Oblivious DNS standard promises improved privacy
Oblivious DNS is a new proposed DNS standard that has been co-authored by engineers from Apple, Fastly and Cloudflare to improve privacy during DNS operations.
DNS is a fundamental cornerstone of the Internet as it translates domain names, e.g. ghacks.net, into IP addresses that computers use. Whenever you connect to a site on the Internet, DNS is needed.
DNS involves a client device, e.g. a user PC, and a DNS server. The server may be operated by the user's Internet Service Provider, but it is also possible to change it to another provider as it may result in better performance and privacy.
The introduction of encrypted DNS standards, DNS over HTTPS and DNS over TLS, protect DNS traffic against third-parties listening in. DNS traffic alone is valuable as it includes all destinations a user visits when using the Internet.
While DNS traffic is encrypted if one of the encryption standards is used, it is still the case that the DNS provider has access to the IP address of the device the user uses and all the destinations. The proposed standard ODoH (Oblivious DNS over HTTPS) promises to change that.
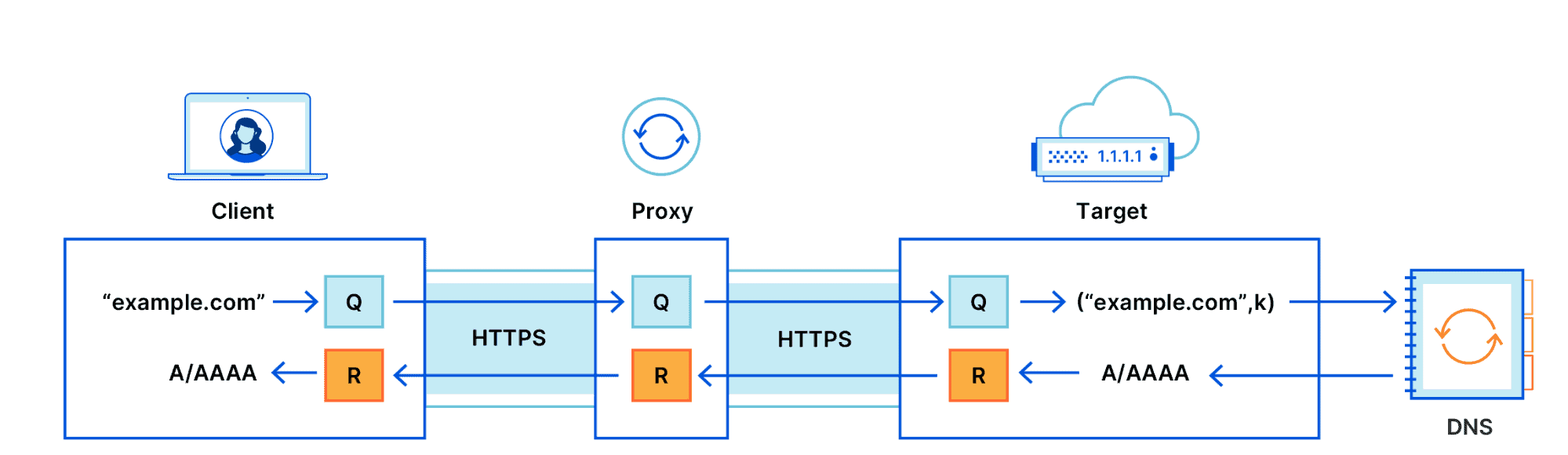
Basically, what ODoH does is add a proxy to the requests that sits between the client device and the DNS provider.

Traffic flows through the proxy and that results in improved privacy.
- The DNS provider communicates only with the Proxy and not the client. In other words, the DNS provider sees the proxy IP but not the IP of the user device.
- The Proxy sees the user IP as it communicates directly with it, but it has no information on the DNS request as it is encrypted.
ODoH adds another level of encryption to the DNS message itself to ensure that the proxy cannot read it. Cloudflare has published a detailed overview of Oblivious DNS that provides additional technical details. The research paper Oblivious DNS over HTTPS (ODoH): A Practical Privacy Enhancement to DNS provides additional details.
Cloudflare ran benchmarks to determine the performance cost of ODoH. It compared the performance to DoH and concluded that there is a cost, but that it is marginal.
Cloudflare's DNS Resolver 1.1.1.1 supports ODoH already; the company has open sourced implementations, Support may come to Firefox in the future, as confirmed by Eric Rescorla, CTO of Firefox.
Closing Words
Oblivious DNS separates a device's IP address from its DNS queries. That is a good thing as it prevents that DNS providers link IP addresses to DNS queries.
Now You: what is your take on Oblivious DNS?





















“ODoH adds another level of encryption to the DNS message itself to ensure that the proxy cannot read it.”
I heard about a meta search engine using that trick too some time ago, maybe on this very site. This should be used for more types of services.
Just use dnscrypt-proxy….
