Chrome 83: rollout of DNS over HTTPS (Secure DNS) begins
Google started the rollout of DNS over HTTPS yesterday in Chrome Stable with the release of Chrome 83 Stable to the public.
The company calls it Secure DNS. DNS lookups are unencrypted by default; this means that DNS may be used to track the sites that an Internet user opens. Additionally, since it is unencrypted, bad actors may exploit it to manipulate or tamper with the connection, e.g. for phishing purposes.
DNS over HTTPS attempts to address this by encrypting DNS lookups. It uses HTTPS for that and that means that these lookups are more secure and private. DNS lookups cannot be used for monitoring a user's activity on the Internet anymore and bad actors cannot manipulate DNS responses for attacks.
Tip: Recent Windows 10 Insider Builds support DNS over HTTPs on the operating system level. All applications with Internet connectivity benefit from this if it is enabled.
Google made the decision to implement DNS over HTTPS in Chrome. The company decided that it would not interfere with the existing DNS setup of a system. Instead, it decided that it would use DNS over HTTPS in Chrome if the DNS servers that are set on the system support it.
In other words: the DNS settings are not changed. Another benefit of the approach is that certain add-ons, e.g. family safety protections or malware filtering, remain active.
Chrome will fall back to regular (unencrypted) DNS if issues are noticed during lookups. The browser won't use Secure DNS at all if parental controls are active on Windows systems or if certain Enterprise policies are set. New policies are available to enable DNS over HTTPS in managed environments.
Two of the main policies are:
​Dns​Over​Https​Mode -- Controls the mode of DNS-over-HTTPS (Chrome 78 and newer)
