NoScript guide for Firefox 57+
The developer of the popular Firefox security add-on NoScript launched a Firefox 57 compatible version of the extension shortly after the release of the Firefox 57 browser.
He worked with Mozilla to create the new version of NoScript and implemented options to migrate settings from classic versions of NoScript to the new version.
The initial version received mixed reviews. Some users heralded the effort and were happy that NoScript was available for Firefox 57 and newer, others did not like the new user interface or criticized missing functionality.
Now that the dust has settled, it is time to publish an updated guide for NoScript for Firefox 57 or newer.
The NoScript for Firefox guide
NoScript Security Suite is a browser extension for the Firefox web browser designed to give users control over the content that sites may run. The extension blocks JavaScript execution by default which improves security and privacy significantly. NoScript supports other features, XSS and clickjacking attack protections and other security enhancing features.
The NoScript interface
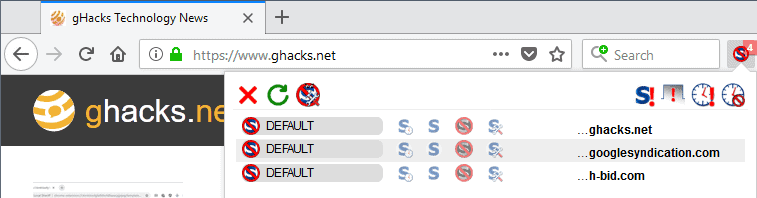
The main interface of the extension changed completely in the new version. The classic version of NoScript listed connections in list view on activation, the new version of NoScript uses a matrix instead similarly to how uMatrix handles connections.
The interface displays a button toolbar at the top and below it the list of domains. NoScript lists the current domain at the top all the time and below it the third-party connections of the page.
The padlock symbol displayed next to domains indicates that the connection to it uses HTTPS. Note that the padlock symbol is not displayed for some trust levels.
Setting trust levels for domains
Each domain listed by NoScript in its interface has a trust level associated with it.
- Default -- JavaScript execution is blocked as are objects, media, fonts, and WebGL.
- Trusted -- Allow JavaScript execution and other elements.
- Trusted Temporarily -- Allow JavaScript execution and the loading of other elements for the session or until revoked whichever is first.
- Untrusted -- Everything is blocked.
- Custom -- Gives you options to allow or disallow elements individually. You may make these temporary by clicking on the "nearly invisible" temp button next to custom.
Each domain listed by NoScript has one trust level associated with it. A click on another trust level in a row switches it to the new one automatically.
The NoScript options reveal the preset permissions for "default", "trusted", and "untrusted".
There you may also change the default presets by adding or removing checkmarks. The elements that NoScript distinguishes between are:
- Script -- Any type of script the site attempts to execute.
- Object -- The HTML object tag.
- Media -- Media elements.
- Frame -- Frames that the site attempts to load.
- Font -- Font elements.
- WebGL -- WebGL elements.
- Fetch -- requests that use fetch APIs.
- Other -- unknown.
The button toolbar
Seven buttons are displayed on the button toolbar in the latest version of NoScript for Firefox. They are, from left to right:
- Close the interface.
- Reload the page.
- Open the Options.
- Disable restrictions globally.
- Disable restrictions for this tab.
- Set all on the page to temporarily trusted.
- Revoke temporary permissions.
NoScript adds a context menu item to the right-click menu automatically. It has limited use though; a click on it displays the main NoScript interface at the top of the browser UI. You can disable the context menu entry in the options.
Using NoScript
Understanding how NoScript trust levels work is essential to using the extension to its fullest potential.
NoScript indicates blocked items in its icon when you load sites in the Firefox browser. A click on the icon displays the connections the extension recognized and trust levels for each site. Note that these may not be all connections a site makes. Since you don't allow the execution of scripts by default, sites may not be able to initiate all third-party connections right away.
If you allow scripts to run on the main domain, you may notice that it attempts to make additional connections when those get loaded.
Tip: Hover over any domain listed by NoScript and click on it to open a page that is full of links to privacy and security services only to display information about the domain.
It may not be necessary to make any changes to trust levels if the site functions properly. You may notice however that some features may not work properly on first connect.
Since scripts and other elements are blocked by default, you may notice all sorts of issues related to that. Sites use scripts and other elements for a variety of things, from verifying form submissions and playing videos to often unwanted things such as advertisement or tracking.
Changing a domain's trust level to "trusted" or "temporarily trusted" allows it to load additional elements whereas a trust level of "untrusted" prevents even more elements.
