VeraCrypt encryption software review
VeraCrypt is an encryption software that is a fork of the discontinued TrueCrypt encryption software. It can best be described as a continuation of TrueCrypt that supports all features that TrueCrypt supported plus a set of improved or new features.
Since it is based on the popular application it supports options to create encrypted containers, encrypt entire hard drives and to encrypt the system partition of the computer system. The popular option to create hidden encrypted volumes is supported as well.
VeraCrypt is an open source program that is available for Windows, Linux, Mac OS X and FreeBSD; developers and researchers can download the source code from the project website as well.
Note: The current version of VeraCrypt is 1.23. This review is based on VeraCrypt 1.23 for Windows but most of it applies to VeraCrypt for Linux and Mac Os X as well.
VeraCrypt installation
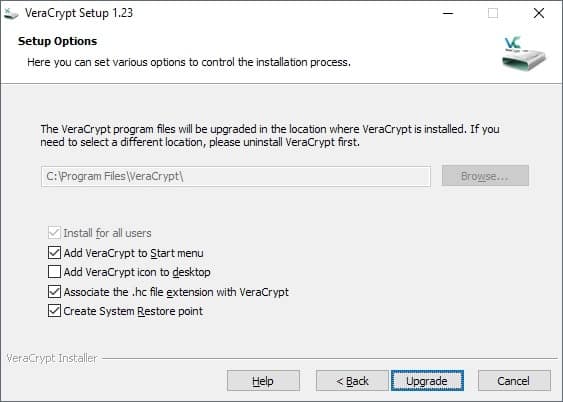
VeraCrypt is offered as a portable version and installer. You can download and extract the portable VeraCrypt archive and run it right away. The installer provides a few extra options such as adding an icon to the desktop or Start Menu, or associating the file extensions .hc with VeraCrypt.
The program creates a System Restore Point during installation and will install its drivers on the system. Note that it requires elevation because of that.
Using VeraCrypt
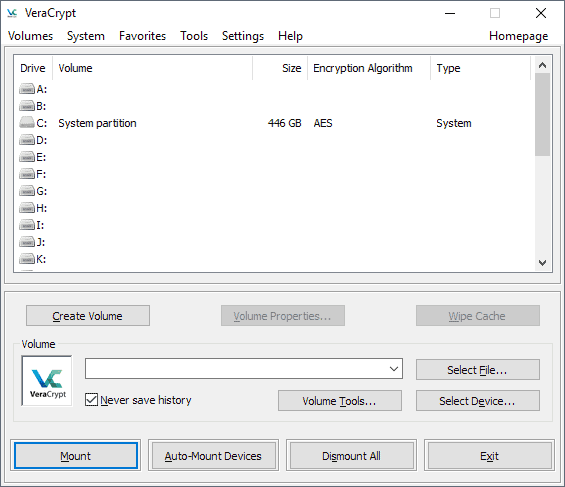
VeraCrypt's main interface looks almost like a copy of the classic TrueCrypt interface. The program lists available drive letters and mounted volumes at the top, and options to create, mount and dismount volumes in the lower half.
The menu bar links to additional tools, options and settings that new users may want to explore prior to creating a new container or encrypting a hard drive partition.
Interface options
- Create Volume -- starts a wizard to create a new container or encrypt a partition.
- Select -- The select options let you select an encrypted file (container) or hard drive partition for mounting.
- Mount options -- Select to mount the file or partition, dismount all, or configure auto-mount.
VeraCrypt Preparations
The very first thing you may want to do is go through all settings and some other steps to make sure everything is set up correctly.
Preferences
Select Settings > Preferences to open the general preferences. The developers squeezed a lot of settings on that single page and there is even a "more settings" button at the bottom that links to other Settings windows.
- Default mount options -- select to mount volumes as read-only or removable media. Read only prohibits writes to the drive and removable media defines certain parameters for the drive.
- Background Task and Startup -- VeraCrypt is loaded automatically on Windows start and a background task is up and running when users sign into the operating system. You can disable that here, configure VeraCrypt to exit when there are no mounted volumes or force the software to mount all device hosted VeraCrypt volumes automatically.
- Auto-Dismount -- Configure scenarios that dismount all mounted volumes automatically. VeraCrypt does so when users log off by default but you can enable the dismounting on lock, screen saver, power saving mode, or when no data is read or written for a set period.
- Windows-specific -- Gives you options to open Explorer automatically on mount, to use Secure Desktop for password entries for improved security, and to disable the wait message dialog during operations.
