Behave for Chrome and Firefox warns you of port scans and local attacks
Behave! is a new browser extension for Google Chrome and Mozilla Firefox that is designed to inform its users when sites misbehave by performing port scans or access private IP addresses. The extension may also work in other Chromium-based and Firefox-based browsers but I have not tested that.
Behave! should not be confused with the Firefox extension behind!, which we reviewed yesterday. The new extension reveals when sites scan local ports or access private IPs. We revealed in May 2020 that eBay and other major sites were running port scans on user systems as soon as the browser connected to these sites.
The sites checked ports used by local remote software and used for fraud detection as remote software may be used for that purpose. Users on the other hand voiced concern that the port scanning was unethical and an invasion of privacy.
The browser extension Behave! monitors web pages for certain activity, and informs the user if it notices it. One of the main features of the extension is that it detects port scanning and will reveal as much immediately.

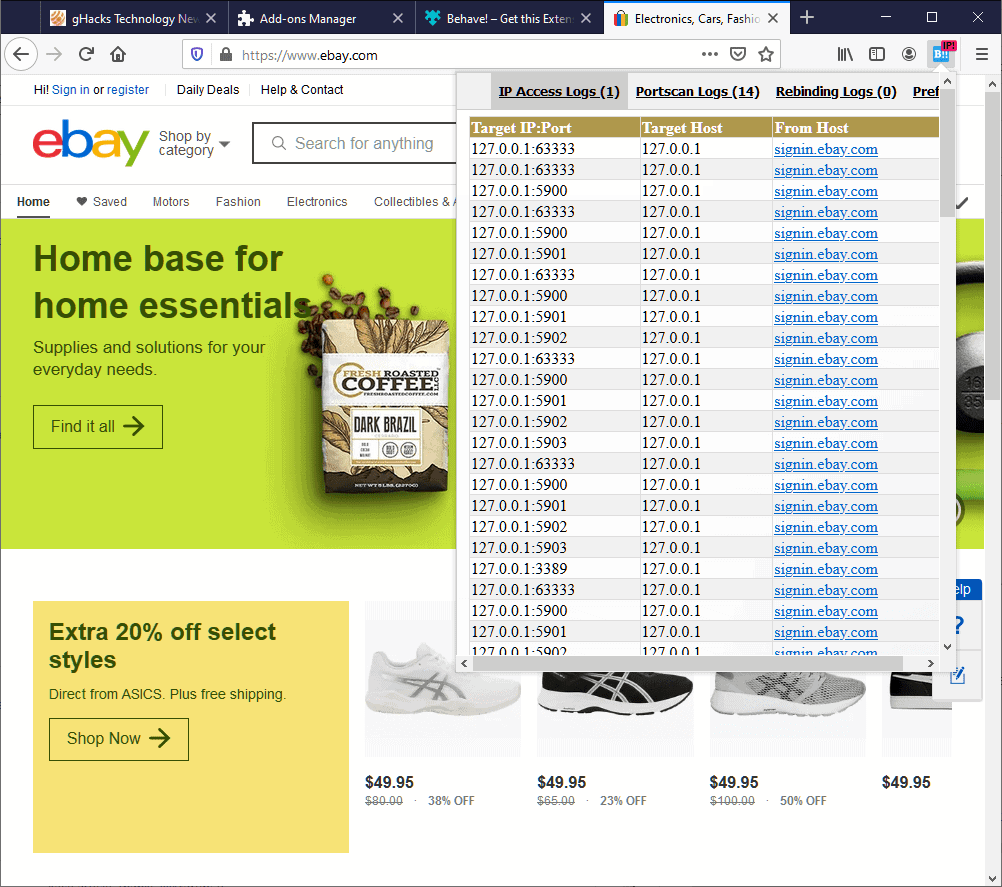
The extension adds an icon to the toolbar of the browser and changes the color of the icon based on its findings. A click on the icon displays information about the activity of sites in the browser sorted by method.
- For IP access, Behave! lists the target IP and port, target host, and the host the request originated from.
- For Port scans, it lists the port, host, and the from host.
- For Rebinding scans, it lists the hosts, IPs and from host.
Behave! detects browser based port scans, access to private IPs, and DNS rebinding attacks to private IPS.