DNSCrypt-Proxy:
https://github.com/jedisct1/dnscrypt-proxy/wiki/Installation-linux
Public Resolver list:
https://dnscrypt.info/public-servers
sudo -s
ss -lp ‘sport = :domain’
Should be nothing listening – disbable any running processes that are listening
systemctl stop systemd-resolved
systemctl disable systemd-resolved
https://github.com/jedisct1/dnscrypt-proxy/releases/latest
dnscrypt-proxy-linux_x86_64-*.tar.gz
Unpack and move “linux-x86_64” to /opt/dnscrypt-proxy (rename to “dnscrypt-proxy”)
cd /opt/dnscrypt-proxy
cp example-dnscrypt-proxy.toml dnscrypt-proxy.toml
./dnscrypt-proxy
Should see resolvers
[create a symbolic link from /opt/dnscrypt-proxy/dnscrypt-proxy to /bin/dnscrypt-proxy]
sudo cp /etc/resolv.conf /etc/resolv.conf.backup
sudo rm /etc/resolv.conf
sudo nano /etc/resolv.conf
Add:
nameserver 127.0.0.1
options edns0 single-request-reopen
In a NEW terminal check as user (not root):
/opt/dnscrypt-proxy/dnscrypt-proxy -resolve example.com
Install as service:
Hit Control and C in the previous dnscrypt-proxy terminal window to stop the proxy.
Now, register this as a system service (still with root privileges):
./dnscrypt-proxy -service install
./dnscrypt-proxy -service start
Want to stop the service?
./dnscrypt-proxy -service stop
Want to restart the currently running service after a configuration file change?
./dnscrypt-proxy -service restart
Want to uninstall the service?
./dnscrypt-proxy -service uninstall
Want to check that DNS resolution works?
./dnscrypt-proxy -resolve example.com
Running as a non-root user:
The following command adds the required attributes to the dnscrypt-proxy file so that it can run as a non-root user:
sudo setcap cap_net_bind_service=+pe /opt/dnscrypt-proxy/dnscrypt-proxy
If the content of /etc/resolv.conf doesn’t stick after reboot
Edit it, then type the following command (in a root console) to lock it:
chattr +i /etc/resolv.conf
To unlock it:
chattr -i /etc/resolv.conf
*************************************
Settings /opt/dnscrypt-proxy/dnscrypt-proxy.toml
Changed:
server_names = [‘cisco’] (Test at https://welcome.opendns.com/)
ignore_system_dns = true
So another dns standard.We already have:
DOH
DOT
DNS Crypt
DNS Curve is another proposed standard.
I think there were another 2 or so proposed dns standards I read somewhere but can’t think of them.
OT: Martin, have you already seen this bit of news? Mozilla moving out of Mountain View, giving up their headquarters… Financial reasons?
https://www.sfchronicle.com/business/article/Mozilla-moves-out-of-Mountain-View-15786106.php
I have, financials may play a role, but Covid-19 and working from home plays probably a more important one.
The encryption allows identification, no need for a ip when you can assign unique ids via proprietary encryption schemes to better uniquely identify a device than any ip could. This is the usual cloudflare smokescreen.
Indeed, same old story. Some corporation really really wants some userdata, metrics or whatever, so they bamboozle folk into giving it away. A large percentage will fall for it, and fall for that, and the other. Soon enough all the data is being feasted on by all the companies you didnt trust at the start. Easy game really.
So, reinventing DNScrypt-proxy then? Which already works…
Can you provide more info or a link on this.
DNSCrypt project
[https://github.com/DNSCrypt/dnscrypt-proxy]
Anonymized DNS is here!
[https://github.com/DNSCrypt/dnscrypt-proxy/issues/960]
People should more worried by Microsoft, Google and Apple’s spying through their OS than about somebody logging DNS requests. You got anonymous DNS but you’re logged in to Google and it’s recording your entire web history and GPS coordinates, think hiding your DNS requests is going to make any difference?
At this point this conversation has to happen, especially when Linux is at an all-time high for desktops (3.61 percent in June 2020). This may not sound like much but it’s a significant increase, and regardless of the reason people are making that shift it inherently improves privacy to those users even if they continue using services like Facebook and the like.
Encrypted DNS has benefits other than logging by a handful of companies like circumventing blocked sites and online services. At it’s core is far better to have your DNS traffic recorded by fewer organizations.
This is not to say that people shouldn’t be concerned about privacy violations happening in their own devices either at software, firmware or hardware levels. As usual it’s another piece of the puzzle, but it’s important to realize this is an outdated protocol that is being systematically exploited for the benefit of few.
https://www.omgubuntu.co.uk/2020/07/linux-marketshare-june-2020
https://infosec-handbook.eu/blog/hns5-dns-configuration/#dns-security-privacy
Nice, but who owns the proxies?
Did we not just change our DNS lookup from our nosey internet provider to some other provider who we hoped was was less nosy? And now we change it from this other provider to yet another proxy provider in between. Seems like someone somewhere is gonna see all our porn site DNS requests. /s
Asking the correct question right there.
If one understands you correctly, the behavior you attempt to describe can be stopped in Firefox by setting network.trr.bootstrapAddress to the DoH sever IP address.
That’s good news. I’ll be waiting eagerly for ODoH being implemented by other services.
As long as the internet-router/gateway does ODNS, DOH or whatever, it would be Ok. But as long as the webbrowser directly asks an outside ODNS/DOH before asking the underlying OS and local DNS, it’s not Ok. Because ODNS and DOH first will try to resolve internal webservers on the external DNS, they will fail and only then they will use internal DNS. So the exterenal DNS could collect internal hostnames, and for many company internal domainnames it’s very clear to which companies these internal adresses would belong. just guess that phantasy name: superdupersecretserver.mercedes-benz.local. I don’t want to see my internal adresses to appear on external dns requests. So I disable DOH and ODNS.
whats your thought on dnscrypt? like simplednscrypt it good for privacy?
I used dnscrypt on a mac with DNSCrypt Menubar 1.0.14 set to Adguards DNS and had no problems.