Brave Browser: strict fingerprinting protection will be removed

Brave Software announced that it will remove the strict fingerprinting option from its Brave Browser. The company cites several reasons for the removal, including that it has been a major website breakage cause in the past.
Fingerprinting refers to a tracking technique on the Internet that uses information to create unique fingerprints of users. The technology combines open data, such as the browser's user agent or operating system of the device, with data that can be retrieved through APIs.
Fingerprints are created and then compared whenever a user visits a resource.
In the past, technologies have emerged to fingerprint users using custom browser protocol handlers, graphics processing units, or language and font information.
Fingerprinting has gotten better over time, thanks to the introduction of new APIs and also technological advancements. In 2023, a proof of concept site claimed that it could track users with a 99.5% accuracy.
Browser makers like Brave Software or Mozilla have introduced anti-fingerprinting capabilities into their browsers long ago. These are designed to render fingerprinting attempts useless. Some protective features may block access to certain information while others may generate data that is useless for the purpose of tracking users.
Brave Browser: fingerprinting
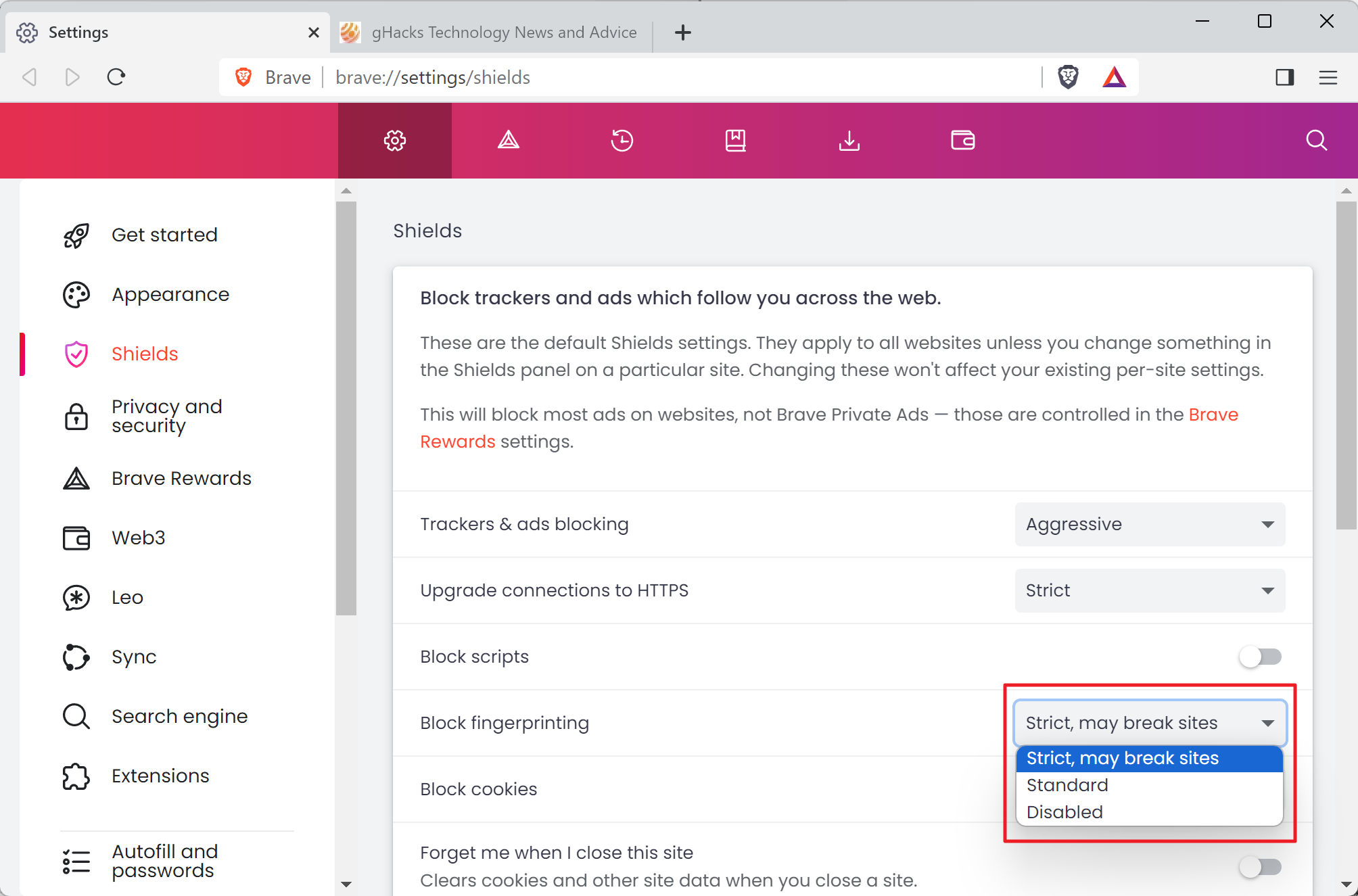
Brave Browser users may set fingerprinting to standard, strict or disabled at the moment. Strict applies additional protections.
