Initial price of Firefox Private Network browser extension service announced
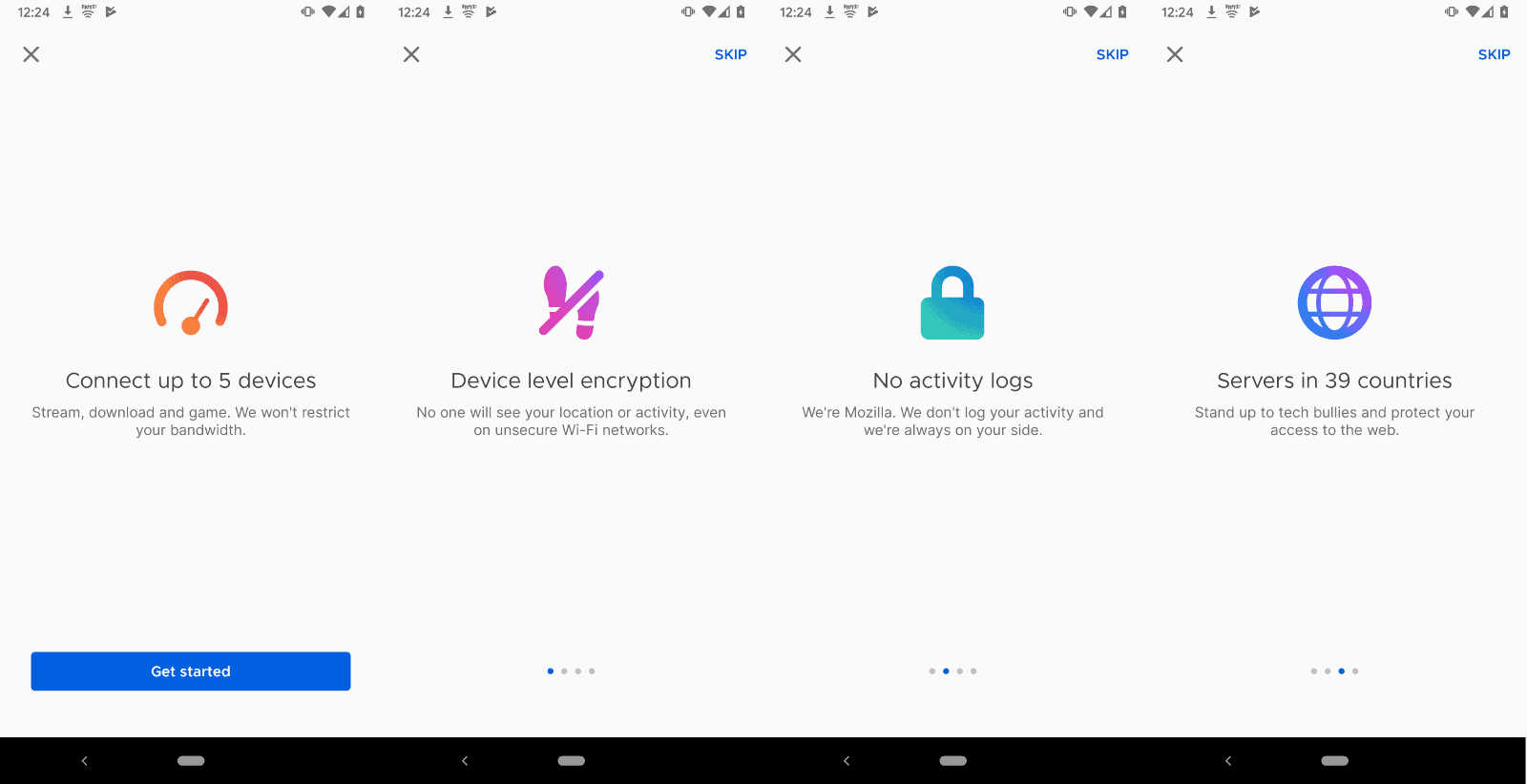
Mozilla unveiled Firefox Private Network back in September 2019 when it revived the Firefox Test Pilot program. The new program would focus on privacy products and one of the first things to come out of it was Firefox Private Network, a browser extension that tunneled traffic through a proxy.
