How to change Firefox's Sandbox security level
One of the major improvements that comes along with Firefox's new multi-process architecture is sandboxing to improve the browser's security.
The multi-process rollout is chugging along nicely, but it will still take at least months before it is enabled by default for all, or at least the majority, of Firefox Stable users.
Electrolysis, Firefox's multi-process architecture, is the prerequisite for Firefox's sandboxing feature as it makes use of child processes to establish security boundaries.
Instead of executing all code in the parent process, code is executed in a content process instead limiting what it can do.
Firefox's sandboxing model supports different levels which determine what code executed in the sandbox is allowed to do.
Mozilla implemented three levels currently, and plans to add additional levels with higher security restrictions later on.
The operating system and the Firefox channel depend what is implemented currently. Here is a brief overview of the current status:
- All: Gecko Media Plugin enabled.
- Windows: NPAPI plugin enabled, content at level 2 in Nightly, at level 1 for other channels, compositor at level 0.
- OSX: content at level 2 in Nightly, at level 1 in Aurora, rest nothing.
- Linux: content at level 2 in Nightly, rest nothing
The next target for Windows is level 3 sandboxing, for OSX level 2 sandboxing, and for Linux level 1 sandboxing.
Sandbox levels
Note: There is usually little need to change the sandbox level, and it is best kept at the default level. While reducing the level should not have any ill-effects on the browser -- besides less security obviously -- increasing the level may cause all kinds of issues.
Sandbox levels get more restrictive the higher they are. Level 0 is the least restrictive level, level 2 the most restrictive currently. Once level 3 is introduced, it will become the most restrictive level available.
Level 3 will be implemented in Firefox for Windows first, and later on in Firefox for OSX and Linux.
You can check the restrictions of each sandbox level on the Mozilla Wiki site. Please note that sandboxing in Firefox is a work in progress. Things may change along the way, but the wiki will get updated when that happens.
Check Firefox's sandbox level

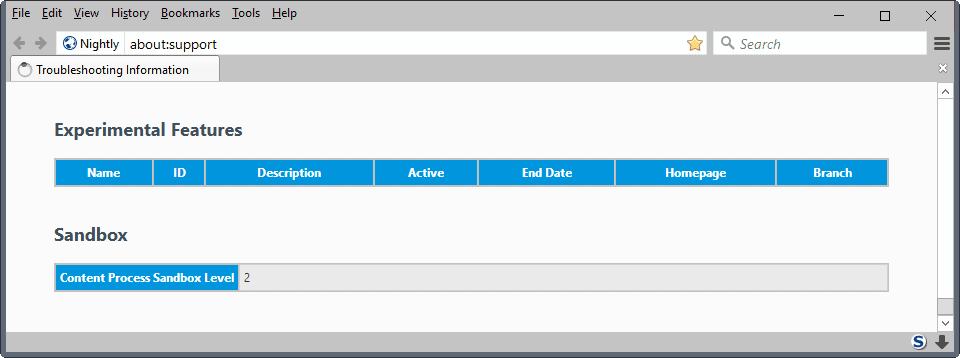
Mozilla Firefox lists the sandbox level that is used by the browser in two locations in the interface. You can load about:support and scroll all the way done until you reach the sandbox listing on the page.
Check the "content process sandbox level" value to find out.
The second option that you have is to load about:config, and search for the parameter security.sandbox.content.level. The value that is returned is the current content level of the Firefox sandbox.
Change the Firefox sandbox content level
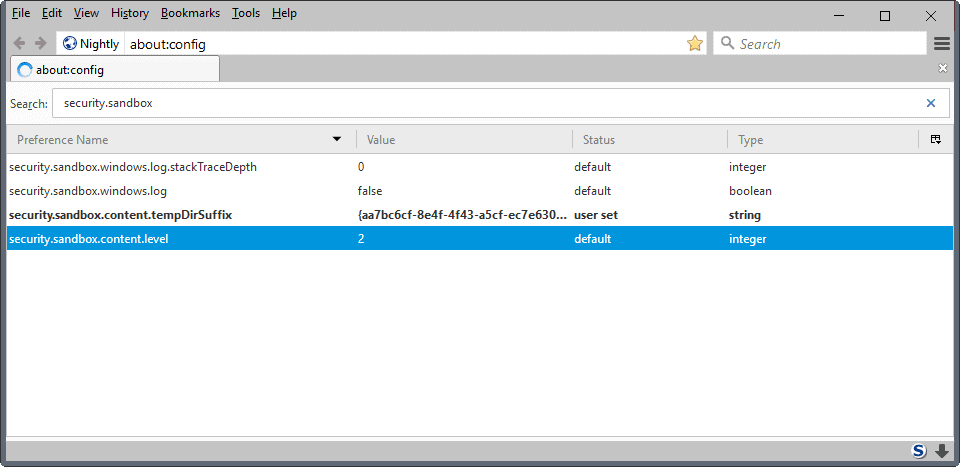
The parameter security.sandbox.content.level determines the level of the sandbox. You may use it to change the level, but only to a value that is supported.
If you pick a lower value, some sandbox restrictions may be lifted, if you pick a higher value -- provided that it is supported -- the sandbox may be more restrictive than it was.
To change the sandbox level of NPAPI plugins, search for the preference dom.ipc.plugins.sandbox-level.flash or dom.ipc.plugins.sandbox-level.default instead.
Closing Words
The next big milestones for Firefox's sandbox feature land in Firefox 53 for Linux, and Firefox 54 for Windows and Mac versions of the browser if the schedule holds.