Note that trusted and untrusted are permanent changes that remain available.
Troubleshooting a site comes into play when you notice that site functionality is not available and suspect it is because of the protections that NoScript provides.
You have a couple of options to deal with the issue. You could temporarily allow a domain or use the custom trust level to set permissions individually for elements.
I'm not a fan of using the "allow all globally" or "allow all for the tab" options as they are often too broad. While they are comfortable, as you only need to press some buttons to get sites to work, using them eliminates most of the protective functionality of NoScript.
NoScript comes with a whitelist that includes sites by default. You may want to check it in the options under "per-site permissions" to make sure that you trust them all. There is unfortunately no option to remove sites that are on the list by default but you can change the level from trusted to default or even untrusted.
If you migrated from a previous version of NoScript, you should see all custom sites there.
Check out our guide on using NoScript efficiently for tips on getting the most out of the extension. It offers ten tips, for instance what you may want to do if a site does not load properly with NoScript enabled.
The options
The options are somewhat limited at this point in time especially when you compare them to the options of the classic version of NoScript.
The NoScript settings are divided into four tabs right now that offer the following functionality:
- General -- Configure preset permissions for the states Default, Trusted, and Untrusted. Also, enable "disable restrictions globally" and "temporarily set top-level sites to Trusted".
- Per-site Permissions -- displays all custom (non-default) permissions. Search included.
- Appearance -- hide the context menu item, disable the count badge of the icon, and enable the listing of full addresses in the permissions popup.
- Advanced -- manage XSS protection and enable debugging.
Options can be reset, imported, or exported.
Resources
- Official NoScript website: https://noscript.net/
- NoScript on Mozilla AMO: https://addons.mozilla.org/firefox/addon/noscript/
- NoScript GitHub: https://github.com/hackademix/noscript






















I agree with many of the posters before me, saying NoScript is, or at least feels like, a waste of time.
But still I really like the idea of having NoScript, I think browsers should have it built-in. With a slight usability standpoint twist though: It should allow everything by default, no blocking by default. With it installed, you can inspect where stuff, which still runs as usual, comes from – something, that for some unknown reason, is absolutely impossible without it. At least by far not as efficient.
I found that JavaScript engines of browsers use up large amounts of RAM. So sometimes it might benefit to block some objects you suspect to slow stuff down. On a quad or more core desktop PC it might be irrelevant, but on Android however… well it’s more hassle to use because of the limitations of mobile GUIs, but the benefits have far more felt impact.
NoScripts defaults are preventing it from widespread adoption. The concept of installing something to have “less features” (as in: suddenly most websites don’t work anymore), is “weird”, if you know what I mean.
I’m not sure if most people giving out operational security tips to the widespread masses, including its dev, realize how this feels to non tech knowledgeable people. Adding something, but having less comfort afterwards – when computers are the epitome of comfort. In return, it makes people miss NoScript not so much anymore, something making life harder for all of us in the end, I’d say.
I wish people would realize this.
noscript was the 1st extension installed after firefox
australis meant – no more firefox for me -at all, which meant “replace for noscript on chrome” and best thing i found is “script block”
best there is
I until a few years ago was using NoScript.
However, uBlock Origin and uMatrix replace it.
With uMatrix, Requests can be visualized and complete control is possible. NoScript is inadequate.
In addition, it has a combination of the following addons as a complementary function.
・HTTPS Everywhere https://addons.mozilla.org/en-US/firefox/addon/https-everywhere/
・Google Analytics Opt-out Browser Add-on https://tools.google.com/dlpage/gaoptout
・Decentraleyes https://addons.mozilla.org/en-US/firefox/addon/decentraleyes/
・Firefox Lightbeam https://addons.mozilla.org/en-US/firefox/addon/lightbeam/
・Privacy Badger https://addons.mozilla.org/en-US/firefox/addon/privacy-badger17/
And now, Netcraft Anti-Phishing Extension was added.
In case you need a lightweight extension that provides XSS protection you could go with the Netcraft Anti-Phishing Extension (https://addons.mozilla.org/en-US/firefox/addon/netcraft-toolbar/).
I’ve installed-removed-reinstalled-re-removed the Netcraft Anti-Phishing Extension for Firefox numerous times, not because of issues (it performs excellently well and I noticed no lag) but rather for psychological reasons (only psychological because Netcraft is a company I trust) as I had explained it when I had an AMO account (User ‘Anonymous user 230035’ at https://addons.mozilla.org/en-US/firefox/addon/netcraft-toolbar/reviews/)
I may very well once again reinstall it. Besides XSS protection it delivers as well information about the opened page’s domain. Certainly a most valuable extension.