Brave Software notes that it has identified several issues in the browser's strict fingerprinting blocking mode. Strict mode may cause some websites to function differently or not at all according to the company. The breakage forces Brave engineers to spend time addressing these issues instead of "focusing on default privacy protections".
The third argument is that the feature is used by fewer than 0.5% of all Brave users. Brave Software argues that the small number could make fingerprinting more likely.
The main argument against strict fingerprinting is that it binds engineering resources because of website compatibility issues.
The decision has been made to sunset strict fingerprinting protections in all Brave Browser versions in the near future. The latest Brave Canary releases already come without it.
Brave Software claims that its fingerprinting protections are "the strongest of any major browser" and that standard is still protecting users against fingerprinting attacks.
Brave users may load brave://settings/shields in the browser's address bar to check the "block fingerprinting" setting there.
Closing Words
The removal of strict fingerprinting protections in Brave affects a fraction of the browser's userbase. Strict is not the default setting and only the most privacy conscious users may have set fingerprinting protections to strict.
Google started to remove third-party cookies support in Chrome earlier this month and plans to drop support for all Chrome users later this year. Cookies are widely used for tracking purposes. The removal in the world's most used browser may fuel other tracking methods, including fingerprinting.
Now You: do you use fingerprinting protections in your browser?
















We need an extension for Firefox that can spoof and randomize browser fingerprints, preferably every X minutes, like ‘Random User-Agent (Switcher)’ does. Right now it tells the web I’m on Chrome for Windows, which is a lie – and in a few minutes it’ll come up with something else. Oh, apparently I’m on a different version of Chrome for linux now. Still a lie.
Re Brave: It’s shady as f, has been from the start.
Hidden VPN installation without asking for it.
Telemetry (enabled by default and with no option to disable it?).
And now the classic “our telemetry showed that you don’t need it, and in general there are not many of you”.
Not to mention past “merits” like spoofing referral links in the past.
In essence, Brave is no different from the rest.
It would be nice to have some fork of Brave like LibreWolf (without telemetry and other cryptoscam stuff).
@Honorius
The VPN was NOT hidden, they added it in their release notes, they were building the VPN for months, how can it be hidden when they told everybody Wireguard VPN implementation was being available?
1. Services are set to “Manual”, that means they will only run if they get triggered to run, and that’s only when you subscribe and use the service.
2. Users gave permission for ANY service to be installed by Brave by installing their browsers with admin rights, why would anyone install their browsers with admin rights? I don’t know. Is it to hard to say “no” when asked admin rights? apparently yes. Just like omaha updater gets installed as services with admin rights, so the VPN… it doesn’t mean they can’t be disabled, or they will be installed if not given admin rights.
3. the VPN services are not even ‘necessary’ for the VPN to run, the VPN services were to make VPN available even on computer restarts, that means, no IP leaks when services will be the first thing to run when you turn Windows on and it means you didn’t have to enable it only by opening Brave and run it every time you close the browser, and it means you can close the browser and keep it running.
The second service was actually to avoid DNS leakage because of some Windows services that ping and resolve local IPs and all that.
So, I don’t know about you, but VPN are justified to exist.
4. Why bring nonsense about Brave when this is about their Strict mode getting removed, which is a good thing, since Strict made WebGL useless? plus only 3 fingerprinting protection were exclusive to Strict, the other ones were or the same for Standard and Strict, or just added a little more noise to Strict and that’s it… it doesn’t mean Standard is not good. But I doubt you have researched any of this.