off = Disable DNS-over-HTTPS
automatic = Enable DNS-over-HTTPS with insecure fallback
secure = Enable DNS-over-HTTPS without insecure fallback
Dns​Over​Https​Templates -- Specify URI template of desired DNS-over-HTTPS resolver (Chrome 80 and newer)
The URI template of the desired DNS-over-HTTPS resolver. To specify multiple DNS-over-HTTPS resolvers, separate the corresponding URI templates with spaces.
If the DnsOverHttpsMode is set to "secure" then this policy must be set and not empty.
If the DnsOverHttpsMode is set to "automatic" and this policy is set then the URI templates specified will be used; if this policy is unset then hardcoded mappings will be used to attempt to upgrade the user's current DNS resolver to a DoH resolver operated by the same provider.
If the URI template contains a dns variable, requests to the resolver will use GET; otherwise requests will use POST.
Chrome users may enable DNS over HTTPS in Chrome right away. The rollout may take weeks or even months to reach certain devices. If you don't want to wait that long, do the following to enable the feature in Chrome right away (restrictions still apply):
- Load chrome://flags/#dns-over-https in the browser's address bar.
- Set the experimental flag to Enabled.
- Restart Chrome
Note that you may need to change the DNS servers on the device as they need to support Secure DNS. Google DNS, Cloudflare, Quad9, and Cleanbrowsing all support Secure DNS.
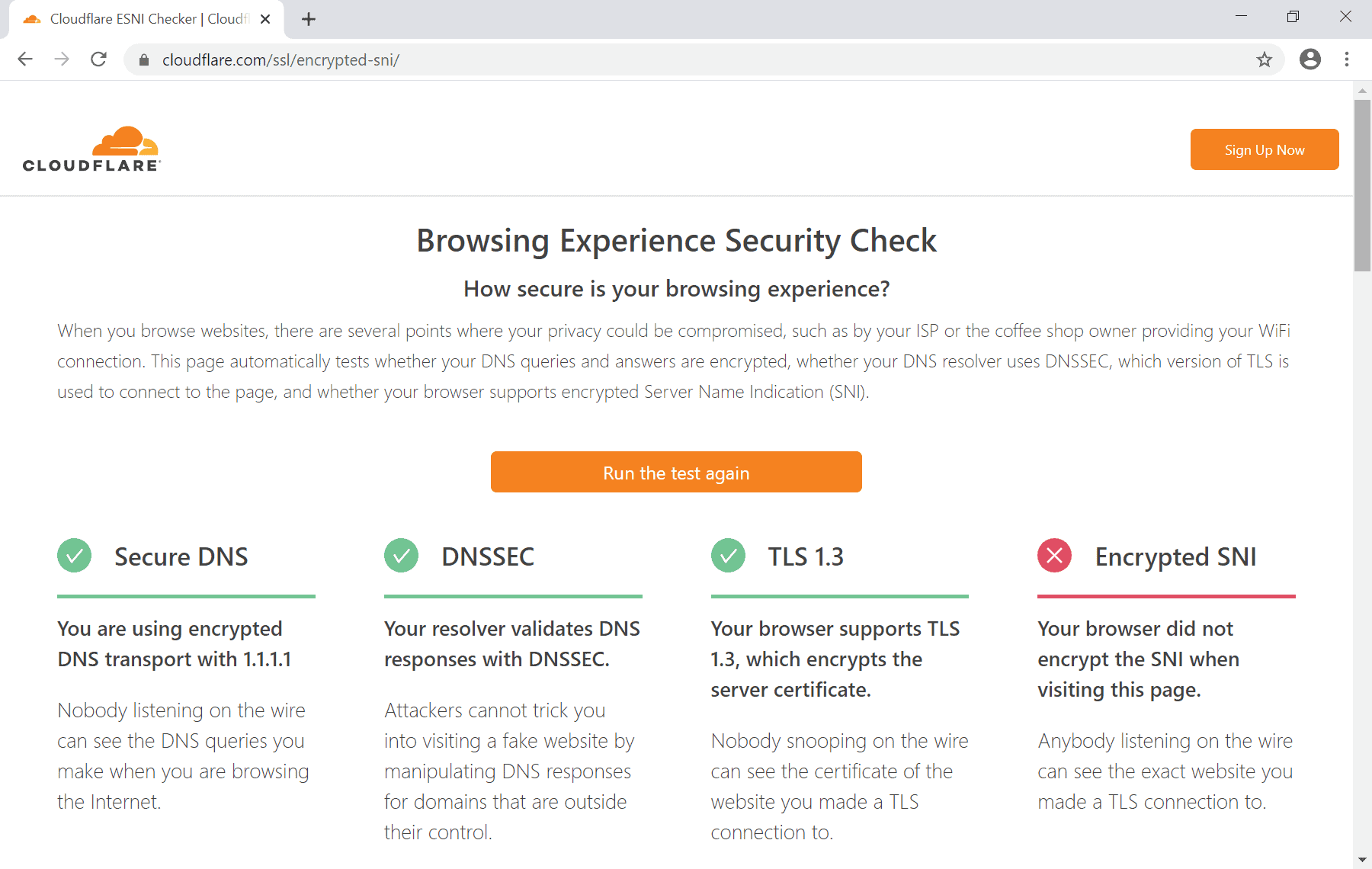
Tip: you can use Cloudflare's Browser Experience Security Check to test if Secure DNS is enabled in the browser.
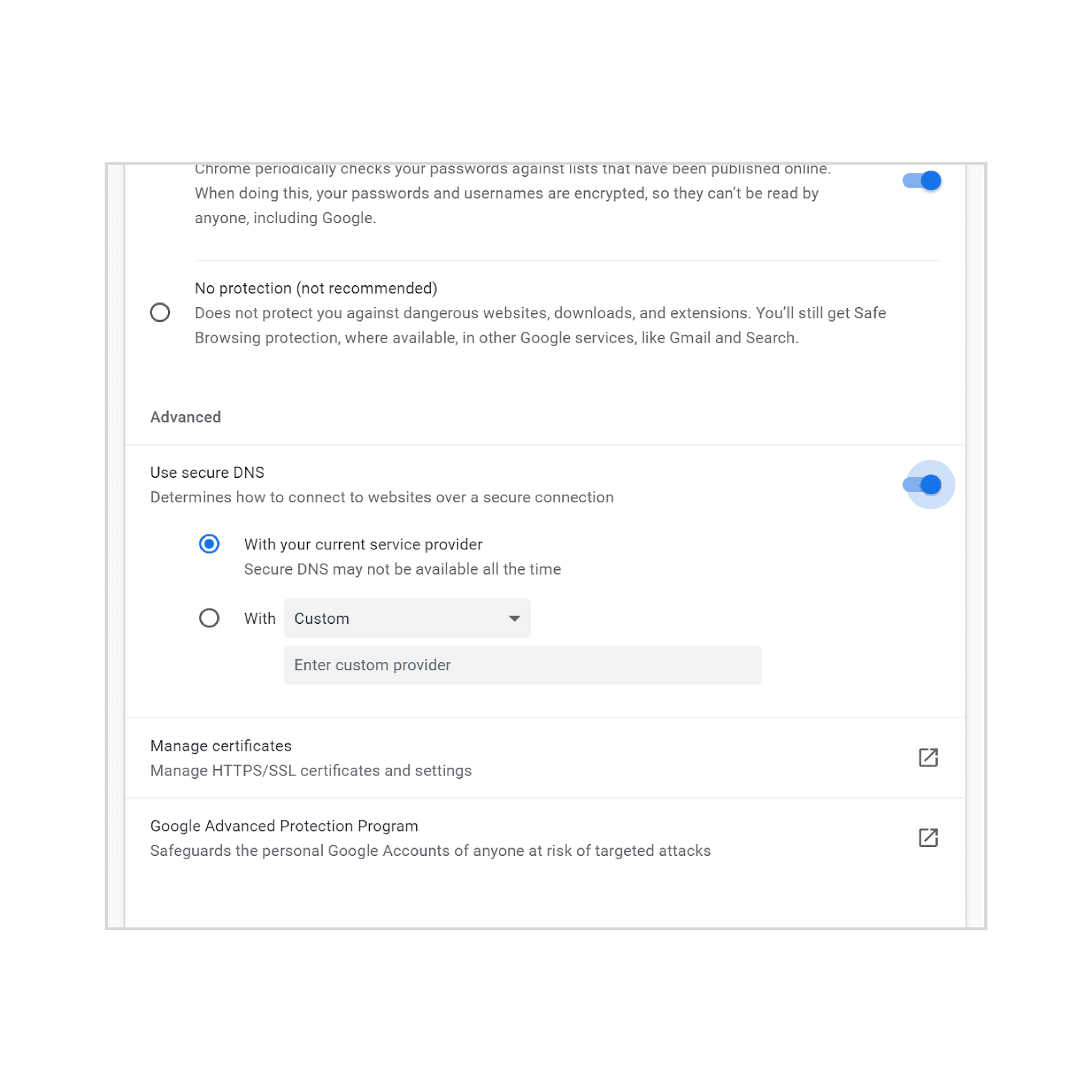
Google plans to introduce better preferences in the browser's Settings application. I checked Chrome 83 Stable and the latest Canary version and both did not have the updated preferences page yet.