The extension comes with a basic set of preferences that let you change the portscan threshold, enable or disable the monitoring, and to enable or disable Windows notifications.
The open source extension is developed by Stefano Di Paola, the co-founder and CTO of MindedSecurity.
Technically speaking, Behave! "will alert if a web page tries to directly access [...] an IP belonging to any of the following blocks":
- Loopback addresses IPv4 127.0.0.1/8
- Loopback addresses IPv6 ::1/128
- Private Networks IPv4 10.0.0.0/8 - 172.16.0.0/12 - 192.168.0.0/16
- Unique Local Addresses IPv6 fc00::/7
Closing Words
Behave! notifies users if sites misbehave or if DNS rebinding attacks are performed. The extension comes without any options to block the site behavior. The developer plans to introduce new features in future versions of the extension. Plans are underway to integrate a whitelist in the application and an option to "track back the code performing the suspicious activity".
Now You: Do you use security or privacy extensions in your browser? (via Bleeping Computer)
























thanks for the infooo
https://www.ghacks.net/2020/07/05/behave-for-chrome-and-firefox-warns-you-of-port-scans-and-local-attacks/
Vanilla Firefox or nothing.
To each their own: https://old.reddit.com/r/privacy/comments/blt6ft/mobile_firefox_app_shares_your_data_with/
You can block these types of scans in Firefox using a PAC file:
https://www.ctrl.blog/entry/block-localhost-port-scans.html
It won’t work in Chrome or Safari because you can no longer configure proxies for them specifically.
So you discover you are being scanned….then what.?..
if this cannot prevent it then i fail to see the point of it.
@Kubrick
Adblockers will usually block the scripts related to port scanning. For example, when eBay was caught port scanning recently, the script they used for that got blocked by the internal adblocker of Brave here.
> Do you use security or privacy extensions in your browser?
Seeing how everyone publishes their privacy configuration, I’ll also publish mine for those who are interested. I have posted it before here, I am expanding a bit on my prior explanations in the following.
1) The browser I use: Brave
The reason is that the Brave team has put a lot of effort into “ungoogling Chromium”, i.e. into removing or disabling all privacy-hostile functionality. More info here:
https://github.com/brave/brave-browser/wiki/Deviations-from-Chromium-(features-we-disable-or-remove)
In addition to removing Google spyware from Chromium, Brave has also sane privacy defaults on the code level already:
– Several APIs that can be used for fingerprinting are disabled out of the box.
– Prefetching and ping attribute are disabled ootb.
– Sane cookie lifetime policy.
– Sane referrer header policy. etc.
2) My settings within Brave:
– All adblock lists enabled (hamburger menu at the right side of the screen, “Brave adblocker”)
In Brave’s settings menu…
– “Show Brave suggested sites in autocomplete suggestions.” – Disabled (this is the default now, do not change it)
– “Block cross-site trackers” – Enabled.
– HTTPS Everywhere / HTTPS upgrades – Enabled.
– Javascript blocking – Disabled (Blocking Javascript in general is not useful and breaks too many websites, if you want to block it selectively, leave the Brave setting disabled and use an extension like uMatrix that allows for more granular control.)
– Cookies – Only block cross-site cookies (Blocking all cookies breaks too many things, especially login forms)
– Fingerprinting – Block cross-site fingerprinting (Blocking all fingerprinting breaks too many things, e.g. the eBay login form)
– Social Media Blocking (Facebook / Twitter / Google / Linkedin) – Disable them all, unless you use a Facebook / Twitter / Google / Linkedin account, in this case disable these settings only selectively and leave it enabled for the website where you have an account.
– Crypto Wallets / Hangouts / IPFS Companion / Media Router – Disabled.
– Tor Window – Enabled, note that Brave does not have the same fingerprint as other Tor users, therefore it is not a full Tor replacement, however, it works well enough if you just want to hide your IP address.
– WebTorrent – Disabled.
– Widevine – Disabled, unless you use a streaming service like Amazon Prime / Netflix / HBO etc. within the browser, in this case leave it enabled. Widevine is a DRM measure but also closed source, nobody knows what it does internally, therefore it should be deactivated, unless it is really needed – goes for all browsers, not just Brave.
– Search and URL autocomplete – Disabled.
