Local Sheriff reveals if sites leak personal information with third-parties
Local Sheriff is a browser extension for Google Chrome and Mozilla Firefox that reveals to you if sites you visit share or leak personal information with third-parties.
The main difference between Local Sheriff and extensions that list trackers on websites is that Local Sheriff may reveal the actual data that gets shared with third-parties.
Websites that you visit may share or leak all sorts of personal information with third-party sites that connections get established to on it.
Sites you visit may leak personal information unknowingly or knowingly. Personal information may be found in web addresses (URLs), on-page content, or as data entered in web forms. URLs may include names, email addresses, or other personal information.
The data may be shared through various automated mechanisms. Examples include through HTTPS Headers when establishing connections, using query parameters, or browser features.
Local Sheriff
Local Sheriff is available on the Chrome Web Store and on the project's GitHub page for Chrome and Firefox. The developer notes that it works in the Opera browser as well, and it may also work in other compatible browsers such as Vivaldi.
The extension requires permissions to "read and change all of your data on the websites you visit". The developer promises that the extension does not transmit any data over the Internet and that all data that is used for analysis is kept on the local system.
Since it is an open source extension, users with the right skills may parse the code to verify that.
Here is how Local Sheriff works:
Think of Local sheriff as a recon tool in your browser (WebExtension). While you normally browse the internet, Local Sheriff works in the background to empower you in identifying what data points (PII) are being shared / leaked to which all third-parties.
- The extension monitors network traffic to find information leaks. It monitors the traffic for form information, third-party resources that get loaded, URL leaks, and GET & Post requests.
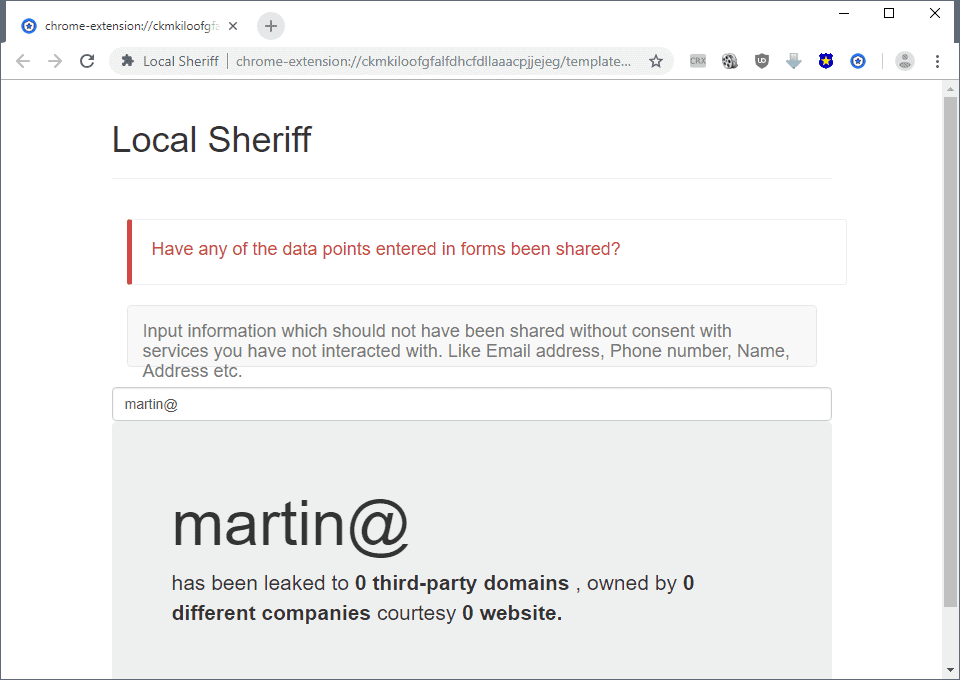
- Users of Local Sheriff can visit the control panel the extension provides at any time to enter information to find out if it has been leaked.
Just connect as you do normally to any site you visit regularly and add personal information that you don't want shared on the control panel page to find out if it has been leaked. Type email addresses, phone numbers, names, or any other personal information to find out if information is leaked.
A basic example is the following: type your email address in the control panel field and fill out a form using that email address on sites, for instance when you leave a comment or sign-up for an account.
Local Sheriff reveals to you if the data was shared with third-parties when you submit the form. The developer notes that the use of content blockers, uBlock Origin and others, may block some information leaks automatically.
Extensions like Privacy Badger, Privacy Possum, or Facebook Container for Firefox, may protect against some leaks automatically.