You need to load chrome://settings/security in the web browser's address bar to access it. There you find a new option to enable or disable Secure DNS.
Chrome users who don't want to use it in the browser may turn it off right then and there once it becomes available.
Google plans to add an option to set a different DNS provider in the Settings; this should make it easier for users who have troubles modifying DNS settings on the network level.
Closing Words
Secure DNS will be made available on Chrome OS, Windows and Mac OS "progressively" according to Google. It will also come to Chrome on Linux and Android "soon".
Now You: Do you use DNS over HTTPs already on your system?



















There’s only one reason to use “secure DNS” (of whatever flavor): to ensure that the name you want to resolve with your name server actually results in the IP address coming from your name server. Whether some “expert” is blowing smoke one way or the other, for or against some “benefit” of securing DNS, is not relevant to the reason for using it.
If I am already using Simple DNSCrypt (on PCs) or DNSCloak (on iDevices), and I am already getting the reults above on the cloudflare ESNI test page, does Chrome’s new encrypted DNS lookup now conflict?
There is another way to get encrypted DNS in Chrome that has nothing to do with DNS servers used by the operating system. You can specify a long parameter string when starting the browser. The string starts with “‑‑enable-features=”DnsOverHttps … ”
I have samples of using this parameter to configure Chrome to use encrypted DNS with OpenDNS, Cloudflare and NextDNS on my website
DefensiveComputingChecklist.com in the Encrypted DNS section
This is an erosion of privacy overall, glad i am not the only one who thinks this.