“Netcraft Extension”
I was interested and tried it.
Indeed, it is practical and very useful.
Official website https://toolbar.netcraft.com/
I use uBO + uMatrix. uMatrix is somewhat similar to NoSCript. I’m also aware that it doesn’t have all the features of NoScript like XSS, etc., but it’s good enough. And uMatrix’s UI is miles better than the convoluted and confusing NoScript’s UI.
Use Disconnect to see visualized Trackers and block em, use Skip Redirect and uBlock Origin.
For more Privacy use Privacy Settings Addon and/or Google Search Link Fix, done.
Check out under about:config Telemetry Settings, turn em to false and get rid of Adressess.
No more Trouble here, Nuff said.
Blame Mozilla for rushing the release of Firefox 57.
They needed to get rid of the old extension system quickly, because they had already pushed out Electrolysis, which also broke compatibility, and they didn’t want extension devs to rewrite their extensions twice.
And they rushed Electrolysis, because they were bleeding users at mind-boggling rates prior to the release of that. If the trend had continued like it did before Electrolysis, Firefox would have negative user numbers by now.
Why can’t someone make a simple plugin that stops all redirects, popups, popunders, and nuisance overlays for a site? Those functions are rarely used for anything legitimate. And if an element breaks you could use something like shift-click to temporarily whitelist it.
Excellent guide, thanks a lot !
Apart from the lack of keyboard shortcuts, uMatrix is superior to NoScript.
Quoting the article, “Some users heralded the effort and were happy that NoScript was available for Firefox 57 and newer, others did not like the new user interface or criticized missing functionality.”
The missing functionality is what makes it far more usable for a beginner. I had tried NoScript for Firefox pre-Quantum (legacy add-on) and remember having felt submerged by the amount of settings; NoScript for Firefox 57+ may show a big loss for experienced users but for newbies as myself it has become “intellectually affordable” so to say :)
I’ve installed NoScript for Firefox last August 3rd (I kept a settings backup file so dated). It is (this time!) easily understandable (for me), excellently presented, intuitive. But in practice I realized I was always having a look when on a website on my ‘uBlock Origin’ settings (hard mode) to decide if a 3rd party website should be or not “moderated” by NoScript. I’m aware that NoScript goes further than handling only javascript authorizations yet I found it at the end to be too much of a work given its extra security when ‘uBlock Origin’ is installed. Also, this extra layer of security, should I consider using it, would be far more precisely handled with uMatrix, IMO corroborated by what I read a bit everywhere.
So no thanks, no NoScript for me at this time. But I do praise the quality of the project and the number of users is there to prove it I guess.
Former user of Noscript. Transitioned to UBlock + UMatrix and never looked back.
Same here.
Guide for NoScript on FF57+
One simple step:
– Install uMatrix
And no, I switched to uMatrix long before FF57. It’s the better and more intuitive script blocker.
It is more powerfull, you can block block on a much finer domain level, you can use filter list and much more.
It’s also on Github now! https://github.com/hackademix/noscript
.. maybe i have securtity-fatique-syndrome. i am tired of (imho) outdated “solutions” like noscript and especially the web-of-trust-bubble (a “bubble” in every sense of the word); and i am tired of broken websites. really. javascript is used excessively in times like these and that will not change in the future. conclusion: disabling javasprict per default is only a pain in the ass (if you are not a nerd resp. if you have other things to do). first of all, block cookies and site data in ff per default (whitelist: new page info – permissions). you do not need an addon for this. for tracking protection (cross-site tracking and long-term tracking) activate the killerfeature firstparty.isolate and use https://addons.mozilla.org/en-US/firefox/addon/malwarebytes/ (blocks malicious _1st party_ & 3rd party code & ads too). not to forget an _adequate_ user.pref: network.http.referer.XOriginPolicy”, 2 / network.http.referer.trimmingPolicy”, 2 / network.http.referer.XOriginTrimmingPolicy”, 2 / webgl.disabled”, true / webgl.enable-webgl2″, false / privacy.firstparty.isolate”, true / privacy.resistFingerprinting”, true / security.cert_pinning.enforcement_level”, 2 / “security.OCSP.enabled”, 0 / security.mixed_content.upgrade_display_content”, true / browser.send_pings”, false / beacon.enabled”, false / media.peerconnection.enabled”, false / dom.battery.enabled”, false / datareporting.policy.dataSubmissionEnabled”, false / … and so on. last but not least: “security” in about:preferences#privacy = everything disabled (keyword google).
