MDS Tool: find out if you are vulnerable to Microarchitectural Data Sampling Attacks (MDS)
MDS Tool is a free cross-platform security program for Windows and Linux devices that checks whether the system's hardware is vulnerable to Microarchitectural Data Sampling (MDS) attacks.
Intel disclosed a new group of security issues in its processors on May 14, 2019 that it calls "Microarchitectural Data Sampling". The flaws are related to speculative execution attacks such as Spectre or Meltdown discovered last year. The issue affects all modern Intel CPUs in servers, desktops, and laptops.
Rogue In-Flight Data Load (RIDL) and Fallout, two MDS attacks, differ from last year's attacks in several meaningful ways that make them potentially more powerful. The attacks don't depend on the processor cache and don't need to make assumptions about the memory layout. They leak arbitrary in-flight data from internal CPU buffers.
Attacks, when carried out successfully, read data from other system processes and could lead to the leaking of sensitive information such as passwords, credit card numbers, or cookies.
Attackers who can run unprivileged code on machines with recent Intel CPUs - whether using shared cloud computing resources, or using JavaScript on a malicious website or advertisement - can steal data from other programs running on the same machine, across any security boundary: other applications, the operating system kernel, other VMs (e.g., in the cloud), or even secure (SGX) enclaves. (via)
Microsoft released patches for some versions of Windows on yesterday's Patch Tuesday, Canonical released updates for Ubuntu yesterday as well.
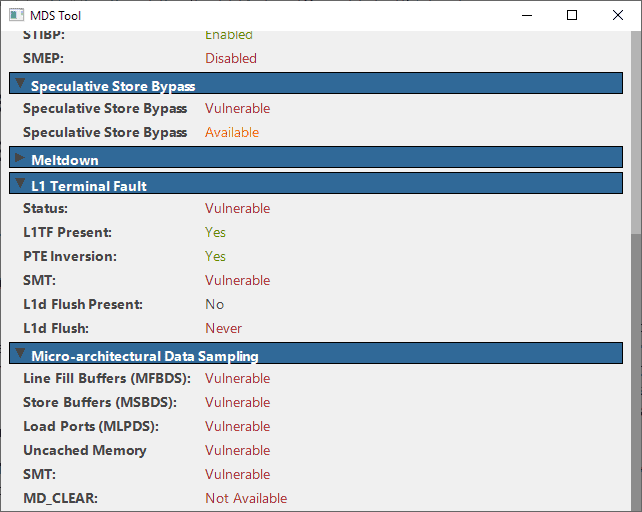
MDS Tool
MDS Tool is a comprehensive program that you may run on your system to find out if it is vulnerable to certain attacks. You can download the program from the MSD Attacks website.
It has been updated recently to integrate vulnerability checks for the disclosed MSD attacks. Just run the program after download and scroll down to the Micro-architectural Data Sampling section of the interface.
There you find whether the system you ran the software program on is vulnerable to the attacks or if it is protected.
If you have not installed patches yet that mitigate the issues, it will report as vulnerable.
Resources
Here is a list of resources that offer additional information:
- Chromium Security -- About Microarchitectural Data Sampling and responses
- Intel Security -- Deep Dive: Intel Analysis of Microarchitectural Data Sampling
- Intel Software Guidance -- Microarchitectural Data Sampling
- MDS Attacks -- Informational site
- Microsoft Windows Clients -- Informational site
- Microsoft Windows Servers -- Informational site
- Ubuntu -- updates to mitigate MDS


















just my i7 9750H ; powned !!!
Win10 hardening PRO x64 1909 up to date + bios and intel plateforme management backdoor up todate
Quoting from venturebeat: …….
“In a just-published support document, Apple suggests that full ZombieLoad mitigation will require Intel chip users to disable Intel’s hyper-threading processing feature — a major selling point of the chipmaker’s CPUs. During testing this month, Apple says that it found “as much as a 40 percent reduction in performance with tests that include multithreaded workloads and public benchmarks,†though actual performance impacts will vary between machines.”
https://www.phoronix.com/scan.php?page=news_item&px=MDS-Zombieload-Initial-Impact – MDS / Zombieload Mitigations Come At A Real Cost, Even If Keeping Hyper Threading On – Written by Michael Larabel in Linux Security on 16 May 2019
No need to disable hyper-threading. It’s just a last resort for folks who have no clue how to properly run a hypervisor box.
The only hackers capable of exploiting such attacks are government agencies and their contractors (see the most recent case of the Israeli government front company NSO Group hacking Whatsapp). The average person is not a target and they have to spend considerable resources just to target someone in the first place. Maybe they will start using AI for attacks in the future, but all of it can be stopped if government cyberwarfare and espionage is banned globally.
Dutch researchers find a major vulnerability in Intel chips. Researchers at Amsterdam’s VU university have discovered a major leak in Intel microchips which make it possible to get hold of passwords and other sensitive information.
Englisch version
https://www.dutchnews.nl/news/2019/05/dutch-researchers-find-major-vulnerability-in-intel-chips/
Dutch version
https://www.nrc.nl/nieuws/2019/05/14/hackers-mikken-op-het-intel-hart-a3960208#/next/2019/05/15/#102
Now if only this said how to get MDS Tool.
Yes. Click the “MDS Attacks” link in the above article to get the MDS Tool.
Good point Mr. AnorKnee.
It would be the best to get the newest version because initial release had some problems (high CPU load by events polling, and wrong SSBD detection routine).
It must be just me, since for the life of me I can’t imagine why an article would exist talking about MDS Tool, but no information on how to even get it.