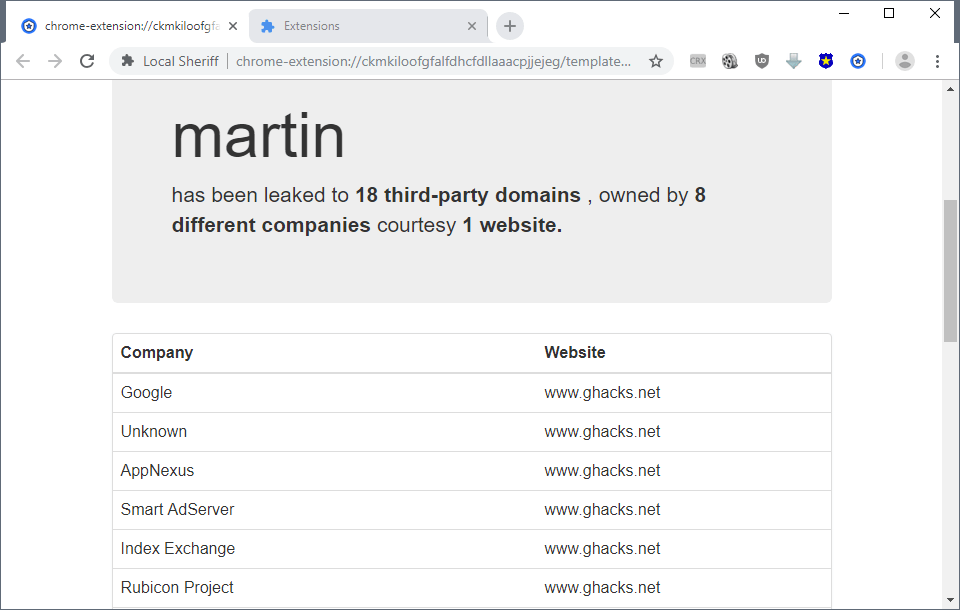
Leak information is displayed by the extension as a summary once hits are found (leaked to xx third-party domains, owned by yy different companies, courtesy of zz websites).
Each company that the entered information was leaked to is listed as well as the website. The list fills up as you use the browser like you normally would. While you may get a single site listed in the beginning you may end up with a lot of sites and even more companies that the information was leaked to after a while.
The extension displays detailed logs on the page as well. Detailed logs list all server connections made to each company information was shared with; useful to block connections or plug leaks if content blockers did not block the connections automatically.
Not all sites that are found to leak information do so willingly. Many webmasters are probably unaware of the fact considering that the leaking happens automatically on connect.
The developer of Local Sheriff has big plans for the extension. Planned features include an option to clear the data on the disk to start anew, automatically notify users when form data is shared, use additional data sources, add HAR support, and display third-party trackers that can track users across the web.
Closing Words and verdict
Local Sheriff is a well designed privacy extension for Firefox, Chrome, and compatible browsers. The current version of the extension requires that you check personal information manually against potential leaks by sites you visited which can be time consuming if you need to check multiple data sets.
Planned features to automate the process will improve the extensions usability significantly for users; this, and the other planned features would improve the extension's rating from four to five here on this site.
Now You: What is your take on Local Sheriff?


























Cliqz – ’nuff said.
cliqz, ghostery .. and now this. sorry, not for me and possibly for no one at all :) .
what happened to ghostery?
@Millenicide: https://www.burda.com/en/news/cliqz-acquires-data-protection-specialist-ghostery/
From the Github page:
“Please note Firefox will remove the extension on restart.”
So what’s the point in installing it?
Testing. Probably not yet launched on Mozilla but this is probably planned and will land on AMO eventually as well.
Just after a quick look already :
(!) Stores tons of history content (ok, locally, still not comfortable)
(!) With no option (yet ?) to clear that data
(!) “As soons as Local Sheriff detects that a URL has been shared with a third-party, it issues an anonymous GET request to that page again to simulate what information can be accessed only based on the URL without user-cookies, session etc.” what ?
(!!) not on AMO
(!!!) very suspect install procedure on firefox
(!!!!!!!#%&@) made by Cliqz, the spyware company
You’ll have to shoot me before that gets installed on my browser
https://en.wikipedia.org/wiki/Cliqz
“Cliqz is majority-owned by Hubert Burda Media. In August 2016, Mozilla, developer of Firefox, made a minority investment in Cliqz. Cliqz plans to eventually monetize the software through a program known as Cliqz Offers, which will deliver sponsored offers to users based on their interests and browsing history. However, these recommendations will be processed locally based on a remote repository of offers, with no personally identifiable data sent to remote servers. On 15 February 2017, Cliqz International GmbH, a wholly owned subsidiary of Cliqz GmbH, acquired the privacy-oriented browser extension Ghostery.”
https://en.wikipedia.org/wiki/Hubert_Burda_Media
The company rose to some prominence in Nazi Germany, where it benefited from “Aryanization” of Jewish property under the leadership of the founder’s son Franz Burda and specialized in printing maps for the Wehrmacht. Franz Burda was a member of the Nazi Party and an avid Antisemite. In 1986, the corporate group was divided up between Franz, Frieder and Hubert Burda…
Cliqz is blocked by my hosts file (my personal ‘local sheriff’).
Could you elaborate on how you blocked Cliqz?
My answers was censored above (first post removed and the second truncated).
Please no Nazi references here on the site. I removed your first comment because nazi.com is obviously not the host that you should block when you want to block Cliqz.
It was not a reference at all.
it’s news that guides me: the German multinational Bayer buying Monsanto.. is it a kind company that wants to make apologize wanting to improve its image (like Burga)?, kindly wanting to treat people with its medicine? or it’s to continue to massacre humans and animals by millions for money like as they have already participated inventing the gaz moutarde, Zyklon B, tabun etc etc etc etc etc.. or even having made women trafficking in Auschwitz. Its medicine like the glyphosate etc? Of course nazis and co are still there, everywhere.. also under deceptive appearances that you do not even imagine. And what about Nestlé buying/annexing French lands in secret like Poutine in Crimée to make them Swiss/German forever? Like with Volkswagen, The Motor of the Europe is still infected. I read somewhere on gHacks something like a company based on Germany like Cliqz can not be naughty due to the German laws, one of the best laws concerning privacy. Probably the reason why German companies are always sentenced by the courts of foreign countries, most of the time by the United States like with Bayer/Monsanto.