In October 2019, Mozilla announced the upcoming launch of a companion VPN product that would move the protection from the browser level to the system level. The launch changed the unlimited nature of the Firefox Private Network browser extensions to a time-limited free service.
The product was launched in December to users from the United States for an introductory price of $4.99 per month.
Mozilla announced the next steps for the organization's Firefox Private Network extension beta yesterday on the official blog of the organization.
The organization plans to transition from the free beta of Firefox Private Network browser extension to a paid subscription beta. The initial price has been set to $2.99 per month and it is good for up to three browser instances of the Firefox web browser and does not limit traffic or the access time (in other words, it is unlimited).
Just like the initial version and the VPN, it is only available to users who reside in the United States initially. Mozilla promises that it will expand the beta service to other regions in the future but has not published a timeline or revealed an initial list of regions or countries.
Mozilla provides some insight into the decision making process. Firefox Private Network browser extension was launched with unlimited access initially but Mozilla switched that to a time-limited offering in December when it launched the VPN offering.
It learned that the unlimited offering was "more appealing" to users because of its set and forget nature; time-limited users seemed to forget to turn the proxy on or off regularly which impacted privacy.
What we learned very quickly was that the appeal of the proxy came most of all from the simplicity of the unlimited offering. Users of the unlimited version appreciated having set and forget privacy, while users of the limited version often didn’t remember to turn on the extension at opportune moments.
Time-limited users would use the proxy less and further research showed that they "often stopped using the proxy after only a few hours".
The introductory price was set after Mozilla conducted a "number of surveys". The organization wants to find out whether users will pay for a browser-based privacy tool. It wants to run a series of "small marketing tests" over the summer to find out about that and determine the interest in "the Firefox Private Network browser extension as both a standalone subscription product and as well as part of a larger privacy and security bundle for Firefox".
New users (from the supported region) and time-limited users will get a chance to join the subscription first. Unlimited users will be asked to migrate to the paid offering as well (which in turn seems to indicate that the free unlimited ride will be over at that point).
Closing Words
It will be interesting to see if users are willed to pay $2.99 per month for a browser proxy. Considering that good VPN services are available for less sometimes, it is probably going to be a hard sell to users who know about these offers.
The main appeal is probably that it is integrated into Firefox directly and that it is a set and forget affair because of that. Some users may also trust Mozilla more than VPN companies, and users who don't know about cheaper offers may also find the offer appealing.
Now You: Does the offer appeal to you?





















FYI : Mozilla will end support for Firefox Private Network on June 20th, 2023
[https://support.mozilla.org/en-US/kb/firefox-private-network-no-longer-available]
Yeah well apps and store apps need a way to privately get a way into your account if you have two step authentication or use passworldless to recover your information or update your phone or email or street address from within the app itself away from your email account you would use for general things as it would be p2p encrypted and only used to recover migrate or change your personal info and payment on your account without needing to talk to a person on the phone or an automated voice and then listening to elevator music for hours before they just fix it for you.
This isn’t just for movies cable tv from comcast and gaming its also for banking and other accounts here too like amazon and Costco..
Couldn’t agree with you more Benjamin :)
If I donated or bought everything being offered to me on the internet I would have to live to be a million+ years old to be able to pay it off and still have nothing real or physical to show for it.
What is it? Seems like a “privacy” proxy similar to what Brave uses. I thought their VPN was a browser extension, did it become a standalone? FF already has Private Browsing Mode, why do need this? Isn’t uBlock Origin still OK? My head hurts :)
IDK how much FF makes selling browsing data and ads per user who may bite at this but I’d bet it’s more than $3 per month.
Mozilla’s yet again going to try something on a test group to see if anyone likes it? Price it too high and push it with their garish, scattered, hard to read What’s New screens that we close as fast as possible?
Yeah, OK, whatever.
The real dangers for all our privacy begins where the network as we understand it ends. Inside the totally unregulated private networks of organisations, corporations and what more.
Coporations and Organisations of which the Mozilla is just one of many thousands speak of privacy and protection while they steal the very data that comes out of our lifes.
It is todays neoliberal criminal energy which allows the outright theft of everything that is unprotected. Rights for our data are such a category… unregulated, liberalised, free for taking, selfservice.