Iron Heart: Well, it definitely has some serious privacy downfalls if you use Google’s DNS provider (I don’t know if Chrome does or is planning to do that, though it wouldn’t surprise me), or Cloudflare like Firefox defaults to, or your ISP’s DNS, since pretty much all ISPs are anti-privacy these days. So don’t do that. There are a ton of other DNS resolvers that support DoH. Pick one that has stated policies you like, here’s a big list of them:
https://github.com/curl/curl/wiki/DNS-over-HTTPS
Take away the “it all goes to a big US tech company” centralization argument by choosing a different DNS server, and I’m not sure what the article you linked to is complaining about. Yes, whatever recursive resolver you use can see your queries. That’s the case with unencrypted DNS, too. Yes, it’s not perfect, because of leaks like SNI. It’s better than it was, and letting the perfect be the enemy of the good is definitely what we want.
Side note, since some people here might find it useful: If you want DoH because you want ESNI (Firefox refuses to do ESNI unless it can do its own DoH. I don’t know what Chrome does but I wouldn’t be surprised if it had the same limitation) but you are also attached to the idea of having your own DNS server on your local network, say because you want local control over DNS filtering, you can run a local server. Most DoH software is focused on accepting unencrypted queries and resolving them using a DoH upstream server, but some will act as a DoH server themselves. I used dnss (https://github.com/albertito/dnss, its in Debian’s repos) which will do TLS termination. Of course Lets Encrypt won’t work on an RFC1918 network with no public domain name, but the PKI/CA model being brain-damaged is hardly new. You’ll have to arrange for your browser to trust a self-signed cert (or local CA) that you tell dnss to use. Then set up whatever other DNS resolver you like on that machine (I used Unbound doing DoT, you can also use DNSCrypt if you prefer) and set it as the server’s default way of doing DNS resolution.
@Door,
> “Yes, whatever recursive resolver you use can see your queries.”
There is a solution for that, works with DNSCrypt-proxy with DNS servers supporting the DnsCrypt protocol, it’s called Anonymized DNS [https://github.com/DNSCrypt/dnscrypt-proxy/wiki/Anonymized-DNS] …
“DNS encryption was a huge step towards making DNS more secure, preventing intermediaries from recording and tampering with DNS traffic.
However, one still has to trust non-logging DNS servers for actually doing what they pretend to do. They obviously see the decrypted traffic, but also client IP addresses.
In order to prevent this, using DNS over Tor or over proxies (HTTP, SOCKS) has become quite common. However, this is slow and unreliable as these mechanisms were not designed to relay DNS traffic.
Anonymized DNS prevents servers from learning anything about client IP addresses, by using intermediate relays dedicated to forwarding encrypted DNS data.”
DoH implemented in browsers, now within an OS itself (Win10) is a scandal and again illustrates the crooks’ method which is to provide security at the cost of privacy. There are alternatives, worthy, honest such as DNSCrypt.
personally i’m using DOH on my synology router like that all my system is protected by it in one go, do dns in each software is heresy
Chromium 83/85, no DoH is used in its default configuration. It uses my system’s resolver, as it should.
Mozilla: adds dns for third party
Yulva: Spyware! Burn them!
Google: adds dns for their own servers
Yulya: Everybody does this, change settings bro.
Same here
I don’t have the dns-over-https flag, neither i have the “Use secure DNS” setting in Chrome 83 stable.
Why’s that?
Maybe that is also being rolled out gradually, not sure!
Run `/Applications/Chromium.app/Contents/MacOS/Chromium –enable-features=”DnsOverHttps –force-fieldtrials=”DoHTrial/Group1″ –force-fieldtrial-params=”DoHTrial.Group1:ShowUi/true”`
This is very bad. Read this insightful article:
https://blog.powerdns.com/2019/09/25/centralised-doh-is-bad-for-privacy-in-2019-and-beyond/
All themcompanies hostile to privacy are implementing DoH as it stands (Google, Microsoft, Mozilla). Makes one think, doesn‘t it?
To all those who claim that this is great for privacy in the following: You have understood nothing.
It isn’t bad for privacy as it isn’t centralized. At worst it’s the same deal people have right now. Firefox does allow you to choose the DoH provider and it isn’t limited by Cloudflare, which is ignore by the article. Chrome will also not use Google’s DNS service, it will instead use your current DNS provider and check if it supports DoH and use it, so there is again not centralization whatsoever, something that they advertised from day one and in this article but you still ignore it.
For some reason, there have been people that are eager to make promises for DoH and DoT that were never there.
It’s not bad if you don’t use any of these companies’ DNS servers. There are plenty of privacy focused servers that don’t belong to a data-sniffing company.
To make it ultra-short : I entirely agree.