Windows 10 build 20185 comes with encrypted DNS settings
Microsoft published a new Windows 10 build to the Windows Insider Dev channel today that brings a number of improvements including options to configure encrypted DNS right in the Settings.
DNS-over-HTTPS is a relatively new security feature that aims to protect DNS traffic from third-parties. It encryptes DNS traffic using HTTPS; DNS is used to "translate" human-readable host names, e.g. ghacks.net, into IP addresses that computers use.
Unencrypted DNS traffic allows the network provider, e.g. the ISP, and other third-parties that have access to the same network, to check which sites are visited. Furthermore. it is possible for ISPs to alter requests, e.g. by blocking them or redirecting them.
Microsoft announced some time ago that its Windows operating system will support encrypted DNS. Up until now, browser makers like Mozilla or Google have started to integrate support for the feature in we browsers.
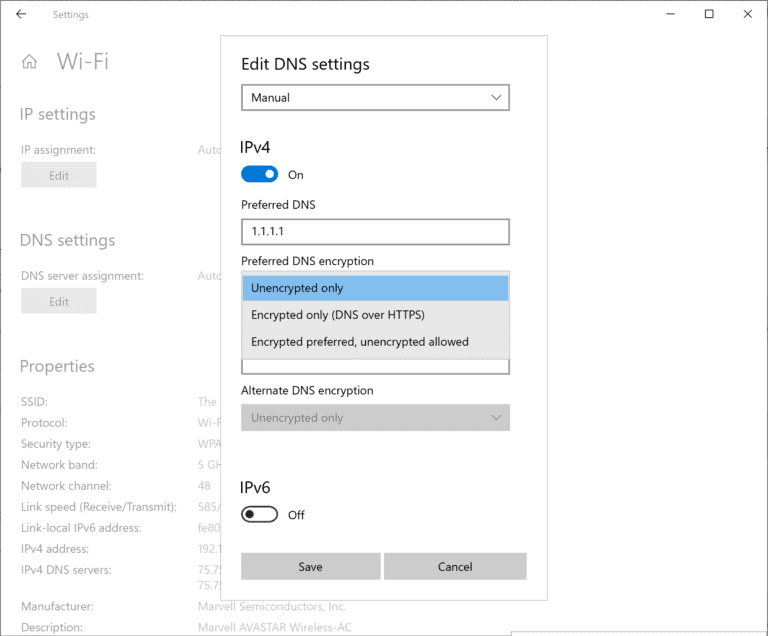
Windows 10 Insiders could add support for DNS-over-HTTPS for a while to the operating system; this required editing the Windows Registry though. The new Windows 10 build introduces support in the Settings.

Microsoft added support for DNS-over-HTTPS for ethernet and Wi-Fi connections.
For ethernet:
- Go to Settings > Network & Internet > Status.
- Click on Properties.
- Select Edit IP assignment or Edit DNS server assignment.
For Wi-Fi:
- Go to Settings > Network & Internet > Wi-Fi.
- Click on the Properties link.
- Select Edit IP assignment or Edit DNS server assignment.
The current build recognizes only some DNS-over-HTTPS providers by default, namely Cloudflare, Google, and Quad9. These are the same that Microsoft revealed back in May when it launched support for the feature.
| Server Owner | Server IP addresses |
| Cloudflare | 1.1.1.1
1.0.0.1 2606:4700:4700::1111 2606:4700:4700::1001 |
| 8.8.8.8
8.8.4.4 2001:4860:4860::8888 2001:4860:4860::8844 |
|
| Quad9 | 9.9.9.9
149.112.112.112 2620:fe::fe 2620:fe::fe:9 |
Type or paste an IP address on the page and select one of the available DNS encryption options afterwards.
The options are:
- Unencrypted only.
- Encrypted only (DNS-over-HTTPS).
- Encrypted preferred, unencrypted allowed.
Confirm your selection and and check whether it is working by looking at the DNS servers in the network properties. They should show (Encrypted).
Microsoft notes that Windows 10 admins may try custom DNS-over-HTTPS servers as well. This requires the use of the netsh command, however:
netsh dns add encryption server=<your-server’s-IP-address> dohtemplate=<your-server’s-DoH-URI-template>


















Stay away from corporate-run DNS-Over-HTTPS servers if you want to keep your privacy, and the Internet free! If you’re concerned about privacy, set up your own DNS resolver (i.e. BIND).
And don’t participate in the DNA collection scam called SARS-CoV-2 testing!