– WebRTC IP Handling policy – Disable Non-proxied UDP – https://github.com/brave/brave-browser/wiki/WebRTC-Custom-Settings
– Brave telemetery / crash reports / remote debugging – Disabled.
– Push notifications – Disabled.
– Delete browsing data – Set this to delete cookies and cache upon closing the browser.
– Google SafeBrowsing – Disabled.
– Send “Do not track header” – Disabled, gets disrespected by most websites anyway and raises entropy, because you will stick out if you have it enabled.
– Allow sites to check for payment methods – Disabled.
3) Chromium flags I have set in Brave, along with the address you can use to access them:
– Reduce default ‘referer’ header granularity. – Enabled. – chrome://flags/#reduced-referrer-granularity
– Prefetch request properties are updated to be privacy-preserving – Enabled. – chrome://flags/#prefetch-privacy-changes
– Secure DNS lookups (DNS over HTTPS, DoH) – Disabled. – chrome://flags/#dns-over-https
My reason for disabling this you can find here: https://blog.powerdns.com/2019/09/25/centralised-doh-is-bad-for-privacy-in-2019-and-beyond/
4) Extensions I use in Brave, downloaded from the Chrome Web Store:
– Nano Adblocker (fork of uBlock Origin), I use it because of its default integration with Nano Defender, but you can run uBlock Origin with Nano Defender as well: https://jspenguin2017.github.io/uBlockProtector/
Even though Brave has its own adblocker included, using uBO / Nano Defender is still useful for adding additional filter lists and for custom element blocking.
– Nano Defender – conceals the presence of Nano Adblocker from websites that check for it “Please disable your adblocker etc.” – you all know it. In order to use it with Nano Adblocker, install the Nano Defender extension and then enable the Nano Defender blocklist within Nano Adblocker.
– LocalCDN (fork of Decentraleyes, more active now and supports more libraries), to block connections to content delivery networks.
– Cookie AutoDelete* – to get rid of cookies upon closing tabs, so that they do not stick around until the end of the session; also clears IndexedDB storage. This can, if used wrongly, break websites, and is generally far more likely to do so compared to the other extensions. Spend some time understanding its settings, this is my recommendation.
– ClearURLs – Supports a great many more rules compared to alternatives like Neat URL, I use ClearURLs to get rid of tracking parameters within URLs, to stop eTag tracking, and to get rid of tracking via the History API.
@Tom Hawack has mentioned more extensions, a quick overview on why I do not use some of his other suggestions, with explanations:
– CanvasBlocker – Useful in theory, but I do not want it to interfere with Brave’s own (likely more effective) anti-fingerprinting measures, which already cover that area: https://brave.com/whats-brave-done-for-my-privacy-lately-episode-4-fingerprinting-defenses-2-0/
– Clear Browsing Data – Not very useful, because Brave gets rid of cookies and cache upon closing anyway, and Cookie AutoDelete and ClearURLs (anti-eTag) are good enough to get the job done already.
– Cookie Quick Manager – I don’t want to know about the cookies installed, I want to get rid of them. Getting rid of all of them is the goal.
– CSS Exfil Protection – Useful in theory, but degrades performance, especially on YouTube.
– HTTPZ – This is already covered with the built-in HTTPS Everywhere of Brave. HTTPZ is based on the premise of trying to connect to https first, and then to fail if it isn’t available, and then to revert to http. I prefer a list-based approach over that for performance reasons.
– Privacy Possum – Not all that useful if you already run uBO / Nano Adblocker in medium mode.
– Privacy Redirect – One can use the original websites if the protections I mentioned are up and running, there is no point in being redirected to something else instead.
– Skip Redirect – Sounds useful, I’ll have a closer look at this one, but not a must have from what I can tell on first glance.
In general, running more browser extensions will make you fingerprintable and defeat your anti-fingerprinting mechanisms if you are unlucky, a “less is more” approach should be followed here. I hope these explanations and my own setup are useful to the community here.
