Browsers have cookie and anti-tracking enforcement issues
A team of Belgian researchers from KU Leuven analyzed third-party cookie policies of seven major web browsers, 31 ad-blockers and 14 anti-tracking extensions and discovered major and minor issues in all of them.
Major issues include Microsoft Edge's unwillingness to honor its own "block only third-party cookies" setting, bypasses for Firefox's Tracking Protection feature, and use of the integrated PDF viewer in Chrome and other Chromium-based browsers for invisible tracking.
Cookie requests can be sorted into two main groups: first-party requests that come from the address listed in the address bar of the browser and third-party requests that come from all other sites.
Advertisement displayed by websites makes use of cookies usually and some of these cookies are used for tracking purposes.
Internet users can configure their browsers to block any third-party cookie requests to limit cookie-based tracking. Some browsers, for instance Opera or Firefox, include ad-blockers or anti-tracking functionality that is used in addition to that.
Anti-tracking mechanisms have flaws
The research paper, "Who Left Open the Cookie Jar? A Comprehensive Evaluation of Third-Party Cookie Policies", detailed information about each web browser, tests to find out if a browser is vulnerable to exploits, and bug reports are linked on the research project's website.
The researchers created a test framework that they used to verify whether "all imposed cookie- and request-policies are correctly applied". They discovered that "most mechanisms could be circumvented"; all ad-blocking and anti-tracking browser extensions had at least one bypass flaw.
In this paper, we show that in the current state, built-in anti-tracking protection mechanisms as well as virtually every popular browser extension that relies on blocking third-party requests to either prevent user tracking or disable intrusive advertisements, can be bypassed by at least one technique
The researchers evaluated tracking protection functionality and a new cookie feature called same-site cookies that was introduced recently to defend against cross-site attacks.
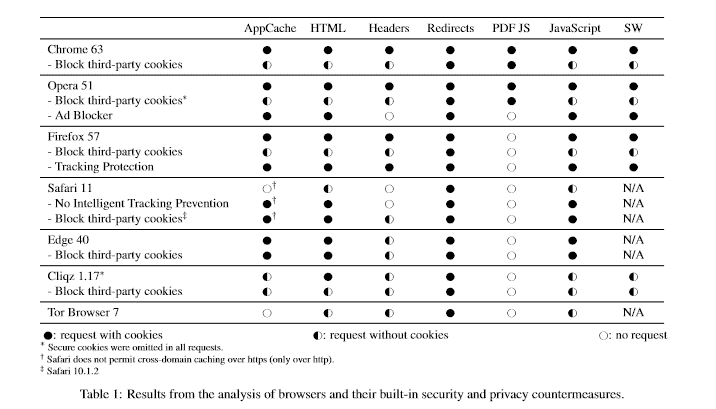
Results for all tested browsers are shown in the table below. The researchers tested the default configuration of Chrome, Opera, Firefox, Safari, Edge, Cliqz, and Tor Browser, and configurations with third-party cookie blocking disabled, and if available, tracking protection functionality enabled.
Tor Browser is the only browser on the list that blocks third-party cookies by default. All browsers did not block cookies for certain redirects regardless of whether third-party cookies were blocked or tracking protection was enabled.
Chrome, Opera and other Chromium-based browsers that use the built-in PDF viewer have a major issue in regards to cookies.
Furthermore, a design flaw in Chromium-based browsers enabled a bypass for both the built-in third party cookie blocking option and tracking protection provided by extensions. Through JavaScript embedded in PDFs, which are rendered by a browser extension, cookie-bearing POST requests can be sent to other domains, regardless of the imposed policies.
Browser extensions for ad-blocking or anti-tracking had weaknesses as well according to the researchers. The list of extensions reads like the who is who of the privacy and content blocking world. It includes uMatrix and uBlock Origin, Adblock Plus, Ghostery, Privacy Badger, Disconnect, or AdBlock for Chrome.
The researchers discovered ways to circumvent the protections and reported several bugs to the developers. Some, Raymond Hill who is the lead developer of uBlock Origin and uMatrix, fixed the issues quickly.
At least one issue reported to browser makers has been fixed already. "Requests to fetch the favicon are not interceptable by Firefox extensions" has been fixed by Mozilla. Other reported issues are still in the process of being fixed, and a third kind won't be fixed at all.
You can run individual tests designed for tested web browsers with the exception of Microsoft Edge on the project website to find out if your browser is having the same issues.