One thing left out of this article, from the first link,
“…we have enabled 647 new MDM policies across 56 ADMX files to enable commercial customers to configure policies that are also supported through Group Policies.”
647 more?! My Pro currently has 210 ADMX files. We have to search for the 56 that have been modified or added and spend hours filtering through gpedit?
One update after another to fix all the problems this could create. Because MS finally got 1909 working well? Yup, that’s why!
Windows is a toy for a bunch of corporate clowns’ amusement. This stuff ain’t gonna stop…
Yeah, whatever. Three DNS providers I’d never use with Windows doing the encryption after you send it a request.
The Windows network stack is such a cobbled mess, this should make it even slower and less reliable. Unless independent sources verify MS isn’t collecting all your requests, now and forever, I don’t trust this at all.
It’s needed to make Chredge do https DNS since Chromium gets its DNS from Windows; FF does not. Use an external tracker blocker that offers the service, not a browser or OS. If you’re good with router firmware, Merlin/Voxel and stubby/dnscrypt/masq, brew your own, will do it.
Linux networking is day and night different from Windows, faster connections and faster data transmission. Change your IPS DNS servers in your router (http is fine) and you’re way ahead of Windows.
I rather use the control panel dialog. I can’t follow anything inside that hideous settings page. Why is still designed for mobile devices? When will it look like something made for desktop computers?
I am kinda skeptical about this DNS over HTTPS push by big American corps in the name of privacy, it looks more like an attempt to stop people from having control over their own networks, bypassing all the DNS filtering people setup, so they can feed your data uninterrupted to the interested parties over a handful approved DoH providers like Cloudflare.
Also I trust my internet provider more than some faceless corp and a middle man a continent away.
You can point Firefox to your prefered DNS over HTTPS or DNS over TLS resolver or even set up your own DNS resolver. Also, other software (e.g., Chrome) keeps using the same DNS resolver and upgrades to encrypted DNS only if that resolver explicitly indicates support for it.
Yes, if I am the only user on my network I can change my browser’s or OS’ settings (for now), but what happens in the future when every random program on your computer or phone starts making DoH requests to some unspecified server on the internet and thus ignoring your wishes as user or network administrator in the name of “””privacy”””? Now you need to manually block every (known) DoH provider by its IP address in the firewall and/or do some fuckery with packet inspection to try to detect and block DoH requests.
Curious and worried how this will affect blocking using HOSTS file and Windows Firewall.
Will it mean that Microsoft IPs will become unblockable from within Windows?
see https://www.ghacks.net/2019/12/18/nextdns-is-new-firefox-dns-over-https-partner/ for Firefox DNS over HTTP ignoring the hosts file several ppl confirmed it.
@Martin Brinkmann
If this works anything like DNS over HTTPS in Firefox works this its a problem for those who block anything via the hosts file, the hosts file of the OS is ignored by Firefox when DNS over HTTPS is enabled, so I wonder what the mileage is with this set at OS side.
It sure would be interesting to find out, shame I dont do insider testing, well its not a shame but someone who does can test that scenario.
Yes, enabling DoH on Firefox bypasses the hosts file. That’s a “feature” on DoH in general I think, though I’m not 100% certain. Can someone confirm if that’s the case on Chrome as well?
If it is, makes you wonder why MS even bother flagging hosts files if they eventually plan to implement Windows-wide DoH anyway.
Mozilla is the outlier with that. The other implementations communicate with the native stub resolver.
For this to absolutely freely and independently to work, for the wider public a public key infrastructure is neccessary so as to be a strong and trustable contender to private sector adventures which are usually controlled by a few US corporations only.
This means that the state not only needs to give public money to the military, for education or what ever.
There needs to be a budget for internet and computer environments, debated and voted for in publicy open parlaments.
Were based on public debates, most people will be able to make qualified choices and be able to understand the implications of technologies on their daily life.
As of today the wider public in all so called democratic countries do not have much of a say in what is being decided for them between corporations and the state.
Not sure if I’m imagining things or what, but DOH seems to introduce some overhead. Quite a lot in fact, at least the browser implementation on both Chrome and Firefox. I have to wait longer for pages to start loading while using DOH; tested on multiple servers – Quad9, Google, ADGuard.
On Android, using system-wide DOH I don’t experience this latency. At least not to the extent as with using the browser implementation. I assume the OS is doing some caching, or it’s simply better optimised.
In my limited testing on Linux and Firefox (Wayland build on Fedora, X11 build on Debian, if that even matters) I haven’t experienced any difference in age loading, though I’ve only tested with Cloudflare, NextDNS and Quad9 so far. Possibly a Windows thing?