Remove Nano Adblocker right now.
https://www.ghacks.net/2020/10/16/time-to-remove-nano-adblocker-and-defender-from-your-browsers-except-firefox/
IMPORTANT UPDATE OCTOBER 16th, 2020:
The original developer has sold Nano Defender / Nano Adblocker, as he announced in this GitHub issue:
https://github.com/NanoAdblocker/NanoCore/issues/362
As it turns out, and this is very regrettable indeed, new versions of Nano Adblocker and Nano Defender published after the sale collect personal data and send them to a remote server. Therefore, those extensions must be considered spyware, and I can no longer recommend them from this day forward! I URGE ANYONE STILL USING NANO ADBLOCKER AND / OR NANO DEFENDER TO UNINSTALL THEM AND TO REPLACE THEM WITH UBLOCK ORIGIN!
gHacks doesn’t allow editing comments once they are posted, otherwise I would have edited my original comment as well to reflect the new circumstances. Thank you for your attention.
Great stuff, thank you my Brave Iron Heart! :)
Just a heads up, one of the most important flags in Brave for Linux users is this one:
chrome://flags/#ignore-gpu-blacklist
Enable it, install h264ify extension and you’ll have GPU acceleration.
@hwa
That’s great, I already use h264ify in my Brave setup on my Mac (it prevents CPU spikes caused by VP8 / VP9 there). I am considering a Linux setup to replace my Windows 8.1 setup soonish, so I will keep this and the flag in mind for sure. :)
h264ify is one the two essential YouTube extensions for me, the other is Enhancer for YouTube:
https://chrome.google.com/webstore/detail/enhancer-for-youtube/ponfpcnoihfmfllpaingbgckeeldkhle
Reasons:
– I hate autoplay.
– But I love theming.
– Some YouTube videos are too quiet, this has a loudness booster.
– Predefined resolutions.
– Infinite loop.
@Iron Heart
Or you can just use invidio.us instead of YouTube, an open source and privacy respecting YT font-end. Check out NewPipe for Android, too. :)
Look, you are a man who values privacy and I admire that. Tho Linux is not perfect (nothing really is!) it’s much, MUCH better than Windows (it has become a privacy nightmare). So your switching from Windows to Linux is definitely a step in the right direction.
If your mind is not set up on any particular distro, Kubuntu might be a good place to start.
@hwa,
Invidio is shutting down tomorrow, but will continue to operate until October 1 according to the notice on their site:
https://omar.yt/posts/stepping-away-from-open-source
@ Martin,
I’m getting a warning that I’m posting too quickly even though this particular post is the first one today!
@hwa
I am aware of invidio.us, but do not like its interface. Plus, Enhancer for YouTube works so nice that I don’t want to abandon the YouTube website. I realize that YouTube is tracking-heavy, but the setup I mentioned above is apparently enough to fend off Google’s tracking: When I close a YouTube tab, and then return to the YouTube homepage in another tab, the content of the homepage has nothing to do with my interests. So I guess that what I am doing is effective enough for now.
As for my (potential) switch to Linux, this needs to be planned out well in advance. Since I will still rely on some Windows applications, very good virtualization is a must have. Wine and probably VirtualBox are therefore out – I’d prefer running VMWare, which would pretty much limit me to Fedora. I know that VMWare is closed source, but then, I am not an open source zealot by any means. The reason why I wouldn’t want Windows 10 is privacy, mainly. Windows 10 is an absolute nightmare in that regard, so Linux (with virtualization) would be the logical outcome.
Dear Iron Heart,
Thank you for such excellent information. Worthy and technical input from users like yourself makes this site one of the best for geeks.
@Heydrich
Thank you, much appreciated. That being said, this is just my browser configuration – there are many more things that can be done! For example, one can use a more privacy-respecting search engine by default (e.g. DuckDuckGo, StartPage, Qwant). Another thing that can be recommended is to set up a Pi-Hole in your network, that protects all of your home devices.
One can also strive to improve the privacy of one’s operating system (e.g. ShutUp10, or switching to Linux if feasible), using a trustworthy E-Mail provider is also a good idea (ProtonMail, Tutanota and others)…
But going into things like that would require a much larger comment, and personally I do not want to tell people to use another OS / E-Mail provider / search engine, because I realize that switching those can be much more problematic to people than hardening their browser. Improving the privacy of the browser, where most of your information is processed, is the first and most important step.
The description of Iron Heart is essentially correct.