5. VPN PR to only install services when subscribing to VPN service is already available in Nightly, it took 3 months to build it, because installing services on demand, with admin rights is not an easy thing to do, you are actually modifying system files this way, which requires more security than just doing it at the installation time. Still, nothing justifies a user to install a browser with admin rights, unless you wanted the benefits of Updater and now VPN services running 24/7 even when the browser is off or on start, of course updater has Task Scheduler too, but the services are in charge of the whole installation.
6. Brave started as a Gecko Fork, and Brendan Eich decided to go Chromium and doesn’t regret it, so it’s time to move on. There is no way Brave will go Gecko now they have built everything on top of a better browser, Chromium, which still today offers a better future for Brave than what Firefox offers, especially when Mozilla is still existing because of a big client, and that big client is Google.
7. About Telemetry, you are WRONG, new installation wizards ask you if you want to keep enabled or disable the P3A telemetry, the only thing they don’t ask you is about the Ping, you know, the information that counts users, and that can be disabled easily in Settings too.
Brave is also Open Source, so you can easily see what P3A is and what features are being sent to Brave servers for telemetry…. Telemetry is good, stop vilifying something developers need to improve the products, and Brave has proven they are not doing anything else with that information. Again, you can check Brave source code and see what they do and how they do it, because it is obvious they can’t identify anyone with the information.
“that big client is Google”
That money is from a search engine deal. The same deal that Brave and every other browser has. The difference is Mozilla makes their public funding, while Brave does not. Better Google money than SBF/FTX money.
In Bizarro Brave land, the browser based on Google Chrome, uses the Google extension and play stores is less Google than the browser that uses none of those.
> Hidden VPN installation without asking for it.
How do you expect the built-in VPN feature to work if the necessary protocols aren’t installed (and still, are by default inactive)? It wouldn’t work, so either you offer a VPN feature (which requires the necessary protocols), or you don’t.
> Telemetry (enabled by default and with no option to disable it?).
So does Firefox, and it takes messing with about:config to hopefully completely disable it there. In Brave, it can be disabled under brave://settings/privacy
> And now the classic “our telemetry showed that you don’t need it, and in general there are not many of you”.
Te actual reason is the web breakage though.
> Not to mention past “merits” like spoofing referral links in the past.
You accept referral links every time you perform a Google search in Firefox. Brave doing it on another website doesn’t make it horrible, and in general a generic referral is not a privacy issue. A per-user generated one would be.
> In essence, Brave is no different from the rest.
The vast majority of the rest is Chrome, Edge, Opera… It is different from those in terms of Firefox. Then there is Firefox, which by and large does the same things.
*in terms of privacy I meant, Brave is not based on Firefox or Gecko of course.
I don’t believe that I know a single person IRL who would know what browser fingerprinting even is…….
Please Martin… Brave didn’t identify issues with Strict Fingerprinting… it was an obvious nightmare!
No WebGL page worked with it, so if someone who used sites with webgl support… what was the point of enabling the Strict fingerprinting support?
You can’t have a feature that breaks so many pages, so easy to access.
I think the problem is nobody is really researching what was the difference between Strict vs Standard.
I think the problem is people not researching enough, the Strict mode still exists, it is just moved as a flag, if people want to enable it, then they can still enable it.
Based on Brave’s team information and the issue to move Strict to a flag, you can find information about what Strict modes were implemented and how Strict didn’t offer ANY really improvement in comparison with Standard.
Issue #31229 in Brave-Browser says:
—–
We are considering removing aggressive fingerprinting mode, to reduce unneeded complexity in browser code and in the UI. To do this, we would need to work out which protections from aggressive mode to drop, and which ones to fold into default fingerprinting mode. Current protections in aggressive mode include:
Dark mode detection: Fingerprinting v3: Dark Mode detection #15265
WebGL: Fingerprinting 2.0: WebGL #9188, Fingerprinting 3.0: WebGL Debugging Followups #15882
navigator.userAgent farbling: Implement navigator.userAgent farbling brave-core#6055
—–
Now, tell me, why is Dark mode detection important for fingerprinting? there is even a flag to disable this, because not having a site detecting dark mode is terrible, some sites don’t let you manually change it to dark mode, so there you go, useless Strict mode.
WebGL that we already discussed how it made WebGL useless, so… no reason to have it if it will make it useless.
And the third one might be the only useful one? and that’s the only one they need to implement in standard if it doesn’t break websites and done?
I mean, if you readthe difference between standard and strict from Brave’s wiki
—–
Brave has two levels of fingerprinting protections. In the default, “standard” configuration, Brave adds subtle noise to APIs commonly used for fingerprinting. This small amount of noise is enough to make you look different to fingerprinting scripts, without breaking websites, and will provide good protections against web-scale online trackers.
