingerprinting vector being inadequate, or whether you just consider Brave’s specific implementation inadequate. Again, not that it matters, because you know that any anti-fingerprinting work (beyond what adblockers would do anyway) is pretty much pointless because you and I deliberately introduce fingerprintable extensions in our SETUPS THAT ARE ABOUT PRIVACY AND NOT ANONYMITY.
Of course, not all fingerprinting scripts will be targeting extensions… But the stupid common ones targeting only canvas are already on my adblocking lists most likely, you were specifically talking about the ones that are likely self-written by determined adversaries, and yeah, those would likely also target extensions. At which point our setups fail.
@Pants
Funny comedy you craft there, but even if you deliberately stupidify (no other ways to put it) what I say, your points don’t ring any more true.
– No, it is not easy to accrue thousands of domains provided you want them to look legit and not like outright malware domains (which is what they were, in fact), there is fraud detection, and real businesses operating within a legal framework do not sell you thousands of domains just like that, without giving it a second thought. They have departments for that, which would look at your case. I call BS. Such behavior is more or less limited to malware, and by extension to domain vendors who sell to malware devs. This is not something your pitiful user.js can solve (in case you don’t realize it), this would be a case for antivirus solutions.
– One form of prefetching that Firefox now blocks (Out of how many? Was it six or or even more?) does not totally invalidate my previous argument that Firefox does not block any kind of prefetching. If anything, this recent development would force me to state that Firefox now only blocks one form of prefetching, out of many. This doesn’t improve its standing by much, you know. But hey, it’s good enough for a typical “It’s not allowing ALL forms of prefetching, it blocks ONE out of the bunch now! Yippie! You were so, so wrong!” Pants moment. Btw, in actuality, I’d have to leave the one sane setting as is, and I’d have to change all the others which still have the user-hostile values by default. You have it the other way around in your comment, just saying.
– The intention of IPv6 is to supplant IPv4, if you would kindly use your brain cells, you could already derive that info from the very names. IPv6 blocking will only become more problematic as time goes on. If you deny that, you frankly have no clue (avoiding the “idi*t” term you just used on me, not going to return the favor as it’s just beneath me). You can demonstrate to me now that websites might (emphasis on “might”, not in all cases) fall back to IPv4, but it won’t last and the signs are already showing. But whatever, it’s not like I can be bothered. I am content with weathering that one out and just let the passage of time inevitably prove you wrong.
– FPI handles one more use case, which is to use isolation within the same session or in terms of the UI, in the same window as tabs (before you go all wha wha again, I know that session ≠window). That’s not “far more use cases”, it’s one more use case when pitted against a profile exclusively used for a single purpose. And no, it’s not covering more items, you are just lying with that one. There is nothing a container could cover that a full new profile wouldn’t cover. Please understand that.
– If you didn’t run Brave through a testing suite, how did you diagnose the issue then? And anything beyond a testing suite / website is beyond your skill level. I know your skill level by now, as you are not trying to hide it anymore.
– I have explained already why understanding the code is relevant, no further comment. Nope, cross that out, one further comment: The time you invest in snark and writing comedy could easily go into developing skills that would actually validate you when you call yourself an expert next time.
> You’re always so concerned with such trivial minor things.
Says the guy who literally digs out a single Firefox pref to demonstrate to me that one of my claims is not 100% true anymore, but only 90% true since recently, thanks to a very minor development I was not aware of (again, kudos!). Do you look in the mirror while you write this, or from where else would you derive such assessments?
> EVERYONE .. IRONHEART IS HAPPY WITH 90% EFFECTIVE SOLUTIONS.
My solutions are not 90% solutions, they are closer to 99% solutions if we exclude the network level (which your “arkengem” or what was it called user.js doesn’t cover, either). The rest, i.e. 1% threats that users are unlikely to encounter in the wild, I gladly leave to you, knowing that the solutions you propose break more than they solve. Quite literally.
> (you seem to think this is some fatal flaw: when it’s behaving exactly as designed)
There is one problem with that: Websites are not being designed with FPI in mind, which is why…
> they could, you know, like you said, it’s so easy, just use another profile (or secondary browser).
…you need a full profile to unbreak some websites (ironic…). What that means is that this is not fit for purpose, let alone mainstream usage (OK, granted, the latter will never happen anyway – unless Chromium does it, too).
> let the grown ups talk
Grown-ups, as in people with actual experience in the field that understand the protections they talk about at a deeper level? Because that would clearly exclude you…
Not sure to how many fairly arrogantly phrased postings of yours I have to react until this ends, seems you have inexhaustible time on hand. My, my…
Why are you still talking?
Example of your useless irrelevant dribbling: “you need a full profile to unbreak some websites” .. what do you not understand about profiles? So it’s OK for you to use a new profile to isolate absolutely everything (assuming your don’t leak cross-domain in all your tabs), but it’s not OK for someone who chooses to use the rock solid doing-it’s-job FPI in their main profile and to use a second profile that is slightly more relaxed. WHAT A HYPOCRITE
Another example: I’ve been talking about FPI/dFPI all this time…. and you keep talking about containers when you reply. Someone else points out that containers are not FPI etc and it’s all “ok mate good to hear”
Another example: “My solutions are not 90% solutions, they are closer to 99% solutions” – that’s NOT what you said, you only claimed with any certainty 90%. Also, no one cares about YOU .. what about all use cases? Whereas, I know for a FACT that FPI (and RFP) by it’s very nature and design can only be higher that whatever you’re claiming
Another example: you’re still banging on about domains. The point was to illustrate that blocklists are not a cure-all. They will never be as robust as actually tackling the fingerprinting itself. Whether it’s 500 domains, a mutated poly-morphous stealth ninja ghost script from hell … using a new/1000/a-billion new domains .. who cares. You’re missing the point entirely
And you’re still claiming weird shit about arkenfox. And you’re still claiming things about me that you have ZERO way to verify. You’re clearly upset about being proven that a lot (in fact almost all) of what you say and claim about Firefox is false or misleading
So, yeah .. go and be happy with your inferior setup. Also, lulz at you being upset at someone “hijacking” your comments – you’re being doing it for years spamming Firefox articles with repeated rubbish. If you don’t like it, don’t post BS
@Pants
> Why are you still talking?
Exposing your BS, mainly.
> but it’s not OK for someone who chooses to use the rock solid doing-it’s-job FPI in their main profile and to use a second profile that is slightly more relaxed.
Huh? Learn to read. I never said that it wasn’t OK, I said there was no credible advantage to it. That’s not quite the same thing.
> Another example: I’ve been talking about FPI/dFPI all this time…. and you keep talking about containers when you reply. Someone else points out that containers are not FPI etc and it’s all “ok mate good to hearâ€
FPI = container created for each domain, invisible to the user.
Do you actually know what you are talking about? FPI is the concept of a per-domain container.
> that’s NOT what you said, you only claimed with any certainty 90%.
Uh oh.
> Also, no one cares about YOU .. what about all use cases?
Show me a plausible use case, then. 2% of people using 500 tabs or something is not convincing. These people can use your suggestions, even though the breakage this will cause will likely make them stop using Firefox out of frustration, reducing the tab count to 0.
> you’re still banging on about domains.
You seem to like fictitious dialogues, here is one for you:
Pants: You can be tracked using random domains or random script names, they can even be dynamically created.
Me: Implausible, good luck finding someone selling you thousands of domains legally just like that. Also, random script names are hardly a thing because this is extremely hard to manage if you have to rename or re-sign your scripts on a per-user or even per-visit basis.
Pants: But, but, malware extensions…
Me: What does malware have to do with that? OK, maybe an extension developer with bad intentions bought thousands of domains from a shady source, what of it? Also, they were not dynamically created. That’s a job for your AV solution, not for arkengem! It’s certain that this can’t be compared to tracking and that tracking can’t be performed in that manner.