For “Firefox”, refer to the following:
Firefox Privacy Guide | privacytoolsIO
https://old.reddit.com/r/privacytoolsIO/comments/d3of43/firefox_privacy_guide/
How Tracking Protection works in Firefox
https://feeding.cloud.geek.nz/posts/how-tracking-protection-works-in-firefox/
Tweaking Cookies For Privacy in Firefox
https://feeding.cloud.geek.nz/posts/tweaking-cookies-for-privacy-in-firefox/
Tweaking Referrers For Privacy in Firefox
https://feeding.cloud.geek.nz/posts/tweaking-referrer-for-privacy-in-firefox/
user.js — Firefox configuration hardening | GitHub – pyllyukko
https://github.com/pyllyukko/user.js/
As reference information:
EFF Report Exposes, Explains Big Tech’s Personal Data Trackers Lurking on Social Media, Websites, and Apps | Electronic Frontier Foundation
https://www.eff.org/press/releases/eff-report-exposes-explains-big-techs-personal-data-trackers-lurk-social-media
What is my Referer?
https://www.whatismyreferer.com/
I doubt that that add-on is necessary. Rather add this list to uBlock Origin:
https://raw.githubusercontent.com/gwarser/filter-lists/master/lan-block.txt
I found a way to clear the logs. I started NordVPN, and went to eBay. Behave!! shows no logs for eBay. I like NordVPN even more!
Why do the browser allow portscanning in the first place? What legit features is that used for?
Behave! (with “yourself” would remind me my childhood!) is the right extension for a non-imaginary problematic. I tried it but as always such extensions lack examples : I visited numerous sites for which I had a doubt and found none. I know… until the day I find one.
Browser privacy extensions? Those which are strictly privacy related :
CanvasBlocker (fingerprinting)
Clear Browsing Data (once in a session’s while)
ClearURLs (clears as it cleans indiscreet urls)
Cookie AutoDelete (clears cookies & localStorage when exiting a site unless this site is set to “allow”)
Cookie Quick Manager (to view the cookies actually installed, mainly.)
CSS Exfil Protection (CSS may be powerful, it’s not the docile script one can imagine compared to JS)
HTTPZ (because ‘HTTPS Everywhere’, given more & more sites are secured, isn’t any longer my choice)
LocalCDN (fork of ‘Decentraleyes’, enhanced, regularly updated)
Privacy Possum (discreet body guard, fights like a warrior, lives as a monk)
Privacy Redirect (redirects YouTube videos, Twitter and Instagram to dedicated alternative instances)
Skip Redirect (NY to LA directly without transiting to Rio)
uBlock Origin (summit of the pyramid)
I guess that’s about it for privacy & security at the browser level.
Hello Tom Hawack,
What do you think about this addon – Don’t touch my tabs! (rel=noopener) ? Do you know if it is handled by some other extension you listed ?
To add that its always a pleasure to read your well educated comments.
Hello @DuMuT6p, I do know that ‘rel=noopener’ is handled by the CanvasBlocker extension in :
Settings / APIs / Window API / Protect API features / ‘opener’ (as well as ‘name’ by the way).
Without CanvasBlocker I think the ‘Don’t touch my tabs!’ extension does the job, but only that job. CanvasBlocker is far more than a simple Canvas … blocker.
> Don’t touch my tabs! (rel=noopener)
> CanvasBlocker
I used to use “Canvas Blocker” before, but from the viewpoint of fingerprint (to match a large number of user bases), I’m using “about:config” as a base and fine-tuned with “Chameleon” without using add-ons.
As the auxiliary, “Don’t touch my tabs! (rel=noopener)” is used.
Chameleon: A WebExtension port of Random Agent Spoofer | GitHub – sereneblue
https://github.com/sereneblue/chameleon
Chameleon | About
https://sereneblue.github.io/chameleon/about
Chameleon | Wiki
https://sereneblue.github.io/chameleon/wiki
As reference information:
Browser Fingerprint – Is your browser configuration unique? | PrivacyTools
https://www.privacytools.io/browsers/#fingerprint
Browser Fingerprinting (Explanation, Tests, and Solutions) | Restoreprivacy.com
https://restoreprivacy.com/browser-fingerprinting/
View my browser fingerprint | AmIUnique
https://amiunique.org/
Surveillance Self-Defense | Tips, Tools and How-tos for Safer Online Communications | EFF
(Electronic Frontier Foundation)
https://ssd.eff.org/en
I’m having portscan logs at DDG and bleeping, can you check if you have the same results?