Brave also includes a “strict” option. When set to “strict” mode, Brave only returns random values from APIs commonly used by fingerprinters. This provides a higher level of protection against highly determined attackers, who may attempt statistical and / or targeted attacks to identify users. This mode will also break websites who depend on these features to work correctly.
—–
You can easily see how Strict only improves this like 0.1% but breaks too many websites. So yes, Standard IS enough, especially if Brave doesn’t want to break the web.
It is a terrible idea to want to break the web because of paranoia, WebGL is important, and only because it exists, doesn’t mean it will be used for anything besides let you have 3D in the web and all that.
So this is why Strict was a nightmare, so many people posted in Brave community and reddit how something broke, and many were cases when people wanted strict protection, but didn’t understand if Strict will give or not an a real advantage.
People can test Brave’s fingerprinting in dev-pages.bravesoftware.com website and see for themselves what it does and it is not doing it.
The flag still exists anyway brave://flags/#brave-show-strict-fingerprinting-mode so I don’t get the issue, when today, anyone can still enable it in Nightly, but like I said, people aren’t researching and understanding how bad Strict is for the web, because anything that breaks the web, and can’t be fixed as the adblocker can (which has broken many websites a lot through the years) it is just bad to have, and should be removed.
If Standard is improved, then good, as long as it doesn’t break websites, because it rarely breaks websites even if it still adds noise to the APIs.
> No WebGL page worked with it, so if someone who used sites with webgl support… what was the point of enabling the Strict fingerprinting support?
just have some tab isolation and user prompt when a site is legitimately webgl oriented, saying they will forefit strict fingerprinting support there?
For the creator of javascript there sure are a heck of a lot of simple oversights when it comes to bundling unwarranted mischief which then needs gullibles volunteering unpaid excuses for those actions/non-actions. Many dodgy things in firefox/brave could have been gated behind prompts or removed to voluntary extensions, it was a choice not to. Come on.
> “It is a terrible idea to want to break the web because of paranoia, WebGL is important, and only because it exists, doesn’t mean it will be used for anything besides let you have 3D in the web and all that.”
Completely agree. IMHO the most effort you do to not being tracked the worst privacy sensation you will get. I spent hours and hours in the past to increase my privacy, however now I use Chrome/Fifefox/Edge configured to clear automatically everything on exit. Also I have a dynamic IP provided by my ISP, and I browse every single day with some pleasure because my online tracking is only done per session. I don’t care about next session.
I have strict fingerprinting enabled, but when I go to https://fingerprint.com
I will be fingerprinted as many times as I go back even when I close the browser. But when I visit in Private Mode, it is unique every time, even when I close the browser.
Because I have strict fingerprinting enabled, I have to disable Brave Shields on my banking website…but I still have my VPN enabled.
Probably because this website makes use of local state to re-identify you. Try to enable “Forgetful browsing” under brave://settings/shields…
This should get rid of caches, cookies etc. which are likely behind this. Websites also track IP addresses so if Forgetful Browsing doesn’t help, it’s probably that.
I didn’t install Brave on my new machine and I removed it from the old one
I will use Brave when I learn that they are not installing their VPN stuff on my machine, even if it is inactive, without my permission.
Yeah……
I’d used Brave as my back-up browser on my laptop until that happened. I’m using Vivaldi instead now.
It doesn’t use up dev time because we strict users don’t report broken sites, we just use a different browser for them.
+1
*fistbump*
As I see it the very concept of blocking fingerprinting makes sens if it is fully achieved, I mean that a ‘soft” approach means that fingerprinting is *not” blocked. On the other hand it appears that a ‘strict’ anti-fingerprinting mode poses issues at least occasionally and even should it run flawlessly would there ever be an certainty of a 100% bulletproof achievement?
A lucid user’s approach IMO is to make things tougher for the intruder, not to believe he may be defeated.
Personally here on Firefox,
– I do not use the Resist Figerprinting (RFP) setting : privacy.resistFingerprinting = false
– I do use the First Party Isolation setting though : privacy.firstparty.isolate = true which doesn’t prevent my device from being recognized but aims to isolate its data from other sites …
I use the ‘ETag Stoppa’ extension (“Prevents Firefox from storing entity tags by removing ETag response headers unconditionally and without exceptions.”)
