Microsoft reveals InPrivate Desktop sandbox feature for Windows 10
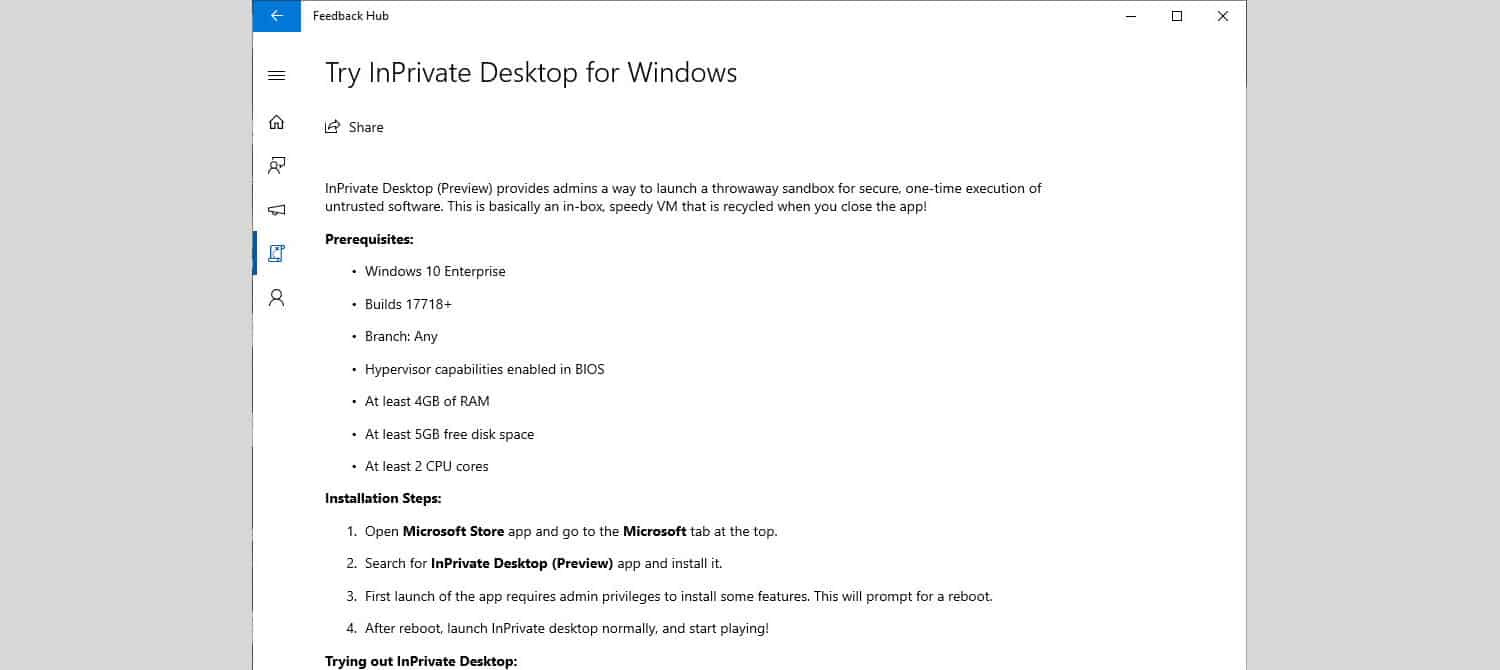
Microsoft revealed a feature that it calls InPrivate Desktop last week on the Windows 10 Insider Feedback Hub before it pulled the quest quickly again.
Bleeping Computer was fast enough to grab a screenshot of the quest and collect the information that Microsoft provided.
The description indicates that the feature is for Windows 10 Enterprise at this point in time. It would not be the first that is Enterprise-exclusive but it has happened in the past that Enterprise-only features were introduced at least in professional versions of Windows 10 such as Pro as well at a later point in time.
The quest had the following description:
InPrivate Desktop (Preview) provides admins a way to launch a throwaway sandbox for secure, one-time execution of untrusted software. This is basically an in-box, speedy VM that is recycled when you close the app!
Microsoft published prerequisites and installation steps as well. The feature requires a Windows 10 Enterprise installation, at least build 17718, Hypervisor capabilities enabled in the BIOS, at least 4 Gigabytes of RAM and 5 Gigabytes of disk space, and a processor with at least two cores.
InPrivate Desktop allows administrators to run untrusted executable programs in a sandbox so that the underlying system cannot be affected in any way by the execution. Similarly to what third-party programs such as Sandboxie offer but integrated natively in Windows 10.
Admins can make use of virtualization to test untrusted executable files but that requires more storage space and resources.
The quest was live for just a brief moment before it was pulled by Microsoft again. It is possible that it was published in error by Microsoft at this point in time.
The quest pointed to the InPrivate Desktop application but Bleeping Computer could not install the application because it had other requirements (Azure Active Directory) and blocked access because of that.
Closing Words
The integration of a quick and easy way to test software in a sandbox environment could certainly help improve overall security. It is a pity that Microsoft seems to target Windows 10 Enterprise exclusively with the feature as it would certainly help non-Enterprise customers of the company as well test and run software programs in a secure environment.
Now You: What is your take on InPrivate Desktop?















Acronis True Image 2013 had already a similar feature called Try&Decide.
That is some 5 (five) years ago.
This is great news. Putting it in the Enterprise edition makes a lot of sense.
You don’t want the amateurs tripping around blaming Microsoft for their self-inflicted injuries.
Add to it the high level of expertise Microsoft has developed in threat abatement and this approach can prevent a lot of problems.
I run my email client in a sandbox. We should be working toward that in the enterprise to limit exposure.
Kudos to Microsoft.
Does it block microsoft spying and private information theft.
Windows 10 is untrusted software for me. Too bad the sandbox can’t be used to run it too.
Interesting concept. But until we see the product and the specs, it’s impossible to pass judgement.
Being somewhat paranoid about Microsoft these days, I would want to know the extent to which the proposed sandbox is isolated from Microsoft’s extensive and complex telemetry. Some may use the sandbox to test malware – but others might be using it to temporarily shelter product innovation or truly private data. I would want to know if Microsoft’s proprietary sandbox can “phone home”.
“Similarly to what third-party programs such as Sandboxie offer but integrated natively in Windows 10.”
I have real problems trusting anything that is integrated natively in Windows 10.
Should be possible to reboot in this mode .
Lots of software require a reboot for functioning , so if you can not reboot in this “sandbox-mode” , its useless……….
The note to reboot was in the installation section, so there’s a good chance that Store app is essentially enabling a form of Hyper-V, very much like enabling Hyper-V the normal way would.
If so, this means you’d be precluded from using something like VirtualBox or VMWare, which install their own hypervisors. That would be too bad, because it would be nice to have one of those AND this.
And I’m not sure how “speedy” the whole thing can be with whopping requirements (to run an app, remember) of 4 Gigabytes of RAM and 5 Gigabytes of disk space. That’s about enough to accommodate a stripped-down Win10.
We don’t know much about this mode and how it works. Might take weeks or months before it comes back up.