- Password Cache -- Define the use of the password cache and related options. Options include forcing VeraCrypt to wipe the cached password on exit (VeraCrypt does to automatically on dismount), or cache passwords in the driver's memory.
Here is a quick overview of other settings pages in VeraCrypt:
- Settings > Language -- change the interface language.
- Settings > Hot Keys -- configure system-wide hot keys to run certain operations such as dismounting all or wiping the cache.
- Settings > System Encryption -- Options that apply when you encrypt the system drive e.g. to skip the pre-boot authentication prompt by pressing the Esc-key.
- Settings > System Favorite Volumes -- Add volumes to the favorites.
- Settings > Performance and Driver Options -- Find out if AES hardware acceleration is supported, allow certain performance or driver related tasks such as TRIM or Defrag.
- Settings > Default keyfiles -- If you use keyfiles to authenticate (more about that later), you may add keyfiles to the list of default files.
Benchmark
VeraCrypt includes a tool to benchmark all supported encryption algorithms. That's useful as it highlights which algorithms offer the best performance.
While you may select any supported encryption algorithm when you create new containers or encrypt volumes on the system, it is often best when you select a fast algorithm as it will speed up operations significantly.
Note: It is recommended that you create a backup of important data on the device before you use VeraCrypt to encrypt it.
Using VeraCrypt
VeraCrypt can be used to create encrypted containers -- single files that are stored on a drive that does not need to be encrypted -- or to encrypt an entire volume.
Volumes are divided into system volumes and non-system volumes. VeraCrypt supports both and can be used to keep all files as they are on a volume when you run the encrypt command.
- Container -- Single file that can have any size (file system limitations and volume limitations apply).
- System Volume -- The partition the operating system is installed on.
- Non-System Volume -- All other partitions.
The encryption process begins with a click on the "create volume" button. VeraCrypt displays the three available options on the first page and it is up to you to select one of the available options.
If you want to make sure that no one can access the computer or the data on it, you may want to select encrypt the system partition or entire system drive.
VeraCrypt displays an authentication prompt on boot then to decrypt the drive and boot the operating system. Anyone who cannot provide the password can't boot into the operating system.
The process is nearly identical for all three options. The core difference between creating a container and encrypting a partition is that you select a file when you select the former and a partition when you select the two other options.
- Standard or hidden volume -- You can create normal volumes or hidden volumes. Hidden volumes are created within standard volumes. If someone forces you to unlock the drive, only the standard volume is unlocked.
- Volume location -- Select a file (it gets created) or a partition that you want to encrypt.
- Encryption options -- Select an encryption and hash algorithm. You can run the benchmark from the page if you have not done so already.
- Volume Size -- Only available if you select the container option.
- Volume Password -- The master password that is used to encrypt the drive. You can use keyfiles and PIM as well. Keyfiles are files that need to be present to decrypt the drive and PIM. PIM stands for Personal Iterations Multiplier, it is a number that you need to supply when mounting volumes when you set it during setup.
- Volume Format -- Select the file system and cluster size. You are asked to move the mouse to create a random pool. Only available for some decryption operations.
There are two things that you may want to do after creating a new encrypted volume:
- Select Tools > Backup Volume Header to back up the volume header; useful if the volume gets corrupted.
- System > Create Rescue Disk to burn it to DVD or to a USB Flash Drive. Again, useful only if the system won't boot anymore or if the VeraCrypt boot manager has been overwritten or is corrupt.
You can mount containers or volumes at any time. Just use "select file" or "select" device" in the main interface, pick the desired target, and fill out the password (and other required things) to mount it as a new volume on the computer system.
Resources
VeraCrypt FAQ
Why was TrueCrypt development abandoned?
The (anonymous) developers of TrueCrypt never revealed why they abandoned the program. They did claim that the software was not safe to use, however.
Is VeraCrypt safe to use then?
TrueCrypt's code was audited and VeraCrypt fixed the security issues found by researchers during the audit. The developers of VeraCrypt implemented additional safeguards and improvements in the program, for instance by increasing the number of iterations significantly to make brute force attacks more difficult.
What are the main differences between VeraCrypt and TrueCrypt?
VeraCrypt uses its own storage format but supports the mounting and converting of TrueCrypt format volumes and containers.
Other major differences are that VeraCrypt includes fixes for vulnerabilities found in the TrueCrypt audit, that VeraCrypt supports PIM functionality, that it supports encryption of GPT system partitions, and that VeraCrypt system volumes don't need to be decrypted anymore during Windows 10 updates.
Which algorithms does VeraCrypt support?