I no longer use the ‘CanvasBlocker’ extension because, in its enhanced mode (again : partial is IMO a misleading concept) it requires too many exceptions for several sites and, on an old PC as mine at least, does slow down page rendering, not excessively but it does, as many extensions by the way among those who are active on every page load.
What has always bothered me is not the fact of being recognized (my device that is, though we know that it is possible to determine more than a device, the very user i.e.via the way he uses the keyboard…), but that one site know where I come from and where I go to : cross-site tracking.
At the end anti-fingerprinting conceived as a mean to not be recognized makes sens when using a VPN : whatever your IP fingerprinting will spot you. But no VPN, you’re spotted by your IP, so what the heck of using anti-fingerprinting? Frankly, IMO, without a VPN the only intrusion to try to block is cross-site tracking.
Globally speaking, in terms of a user’s psychology, terms which are essential in his approach of his very privacy, you have and always will have three answers to an intruder’s request to undress ourselves :
1- Yes sir,
2- Underwear as well?
3- Move off, jerk.
Even if you get naked at the end, at least try answer (3).
@Tom Hawack
I use two modes(or profiles or browsers – Firefox & Librewolf. Both are essentially same and Firefox can be configured to look like Librewolf) for browsing web.
1. Firefox with ETP strict(used to select custom mode with FPI enabled but with Firefox containers I’ve switched to dFPI and strict mode). Disabled DRM. This profile is used for logins as I’ve assigned Google(old account), Meta websites to their respective containers, and then other logins on a separate container. Little to no breakage for login stuff & cookies, site data from different websites remains isolated from each other. One disadvantage of dFPI was unlike FPI which was strict and allowed no exceptions, dFPI was more relaxed as it can allow exceptions with a click. So I now use Firefox Container to mitigate that issue.
2. Librewolf – RFP enabled, WebGL disabled. This is the one I use mostly. The reason I disable WebGL is to prevent my graphic processor from being used by websites – security and privacy benefits with this move. If a site needs WebGL I have 1st mode to switch to for that site. I use RFP so no automatic dark mode and UTC remains 0 which helps with standard time on all sites, with or without VPN. DRM disabled. All data cleared on exiting the browser. Temporary containers is installed so I don’t have to use incognito tabs, but I never dived deep into this extension to replace Firefox container on 1st mode.
@Yash, the main thing is to consider our privacy, find a configuration that fits our needs. I’m not sure even an expert could assert there is an optimal, an ultimate per-browser configuration. Once we have our privacy targets in mind we must adjust settings, prefs accordingly : like with a motor engine modifying one thing is likely to have an impact on another which in turn may require to be modified itself in turn : many settings are interconnected and often an issue may appear because we’ve modified one pref without considering the impact on others …
I know nothing of Librewolf, and I admit having so much focused on optimizing Firefox (for my needs and arguably the best way) that I’ve put aside a healthy curiosity for other browsers : I’ve drilled the oil (Firefox) rather than scanned for other perhaps as/more worthy spots/browsers.
I don’t use Firefox’s ETP (Enhanced Tracking Protection) and I’ve focused on FPI (First-Party Isolation). To be coherent this choice (which is arguable and argued : I’ve read several articles that consider FPI as a feature of the past bound to disappear) has implications. Hereafter perhaps the main ones though there are many others likely less or not at all related ones.
Again, we do it our way, this is not an expert’s work and even less advice. I may very well be mistaking in the general scope mainly of preferring FPI.
Have a nice day after a lengthy though partial summary:)
// TRACKING PROTECTION (ETP) MODE
// ‘strict’ or ‘custom’. Strict mode includes Total Cookie Protection and Smart Block and a stricter list
// NOTE : if ‘custom’ then dynamic storage partitioning is disabled for all sites
pref(“browser.contentblocking.category”, “custom”);
// COOKIE BEHAVIOR
// 0 = BLOCK NONE, 1 = BLOCK 3RD-PARTY, 2 = BLOCK ALL, 3 = block unvisited, 4 = block trackers, 5 = ISOLATE ALL (default)
// NOTE-1 : This also controls access to 3rd party Web Storage, IndexedDB, Cache API and Service Worker Cache
// NOTE 2 : Auto-sets and resets to 5 if “browser.contentblocking.category” = “strict”
// HANDLED BY Toggle-cookie-behavior.uc.js => DO NOT LOCK
pref(“network.cookie.cookieBehavior”, 1);
pref(“network.cookie.cookieBehavior.pbmode”, 1);
// ENABLE FIRST-PARTY ISOLATION (FPI)
pref(“privacy.firstparty.isolate”, true); // DEFAULT=false — WE ENABLE AND LOCK
// WITH FPI ENABLED SOME SITES HAVE A TENDENCY TO BREAK SO WE HAVE PRIVACY.FIRSTPARTY.ISOLATE.RESTRICT_OPENER_ACCESS TO OFFSET THE BREAKAGE.