Pants: Stop talking shit about my arkengem! I created this with the intention of blocking implausible tracking scenarios!
Jeez…
> They will never be as robust as actually tackling the fingerprinting itself.
Well, for your tracking protections to become mildly interesting, websites would first have to stop getting the same, lame, old scripts from the usual third party sources. Until then, the adblocker just works for 90%+ of all cases.
> And you’re still claiming weird shit about arkenfox.
It’s not a secret that arkengem causes more problems than it solves. I am also sure that I am not the first one saying that.
> And you’re still claiming things about me that you have ZERO way to verify.
I said that you can’t code with all the associated lack of understanding, you admitted that you can’t code in one of your comments above. Is further verification needed?
> You’re clearly upset about being proven that a lot (in fact almost all) of what you say and claim about Firefox is false or misleading
So far, if I may remind you, you have shown to me that Firefox now blocks one form of prefetching instead of allowing them all (wohoo!). I am willing to correct my statement of it allowing all kinds of prefetching as a result, from now on I’ll say that it blocks one type of prefetching while still allowing all the others. Since it still allows various other forms of prefetching, the vast majority even, I don’t see how it blocking a single form of prefetching now could possibly invalidate my argument?
As for the extension leak – I showed you the Bugzilla bug, it’s clear that it’s a problem. You never replied to that because there is nothing left to discuss here. If even the Mozilla devs admit the problem, it would be funny for someone like you to claim that it isn’t one.
> So, yeah .. go and be happy with your inferior setup.
*sob* That I seemingly* can’t defend against obscure scripts and other irrelevant forms of tracking that won’t be encountered by me in the wild truly is disheartening, I tell you that.
*I say “seemingly” because good luck finding a script that specifically targets Brave’s weaknesses.
> Also, lulz at you being upset at someone “hijacking†your comments – you’re being doing it for years spamming Firefox articles with repeated rubbish. If you don’t like it, don’t post BS
You hijack my comments under a Brave-related articles, how is that any better than what you claim I do? You have yet to show where I have ever claimed BS, some things you claim that I’ve said, and which would indeed be BS, turned out to be a result of you putting words in my mouth. All those novels you write here, wasting my and everyone else’s time in a fairly outrageous manner, and you have yet to show that anything I have said is invalid. Good job.
You actively hijack comments of mine where I try to help others out, in order to argue with me over the corpse of a dead browser (3% market share Firefox)… Some personal beef, or do you just like to pick fights? Which is it? What you do to my posts is not much better than what is commonly considered trolling, hell, sometimes it IS trolling! Please stop, nobody cares. I certainly don’t, not about you, not about arkengem, not about Firefox.
I guess I made the mistake of warning someone of some highly questionable recommendations you give in your pre-configured user.js, uhm I mean “template” of course, because those WILL be breaking certain workflows. In the future, I’ll just let people experience this stuff themselves, so that it will be upon you to discuss with them about the breakage you cause.
Sheesh, you’re still talking?
> Until then, the adblocker just works for 90%+ of all cases
So you’re 100% agreeing with me that it’s an incomplete, inferior solution. Your words, 90% (the + means nothing, the highest you’re claiming with any certainty is 90). I don’t know where you’re getting your figures from – have you mapped and analyzed the entire internet or something? Give yourself an extra 5%. Call it 95%. Go on.
I’m not bringing up extensions or malware – that was an example you ASKED for: to illustrate that new/unknown domains (the number is meaningless but I did say 1000s and there is one that used 1000s) are easily gained/set-up and blocklists are a game of whack-a-mole.
It’s as simple as this: fixing the underlying problems vs treating the symptoms: e.g. the actual fingerprinting vs blocking known scripts, fixing the actual tracking mechanisms vs trying to put bandaids on it like sanitizing after the fact when the damage may already have been done.
One strategy/solution is superior to the other (or in the case of blocklists is only a first step in the overall solution)
> Show me a plausible use case, then
Plausible? I went further than that – I gave you proof that it really ACTUALLY happens. Multiple cross-domain tabs in a session that can share trackers. Without FPI there is risk. It doesn’t have to be 500 tabs, or 100s – the number once again is not material. So I used “100’s” in my comment to bring up multiple domains in a session and you’re fixated on it. That’s not the important bit, but you asked for proof. I give you proof that it’s a real thing, and now you’re fixated on the number 500.
The number that is important is TWO. Two different domains in the same session without FPI carries RISK. Forget about session restore (which is a snapshot at close), how about 99% of users would have more than one domain opened in a session: the tabs don’t have to always open, loaded, or active, as long as persistent data persists. So sanitizing on domain close helps, but it doesn’t do anything while multiple domains are loaded. It’s not a complete solution
As per my first comment, your setup is inferior to what Firefox can achieve: e.g. FPI/dFPI/RFP. Can you achieve the same re FPI/dFPI with a new profile – almost: but it doesn’t cover the RISK of multiple domains in the same session. Can you defeat known scripts with blocking and naive scripts with farbling – of course: but it doesn’t cover unknown and smarter scripts = a RISK.
So your choice is a decision for you to make based on RISK, and you’re happy to be 90% covered (again, this is your figure you claim for you in your setup: call it 95% if you want), good for you: be happy with your inferior solution: meanwhile Tor Browser and Firefox engineers are working on REAL solutions for ALL use cases
You clearly hate Firefox with the passion of a thousand burning suns, so you do not have the option of FPI/dFPI/RFP. That’s your choice. So you HAVE to make do with what you can. But that _still_ doesn’t even get it near what Firefox can do.
Are you going to continue to argue that FPI/dFPI are _not_ more comprehensive and a superior solution than a sanitizing extension or even using multiple profiles (there is still risk in using a separate profile).
@Pants
> Sheesh, you’re still talking?
Yeah, still exposing your BS. How many times will you bring up that question? Stop the BS, and I stop the replies. It’s that easy. You have no say in when I am allowed to talk.
> Your words, 90% (the + means nothing, the highest you’re claiming with any certainty is 90).
Again: Uh oh.
And you are the one talking about number fixation, my my…
> I don’t know where you’re getting your figures from – have you mapped and analyzed the entire internet or something?
Dude, there are databases showing you the most used trackers, how many websites use them, what percentage of the web in total uses them, whether or not websites deploy more than one tracker etc. Do the math, I won’t do it for you.
> to illustrate that new/unknown domains (the number is meaningless but I did say 1000s and there is one that used 1000s) are easily gained/set-up and blocklists are a game of whack-a-mole.
This example is fairly asinine because it can’t be applied to tracking. It should be obvious to someone with your expertise(?), but I am telling you why regardless:
– Firstly, the extension author bought thousands of domains and coded the extension in a way that would allow it to connect to them, i.e. they were hardcoded. Your claim that they were created dynamically is BS, and yes, I looked up the case you mentioned.
– Secondly, the extension was active on all websites (it was not limited to a single website), so it spied on users on all websites, reporting the data to the thousands of domains you mentioned.
You are telling me this is the same thing as dynamically created domains which are deployed on various websites? I don’t even know where to start, but: It should be obvious that an extension slurping data no matter on what website you are is not comparable to how an ad network which has to actively deploy thousands of trackers and associated domains to websites would operate. Not at all.
> Multiple cross-domain tabs in a session that can share trackers.
Eh, sure, if they aren’t getting blocked (extremely likely).
> Without FPI there is risk.
*minimal risk
> So sanitizing on domain close helps, but it doesn’t do anything while multiple domains are loaded.
Eh, it seems you do not understand my point:
– Most trackers are already on blocking lists.
– No third party cookies.
– That leaves irrelevant stuff that’s mostly first party.
The solution for an irrelevant problem (FPI) degrades user experience and causes more problems than it solves. Does that mean it is a bad idea? In principle, no. However:
– I don’t care because low likelihood.