Now You: What are your expectations for the feature?






















Software development generally lacks discipline. That is why all software companies should be seriously confronted and held accountable by the general public. When it takes 15 years to get something right or secure, that’s bad and it is because software is being developed too quickly while the emphasis is on wild features instead of a solid time-tested foundation. The general public needs to be educated to start demanding reliability, security, and privacy instead of fancy features. Eighty percent of all software teams could not make it in the hardware development world, where things literally have to be done right the first time. A majority of time is spent coding when the majority of time should be in analysis and design. If this mini lecture helps enlighten you at all then spread the word tell people to demand reliability, security and privacy not fancy features. “Rapid Release” — riiiight — that is the OPPOSITE of the way to develop software. You don’t see any “Rapid Release” motherboards on the market, at least not reliable ones.
Thanks for the warning against changing Firefox’s sandbox level! I’d rather wait for an update that risk breaking the browser or weakening security.
https://www.reddit.com/r/firefox/comments/5fs19b/has_anyone_changed_their_sandbox_level/daml6q4/
Each level cumulatively adds more features to the sandbox.
I would strongly advise you to leave this pref as the default, for a very good reason: We only enable a particular sandbox level by default once the rest of Firefox is compatible with it.
If we are not yet shipping that level by default yet, then manually turning up that level will break various parts of your browser. The pref exists so that it is easy for developers and testers to try things out and file bugs, but that setting should not be used for your day-to-day browser profile.
https://wiki.mozilla.org/Sandbox
That reddit comment was written by me, FWIW
I am a developer who works on sandboxing at Mozilla. I STRONGLY RECOMMEND AGAINST tampering with the sandboxing level!
We only enable a particular sandbox level by default once the rest of Firefox is compatible with it.
If we are not yet shipping that level by default yet, then manually turning up that level will break various parts of your browser. The pref exists so that it is easy for developers and testers to try things out and file bugs, but that setting should not be used for your day-to-day browser profile.
@Aaron Klotz waterfox disables dom.ipc.plugins.sandbox-level.flash is this safe https://github.com/MrAlex94/Waterfox/blob/master/browser/app/profile/firefox.js#L968 this has been done for many many versions and previously changed other settings similar to this lowering security. my question is does it make the browser less secure with flash content then firefox.
this is not the only time security settings have been turned off or disabled in waterfox by the developer
Is it the same for first-party isolation or TLS 1.3 ? Can force-enabling these features that are not ready actually be counterproductive, reducing security ?
I think there’s a lesson to be taught here. There is such a thing as pref footguns.
Thanks. That will allow me to show more certainty when giving that advice to adventurous users :)
I don’t work on those features so I cannot comment specifically on them.
However, in general it is advisable to treat any prefs for yet-to-be-released features as potential footguns. We know our users want those features ASAP, but when those features’ prefs are not yet defaulted on the “on” setting, it is because they are not yet ready for day-to-day use.
Thanks for the information
> Didn’t Mozilla say people with any add-on represented 40% of Firefox’s user base ? So the majority of Firefox stable users has had multi-process since September 2016, no?
No, since there are more criterias than add-ons. Firefox in a RTL language + e10s needs Firefox 50 on Windows and macOS, Firefox 52 on Linux. Firefox + a11y tools or touchscreens + e10s needs Firefox 53. The russian version of Firefox needs to be 51 or higher for e10s.
Thanks. Just for kicks, trying to guess from your new data.
We have
– 95% of Firefox users on Windows
– RTL is e10s enabled since Firefox 50
– Linux, a11y and touchscreens represent low percentages
– Russia represents some
– 40% of people don’t have add-ons
– Let’s say 50% of people with add-ons, could have e10s enabled on non-russian Windows or Mac Firefox 50
– Firefox 50.x should represent only a portion of all Firefox used, like 70% maybe.
With all of this, I would guesstimate that slightly more than 50% of all up-to-date Firefox users may have e10s enabled. So, slightly less than 50% of Firefox users regardless of version.
I wish I could see actual numbers to see if I guessed right :)
I have a few more numbers. ;)
> Russia represents some
The russian version represents five percent of the e10s population according to Mozilla (I don’t remember the source, could be a Bugzilla ticket or a Wiki page).
> With all of this, I would guesstimate that slightly more than 50% of all up-to-date Firefox users may have e10s enabled.
According to the newest article on the Firefox Nightly blog “more than 50%” of the users of the release channel will have e10s activated in Firefox 51.
I’m always weary playing with defaults like these. I would not dare to disable certain crypto algorithms for example, and same goes for alpha quality features. Enabling sandbox level 2 may make certain function calls fail in Firefox Stable, for all I know, leading to undetectable problems that could maybe, who knows, actually weaken security. I’m going to wait for Mozilla to decide level 2 is ready for release, but YMMV!
“The multi-process rollout is chugging along nicely, but it will still take at least months before it is enabled by default for all, or at least the majority, of Firefox Stable users.”
Didn’t Mozilla say people with any add-on represented 40% of Firefox’s user base ? So the majority of Firefox stable users has had multi-process since September 2016, no ? And since Firefox 50 something like 50% of the add-on users have had multi-process enabled, didn’t they ? Many numbers I give here are made up off hand from a hazy memory, except the 40% thing, so this comment is all a question, not an affirmation.
I understand that more content processes are to be enabled later on, but multi-process itself is already there for most users, that was my understanding so far :)
Mine was at level 1 and I changed it to level 2… What issues should I expect? Any idea?