FF ESR, canvasblocker+uBO+uM, first party whitelisted, ESET Internet Security (should have blocked port scanning).
Thanks Martin for the useful tip!
@SpywareFan, I’ve just re-installed Behave! for the sake of checking here what you’ve experienced :
Behave! 0.9.6, monitoring is ON / Firefox 78.0.1 (x64) / Windows 7 (x64)
bleepingcomputer.com : no logs, the site being or not whitelisted on ‘uBlock Origin’
duckduckgo.com : no logs, the site being or not whitelisted on ‘uBlock Origin’
The reason I encounter no logs contrarily to you may likely be due to another of my above mentioned privacy related FF extensions, unless it be the effect of an OS-wide defense. I have no idea at this time.
Maybe FF ESR? I’m running latest 78.0.1
Probably it’s a module of ESET (maybe tls scanning) that causes my behaviour since I have logs for every website I visit, but only with those mentioned here https://github.com/mindedsecurity/behave I have alerts.
Better if I review all my configs before causing issues to those I help!
Thanks.
@SpywareFan, there’s a lot of technical stuff far beyond my knowledge, I’m not a specialist, maybe someone like ‘Iron Heart’ could answer. I don’t advise, suggest anything because I lack technical arguments, my approach is pragmatical only, I read quite a lot users’ experiences and specialists’ advice, compare, test myself, always backup before, and there we go, step by step. I manage that way, experience is an ignorant man’s friend but becomes his enemy if he extrapolates from what he’s encountered to establish general theories which require a global knowledge, at least, as a basis, even if knowledge may lead to excessive confidence and lack of modesty. No need to say I’m excessively modest :=) I just share what I’ve experienced, period.
Every fricken FF extension I have is for security and privacy.
I like the sound of this one though, simple and informative. Think I’ll check it out.
Just needs the ability to whitelist, hosts blockers and router hosts based ad blockers cause the addon to overload with false positives and clutters the logs
At first glance, it seemed “useful”.
For now, I’ll implement it and trying it.
usage environment:
NordVPN: Obfuscated Servers (OpenVPN)
W10Privacy https://www.w10privacy.de/english-home/instructions-1/
simplewall https://www.henrypp.org/product/simplewall
Windows 10 (x64) Version 1903 (build 18362.900)
Firefox 68.10.0esr (64-bit)
Now You: Do you use security or privacy extensions in your browser?
API-Killer-IndexedDB, Chameleon, ClearURLs, Cookie AutoDelete, Cookie Quick Manager, Decentraleyes, DuckDuckGo Privacy Essentials, Flagfox, Hide Private Mode, HTTPS Everywhere, IndicateTLS, Invidition, IP Address and Domain Information, NoScript, Privacy Badger, Redirect AMP to HTML.
As reference information:
Firefox Privacy Guide | privacytoolsIO
https://old.reddit.com/r/privacytoolsIO/comments/d3of43/firefox_privacy_guide/
How Tracking Protection works in Firefox
https://feeding.cloud.geek.nz/posts/how-tracking-protection-works-in-firefox/
Tweaking Cookies For Privacy in Firefox
https://feeding.cloud.geek.nz/posts/tweaking-cookies-for-privacy-in-firefox/
Tweaking Referrers For Privacy in Firefox
https://feeding.cloud.geek.nz/posts/tweaking-referrer-for-privacy-in-firefox/
user.js — Firefox configuration hardening | GitHub – pyllyukko
https://github.com/pyllyukko/user.js/
I have been using NordVPN for almost a year. It works very well. I wish I could find a way to clear the logs in Behave!! ….. That would make it easier to see if NordVPN is helping with this intrusion.
@owl:
Using both DuckDuckGo Privacy Essentials and HTTPS Everywhere is a bit pointless, as the DDG extension has integrated HTTPS-Everywhere’s functionality.