The whole concept of today’s internet is based on such criminal unregulated unprotected areas long since taken over by large shareholder driven for profit corporations and corrupted politics.
There is as of today no public open transparent internet.
The goal is to keep your data from many to make it more valuable to one.
If it deals with fingerprinting I would be interested. Otherwise I’ll pass. Firefox says it blocks fingerprinting but it does not. See https://panopticlick.eff.org/
@NetCentric
Brave is currently coming up with a new and unique approach to fingerprinting, based on randomization:
——
“The most common defense is to try and make different browsers look as similar as possible, by having all versions of the browser report the same value for different fingerprinting data points. In some cases, this is by removing fingerprintable values where possible (Brave, for example, by default removes the canvas and WebGL APIs from third parties). Other tools try to protect against fingerprinting by having all versions of the browser report similar value (Safari for example reduces differences between its browsers by limiting which fonts web sites can access).
Another approach to limit fingerprinting is to only allow sites to access certain features after the user has explicitly given permission (Firefox in “resist fingerprinting†mode, and the Tor Browser Bundle, both require permission for sites to access canvas).
The unfortunate truth about all these approaches is that, despite being well intentioned, none of them are very effective in preventing fingerprinting. The enormous diversity of fingerprinting surface in modern browsers makes these “blockâ€, “lie†or “permission†approaches somewhere between insufficient and useless, unfortunately.
Starting in Brave Nightly now, Brave is deploying a new type of fingerprinting defense that we expect will be uniquely effective. Instead of removing or modifying browser differences, or adding troublesome permission prompts, the Brave browser will start adding subtle randomization to some fingerprinting endpoints. This privacy-through-randomization approach has been studied by privacy-focused computer scientists, most recently in the PriVaricator (Nikiforakis et al, WWW 2015) and FPRandom (Laperdrix et al, ESSoS 2017) projects. This is the first time those approaches are implemented in a mainstream browser.
This approach is fundamentally different from existing fingerprinting defense approaches; current approaches attempt to make all browsers look identical to websites (an impossible goal). Brave’s new approach aims to make every browser look completely unique, both between websites and between browsing sessions. By making your browser constantly appear different when browsing, websites are unable to link your browsing behavior, and are thus unable to track you on the Web.”
source and more info here: https://brave.com/whats-brave-done-for-my-privacy-lately-episode3/
——
I think that deserves a closer look, and without exaggeration, Brave is really on the forefront when it comes to fighting fingerprinting. Needless to say, these capabilities are unique among Chromium-based browsers, e.g. Ungoogled Chromium can’t do it even though it’s an otherwise fine browser. Do note though that fingerprinting randomization has not rolled out to the stable channel yet, but I expect it to arrive within the next three months.
> Brave is currently coming up with a new and unique approach to fingerprinting, based on randomization
This is not new. This is not unique. Tor Browser’s RFP has used randomization since at least FF57, and the concept has been around for much longer. There are many ways to combat fingerprinting, of which lowering entropy and raising entropy (constantly randomizing) are but two. They both have pros and cons, and it really depends on what metric is being protected (e.g. it makes no sense to randomize user agents, but it might for canvas or audio or textmetrics etc)
In canvas, randomizing vs faking a static result are both easily detectable (even if you randomize per domain so multiple passes return the same random value). You cannot hide that a known canvas result is tampered with. It is trivial to detect. So the end result technically is the same. e.g. RFP (in FF77 or lower: in FF78+ it randomizes some Canvas APIs and spoofs the rest as static) returns a static white canvas, and Brave with it’s protection returns a static “hey I’m random” (assuming the script decides to test that).
What you’re talking about is a “poison pill”, and that concept has been around for at least a decade in browser FPing. And poison pills are great, so “dumb” scripts swallow them. But Brave hasn’t invented or implemented anything new here.