Woah, this interactive Guide in mdsattacks.com is really cool. I’ve never seen this before… now i checked my setup, a Microsoft Surface Tablet setup with Windows 10 Pro and latest official patch level made by the system.. and i am vulnerabel… i thought so. The people who are able to find this vulnerablities are geniuses themself… respect for that. I am sure there are more since the whole computer architecture is a purely private undertaking and not public.
These side-channel attack vulnerabilities will only enable very resourceful hackers to steal user-data, passwords, etc. Enterprises and other high-value targets should be patched asap, even though their computers may suffer a performance hit.
……. For home-users, it may be a different story, eg since the ‘Meltdown’ in Jan 2018, I do not think my unpatched computer with an Intel processor has been hacked.
Intel has stated that their new 8th-gen and 9th-gen processors are not vulnerable to all the side-channel attacks via Meltdown, Spectre, Zombieload, etc, because the mitigations have already been built-into the processors.
……. Problem is, the newer Intel 8th-gen Cannon Lake processors perform much worse that Intel 7th-gen Kabylake processors in benchmark tests. …
https://www.anandtech.com/show/13405/intel-10nm-cannon-lake-and-core-i3-8121u-deep-dive-review/7
Time to buy AMD.?
Are AMD processors still heaty or hot.?
No. Ryzen is great. When it first came out, it was a ****ing nightmare. But all the kinks have been ironed out now. I personally was one of the lucky ones who had to exchange CPUs with AMD because programs on Linux would randomly segfault. And then there was the problem where the system would spontaneously restart every couple of days without any warning! Both of which were widely documented problems, experienced by many more than just me.
But neither has been a problem now for over a year. And I am running my Ryzen 7 1700 overclocked at 3.6GHz on all cores. And it just works. It stays running all day and all night, recording TV, rendering and being a desktop.
“Intel has stated that their new 8th-gen and 9th-gen processors are not vulnerable to all the side-channel attacks via Meltdown, Spectre, Zombieload, etc, ”
Intel is lying. 8th-gen and 9th-gen processors are vulnerable. My 8th-gen i7-8850H looks like a holed Swiss cheese, littered with red ‘vulnerable’.
A recent Intel report said that it will take Intel 5+ years to come up with a new clean/secure CPU.
… https://www.zdnet.com/article/intel-cpus-impacted-by-new-zombieload-side-channel-attack/
@ ilev
Quoting from ZdNet: ……. “”Microarchitectural Data Sampling (MDS) is already addressed at the hardware level in many of our recent 8th and 9th Generation Intel Core processors, as well as the 2nd Generation Intel Xeon Scalable Processor Family,” Intel told ZDNet via email last week.”
….
Why relying on third-party gibberish? Intel provides resources and tables enumerating all CPUs; and except for a few old CPUs, all current CPUs are more or less affected. And it’s not just Intel CPUs that have such design flaws.
Exactly, pure lie to tabloit websites like ZDNET. Intel lists *ALL* of its CPUs as affected, 8th and 9th generation including. Doing a lot not to loose market to AMD are we?
Time to get rid of israeli spyware (IntelME) and other NSA holes in the CPUs…
https://www.intel.com/content/dam/www/public/us/en/documents/corporate-information/SA00233-microcode-update-guidance_05132019.pdf
@ Expert
Quoting from the comment section of https://www.phoronix.com/forums/forum/phoronix/latest-phoronix-articles/1099405-mds-zombieload-mitigations-come-at-a-real-cost-even-if-keeping-hyper-threading-on/page3 …….
“Only certain (very recent) steppings of the 8th and 9th gen CPUs have hardware mitigations for the MDS vulnerabilities. My brand new (under 1 month old) work laptop with an i7-8750H has an ‘A’ stepping CPU which is vulnerable, only the ‘C’ and ‘D’ steppings aren’t vulnerable. Cascade Lake has one stepping vulnerable to two variants of MDS and two newer steppings that aren’t vulnerable to any variants. ” …
https://software.intel.com/security-software-guidance/insights/deep-dive-cpuid-enumeration-and-architectural-msrs#MDS-CPUID
According to the tool i’m vulnerable to all attacks & my system is up-to-date. Meh…no risk, no fun because i’m not going to buy a new PC. On the other hand i use an adblocker and it blocks 3rd party scripts and ressources. That should keep me safe from malicious code on websites. So i guess the situation is not so bad after all.
Why wasting time with such tools when almost all Intel CPUs are affected? The whole side-channel attack hype is getting old and the talking heads from the academia still owe us a real-world exploit that gets the job done in seconds, not days, weeks, months, or years. If they don’t come up with something better soon, affected CPUs no longer exist and have been replaced by new CPUs. But thanks for sharing the fun.
These 2 guys seem to be Intel Reps.
My 8850U is vulnerable to 17 of the Attacks and Ridl only takes 4 seconds to leak your root pass. Great.
Sure, most processors are affected. These tools provide information on protections as well, and that is in my opinion important as it is easy to overlook something with all the patching going on.
Indeed, it is certainly important to high-risk targets, but the average user couldn’t care less. Furthermore, it’s next to impossible to mitigate this type of vulnerability and patches may introduce even more vulnerabilites. Even if such tools confirm that related patches are applied (that’s all what they do), it doesn’t guarantee security. Due to the nature of the vulnerablity, it’s a never-ending patching story and only new CPUs can solve the issue. However, it will take years until CPU makers can deliver.
This tool output is questionable. Latest Windows 10 patch on 1809, latest firmware (BIOS) for L1 Terminal Fault/Spectre and what-not, lists green yes in the main categories yet category header says = vulnerable almost everywhere.
I would expect to pass everything apart from MDS (there’s typo leading to the MDSAttack website Martin)
So without proper documentation what it does and what is check based on this is like running some kid’s toy to tell you its oppinion.
Microsoft’s PowerShell tool (https[://]github[.]com/Microsoft/SpeculationControl) might offer more insight.