I dislike NoScript with all my forces, imho it is the worst bloated extension ever made which success is coming from selling an absolute paranoia that apparently surrounds the web browsing. For my wide experience browsing everyday over dozens of differents sites for years, I can say that it is better uBlock origin with their amazing filters than this tedious and annoying Firefox extension. If you install this crap you will be its slave forever, always touching here and there and keeping an eye on it every move you make and every breath you take (yeah, like the famous song). I am a former user of NoScript and I have lost so many time setting per-site configs that it ruined entire weeks of browsing. The best moment was when uninstalled. As I said, Firefox + uBlock is one thousand times better than NoScript, the browsing is mostly 100% secure because the high wide range of protection from thousands of malware sites and so forth.
ublock origin isn’t going to speed up extremely js heavy content or stop all malicious javascript attacks
i myself was using ublock origin only 4 days ago and i was exploited by the new exploit involving windows anti-virus, and i had verycomplete, updated lists too. i ran adguard’s dns as well as pi-hole and was behind a tz205
and it still happened
if you wanna be safe, noscript is your only bet seeing as how scriptsafe has insane telemetry
Forget to mention:
It’s funny no one has ever proven the benefit of such extensions in practice. I think it’s almost impossible to compromise your computer without such extensions as someone who knows basic security stuff. Any everyone who knows about NoScript, already knows enough to safely browse the web.
There are almost no problematic sites anymore, and most just want you to download some suspiscious adware stuff or register at a suspiscious site, both of which require active behavior. The browsers are sufficiently sandboxed nowadays.
I know there are practical risks especially for tech noobs, but it’s very telling that it’s mostly just theoretical.
The web has become extremely safe. If anyone knows about practical case studies comparing extensions with no extensions and randomly browsing with the goal of attracting malware, I would love to hear about it.
@user17843
I’m sorry, as a computer security professional, I can’t just let some of this go…
“no one has ever proven the benefit of such extensions in practice”
This is simply untrue. Such extensions have provably blocked numerous attempts at malicious activities.
“I think it’s almost impossible to compromise your computer without such extensions as someone who knows basic security stuff”
This is entirely incorrect. The reality is that if your browser is allowing Javascript to execute, it’s incredibly easy for your computer to be compromised. It has happened (and still happens) even if you only browse to mainstream sites, never download anything, etc.
“There are almost no problematic sites anymore”
If anything, there are more now than ever — in part because of ad networks which can turn any website that uses them into a security threat.
“The browsers are sufficiently sandboxed nowadays.”
Sandboxing is useful, but sandboxes are not exactly airtight.
“it’s very telling that it’s mostly just theoretical.”
Except it’s not.
“The web has become extremely safe. ”
To call this statement laughably incorrect is doing a disservice. This statement is *dangerously* incorrect. The web is more dangerous than it used to be. In the past, you could largely remain safe by following simple rules (don’t go to sketchy sites, don’t download stuff, etc.). Those rules are no longer sufficient. Encouraging people to think the web is safe is, in my opinion, incredibly irresponsible.
Thanks for your reply. If the web is so unsafe, where are the studies that prove it?
Personally I know about some of the potential risks, that’s why I block most third party content. I know about the risks with Windows systems, that’s why I don’t use it, etc.
But I know enough people who don’t, and they seem to be just fine. Now, I know that people don’t necessarily know when they are being compromised, but for something that’s supposedely a real problem, things are surprisingly quiet.
20 years ago I didn’t know a family PC that wasn’t extremely slow due to all the adware and spyware that was often even automatically executed without permission. Nowadays things are a bit different. With Linux and Mac the system architecture itself prevents most compromises in the first place. Chrome as the leader in web security has additional sandboxing techniques. Nowadays there are multiple layers between personal data and the web, so often it shouldn’t even be a problem just visiting malicious sites.
But please educate me with studies that show how dangerous the web is.
The web has become very safe for the masses. Obviously there are lots of dangers, but when you look at them often it becomes obvious that human failure is involved to a high degree, and human interaction is needed, like downloading a malicious App from Google Play.
“Encouraging people to think the web is safe is, in my opinion, incredibly irresponsible.”
I don’t think its helpful to bring morality into the discussion. Of course the web is never safe, just like nothing in life is safe, no matter what you do.