– I actually want to use my browser.
I don’t know how else it can be explained to you. I did never claim that comprehensive solutions are bad (why do you insinuate this all the time? Please stop putting words in my mouth…), but they cover irrelevant scenarios, and break stuff, those are good reasons not to CARE.
> As per my first comment, your setup is inferior to what Firefox can achieve: e.g. FPI/dFPI/RFP.
Nobody is going to use this problem-free. No web dev is going to fix website behavior for an irrelevant browser. Worse, it’s a setting that is not even enabled by default in an irrelevant browser, again reducing the chances for a fix. You seem to live in a galaxy far far away…
> but it doesn’t cover the RISK of multiple domains in the same session.
…provided you actually open multiple domains within the same session. Big IF.
> Can you defeat known scripts with blocking and naive scripts with farbling – of course: but it doesn’t cover unknown and smarter scripts = a RISK.
Quantify that risk. I know that you don’t like it when I say that, but the threats you come up with are more or less irrelevant. I don’t know what to want to hear from me at this point:
Do I deny that comprehensive solutions are a good thing? Nope.
Do I think they are needed in the vast majority of all cases? Nope.
Do I think those comprehensive solutions are actually workable in real world environments? Nope.
You insinuate all the time that I say “Yes.” to the first question (even though I clearly don’t) while ignoring the two others because they are inconvenient to you. From what I gather you do not care about usability and a realistic quantification of risks.
> meanwhile Tor Browser and Firefox engineers are working on REAL solutions for ALL use cases
Again, proof that you are writing from a galaxy far far away. It matters not what Mozilla does. The browser has no future, so even though they come up with problem-causing solutions for barely existing problems, the fact that Firefox is on its way out would already mean that I don’t care. Website admins won’t fix any breakage caused by Mozilla. Tor Browser will be based on Chromium by 2025 (generous estimate).
> You clearly hate Firefox with the passion of a thousand burning suns, so you do not have the option of FPI/dFPI/RFP.
I don’t hate it, rather I just don’t trust it, which is why I am not using it. I also have no intention of switching browsers again when Firefox inevitably dies in a few years. And keep your solutions for barely existing problems to yourself until they are workable, i.e. non-breaking. Then we’ll talk.
> So you HAVE to make do with what you can.
I have not yet encountered anything that would make me switch, also nothing you said so far would make me switch.
> But that _still_ doesn’t even get it near what Firefox can do.
This is unrelated, but Firefox doesn’t even get the very basics right:
https://madaidans-insecurities.github.io/firefox-chromium.html
Me switching to Firefox would solve irrelevant problems, but it would also mean worse security / exploit mitigations, worse web compatibility, worse performance etc. pp. Switching to Firefox is not advantageous in summary, if you would care for once to look at all involved factors. I don’t know what it will take to make it clear to you that I envy you not, and that I will not be using that dying browser…
> Are you going to continue to argue that FPI/dFPI are _not_ more comprehensive
Putting words in my mouth again? I literally never said that. I even said the PLAIN CONTRARY above. But the “comprehensive solutions” you offer fix irrelevant problems while causing new ones, so I don’t care.
> than a sanitizing extension or even using multiple profiles (there is still risk in using a separate profile).
They are superior to a separate profile if you don’t understand that you are not supposed to use the separate profiles with multiple domains, if the goal is to isolate stuff. FPI is only superior to separate profiles if you use separate profiles in a fairly stupid manner, a fairly stupid manner I have never suggested in any of my comments.
FACTs
– FPI/dFPI is more comprehensive than a sanitizing extension because it covers a lot more that what an extension can touch. And because it tackles the underlying problem instead of treating the symptoms, it handles all use cases
– Additional profiles (or constantly creating new ones with defaults?) are completely “isolated” from other profiles, and assuming you sanitize it on close if you plan to re-use it, when used is basically a clean start – I’ve stated that as have you
– An Incognito, Tor Mode, or Private Browsing Mode window is much the same as a new profile (not quite but close enough) – we already both know this
– Those three modes and using different profiles don’t offer any “isolation/partitioning” protection for multiple domains within their own “modes/profiles” by default. That’s why they’re inferior… without FPI
So you say .. let me quote what you just said: “you are not supposed to use the separate profiles with multiple domains, if the goal is to isolate stuff” .. and I’m going to say … if you don’t isolate stuff, then you do not have parity .. which means you’re advocating one domain per profile, exhibit A: your quote
Now that would be impractical for ALL your web browsing .. so you’ll say you’re happy to use your main profile for most of your sites and it’s 90% covered (but not isolated/partitioned and carries risk), and that you can use a one off window EACH TIME for problematic sites – and that’s true, you can. That’s your use case and you’re happy with it. But it’s inferior because it doesn’t handle all use cases, and your main profile isn’t doing the stuff your one-off windows/profiles are protecting you from.
It’s also not scalable (everyone will have different use cases). For example, in Firefox, as long as one Private Browsing mode window is open, they are the same Origin Attribute: so you could only ever have a single domain open in PB mode at a time to gain parity. When the last PB window is closed only THEN is everything released from memory etc. This is just one more reason why FPI/dFPI/partitioning is superior
Your setup is an inferior solution. Thanks for proving my point YET AGAIN
> Nobody is going to use this problem-free
It’s ALREADY being used problem-free. The only thing FPI broke were some (not all) cross domain logins due to how those few companies structure their cookie-type-login flows. Many users can get by just fine: there’s been no complaints to Tor Browser, and I have no issues on Firefox with it either. FPI is working exactly as it was designed. It’s about user expectations and training/opSec /whatever.
However, 220mn Firefox users will have different expectations and some will want to use these, so it needs a very slight tweak: which is already there and working in Nightly and has been for quite a few releases: it’s called dFPI. It’s not a carte blanche, free-for-all – it’s detection of user gestures and specific actions such as clicking on a FB login widget to loosen the restriction on a first party for that third party in that session – and a few more tweaks to come to make it more configurable
—
And I don’t know where you’re going with this: just more crap and noise I guess: something about websites are not being designed with FPI in mind. Well, of course not. FPI is not a standard.
@Pants
> FACTs
Impressed and stunned right from the get go.
> FPI/dFPI is more comprehensive
Cool, I never stated anything to the contrary. I said that this is not workable in real life setups and that isolating literally everything is not even needed. Also, literally who cares what Firefox does.
> Tor Mode
…is, in Brave’s case, a full profile. Not that I use it or give much consideration to it…
> for multiple domains
Did I ever say you are supposed to use alternate profiles in such a stupid manner? No? Then why do you ride that point to death…
> which means you’re advocating one domain per profile
Bingo. Also, one “parent domain”, not just domain.
> Now that would be impractical for ALL your web browsing ..
How exactly? What if I open a new profile and call it “Facebook”, have it set to clean everything upon closing the browser. What then? What if I only use that for facebook.com, how is that impractical?
> That’s your use case and you’re happy with it.
Bingo.
> But it’s inferior because it doesn’t handle all use cases, and your main profile isn’t doing the stuff your one-off windows/profiles are protecting you from.
Your suggestion doesn’t handle all use cases, either. Cross-site logins are just one example, it also causes reCAPTCHA hell that absolutely nobody wants to deal with. I can avoid all that with one or multiple different profile(s).
> Your setup is an inferior solution. Thanks for proving my point YET AGAIN
LOL, yeah. Inferior to a non-workable solution, happy to hear that one.
And then again, I feel like I repeat that for the 100th time by now, it matters NOT what Mozilla does. They are the very definition of irrelevant in 2020. You’ll be using Brave or whatever Chromium-based solution Tor comes up with in a few years anyway, you better believe that. Seems like this thought is too traumatizing for you to even contemplate it, haha. The realities are a complete blind spot to you. I don’t use products that are bound to die in the mid-term and neither do most others! So even if they come up with non-workable solutions for barely existing problems, the above FACT (you seem to like that word written in capital letters, consider this my Christmas present to you) alone would already be enough reason not to care.