pref(“privacy.firstparty.isolate.restrict_opener_access”, true); // DEFAULT=true
// IF ‘PRIVACY.FIRSTPARTY.ISOLATE.BLOCK_POST_MESSAGE’ IS TRUE, POSTMESSAGE ACROSS DIFFERENT FIRST PARTY DOMAINS ARE BLOCKED
pref(“privacy.firstparty.isolate.block_post_message”, true); // DEFAULT=false
// DO NOT ENABLE SCHEME WITH FPI [FF78+]
// EXISTING DATA AND SITE PERMISSIONS ARE INCOMPATIBLE AND SOME SITE EXCEPTIONS MAY NOT WORK E.G. HTTPS-ONLY MODE
pref(“privacy.firstparty.isolate.use_site”, false); // DEFAULT=false — WE ENFORCE FALSE
// DISABLE DYNAMIC FIRST-PARTY ISOLATION (DFPI)
// NOTE : “It seems safest to disable dfpi when fpi is enabled.” [https://bugzilla.mozilla.org/show_bug.cgi?id=1631676]
// DFPI isolates all third party cookies and storage, similar to FPI.
// DFPI uses a new key (partitionKey) instead of the existing firstPartyDomain key to isolate cookies.
// The most important difference between DFPI and FPI is that DFPI will adhere to exceptions granted through the storage access API and thus ensure better web compatibility
pref(“privacy.dynamic_firstparty.use_site”, false); // DEFAULT=true
@Tom Hawack
Yeah I get that. Infact when it comes to fingerprinting one should use Mullvad or Tor.
I suppose it was mistake from my part to make a comment and not mention the main points – how do you see ETP strict now compared to FPI? I used to enable FPI which overrides dFPI. Main reason was to prevent indirect access of sites through prompts as possible in dFPI, and also to disable Firefox’s tracking protection feature which used to cause problems on select sites. But now after trying containers as main feature, not as an afterthought, it came to me dFPI can be made strict using them and container takes superiority when put on same floor with dFPI and FPI. Plus those sites which needed exception in ETP strict mode work fine now. So I stopped using FPI. Then I read your comment in which you use container along with FPI. Just want your perspective on continued use of FPI even with containers
@Yash,
> “how do you see ETP strict now compared to FPI?”
In the very same terms as yours.
> “But now after trying containers as main feature, not as an afterthought, it came to me dFPI can be made strict using them and container takes superiority when put on same floor with dFPI and FPI. (…)”
Now this is a scoop for me and should I have one solid reason to revert to dFPI and abandon FPI (disabled by default BTW) it’d be for the very reasons you’ve experienced. This is really a major point for me. especially that I use the ‘Temporary Containers’ extension in automatic mode (all tabs are systematically isolated).
Many thanks for pointing it out.
In my opinion, best privacy method is using a “non-fixed” IP combined with automatic deletion of all kind of navigation trace after browsing, using own browser’s clear methods or even using third party software. Doing this for at least five months with no kind of problem at all, simplest way of browsing with relax and no browsing warning nor websites malfunction neither. In other words, the most you fight against privacy, the worst sensation of being invaded you will get.
@John G., a device’s dynamic (“non-fixed”) or static IP is decided by the user’s ISP, at least in my case. I think it is mostly static for what I know. Mine is static, though recently was modified by the ISP after more than 3 years …
Deleting traces is the way to go, I agree. Perhaps the idea is to consider to what degree.
@TomHawack: I forgot to add that I had used ETag Stoppa as well. But with Temporary Containers it’s no longer necessary. This is what the Etag Stoppa author writes on AMO:
“Keep in mind that ETags are only *one* of the known tracking/de-anonimizing vectors related to the cache. I am aware of at least three other less straightforward methods to exploit the cache for those purposes. If you are absolutely serious about your privacy, do not rely on this extension. Instead, disable the cache and/or use another extension like Temporary Containers in automatic mode.”