VeraCrypt 1.23 supports the following algorithms:
- AES
- Camellia
- Kuznyechik
- Serpent
- Twofish
Combinations of cascaded algorithms are available as well:
- AES-Twofish
- AES-Twofish-Serpent
- Camellia–Kuznyechik
- Camellia–Serpent
- Kuznyechik–AES
- Kuznyechik–Serpent–Camellia
- Kuznyechik–Twofish
- Serpent–AES
- Serpent–Twofish–AES
- Twofish–Serpent





















Used it to open Truecrypt volumes repeatedly tells my my password is wrong. No longer can access my important data in VeraCrypt or TrueCrypt! Looks like I’ve lost this important data forever. Don’t trust VeraCrypt!
Stick with VeraCrypt or TrueCrypt because they are open-source. At least, as a software engineer, you can independently verify and compile your own versions of said software.
Bitlocker, on the other hand, is proprietary and closed-source. Also, it’s written by Israelis on behalf of Microsoft – a fact Microsoft never admitted openly. Bitlocker has backdoors to allow security and spy agencies like Aman (Israel), Mossad (Israel), Shabak (Israel), CIA (USA), NSA (USA), etc, to access any Bitlocker locked drives when the needs arise (wink! wink!).
So beware what you choose for your hardware and software encryption. You might regret your choice.
Main ‘issue’ with VeraCrypt is the storage performance hit – it’s typical when I’ve tested it to see it cut random read performance by about two-thirds on a HDD, with the effect on SSDs being similar or far more dramatic depending on the specific test. The problem doesn’t seem to be in the encryption/decryption part measured by the built-in benchmark – there’s obviously no bottleneck in the CPU’s AES hardware. It is some other kink in the code that the developer has acknowledged and which is apparently not easy to fix.
On the same hardware, Bitlocker’s performance impact can be basically nil, even in software mode.
VeraCrypt wins in features/flexibility, though, and perhaps trustworthiness. And having used it and its predecessor across multiple systems for over a decade, I can also credit it with being very robust – never had a volume go bad or encountered any data corruption issues (athough this is only speaking for non-system volumes – I’ve never tried it on an OS partition).
Create an over 1tb container (say 1100gb) as a network drive, use windows 10 to access it. After few times, it breaks it and it is unusable – windows 10 literally corrupts the file. So they are not that great when it comes to working with win 10.
TrueCrypt was audited, but Veracrypt was not.
Which one would you trust?
VeryCrypt was audited as well: https://www.ghacks.net/2016/10/18/veracrypt-1-19-fixes-security-vulnerabilities/
Didn’t realize that. Thanks for pointing it out!
Just a heads up guys! To encrypt your system partition on Windows Veracrypt needs to replace Windows’ bootloader. When Windows upgrades though it may need to upgrade the bootloader as well. Then you’re left with a system that won’t boot unless you’ve kept your Veracrypt rescue disk ( please do, you’ll thank me later ), put it in a flash drive, boot from it and reinstall it. If you plan for it , it should be fine but don’t get caught off guard
I love VeraCrypt, but the problem is SSD performance, especially writing performance.
Instead of 330MB/s in crystal mark, I get 1.5MB/s. It’s noticeable even in office tasks, my entire system freezes, with the SSD at 100% writing at like 2MB/s.
Other encryption solutions don’t have this problem.
Scroll toward the bottom for comparison charts: https://superuser.com/questions/235420/bitlocker-performance-impact-on-ssd
That’s very annoying. I was planning to move to an SSD. Does anyone know whether SSDs embedded encryption systems (noticeably Samsung’s) are a replacement for Vera Crypt ?
The specific test you were pointing at is here : https://superuser.com/a/1306590
There is absolutely no issue with VeraCrypt and SSDs. I run it on several and there is no impact. Impact is encryption and decryption which are CPU constrained. Which is why it is usually the best to pick AES as it tends to be the fastest algorithm.
Internal benchmark can give you exact numbers for the machine you are using.