That I discuss with you about Firefox is in itself a form of courtesy, I have to pretend that whatever Mozilla does is actually relevant for this discussion to make sense.
> It’s ALREADY being used problem-free.
Haha, no. There are daily bug reports on r/firefox and in other places, you just have to care enough to look them up.
> and I have no issues on Firefox with it either.
Wasn’t it you who said that this is not about you and me, but rather about every use case out there? I vaguely remember…
> FPI is working exactly as it was designed.
Yeah, the problem is that the web, in turn, was never designed for FPI.
> which is already there and working in Nightly and has been for quite a few releases: it’s called dFPI.
Experimental feature of an equally experimental alpha build. When does that stabilize? In a year or so? Is that all you got, or are you actually trying to convince me? Because that sure doesn’t.
> it’s detection of user gestures and specific actions such as clicking on a FB login widget to loosen the restriction on a first party for that third party in that session – and a few more tweaks to come to make it more configurable
That would amount to guesswork and is not at all the main point of dFPI. I worry about you at this point, you failed to grasp that FPI is basically the concept of a container on a per-domain basis, you fail to grasp what dFPI is about (hint: explicit exceptions granted through the storage access API). And then you still wonder why it is important to understand what the code does… My my…
> just more crap and noise I guess
So usability = crap, quantification of risks = noise? Because that is what I am talking about all the time. You prove to me again and again that you do not care about either, but at the same time, funnily enough, you complain about me stating that the suggestions you come up with give little consideration to – especially – usability aspects… Wow.
> I guess: something about websites are not being designed with FPI in mind. Well, of course not.
And I guess that is not a problem, lol.
Pants, you are the best involuntary anti-advertisement for Firefox imaginable, one who rides totally irrelevant problems to death to prove a point, doesn’t care about usability, doesn’t care about more basic tenets like effective exploit mitigations or performance (which would be good reasons not to use FF before even getting into the whole privacy-related debate), mixes all of that with personal attacks and defamations, while posing as an expert in spite of having very little to show for it, and so on and so forth… If your goal is to further the usage of Firefox, you totally fail here. Just saying. Go on now, pretending that I care one iota.
@Pants
> You are either totally ignorant, or being misleading (or both).
You repeat that unproven accusation in every post, you know? Very creative indeed… And no, I am not. I am just not trying to come up with nonsense scenarios that are not even demonstrable in the wild, just to prove a point.
> Look up the meaning of the word “comprehensiveâ€: no cares about your anecdotal usage. We’re talking about a _real solution_ for _all use cases_.
Such a thing does not exist. Every solution proposed has weaknesses and the potential to break things, including containers (those more than anything else, lol).
> I even gave an example e.g. “what about users with 100s of tabs open†and your reply was something like “doesn’t affect meâ€
That kind of tab usage would cause a system crash / kernel panic or at least noticeable slowness, even when tabs are being discarded, but Chromium tries to keep them in the RAM, even if that means writing to the SSD or worse HDD in a heavy manner. You know very little about the inner workings of Chromium, or typical memory management of operating systems. What you propose is not even conceivable unless you have like 120GB of RAM, you come up with nonsense scenarios to make a point.
But then, again, trackers usually drop 3rd party cookies (which are being blocked here), not first party ones. You know that, I know that, most readers around here know that. One can drop unrelated first party cookies on me all day long, even in hundreds of tabs.
> Not all cross-domain logins break in FPI, and this is what dFPI aims to solve.
“Aims to solve”, nice way of dancing around the fact that it’s still a problem. And yeah, most cross-site logins would break. Again, websites are NOT being designed with containers in mind, it is a buggy solution at best, and will stay that way in the foreseeable future. By the way, on a semi-unrelated note, this is why web devs don’t bother to optimize their stuff for Firefox anymore, nobody fixes exotic bugs for this minority anymore.
> And now you’re confusing Tor protocol with Tor Browser’s FPI. It’s one thing to break the digital footprint of your IP address, and a completely DIFFERENT thing to break linkification of traffic.
Pants, Tor windows in Brave run off a different profile, so they isolate the stuff I do in them from the main profile as well, even if Tor would not be used at all. I didn’t even talk about the “digital footprint of my IP address” in that context, in case you haven’t noticed. The “Tor” aspect of Tor windows is totally irrelevant to me, I was talking about the isolation aspect.
> let alone in one of your many profiles (isolated from each other but nothing in the profile is)
So? Creating a new profile in Brave takes like, what, two clicks? I do that, then do some Facebook stuff in that profile for example, then delete the profile again (again, takes one click or so). How is that not isolated? What are you talking about? I wouldn’t even use those profiles for multiple things. It’s perfectly doable.
> Your antiquated ideas on using cookie cleaners and multiple profiles and one off tor mode windows and one off incognito windows is the way of dinosaurs, and contain many flaws and holes.
Maybe they seem antiquated to you, but you seem to have no idea about the cost and resource usage aspect of tracking. If you have to do it all server side, this will cost lots and lots of money, hence almost nobody does it. Instead, they still drop cookies for re-identification purposes because that removes workload from their servers. And these cookies (or other kinds of local data) are vulnerable to cleaning.
Sure, you will now show me server-side tracking, which I know is possible (provided that your scripts work on me), BUT NOBODY –> EVER So you’re relying on user behavior and the status quo. If there is a hole, then patch it.
Well, yeah, of course!? Why would I worry about your proof of concept stuff, that you can’t even demonstrate in the wild, in spite of me asking for proof? You read about that in some study, but without it being a problem in the wild, it does NOT concern me. If it becomes one, rest assured that I am staying on top of the news, and will hear of it.
> e.g.just because you block most FPing scripts, so what: that’s just the first line of defence.
First line of defense that works like 90% of the time (conservative estimate), if not more. Again, show me something that would be a real concern.
> What about when scripts mutate on demand with random names from random third parties and get super sophisticated and ultra-smart and block lists start to become ineffective.
“Mutate with random names”, dude, that sounds like some virus or something. What happens in reality is that even randomly generated scripts have identifiable letter- and / or number-combinations in their names across all variants. You propose that scripts exist, let’s name them after animals:
donkey, snake, elephant, giraffe (4 randomly generated script names) –> This is not how it works in real life.
This is how it works in real life:
giraffe100a, giraffe101b, giraffe129e239ue, giraffe103i2epqie02ie (4 randomly generated script names designating a common origin, in which case it would suffice to block “giraffe*”)
You know, randomly generating script names for each user, with seemingly nothing in common between the names, is not manageable and would confuse not only the advertiser, but also the contractor (especially, like you propose, if they come from random servers or even just random domains). Usually tracking networks are happy enough to break Pi-Hole, in which case it would suffice to use one common name and add random ranges of numbers or letters right behind it, because Pi-Hole needs concrete addresses to block.
> from random third parties
Dude, this is cost-intensive as hell. Why do you think they are running big, centralized servers with a range of domains form which ads are being served? You can’t do this endlessly or randomly, and hiding a common origin (if there is one) is absolutely not trivial.
> and get super sophisticated and ultra-smart and block lists start to become ineffective.
:D
Show me one, just one, ultra-smart, unbeatable script… Good luck.
> What about when all FPing scripts are first party and you can’t detect them,
Well, then I wish the ad networks good luck in writing new fingerprinting scripts for each website, that will also make cross-site tracking so much easier and cheaper even if collected data can be linked (irony!). Nope, they will continue to use a limited number of known scripts on various websites.
> as they are bundled deep within needed JS files for the site to work.
Dude, they usually get those from third party ad networks, of which they are contractors anyway. That’s why there are not that many popular fingerprinting scripts, to a degree where they are manageable on blocking lists. There is no easily maintainable way to include this into needed JS files, believe me.