Closing Words
With more and more technologies being added to browsers, it is clear that the complexity has increased significantly. The research should be an eye opener for web browser makers and things will hopefully get better in the near future.
One has to ask whether some browser makers test certain features at all; Microsoft Edge not honoring the built-in setting to block third-party cookies is especially embarrassing in this regard. (via Deskmodder)
Now You: Do you use extensions or settings to protect your privacy better?





















So where is the link to check my browser, a reference on https://wholeftopenthecookiejar.eu/ ?
Or a “test” facility on the “Who Left Open the CookieJar” web page?
I would like to know how PaleMoon performs. ?
Raymond Hill should make his own privacy-centric browser. Or someone should. Don’t expect Google or Microsoft to do it, and Mozilla likely won’t go directly against the spy/ad industry directly either.
Tried all test in https://wholeftopenthecookiejar.eu/ and they all failed with “Request was NOT triggered”.
I’m using the latest Chrome with ublock origin, https everywhere and privacy possum.
For pdf I’m using sumatra pdf.
Test with cross-site request that should be blocked by easylist.txt: No difference in results checked or not.
Third-party cookies are still included in all requests when enabling the option to block these in Edge. – https://wholeftopenthecookiejar.eu/
Count on MS to include the option – then ignore it.
Edge has always been on the border-line.
This is becoming an epidemic. I just read an article that says Google saves location data even when you turn off Location History. I quote Google…
“This setting (location history off) does not affect other location services on your device, like Google Location Services and Find My Device…Some location data may be saved as part of your activity on other services, like Search and Maps.”
Source…https://www.zdnet.com/article/google-to-be-clear-this-is-how-we-track-you-even-with-location-history-turned-off/
Google only clarified what they were doing because the Associated Press news service caught them doing it on one of their smart phones. I once owned a cheap Amazon tablet. It appeared to me that Amazon apps were feeding user info back and forth – even when there seemed to be no logical reason for it. I took the tablet into a shop, smashed it and threw it away.
The original AP article is here…
https://apnews.com/828aefab64d4411bac257a07c1af0ecb
Now, everybody wants to know everywhere I go and everything I do. Why wasn’t I this popular with girls when I was in school?
@jern: “Why wasn’t I this popular with girls when I was in school?”
Because those girls couldn’t make money off you.
I have an old maid, and her name is CCleaner. She basically cleans up after me… removing every cookie, or crum… sometimes, even CUM. 🌚
I don’t update her though, cuz I heard she’s hungry for usage data collection. 🌚
Firefox – Security/Privacy in general
———————————————–
Base :
Policy Templates, Autoconfig, Pants’ Ghacks-user.js
Extensions :
uBlock Origin : Hard Mode, Settings/Privacy with all four options checked
Privacy Possum
Trace (partially only)
Decentraleyes
HTTPS Everywhere
Neat URL
Skip Redirect
Clear Cookies and Storage Button
HistoryBlock
Firefox – Cookies
———————–
Policies :
Cookie behavior set to allow same host : (“network.cookie.cookieBehavior”, 1)
Cookie lifetime policy set to session : (“network.cookie.lifetimePolicy”, 2)
Extensions :
Forget Me Not : wipes cookies on site exit by default unless whitelisted
Cookie Quick manager : as cookies’ editor
Forget Me Not cleans cookies, localStorage (specific to cookies) but beyond as well.
Why set Firefox cookies lifetime policy to session only given ‘Forget me Not’ will wipe non-whitelisted cookies?
Because session only prevents sites from feeding user’s localStorage — Even though ‘Forget me Not’ cleans localStorage as well on non-whitelisted sites, I dislike seeing my webappstore.sqlite file getting heavy (YouTube i.e. can leave MBs of localStorage, and when localStorage is cleaned by ‘Forget Me Not) it gets emptied but not resized.
How do I deal with cookies I wish to keep beyond session only?
In Firefox / Options / Privacy & Security / Cookies and Site Data / Exceptions
I allow sites accordingly
How do I deal with sites laying data in my IndexedDB (‘Profile / storage / default’ sub-folder)?
I use an external application called ‘Folder Monitor’ set to monitor above sub-folder : when a site dares lay its data, Folder Monitor’ alerts me and I then block all cookies for that site in Firefox’s Cookies and Site Data exceptions mentioned above : cookies blocked means a site can lay neither cookies, neither localStorage, neither indexedDB : radical but those sites just had to remain reasonable (as most do).