“Thanks for your reply. If the web is so unsafe, where are the studies that prove it?”
Given that you’ve already made your mind up on this topic, it’s hard for me to know which studies you won’t dismiss out of hand, so I encourage you to do a web search or two yourself, so you can use the sources you trust the most. These studies are very, very easy to find. I’ll start you off with two:
https://www.symantec.com/security-center/threat-report
https://www.statista.com/statistics/494961/web-attacks-blocked-per-day-worldwide/
“Personally I know about some of the potential risks, that’s why I block most third party content.”
I’m very confused by this. You’re pooh-poohing extensions that block third party content as unnecessary, but you block third party content because you recognize that there’s a real threat there?
“But I know enough people who don’t, and they seem to be just fine”
That’s irrelevant. Most people drive cars every day and don’t get into a horrible wreck. But horrible wrecks do happen, and often enough to make wearing a seat belt a good idea.
“With Linux and Mac the system architecture itself prevents most compromises in the first place. Chrome as the leader in web security has additional sandboxing techniques.”
All of which is good, but even here you’re using qualifiers such as “most” — which indicates that you recognize that there’s a risk even with these measures.
“there are multiple layers between personal data and the web, so often it shouldn’t even be a problem just visiting malicious sites.”
This is fallacious reasoning. In fact, it’s such a common form of fallacious reasoning that it can lead directly to the counterintuitive truth that safety features can result in greater danger overall, as people tend to think that because they have safety features, they are “safe” and so they don’t have to worry about engaging in riskier behavior. See the debate about motorcycle helmets for more on this effect.
“The web has become very safe for the masses.”
I strongly disagree. If you’re accessing the web cautiously and are using a browser that provides a strong degree of protection, using the web can safer than it used to be. But it nowhere near “very safe”.
“I don’t think its helpful to bring morality into the discussion”
We must have different definitions of “morality”. I wasn’t making a moral (right/wrong) argument, I was making an argument about speaking in a responsible fashion (wise/unwise).
@John, I’m really interested and open to changing my mind.
When you read my previous comments, you see that I regard NoScript as overkill, but use uBO myself. I see uBO in easy mode as essential for the average user to protect against web based threats.
Without a content-blocker like uBO people can more easily fall victim to social engineering when users don’t know how to spot malicious sites that want them to give away their personal information or download exe files. With uBO attack surface is reduced greatly.
Afaik uBO has protected users right from the beginning against coin mining. The risk of encountering a coin-miner without using a Content-Blocker is still very small, and the process is stopped when closing the browser. The highest risk for actual infection is for uneducated mobile Android users as the risk for infection is higher with shady android apps. Lasting Coin miners affect mostly hosted servers in countries like Taiwan, India and Russia, where a lack of security best practices make it possible to combine coin-mining with system vulnerabilities and create botnets. (1) In general I regard web based coin mining more as a nuisance than as a security problem.
Everything else mentioned by Symantec – Targeted Attacks, Ransomware, Supply chain attacks are targeting vulnerabilities in old operating systems, mostly in corporate environments. These are not related to web-browsing. Android infection is a combination of uneducated users, old versions, and failure by Google to guard the App Store.
Practical web threats for average users are imho mostly phishing mails, in combination with a willingness to give away personal data or download unknown software from these mails.
(1) https://www.zdnet.com/article/a-giant-botnet-is-forcing-windows-servers-to-mine-cryptocurrency/
I agree 100%. NoScript is a product of people’s paranoia, which is seldom justified.
If you just browse the web for reading, research, consuming, finance, etc., there is absolutely no reason for something like NoScript.
It’s use has a self-therapeutic effect though, as it gives users a feeling of extreme security.
I use uBO in medium mode, and it took a while to work 100%, but even that’s already overkill. I like it though, for the benefits in performance, and as a somewhat political statement against the state of the web.
The people who create the filterlists are doing an excellent job filtering out the garbage, and the critical stuff is blocked by Google Safe Browsing.
I love the old NoScript. I hate the new NoScript.
uBlock is OK — I’d use it if I couldn’t use the old NoScript — but it doesn’t really turn my gears.
John, you’re extremely correct. The most bloated and most bothering extension out there. After all these years of development, it has become total rubbish. Meanwhile, using jus ublock origin with the appropriate filters does the job automatically for you. Less the alone the fact the web become safer day by day against NoScript.
Now that Internet will require all sites to use HTTPS will help even further. Only for half a year I used NoScript, and like you, I was spending all my time on it rather on the page itselft.