That’s probably also why each website is so eager to use their own CDNs, and would never ever rely on a third party, because it’s so easy to maintain (lol). Same story with the fingerprinting scripts, if they can get them from a third party, they will, and when they do, they are not that deeply integrated into websites. Because if they were, you’d have to react (nearly) each time when the scripts receive a code update. Nobody ever does this. Scripts will continue to operate very loosely (because anything else would be maintenance hell), and will continue to come from third parties. Again, not talking about proof of concept studies here.
> Actual anti-fingerprinting is the last line of defense: you don’t ignore it because it may be deemed low risk.
I don’t ignore it, however so far I also don’t ever actually needed it.
> go look up the word comprehensive
Comprehensive implies “workable” to some degree, but that’s not the case for your solutions, as websites just tend to ignore Firefox and its breakage-inducing features like containers. That’s the reality, and that’s why your solutions are not workable in the wild.
> You clearly do not understand what you are talking about.
So? Well maybe, but at least I am not ignorant to a degree where I can’t differentiate between privacy and anonymity. Tools like uBlock Origin enhance privacy but do weaken anonymity, as they increase the fingerprinting surface by virtue of their very existence, and that’s not even taking into account the filter list leaks. Your anonymity gets wreaked by using uBlock Origin, but privacy on the other hand is being enhanced by its script blocking. You recommend both in your “arkenfox” setup, fingerprinting protections and uBlock Origin, that is.
Why do you think the Tor browser (an anonymity tool) doesn’t come with uBlock Origin? Perhaps they are doing things wrong, and should ask Pants for help next time. Or – and that’s the more likely scenario – they understand the conflict between privacy and anonymity tools, as opposed to, well, you… My setup above is a *privacy-enhancing* setup, not an *anonymity-enhancing* setup. Recommending to install any extension at all, or to change any setting in the browser, would run counter to the anonymity goal, but many privacy violations would be made possible. You talk about the weaknesses of Brave’s fingerprinting protections which would only be relevant if my goal was anonymity, but since my goal is privacy, me installing extensions in the first place would already totally and irrecoverably ruin anonymity!!! If people follow your “arkenfox” advice, they will be private, but not anonymous, but you argue in favor of anonymity, and about aspects of anonymity, with me here. Makes no sense.
Firefox with your user.js + uBlock Origin –> private, not anonymous
Brave with my setup + uBlock Origin –> private, not anonymous
Both setup contain fingerprinting protections but the real purpose of those would be providing anonymity, for which both our setup suggestions are ILL-SUITED. I repeat: ILL-SUITED, not fit for purpose at all. Anti-FP beyond adblocking makes sense in anonymity tools like Tor, not in common purpose browsers where the installation of extensions (if not anything else) would already totally destroy the anonymity aspect.
> For example stating that SSL session ticket IDs are cleared when you close the browser – that’s by design: FFS, that’s why they’re called SESSION ids.
Brave blocks session identifiers by default, but even so, deleting the browsing history of Chromium also happens to empty the SSL cache. You’d know that if you had more than basic knowledge of Chromium.
> Go educate yourself or listen for once. You’ve already shown you don’t know anything about Firefox, you sure as hell don’t understand fingerprinting or entropy or how that can be used to linkify traffic. And you sure as hell don’t know how a lot of other linkifying/tracking mechanisms work:
Dude, usually I am not this direct, but here I have to be: All you have ever done on GitHub so far was to provide a preconfigured user.js, oops I mean “template” of course, of which most settings with explanations can be found elsewhere, and whose goal seems to be anonymity, however such a thing only makes sense in an anonymity tool like Tor (which is where you get all your info from), not in a setup where you recommend to install extensions at the same time, thereby totally foiling anonymity(!) and rendering any related fingerprinting-related discussion moot. If I can identify you via extensions, solid fingerprinting defense won’t save you… Your setup recommendations fail to make that differentiation, so the question would be: Do you even understand it?
Your GitHub history also shows no code contributions of any kind, despite it existing for some years already, and when you have the chance of actually analyzing code, e.g. the code of Brave’s fingerprinting defenses, you have to ask the Brave devs for an explanation, because you seemingly don’t understand what the easily located and logically structured code means. You go test browsers on specific testing websites and you read various studies, but I am inclined to believe at thus stage that you can’t even write a single line of code, unless you can convincingly prove the contrary to me. I have seen no evidence so far, despite searching for it. Why is that important? In order to really discuss the defenses, you’d have to have the ability to spot weaknesses of the inner workings and provide potential fixes. Testing websites don’t tell you the whole story. I am not very happy about a person with seemingly no coding ability (maybe I am wrong, your GitHub history shows nothing to that effect), getting most of her info from pre-existing Tor docs, telling me that I have absolutely no clue. That’s just a bit gross, you see. I am not trying to insult you here, but perhaps you should reduce your publicly displayed arrogance towards me a bit, as your previous work does not strike me as too impressive, either. I am willing to take advice from experienced coders with many years of working in the field… From you? Not so much, unless you can show me concrete evidence that you are such a person.
> it’s not just about your stupid cookies
Please understand that cookies are an easy way to mitigate further workload on servers. Nobody wants to do all the tracking server-side, hence why cookies are being dropped. They won’t die out for a long time, if only for cost-saving reasons. Most people don’t bother to delete them, cookie-bound methods would still work on them (the vast majority). They are also not *my* cookies, if they were, I’d be much richer than I am now. :D
PS: It’s not necessary to wait with the reply until the article moves to page two, I am being notified of replies.
@Pants
> As per usual: right over your head, or deliberately ignored, or twisted when confronted with FACTS
You twist whatever I say and accuse me of twisting your stuff. Look in the mirror.
> Who said it was a prerequisite for Brave Rewards? I said it “benefited†it, not “enabled†it. Also, why would BR not exist afterwards? Is it a blocker? Or is it a prerequisite? Try making sense for once
It is you who does not make sense. You said that Brave Software only to further their business model, which is to replace website ads with their own (that is not accurate in its own right, Brave blocks ads on websites and doesn’t inject any, its own ads are system notifications). This is clearly bullshit. They did the CNAME uncloaking to further improve on the internal adblocker. It has nothing to do with further pushing Brave Rewards, as you imply. That content creators are annoyed that Brave blocks ads, and now even more so than before, is expected and won’t change.
> The point is that the planned additions will come up against the same problems that already plague them
And? Do you think their employee count will always stay the same, in a growing project? Pretty please… That they are resource-constrained now doesn’t mean they’ll never tackle it, but hey, keep repeating that Brave’s fingerprinting protections are not complete until it’s no longer possible, who am I to take that temporary argument away from you.
> So massively inferior then. Having to fluff around with profiles.
Huh? Massively inferior? In what way? From a usability standpoint? It’s enough to go to the hamburger menu -> “Open Private Window with Tor”… Boom, done. From a technical point of view it’s not inferior to containers, quite the contrary. You are making stuff up out of thin air.
> Or using Tor mode with the latency (and trusting they have it right)
Brave’s Tor mode is not a Tor replacement. But, just in order to isolate some stuff, it doesn’t have to be. Firefox Containers are no Tor replacement, either. I only want to isolate here, using Tor network or not (and how) is irrelevant for that purpose.
> and please, show me the proof that while in Brave’s Tor Mode that it has anything like FPI (they don’t) – i.e multiple domains open in Tor Mode.
Sorry, I don’t have that much stuff to isolate, i.e. stuff that would be worthy of isolation. I really don’t. The occasional Tor mode is enough.
> Network partitioning
Nice name dropping, I have one for you as well: Split cache. Firefox is far from implementing that. If you want, you can find advantages on both sides.
> While third parties exist they can be used (imagine users with dozens, hundreds of tabs open).