Above mentioned ‘Forget me Not’ extension can wipe sites’ IndexedDB as well, but only manually by the user or automatically on Firefox restart : I prefer to block than to wipe.
From there on, no problems. History and cache (RAM only, disk cache is disabled) are cleaned on Firefox exit (and occasionally within the session with a dedicated extension : ‘Clear Cookies and Storage Button’). No need for years’ old history, I know what I like when I see it and bookmark it accordingly). One last extension fits here : ‘HistoryBlock’ used for sites such as Google Maps which increment the user’s history on every latitude/logitude second of arc change … true pain.
I think it’s about all at this time.
> cookies blocked means a site can lay neither cookies, neither localStorage, neither indexedDB
Not quite true. Service workers use IDB. But of course you can control SW via uMatrix (if you want the flexibility of whitelisting a site to use SW), or block SW completely via the FF pref
@Pants, nice and thanks for correcting that assertion of mine. I tend to forget these Service workers, always in a shadow or in that of my mind. One thing is sure : many sites lay their data in the userr’s profile when not at all necessary, you know that better than anyone. Cookies are the leader of the band but as we know other opportunities have become the entry point to our privacy and that’s what you manage with Ghacks-user-js, as well as several dedicated extensions do. The aim is to find the right extensions for a given task and get all these defenders to work in harmony of course.
That’s a lot of fortifications/settings, do you have performance issues with browsing and page load times?
I guess this question is for anyone using hyper defense methods for protection.
I adhere to the KISS principle, keep it simple but ready to change/adjust as new threats emerge.
Using Chrome, it’s just ublock with 3rd party partially blocked and 3rd party scripts & frames blocked as well.
Plus dynamic and cosmetic filtering as needed.
Three other items you might consider: Nano-Defender-can help bypass anti adblock firewalls
Sandboxie (free) Essential. Set the box to auto delete session on close.
Minimize filter lists: am using Steve Blacks hosts addon as it has comprehensive base filtering plus extended social/fake news sites & trackers blocked with frequent updates. https://github.com/StevenBlack/hosts
Just Windows Defender/Firewall protecting everything else,
@ddk, no performance issues, on the contrary. It’s all very simple in fact, don’t rely on my explanations which make it sound more complex than it is, though I’ve tried to make it as clear as I could. The idea as always is that a browser comes in with arguable settings and that these settings are modifiable or not, opt-in or opt-out. If modifiable (Firefox definitely is flexible) then we call tools and extensions dedicated to fine tune the browser. And let’s not forget that it’s less the amount of processes we induce or block that counts than their interaction, non-redundancy, compatibility that counts : if two actions do the same job or if they appear at one time to be incoherent then the system slows down, not otherwise.
@ddk: interesting you mention Nano Defender. It is made to work in tandem with Nano Adblocker. Since the latter is almost identical, though not quite, to uBlock Origin, ND can work with uBO too.
Do you have any experience with Nano Adblocker? If so, what do you think of it?
@klaas: No experience with Nano Adblocker. Actually I just recently found out about Nano from reading the ublock Reddit support threads, then discovered this addon site which has all sorts of extra filters for various ad blocking extensions: https://filterlists.com/.
So just using Nano Defender Integration at the moment which I’m guessing is not the actual ad blocker. The main purpose for my using Nano is getting around anti ad block techniques, but may check out the ad blocker itself later. Thanks for the heads up.
All the tests failed on Vivaldi 1.15 (while using Chrome 67 and 68 codes), by failed I mean no cookies were stored.
This is not because of the browser settings though, Adguard blocked all the requests (means it will protect me from this exploit in all the browsers).
First, you need to disable the blocking of 3rd-party cookies in your browser if you want to test content blocker extensions.
Adguard does not fail the “Redirects” category — uBO does, because of its strict-blocking feature.
The test on the site is broken for that category — they used network requests to “adition.com” in their real benchmarks, not so on the test site, probably because that would cause undue network traffic to adition.com servers.
The way they test “Redirects” on their site will not give you the proper result. You can simulate the proper result by using the filter “||cross-site.com^$document” in your blocker before launching any of the “Redirects” tests.