Temporary Containers is no longer maintained (Claustromaniac has passed on.) and I’ve stopped using it…..
Correction:
It’s not Claustromaniac, it was *Stoically* who maintained the Temporary Containers extension and who has passed on!
Sorry.
Most valuable information, thanks.
So, if the ‘Temporary Containers’ extension is installed and run with automatic mode, following extensions become obsolete :
– ETag Stoppa
– CookieAutodelete (which has an option to manage Containers but advises to avoid it, i’ve tried and agree).
I’ve removed CookieAutodelete, and will now remove’ETag Stoppa’ … and leave a note in my extensions’ archives that these 2 have been removed because of ‘Temporary Containers’.
—
You had mentioned the ‘JShelter’ extension which I had tried years ago. Just installed it again for the sake of curiosity : in default mode hasn’t broken any of the few “heavy” sites I tested, handles Canvas as well. But I’m not sure it’s pertinent given my browser privacy approach (cross-site tracking rather than site fingerprinting).
@TomHawack: Tom, I don’t use RFP, either. However, since Firefox 120 there is FPP (fingerprintingProtection) as an alternative – see https://github.com/arkenfox/user.js/wiki/3.3-Overrides-%5BTo-RFP-or-Not%5D. It’s discussed on https://github.com/arkenfox/user.js/issues/1716.
privacy.fingerprintingProtection=true randomizes canvas according to arkenfox.
I’m also using the JShelter add-on. More info on https://jshelter.org/
@linuxfan, I beg your pardon however I must disagree certainly a lot with the deep way apply by you to deal with the fingerprint traces and other related issues by your side. In my experience the easiest method to avoid the long term fingerprinting privacy problem is just to clear the traces/cookies and so forth annoying mess when you finish browsing (i.e., using the own automatic cleaning capabilities of the browser at exit, or even using some kind of third party browser utilities like Ccleaner). Just please read the next article (also recommended for @TomHawack), because it contains the technical explanations about I meant, you both will understand better my point of view, about the weird fact that the less effort applied by myself to be traced while browsing just gives me the more sustainable results on privacy.
https://fingerprint.com/blog/browser-anti-fingerprinting-techniques/
@John G. :
> In my experience the easiest method to avoid the long term fingerprinting privacy problem is just to clear the traces/cookies and so forth annoying mess when you finish browsing (i.e., using the own automatic cleaning capabilities of the browser at exit, or even using some kind of third party browser utilities like Ccleaner).
That‘s what I‘m doing anyhow. And Temporary Containers additionally does it during the browsing session for every single website.
And summarizing what I’ve learned up to now about the implications of using the ‘Temporary Containers’ Firefox extension :
– The ‘Cookie Autodelete’ extension becomes obsolete (thanks @linuxfan);
– The ‘ETag Stoppa’ extension becomes obsolete (thanks @linuxfan);
– “(…) container takes superiority when put on same floor with dFPI and FPI” (thanks @yash)
I’ll have to test the 3rd implication but given my Firefox configuration is heavily tweaked, because reverting from FPI to dFPI will require other modifications, it’ll be done when I get the time.
Point is this ‘Temporary Containers’ extension, because it adds to the advantages of the Container feature the ability of cleaning a closed container during the very session (when in automatic mode), is a true gem in the scope of what I aim for on a browser.
Thanks to all.
@linuxfan, I acknowledge what is for me news : Firefox FPP (Fingerprinting protection), news because I’m running Firefox 115.* ESR. Tanks for the info and for the link.
Anyway, randomizing the canvas can be performed with the ‘CanvasBlocker’ extension I mentioned above and, though native blocking is always a better option (given equal/better quality) it remains an anti-fingerprinting tool among many other fingerprinting intrusions and, as far as I’m concerned and for the reasons I mentioned, given I use no VPN, the anti-fingerprinting battle doesn’t make great sens, IMHO again and of course.
“a fraction”
I don’t think most users who care enough to use the strict setting would have telemetry on. There’s a pretty strong Venn diagram overlap between the “uses strong privacy measures” and “disables telemetry” users.
With that said it is a hassle and it does eat up devtime – and they don’t have as much staff as Mozilla, Microsoft and Google to remedy it properly. So as a result they’ve been doing a shoddy job at it *and* at the browser itself for it. I understand their reasoning and am looking forward to the browser getting better – Firefox is getting on my nerves and this is the only remotely comparable browser to it so I’m excited for the future.