Do you know what a “bookmark” is? I don’t have hundreds of tabs open, I also want my RAM to survive for another year or so. And no, I have taken my precautions. Trackers would usually drop third party cookies, not first party ones, and my Brave setup doesn’t accept them in the first place. The first party cookies get destroyed pretty quickly and they are usually not suitable for tracking purposes (mostly logins drop 1st party cookies). OK, there are also other types of local data but their use for tracking is even less likely, especially cross-site.
> Firefox engineers actually come up with way-more-comprehensive and **real solutions**: not your namby pamby feel-good antique fuffyness
Their way-more-comprehensive **real solutions** tend to break cross-site logins and other stuff, there are enough bug reports to that effect. Websites are NOT designed with containers in mind, and break accordingly. At least my setup works, and amounts to more than just a proof of concept that you can show to your friends.
Also, what Firefox engineers come up with is totally irrelevant. It’s not like Firefox will be around anymore in five years anymore (source: market share of the Gecko engine). Please understand that I do NOT care about dying projects that will switch to Chromium or perish.
> So CNAME uncloaking is a meme,
Yes, because it is not very prevalent. It’s certainly good enough for a Pants gotcha moment, but it’s not a real world thread I would be too concerned about, even though Brave supports it now.
> and fingerprinting is a meme
Yes, because fingerprinting scripts that are non-obscure will inevitably land on the EasyList or EasyPrivacy list very quickly. OK, let’s see how you can catch me (I am just writing this to show others how outlandish the threats you propose exist are):
– First, you have to come up with a script of your own, because if you just re-use a known fingerprinting script, chances are that it will be blocked by my adblocker.
– Then, you have to keep Brave in mind while you write that script. Brave is not that popular yet, so in the real world this is fairly unlikely. However, let’s give you the benefit of the doubt and say that you also target minor browsers and their fingerprinting defense weaknesses with your scripts. Hint: Most scripts don’t bother, because default Chrome and default Firefox (= most users) don’t even attempt to hide the true values.
– If you are lazy and drop a cookie on me for re-identification purposes, better pray that it is a first party one, because third party ones won’t be accepted by my browser. OK, let’s say you drop a first party cookie on me – bad luck, it will always get deleted by Cookie AutoDelete once I leave your website, same for other types of local data.
– So you have to track me server-side only, which is resource-intensive because you have to evaluate whether or not it’s me every single time I visit your website.
So…
– non-popular, likely self-written script which
– targets Brave’s weaknesses (on a continual basis, ’cause fixes) and
– doesn’t just lazily drop a cookie
How likely is that, please? Do you know how cost-intensive that would be? Hardly anyone would do that in real life! OK, unless you target me directly and specifically, in which case you are likely not a website operator or advertiser, but rather a three letter agency. In which case I would likely know why you would target me, and would likely have taken my precautions by using different tools (Whonix, Tails, Qubes OS etc.). Dude, this is so outlandish, it is not even conceivable.
Even YouTube, one of the most tracking-heavy websites I know of, doesn’t go beyond using ordinary tracking scripts, dropping some cookies, cache, and a service worker. Tracking script –> adblocker, local data –> Cookie AutoDelete.
The threats you come up with here, in order to advertise the dying browser Firefox, basically don’t exist in real life.
> except when you want to tout them as features in Brave.
That they are features of Brave doesn’t mean that they are relevant or a real threat. I mention them for completeness’ sake only. You just can’t accept that and read too much into things because Mr. Iron Heart has to have bad motives and / or has to be a hypocrite, lest Pants’ world view be challenged.
> And now isolating/partitioning via origin attributes (like containers, FPI, dPI) are a meme – but won’t be once this concept starts to be applied to chromium. OK, got it, genius
Even if they were in Chromium, I would NOT use them. As I said, I don’t have much if anything to isolate. If I had, the Tor window would likely suffice.
> Stick to the topic dude. What does sandboxing have to do with it? “isolation†can apply to more than just processes. You’re mixing up security and privacy/tracking issues
Tor inherits a weak sandbox from Firefox. If I wanted to de-anonymize you, I’d just exploit this weak sandbox, drop malware on your PC, and then take a look at what you are doing. Not that I would do that, but three letter agencies do, they actually describe this as one way to de-anonymize Tor users. Well, this and sybil attacks. If you make a big deal about the fact that Brave inherits Chromium code and has to deal with the issues, then I can point out that the same is true for Tor in relation to the Firefox code.
uBlock Origin is the best adblocking extension, no matter what platform and better than any browser’s internal adblocking. I wonder if, assuming ever, Brave for Android gets support for extensions.
@James Kirk
uBlock Origin won’t survive Manifest V3 on Chromium, at least not in its current condition. Some Chromium-based browsers like Vivaldi or Brave have pledged to keep support for Manifest V2, but it’s unclear how long this will be doable, and whether or not uBlock Origin would be maintained for those browsers alone when it can no longer target Google Chrome.
So better not to count on it too much, it’s on its way out on Chromium, and on Firefox the jury is still out (Mozilla typically wants to maintain compatibility with Chromium’s extension APIs as that eases cross-browser development of extensions).
Nevertheless, Brave’s adblocker – in my experience so far, anyway – is only inferior to uBlock Origin in that it can’t use custom lists yet. If it could, I would just drop uBlock Origin and add those to the internal adblocker of Brave. Brave’s internal adblocker can also do CNAME uncloaking which uBlock Origin can’t do on Chromium due to an extension API limitation.
As for extensions on Android, they are working on it currently as per their GitHub.
@Iron Heart
I added your 3 custom filters to UBlock Origin, but each filter says 0 used out of 0. What am I doing wrong?
@Anonymous
Go to the filter lists page of uBlock Origin, empty the cache (at the very top of the page), then force an update. Hopefully this will fix it. Cheers.
Thank you, Thank you!
I hope ghacks will consider occasional user submitted articles like this one as a featured article. Maybe someone like Tom Howack can do one for his setup, which if I remember beefs up privacy and reduces ads at the system level using dnscrypt and others. User submitted articles could be useful in expanding into other areas like linux which could help draw in more talent if desired.
Iron Heart
I have looking for a comprehensive solution such as the one you describe, where all the parts are designed to work together without interference, but none have included, first adjusting the browser settings, then which extensions to choose and how to set them up as well. So thorough and with practical explanations to boot.
I have saved these guidelines and applied them to firefox, to give them a go. I have been thinking about using Brave and now i have the perfect reason to do so. I hope more knowledgeable talent will begin contributing their well thought out setups too.
@ipnonymous
Thank you for your kind words, they are appreciated. Good to see that my config is helpful to some people, and yes, it can be (partially) applied to other browsers as well, the extension settings in particular.
The “arkenfox” project is a comprehensive list of Firefox settings that you might want to look into: https://github.com/arkenfox/user.js/blob/master/user.js
I have my misgivings about some of the settings suggested there, because they IMHO break too many things. Particular examples would be the suggested cookie settings or their suggestion to turn off IPv6, which means that 5% of all websites (statistically every 20th website) would break. They are going for privacy but lose sight of practicality / usability at times, yet since it is the most complete list that I am aware of, I am linking to it anyway in the hopes that it might be useful to you.
Brave sometimes gets flak for being less configurable than Firefox (without the critics taking into account that the Brave team has already turned off many things by default, things that they would have to turn off themselves in Firefox as Mozilla leaves them enabled – see my first link) or for being based on Chromium (again, without the critics taking into account that all unsolicited connections to Google were removed by the Brave team), but all in all, I think it is a solid foundation to build on. Like any other browser, it’s expectedly not perfect (hence the extensions) – I am very satisfied with it for my own use case, though.
Iron Heart said
> I have my misgivings about some of the settings suggested there
Stop talking about things you don’t understand, or making things up just to make others look bad. Just because you can use a preferences interface and install an extension or two, doesn’t make you knowledgeable.