I’m glad it works for you, however it seems it’s a known problem. This, from Vera Crypt forum :
SSD Very Slow Performance Compared to Bit Locker (using AES)
https://sourceforge.net/p/veracrypt/discussion/general/thread/9cb021ad/
Vera Crypt not working correctly on M.2 Samsung 960 Pro
https://sourceforge.net/p/veracrypt/discussion/technical/thread/9c72fd1e
On the two following threads, Mounir Idrassi, the developer, seems to admit the problem :
System Encryption SSD poor performance
https://sourceforge.net/p/veracrypt/discussion/technical/thread/b17b65d0/
Vera Crypt performance vs no encryption
https://sourceforge.net/p/veracrypt/discussion/technical/thread/ead5ae6c
This user, however, experiences no issue :
https://sourceforge.net/p/veracrypt/discussion/technical/thread/06def483/
Performance-related threads on Vera Crypt forum bring up the SSD issue :
https://sourceforge.net/p/veracrypt/discussion/search/?q=performance&project=0
Mounir Idrassi warns about another possible, security issue with SSDs and Vera Crypt :
https://sourceforge.net/p/veracrypt/discussion/technical/thread/88cef61b/#6ae8
In 2014, Mounir Idrassi confirmed that mounting of system, or even non-system partitions, was significantly slower with Vera Crypt than with True Crypt, and that is was by design :
https://sourceforge.net/p/veracrypt/discussion/technical/thread/77d58591/
I would just like to point out a tip here. It says that you cannot dual-boot encrypted Windows and Linux on a single drive. This is false, you can. What you do is, install GRUB to the Linux partition, NOT to the MBR where Veracrypt lives (or else GRUB will nuke the Veracrypt loader/master key, breaking Windows in the process). E.g. instead of “grub-install /dev/sda”, you would do “grub-install –force /dev/sda2”, or whatever the Linux partition is. Of course, don’t get the number wrong either. Now just press esc when presented with the Veracrypt boot loader to boot the next partition.
But an easier way is to just use two drives, like an HDD and an SSD and put grub on the HDD, while veracrypt boots off the SSD.
Love veracrypt. The only boring is that the pre-boot operation takes a hefty time to verify the password. While with LUKS it takes max 2 seconds to boot the computer on full disk encryption
Thanks for your comments. PIM is not an option to touch.
The security is the main topic here. The only possible outcome is to increase the PIM never decrease
This is because of the PIM iteration count. If you want, you can decrease it (use the change password option and change to a lower PIM). Note that this will weaken security, but you should still be well protected from the average thief or if you misplace the computer, as long as you choose a decent password.
That is the entire point of PIM. Initial decrypt should be slow as hell as that means that each attack try takes very long time and a brute force attack becomes less rhan feasible.
The time taken for decryption with a single, correct password does not bear any relationship to the time taken by an attacker attempting brute force. Mounting of encrypted volumes should not have a significant, perceived delay. This is a matter of compromise and good programming.
I do agree that Vera Crypt seems to take much longer than True Crypt to process the password. And yes, it’s annoying. (I haven’t even attempted system disk encryption.)
I see that I phrased it badly. I meant a brute force attack on the password as that tends to be far weaker than doing brute force attack against the underlying symetric chipher.
Longer it takes to check the password (Essentially number of iterations controlled by PIM setting) the slower the brute force attack against it. Especially with variable PIM where it’s difficult to know if password or PIM are wrong (although you can make an educated guess on maximum PIM).
@ AxMi-24
In fact, that’s what I had understood from your remark. My point still holds. Encryption software should not get in the way. Decryption should be, if not instant, at least fast enough that you don’t really notice it. True Crypt worked that way. My Macrium Reflect disk images are AES-encrypted by the program, and mounting them is almost immediate. You don’t feel that you have to wait.
I don’t have cryptographer expertise, but brute-forcing a good password is so expensive in term of resources, that you certainly should not need to make decryption slow for users in order for the software to be safe. Aren’t you assuming a weak password here ?
A volume or system disk encryption password should obviously be a very good one. And it should be commited to memory, although some users might prefer to write it down somewhere safe.
That’s also why I’m skeptical of Vera Crypt’s PIM option as a second password. Yes, having a second password increases security in theory, but it decreases it in practice, because you need to remember two passwords instead of one. Simplicity is security. Remembering a single, good password is difficult enough.
That being said, I did not make extensive tests with Vera Crypt, changing settings and timing decryption. But just transitioning from True Crypt to Vera Crypt felt like a downgrade, as far as user experience is concerned. True Crypt was intimidating at first, but once I learned it, it felt unobtrusive. Finger memory was enough to interact with it. Not so with Vera Crypt.
@Clairvaux
The slow part is due to PIM controlled iterations that decrypt the symetric key that controls the symetric encryption (usually AES). So that delay has nothing to do with AES. This ensures that the symetric key has maximal possible entropy without impacting the operational speed.
However, any password that is reasonably easy to be remembered by a human is a bad password. We are utterly incapable of remembering high entropy passwords and this is why default assumption is that password is weak and should be protected as much as possible.
It’s similar to how 2FA is used to protect accounts despite less than optimal password protecting it (it ofc has other additional benefits so it’s not 1 to 1 comparison)