For network protection I’m using MVPS hosts file, Peerblock, NoScript, Comodo Firewall v.5.10 with Firefox 52.8 ESR on an XP sp3 machine and a Cisco/Linksys business firewall. So far, so good. :), but what I wanted to mention here is that maybe about a week ago after I read one of Martin’s article, based on the feedbacks I added google.com and youtube.com to the list of website that Firefox should not accept cookies from, and to my greatest surprise, half an hour later I checked the cookie blocking list because I wanted to add one more website and bumm, the list was empty! I added these two websites again to the blocked cookie list and checked back 5 minutes later, they were gone again. So, I gave up and just now I figured maybe I’ll post it here, maybe someone has a good explanation for this?
Excessive protection imho. Windows 10 with Chrome+uBlockOrigin should be enough, no problem for me since 2015. I dislike W10 updating/upgrading method, however is 100% better than WXP.
I use Chrome and it must be configured after every update/upgrade because the settings changed, including cookies, form-filling, password manager and also stored pay methods. It’s so annoying.
They even tested things like “uBlock Adblocker Plus”, “uBlock Plus Adblocker”. Nothing wrong with a thorough research, but imo such blatant ripoffs should not be allowed in any store. Even if they are open source and clean, for now, you never know when you end up with an update which will make them behave in a malicious way. Company names such as “Block Systems, inc.” and “uBlock Plus Adblocker” respectively do not inspire too much credibility. And they are trying to deceive the users, there is no denial, both are using versions higher than uBlockOrigin, implying they are newer.
On a similar note, shame on the guy behind the product simply called “uBlock” nowadays for not taking it down or redirectly everyone to uBlockOrigin. Apparently the Chrome version has been updated on 26th June 2018 to version 0.9.5.7, but hell knows why. It even has crap like “Allow uBlock to collect anonymous ping and usage data.” and probably will gladly accept your donations too. The scum of the Earth the guy behind this extension is, no other way of describing him. Fuck him.
Holy shit. ‘uBlock, LLC’, Is this the same guy? they registered their company name after the open source software from which they don’t own and merely copied from. These are the types of people that need to be culled from the general population.
But the real shaming should be directed towards Mozilla / Google for allowing this and not enforcing real quality control.Think of the case with Stylish: Over a hundred thousand users had their browsing history tracked and sold off over a 11 month period. It took a 3rd party to discover this and make a big fuss for them to do anything about it. The thing is, Mozilla / Google does receive a copy of unobfuscated code to review and the Stylish EULA clearly stated they collected user browsing history. If they actually cared they would have vetoed it right from the very beginning.
From https://bugzilla.mozilla.org/show_bug.cgi?id=1447933 :
“AppCache is going away. We won’t be doing any work to support it.”
Wonder which route will be taken by Waterfox and Pale Moon.
I have converted to uMatrix on all my browsers : Firefox, Opera and Vivaldi. I have ditched all the other blockers. On Tor, I don’t alter the native configuration which comes with No Script.
I have discovered a rather annoying problem with uMatrix and the latter versions of Firefox (but it’s the same on other browsers) : you can’t see the whole matrix when the browser’s window is narrowed to roughly 2/3 of its full width.
Interestingly, this is also a problem with many websites, that I had not noticed pre-Quantum : they tend not to reflow their layout when you narrow the browser’s window. Or at least not very much, or not as much as would be needed. Opera and Vivaldi seem to behave in a similar manner. So you need to scroll horizontally.
Has anybody else noticed that difference ? I find it very annoying.
I use Chrome beta and the free Foxit replacing Chrome for PDF renders. I did this for better PDF options for me, but now there seems to be a further advantage per this fine article.
as i always write when it comes to cookie – handling under ff: no addon. block cookies and site data per default and whitelist some sites (logins, et cetera) per right click – view page info – permissions . that’s it. for the rest, i’m using mwb – browser – extension (beta) + balanced user.js. . the ff – tracking protection (in this case even vulnerable and based on a very weak disconnect.me block list (even the “strict block list” is weak)) is disabled. see also: https://wholeftopenthecookiejar.eu/ (bypasses for the firefox tracking protection discovered).
Great research, kudos to them !!!
And thanks a lot for the sum-up Martin !
Agree!
To the truth of its effectiveness, I was very interested.
It is meaningful to parallelly compare Browser’s representative (Google, Opera, Microsoft, Apple, Mozilla, Tor) and prominent extensions and to do it fairly.
By publishing the result, light is given to the darkness and justice is brought.
Thanks to the scientific view of the truth “KU Leuven’s Belgian researchers’ team” and Michael Horowitz, Deskmodder.de, ghacks.net.