First: https://github.com/arkenfox/user.js/pull/1007 – just because at the time approx 5% (it is now about 8%) of Firefox connections were IPv6, doesn’t mean disabling IPv6 breaks them: most fallback to IPv4. Do you seriously think that sites wouldn’t by default fallback, thus cutting off the bulk of possible visitors. A lot of the world can’t even use IPv6. As for disabling it by default in the template: breakage should be rare (there will be edge cases for authentication and security where the MAC address is used), it doesn’t affect those who can’t use IPv6 anyway, and it’s a defense-in-depth for those using VPNs. Given the target audience, it is safe to assume that users should/would be masking their real IP. Also, ~5% of connections !== ~5% of websites. Educate yourself.
Second: The arkenfox user.js is a TEMPLATE and users are expected to tweak it. It says this in the wiki, in the github readme, and in the user.js itself. Items that may break or alter expected outcomes are tagged. Everyone’s experience and expectations will differ. It’s fairly balanced: you can either relax a few things or harden it up even more – that’s the end user’s choice. Learn to read.
@Pants
IPv6 is growing and you recommend disabling it… Nuff said. What will you do when it is supported by a greater share of websites, and when IPv4 fallback won’t be a thing anymore? I guess you will then recommend enabling it… Recommending to disable it is bad(!) from a usability standpoint.
5% of all connections would have been more accurate, Mrs. Nitpicker, I agree.
No, installing extensions doesn’t make me an expert and I never claimed such in my comments (Please don’t put words in my mouth, thank you). However, you recommend those extensions as well on GitHub for much the same reasons and they should be part of a good setup if I may remind you.
I am not using Firefox and for good reason – many things your pre-configured user.js, uh I mean “template” of course, recommends, are already the default in Brave. I have no time to waste there, and I don’t personally need it. I just pointed at it because someone else seemed to be interested in improving the privacy of Firefox, not because I am in need of it myself. That any mention of it would summon you like genie out of the bottle, because you seem to silently read anything I write (seriously?), is something I couldn’t have foreseen. That’s why I usually avoid mentioning you or your stuff. I’ll return to this policy, for the betterment of gHacks and for the sake of tranquility.
Thanks Iron Heart for the info.
I, too, was a Firefox user for a very long time. I finally grew tired of issues that arose from updates, etc. I have been a follower of Ghacks for some time now and after reading your comments and replies decided to give Brave a try. Six months or so into it, I am a convert.
I am having a couple issues that you may be able to help me with.
Trackers & ads blocking – every time I set it to aggressive, the time I check it’s set at standard.
WebRTC IP handling policy – will not stay in the disable selection
@Dave H
Glad to hear that my setup was helpful to you, and indeed, Brave is a good browser and has potential to stay that way and further improve in the future. As for the issues you face:
> Trackers & ads blocking – every time I set it to aggressive, the time I check it’s set at standard.
1) Are you sure that you are running the most recent Brave version (as of today, 1.18.70 on the desktop)? If you are not sure, check which version you run with the hamburger menu –> “About Brave”. If the version you run is older, you can get the most recent one here (standalone installers):
https://github.com/brave/brave-browser/releases/tag/v1.18.70
2) If you run the most recent version, then check whether or not you have set it to delete website settings under brave://settings/clearBrowserData … Should you have set it to delete website data, uncheck this setting.
3) Are you sure you’ve set it to “Aggressive” under brave://settings/shields (which is the general setting), because if you set it to “Aggressive” using the lion icon in the address bar, the setting will only be applied on a per-site basis.
4) If none of the above applies or helps, there may be a corruption in your profile. Create a new profile and check again. If the error isn’t happening in the new profile, export your bookmarks to HTML in the old profile, and import the HTML file into the new one using the bookmarks importer / exporter in Brave’s settings.
5) If not even a new profile helps, report the issue on https://github.com/brave/brave-browser by creating a new GitHub issue, and have the Brave devs troubleshoot it with you.
> WebRTC IP handling policy – will not stay in the disable selection
1) Are you using the WebRTC related setting in uBlock Origin (or for that matter, any other extension interfering with WebRTC)? If so, go to uBO’s dashboard / settings pane, and uncheck the WebRTC setting there. I had the same issue and this fixed it for me, afterwards the Brave setting stayed at “Disable Non-Proxied UDP”, as intended.
2) If the above doesn’t help, the same advice aseith the adblock setting applies. Check whether or not you run the most recent Brave version, if yes, create a new profile. If nothing works, report the issue on GitHub.
Hope this helps.
@Iron Heart
Thank you for your reply and your help.
The issue with the aggressive setting was that I had checked the box to clear website settings and data. I unchecked that box and now all is good.
As for WeRTC IP, I found that it was an extension that I was using. I changed to different extension and now all is good there as well.
Thanks for posting your set up, Iron Heart.
> It is the only Chromium-based browser with credible fingerprinting protections
Brave is not the only Chromium browser that handles anti-fingerprinting. Ungoogled Chromium is almost (if not) on par with Brave here, except for CNAME-cloaking. Firefox does offer the best anti-fingerprinting customization out of all browsers though. (Yeah, using Firefox does add to your fingerprint I get that.)
> On Android, I use Kiwi + the extensions I mentioned in my post above, which would include uBlock Origin
Kiwi phones home – https://forum.xda-developers.com/t/app-4-1-kiwi-browser-chromium-adblock-caf-night-mode-2020-04-17-active.3797252/post-76666256.
Be sure to change whatever settings you can.
I briefly used Kiwi, but decided to switch to Fenix and Ungoogled Chromium with Extensions support even if extension support is far from complete.
@Ray
> Brave is not the only Chromium browser that handles anti-fingerprinting. Ungoogled Chromium is almost (if not) on par with Brave here, except for CNAME-cloaking. Firefox does offer the best anti-fingerprinting customization out of all browsers though. (Yeah, using Firefox does add to your fingerprint I get that.)
Ungoogled Chromium’s anti-fingerprinting is weaker than that of Brave, I know that they enable the –fingerprinting-client-rects-noise flag, but it’s not the same. Bromite has stronger anti-fingerprinting mitigations and would be a contender (on Android).
Firefox gets its improvements from the Tor project more often than not, and follows a different approach. It’s also a longer-standing project than Brave, Brave doesn’t cover some fingerprinting vectors yet (but they continually update it and cover more). I think the jury on this one is still out and comparisons can’t be drawn in the short term just yet.
I refuse to use Firefox because of its weaker sandboxing and the continuous influx of anti-features coming from Mozilla. I also don’t like that it has experiments enabled by default (yes, I know how to disable them) and that it installs a telemetry task on Windows outside of the browser. In short, I don’t trust it more than Brave by any means.
> Kiwi phones home
Let’s examine that posting:
> search.kiwibrowser.com tells you what is the closest google.com server (google.fr/google.de/google.it)
OK, I think they do this to provide you the correct Google search for the area and / or language set you are in. That would be concerning if your location is transmitted, but I don’t think it’s the case. I tested this URL with Brave on my MacBook and what it seems to do is to evaluate what language you use and set the Google Search accordingly. Unless you consider it problematic that the Kiwi creators know what language you speak, I don’t consider this a problem.
Though I do have to wonder, couldn’t Kiwi just grab this information locally from the system itself. Anyway, even though I think nothing of great value is being transmitted here, I think it’s something to be aware of. The comment you linked to gives more or less the same explanation:
“This is a speed reason, if you go directly to google.fr rather than google.com and then google.fr it’s faster, and the browser caches this information”
> update.kiwibrowser.com is to download the ad blocking list
OK, this is definitely a beneficial connection and shouldn’t be a concern. The blocklist has to be updated somehow, and in order to accomplish this, it has to fetch the update from some URL. Even well-respected extensions like uBlock Origin fetch their list updates in this manner and there is likely no alternative to this (aside from pumping out new extension versions daily, which is not a conceivable approach).