@owl
> Decentraleyes
Small hint on my part: Decentraleyes has been fairly inactive for quite some time now:
https://addons.mozilla.org/firefox/addon/decentraleyes/versions/
There is an open source fork of Decentraleyes called “LocalCDN” which is much more active now and supports more libraries:
https://addons.mozilla.org/de/firefox/addon/localcdn-fork-of-decentraleyes/versions/
It’s also available for Chromium-based browsers:
https://chrome.google.com/webstore/detail/localcdn/njdfdhgcmkocbgbhcioffdbicglldapd?hl=de
I highly recommend to replace Decentraleyes with it.
@Iron Heart: I don’t know if you get to read this, but I want to thank you mentioning LocalCDN. I discovered your post by accident. I have replaced Decentraleyes with LocalCDN.
Funny what you say about Decentraleyes. Recently I contacted the dev, Thomas Rientjes, to ask him banking details because I was prepared to make a donation. I received no answer. Oh well ……
@Klaas Vaak
No problem – and yes, LocalCDN is much more active than Decentraleyes, the latter seems to be more or less abandoned by now.
@Iron Heart,
LocalCDN requires FF63 minimum unfortunately so it won’t work with Waterfox Classic which the addon site identifies as FF57.
As regards the updating Decentraleyes which you mentioned I’m not so sure if the seemingly lack of updates is necessarily a problem. If you check the versions on the Moz addons site you’ll note that there was a gap of seven months between versions 2.0.13 and the current 2.0.14. It’s a similar story with previous versions. You can use the addon’s testing utility if you have any doubts: https://decentraleyes.org/test/
@TelV
Waterfox Classic lacks a number of WebExtension APIs of later Firefox / Waterfox versions, which is why it does not support some extensions.
Decentraleyes lacking updates – that means support for new libraries in this case – is a problem for an extension that is meant to provide those libraries locally. The number of libraries supported by LocalCDN is far greater than those supported by Decentraleyes at this point.
The test website you mentions uses the jQuery library, which gets inserted by LocalCDN / Decentraleyes, that way the testing website checks whether or not the extension works at all. LocalCDN inserts this library as well (just tested) and works – that’s not the issue, it becomes one only whenever you encounter a library that is not supported by Decentraleyes, yet supported by LocalCDN. LocalCDN has the edge with all libraries the developer has added in the last months.
But yeah, since you probably want to stick with Waterfox Classic (instead of Current), Decentraleyes is your only option anyway – but for all users of more recent codebases / browsers, LocalCDN is clearly better, due to more libraries being supported.
@Iron Heart,
> Decentraleyes
I have a regular job, at home I am simply in a “digital detox†lifestyle.
I’m not interested in SNS(Social networking service), neither YouTube nor Amazon.
At home, I only need to check for “E-mail incoming” and “RSS subscription”, so Thunderbird is sufficient.
Opportunity to use Browser (Firefox ESR) is a degree when posting to “GHacks Tech News” or when using “GitHub” or “Crowdin”.
So I didn’t have any problems with “Decentraleyes”, but let’s consider “Local CDN”.
Thanks for mentioning.
As a result of verification, I switched from “Decentraleyes†to “Local CDNâ€.
https://www.localcdn.org/
Thanks to enthusiastic advice of Iron Heart.
Windows security = machine turned off
Been running it in Firefox and works as advertised.
It also confirmed for me that reports of the EasyPrivacy list as being the simplest (again, simplest) way to protect from the scans are well founded. And by association, Fanboy’s Tracking List.
So, running Behave! will alert to the behavior for sites not yet in the lists.
For those sites, it would be useful for the extension to detail the offending behavior (hopefully that “track back the code”) so one might build a filter, as the ones I built for AdGuard, like
||src.ebay-us.com/fp/check.js$domain=signin.ebay.com
before I leaned of the EasyPrivacy “solution.”
For Behave!, I think a method to block the site behavior is beyond the scope of its mission.
Fantastic. Installed in Firefox. eBay seems to be not doing it at the moment.
It probably is. Click on the B!! icon > IP Access Logs
I use Privacy Badger, UBlock Origin. and Windows Security. Only Windows Shutdown seems to work effectively. :-(
â€Privacy Badger: Is easily detected and additional blocking via hueristics is redundant or negligible when using uBlock Origin (depending on your configuration)â€
https://github.com/ghacksuserjs/ghacks-user.js/wiki/4.1-Extensions
I have Privacy Badger, which works very well for other things, but not this. I freakin’ HATE people spying on me!!