> despite being well intentioned, none of them are very effective in preventing fingerprinting
Rubbish. As already mentioned, there are more than two ways to combat a metric being FPed. You can block known scripts, you can use heuristics, you can disable an API (reduce the attack surface), you can lie with a set value (lower all users to the same), you can lie in “buckets” based on some other metric such as the OS (this still lowers entropy but can eliminate information paradoxes which can also cause breakage), you can randomize per bucket, you can randomize (either per domain session or on every pass)
Let’s examine one item. RFP spoofs everyone’s timezone as UTC 0. Everyone has the same timezone. Therefore, in the set of all TB users (or all RFP users on Firefox), this metric becomes totally useless. It has zero entropy. And yet you call that ineffective? TB is not trying to hide that’s it TB (that’s impossible), so randomizing is completely unnecessary.
Let’s examine one more: Canvas. RFP canvas is always returned as the same result for all users. Therefore the entropy is zero in the set of all TB or RFP users on this metric.
Randomizing generally increases complexity and can have side effects. For example the complexity of caching randomized results per domain (or eTLD+1), or per tab, or per session. Side effects can cause information paradoxes which affect feature detection which can cause breakage.
Again, it comes down to what is appropriate to randomize or not, or if it’s even worth randomizing. That doesn’t negate it’s effectiveness.
> Brave is really on the forefront when it comes to fighting fingerprinting
No it’s not. Look, I applaud all and any efforts to defeat fingerprinting, but Brave doesn’t even come close to what Tor Browser does or what Firefox can currently do with RFP and a couple of other changes (such as using the already built in font whitelisting pref)
For the record: I’ve been interested in fingerprinting for over a decade, I’ve been involved with Tor Uplift and Mozilla, I’ve been to Mozilla All-Hands specifically for fingerprinting and Tor Browser (pretty sure they didn’t need me, but they recognized my work/contributions: 99% of which is behind the scenes). I’ve read hundreds of academic reports, theses, PhDs, and more over the years. I’ve tested thousands of PoCs. And I have followed all of Brave’s FPing measures. Take from that what you will, but what you claim here is just flat out marketing BS.
I guess they only check within their database..? Anyway, the whole “fingerprinting” and “having a common fingerprint” nonsense is a lost cause. Font rendering can differ from one graphics driver to another, on the same machine with no hardware changes. More *worrying is that I’ve seen the AA take different shades of blue/amber after a GPU driver crash, after a log off/on or restart.
* On the bright side this means this cannot be used against you for tracking purposes, since it’s so inconsistent and unreliable. At least not for long periods of time. But it also means a common fingerprint is nearly impossible, even for something like TBB.
@NetCentric.
It reduces the fingerprint and if you had no fingerprint then you would never be able to connect to the web.
I would ignore panopticlick as that is just a scareware site to induce you to install their extensions.
The “Fingerprinters” blocking in ETP (Enhanced Tracking Protection) is a blacklist: it blocks some known fingerprinting scripts, but by it’s very nature, it can never catch them all. Also, it wouldn’t make much sense blocking a test site’s script, since that’s what you want to actually test
“Fingerprinting” though, is the attempt of JS APIs/CSS and other methods to extract the information: and that’s a hidden feature called RFP (resistFingerprinting) as part of the Tor Uplift: there are a couple of slight differences between Tor Browser and Firefox, and by all means it is not complete: it never will be
The new color palette by Mozilla where each icon has a 2-color gradient is making me nauseous for some reason, just like Brave browser’s purple/orange gradient palette. I can’t explain it, but it makes me feel like I’m suffocating and wanting to vomit.
It’s not appealing at all.
Agreed 100% – same as Brave which makes me even more nauseous.
Instagram designers did those logos. . .
@The Equestrian with those symptoms you might want to get checked by a docor.
@Malte
Nah, I’m just allergic to SJW stuff. xD
That’s literally what these designs scream and they are inspired to promote that, not to look good and professional. I hate giving credit to Microsoft these days, but thew new icons they are giving to their UWP apps after they discovered people hated the flat 2-color designs are exactly how they should be – pleasing and looking professional at the same time.
Here you can see what I’m talking about as well as the Instagram icon sitting among them looking like a pus-filled blister or a barf puddle:
https://news-cdn.softpedia.com/images/fitted/620×348/more-new-fluent-design-icons-coming-to-windows-10-527268.jpg
@The Equestrian
Don’t worry, those “SJW icons” won’t turn you gay.
They want to diversify their revenue streams, in order to reduce their strong dependency on Google. Let’s see how it goes, personally I don’t think that this will generate any amount of income worth writing home about.