> suggest.kiwibrowser.com is a 302 to Google autocomplete (and DuckDuckGo for some users who are beta-testing Bang support)
If you change your search engine, even to the baked Google one, you won’t get connected to suggest.kiwibrowser.com at all as far as I know.
I think this thread would be relevant here, the Kiwi dev explains it:
https://old.reddit.com/r/androidapps/comments/d8pxzh/how_safe_is_kiwi_browser_just_found_a_worrisome/f1e23nq/
Suffice to say that the reason this is done is much the same as with the first conncetion, i.e. non-malicious.
> I briefly used Kiwi, but decided to switch to Fenix and Ungoogled Chromium with Extensions support even if extension support is far from complete.
Didn’t know there was an Ungoogled Chromium on Android, will have to check it out. I am really only trying to get by here until the Brave team introduces extension support in Brave on Android. There is no reason I wouldn’t want to use Brave on Android just like I do on the desktop, but the missing extension support so far is a huge bummer in my book.
Useful. Thanks for the time you took creating it.
Does anyone know how to link a list rather than use Brave’s high maintenance method. For example
https://github.com/hoshsadiq/adblock-nocoin-list
UPDATE: Added the nocoin list using uBlock but didn;t really want to install uBlock.
NOTE: to do this, you need to open the .txt file, then select the RAW list. Direct link:
https://raw.githubusercontent.com/hoshsadiq/adblock-nocoin-list/master/nocoin.txt
@Iron Heart:
Thanks for the recap, always useful to compare up-to-date configs.
As an aside, do you know why Brave on Android doesn’t have the ‘Aggressive’ adblocking mode it has on the desktop? It currently lets in annoying Google ads on my mobile device, and the only way to stop it is via rerouting in AdGuard (not a bad thing in itself, but I prefer native adblocking where available).
Why does Brave on Android does not have Aggressive ad-blocking?
Either way even on PC I use Brave with uBlock Origin and Privacy Badger. I would not take any chances to see any filthy ads.
@Allwynd & ShintoPlasm
They have not yet implemented the “Aggressive” setting on Android, don’t ask me why. If I were a Brave dev, it would definitely be a priority for me.
On Android, I use Kiwi + the extensions I mentioned in my post above, which would include uBlock Origin. I won’t use Brave on Android as my primary browser until they implement support for extensions.
@Iron Heart
I thought I recall you using Bromite on Android (was I mistaken?). Is Kiwi better than Bromite? If so, why?
@Anonymous
For me, on Android it would go:
Kiwi (with extensions) > Bromite >= Brave >>> Kiwi (without extensions)
Bromite is better than Kiwi without extensions because it already comes with built-in adblocking and has very good privacy defaults. Bromite also has better fingerprinting protections, by the way.
BUT, uBlock Origin must be considered superior to Bromite’s internal adblocker, and one can run uBlock Origin in Kiwi. Also the other extensions like LocalCDN, ClearURLs, Cookie AutoDelete, HTTPS Everywhere, them working in Kiwi seals the deal for me.
I have both Kiwi and Bromite installed (and I use them interchangeably), both are good browsers and you really can’t go wrong with either one. I’d prefer using Brave on mobile as well, but since it doesn’t support extensions, I currently use both Kiwi and also Bromite over it.
@ Iron Heart
What do you think of DuckDuckGo Browser, which is available on F-Droid ?
@Rubio
It’s a good browser in that it doesn’t perform any data collection. Good interface and performance, too. You can’t go wrong with it, and I would recommend it. As for the included features:
– Comes with tracking protections, which further puts it ahead of included by default options like Chrome. However, it uses weaker lists than both Brave and Bromite. It’s also nowhere near as strong as uBlock Origin if you run that extension in Kiwi.
– Has HTTPS Everywhere built-in, which is good, but e.g. Brave has that as well, and in Kiwi that can be achieved via downloading the extension of the same name from the Chrome Web Store. That being said, neat security and privacy feature to have.
– Being able to use DuckDuckGo is not unique to DuckDuckGo Privacy Essentials, you can use DuckDuckGo as the default search engine in other browsers as well. That being said, DuckDuckGo as a search engine can be recommended as it doesn’t do data collection.
Compared to other available browsers, my ranking on Android would be (from best to worst):
1) Kiwi (with extensions uBlock Origin / HTTPS Everywhere / LocalCDN / ClearURLs / Cookie AutoDelete, however lacks fingerprinting protections)
2) Bromite (strong adblocking by default, also blocks 1st party trackers and ads, however lacks HTTPS Everywhere – that being said, the browser by itself would often opt for HTTPS anyway, arguably best fingerprinting protection on Android)
3) Brave (strong adblocking lists, however doesn’t block 1st party ads and trackers on Android, has HTTPS Everywhere, good fingerprinting protection)
4) DuckDuckGo Privacy Essentials (weaker tracking protection overall, blocks 1st party trackers, has HTTPS Everywhere, lacks fingerprinting protections)
5) Kiwi (without any extensions it’s just nothing spectacular and would be worse than all of the above).
All IMHO of course, I am also not quite sure whether or not it’s entirely fair to put Bromite ahead of Brave, they are roughly at the same level, if you ask me. I gave Bromite the benefit here because it blocks 1st party trackers and ads on Android, and Bromite not having HTTPS Everywhere is not a very strong argument against it.
Needless to say, in terms of privacy, all of the above range far ahead of data collecting browsers like Edge, Chrome, Opera etc., I think this goes without saying.
Cheers.
@Iron Heart:
One comment regarding your setup. Disabling Do Not Track doesn’t make much of a difference anymore, now that Brave has Global Privacy Control baked in and impossible to disable. So if you’re worried about a specific fingerprint, the DNT switch won’t make a dent.
@ShintoPlasm
Ah, OK. Good to know. One item that I can cross from my list going forward. I wasn’t aware of this – thanks for the hint.
Brave advertiser or what?
If we need to make all these things to a browser to make it smooth and safe, then its no browser. Brave was speed. Now its nothing compared to other browsers
@Pet
> Brave advertiser or what?
No, just a user posting his setup. That is what an advertiser would sound like:
“Brave is the greatest invention since mankind discovered fire! Get it while it’s hot! Where are my lions!?”
Okay, maybe not quite, but you get the point.
> If we need to make all these things to a browser to make it smooth and safe, then its no browser.
Brave is objectively the most private browser out of the box:
– Removes all useless Google dependencies.
– Comes with fairly good adblocking without having to install an adblocking extension.
– Comes with anti-fingerprinting defenses.
– Comes with HTTPS Everywhere by default.
As you can see, the default protection is already quite good, but my add-on setup aims to further improve on that.
You would need all the add-ons I mentioned and likely also HTTPS Everywhere in other browsers as well. All the add-ons I mentioned are essentials in my book, but if I had to remove one from the list, it would be uBlock Origin. The only reason I run it in Brave is custom lists, because I found some lists that don’t come bundled with Brave quite useful. But… The internal adblocker is not shabby at all, so one can manage without uBO.
> Brave was speed. Now its nothing compared to other browsers
It’s not slower than other Chromium-based browsers.
@Iron Heart Just use Mozilla Firefox. It’s easier to maintain and privacy focused.
@Leonard
I would have to modify Firefox in much the same way if not more, without it providing a benefit. I actually switched from Firefox to Ungoogled Chromium and later on to Brave because I was annoyed by Mozilla’s frequent anti-feature additions that I would have to turn off in about:config all the time. They’ve also announced that they’ll monetize Firefox more in the future, and they have badly crippled their mobile version recently.
After a management change and subsequent change of course I’d give it a fair chance again, but not these days, sorry.