I’ve been using Firefox’s optional highest-level fingerprint blocking (open about:config, then set privacy.resistFingerprinting to “true”) since it was available, as well as having Enhanced Tracking Protection (open Settings – Privacy and Security) set to “Strict”, and have additional tweaks, and I’m simply not seeing much site breakage. Most of the web works just fine even with fairly strong anti-fingerprint measures in place.
Re the statement “Browser makers like Brave Software or Mozilla have introduced anti-fingerprinting capabilities into their browsers long ago. These are designed to render fingerprinting attempts useless”. Well, no. Browsers can use measures like these to make fingerprinting more difficult, but they’re not 100% effective. It’s more a question of how much energy the site is willing to put into fingerprinting vs how much energy you are willing to put into countering it.
> I’ve been using Firefox’s optional highest-level fingerprint blocking (open about:config, then set privacy.resistFingerprinting to “true”) since it was available, as well as having Enhanced Tracking Protection (open Settings – Privacy and Security) set to “Strict”, and have additional tweaks, and I’m simply not seeing much site breakage.
What makes you think your browsing is representative for everyone else’s? Yash makes the same mistake in his comment, it doesn’t mean anything. I would rather trust the devs of the browser who receive breakage reports from multiple users than the anecdotal account of single users writing here.
“The third argument is that the feature is used by fewer than 0.5% of all Brave users. Brave Software argues that the small number could make fingerprinting more likely.”
lol
Just the same reason that Microsoft says about the taskbar… “99.99999% uses it at bottom”. LOL.
Brave’s fingerprinting protection were always trash. I use RFP and WebGL disabled on FF and save for some sites I can count on my fingers, I haven’t run into compatibility issues. Even in Firefox ETP strict mode I’ve yet to disable it on a site. Brave couldn’t build a proper strict mode to prevent fingerprinting and now they’re making an excuse. Mind Brave aren’t even developing Chromium engine. Goes a long way to show all they add to their browser is crypto nonsense and couldn’t even maintain a proper fork.
> Brave’s fingerprinting protection were always trash.
No, what is trash is the idea that you can configure your browser yourself in a unique way to combat fingerprinting, which is exactly what you do to Firefox.
> I haven’t run into compatibility issues
Who cares? Your browsing is not reflective of everyone else’s.
> Even in Firefox ETP strict mode I’ve yet to disable it on a site
Speaking of trash, Firefox’s tracking protection is based on the very weak Disconnect list, so no wonder you are not running into any issues lmao.
> Brave couldn’t build a proper strict mode to prevent fingerprinting and now they’re making an excuse
No, Brave is a general purpose browser and as such has to strike a compromise between privacy and usability. Contrary to projects like Tor BB, that absolutely prioritize priavyc over usability.
> Goes a long way to show all they add to their browser is crypto nonsense and couldn’t even maintain a proper fork.
Has development ceased or why can’t they “maintain a proper fork”?
@Iron Heart
“Speaking of trash, Firefox’s tracking protection is based on the very weak Disconnect list, so no wonder you are not running into any issues lmao.”
I wrote ETP strict mode which is hell lot more than weak disconnect list. Mind Mozilla knows disconnect is weak hence it provides uBlock Origin on every platform even Android so even normies can use it. Back to main point why is Brave team so interested in scrapping strict mode? I get WebGL randomization causes website breakage but isn’t that the whole point? You use strict settings on all sites and change it on select sites which need WebGL.
It is amusing that basically all use standard mode. Most people just use browsers without configuring them because someone told them to. Explains why so many use “adblock” instead of ublock origin.
One of the many reasons I stopped using brave in favor of Librewolf.
Brave was a good, privacy focused browser at one point but that is no longer the case.
> Brave was a good, privacy focused browser at one point but that is no longer the case.
…because?
In addition to what Iron Heart mentioned, how about forced download of unverified AI components that could have thrown my entire business out of regulatory compliance?
Don’t give the “you can disable it” cope mechanism either. Cost many hours of otherwise productive time getting the systems verified, reverted to 1.59 and lock down the brave update mechanisms until an alternative browser could be found.
Any company that has forced updates and then mingles security updates with new features has no clue what they are doing from a security standpoint.
VPN malware, questionable financial supporters like FTX. Eliminating privacy friendly settings, laying off developers, built in trackers Brave claimed were “bugs” when called out.