Mozilla adds NPAPI plug-in sandbox to Firefox
Sandboxing finally comes to the Firefox web browser. After enabling a (currently) non-restrictive content sandbox in Firefox Nightly last month, the organization enabled the upcoming NPAPI plug-in sandbox in Aurora and Nightly versions of the browser as well.
These sandboxes are designed to limit the rights of tabs and plug-ins in the browser to harden and stabilize it.
The plug-in sandbox is deactivated by default and needs to be enabled by the user before it becomes available.
It is sandboxing all browser plug-ins by default when enabled, but there is also an option to enable it only for select plug-ins.
Note: NPAPI plugin sandboxing is enabled by default on Windows in newer versions of Firefox.
Enable the plug-in sandbox
To enable the plug-in sandbox in Firefox do the following:
- Type about:config in the address bar and hit enter.
- Confirm you will be careful if the prompt appears.
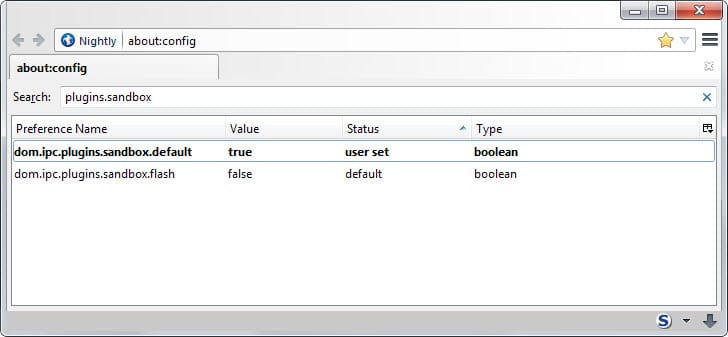
- Search for dom.ipc.plugins.sandbox.default.
- Double-click the name to change its value from false to true.
Enable the sandbox for individual plug-ins
If you don't want to enable the sandbox for all plug-ins, for instance because you noticed issues with some after doing so, you can enable it for specific plug-ins instead.
The preference dom.ipc.plugins.sandbox.flash handles the sandbox for Adobe Flash. You can set it to true (without touching dom.ipc.plugins.sandbox.default to enable the plug-in sandbox for the Flash plug-in in Firefox.
The preference does not exist for all other plug-ins in Firefox. To enable the sandbox for one of those, create a new preference in the browser and name it dom.ipc.plugins.sandbox.<plugin-nice-filename>.
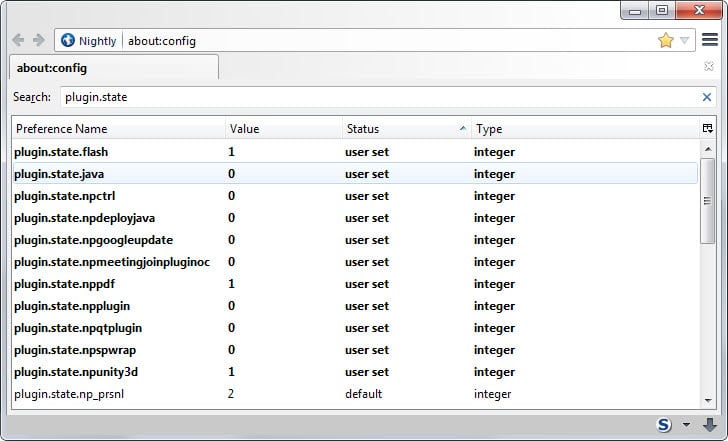
The easiest way to look up <plugin-nice-filename> is to search for plugin.state while you are on the about:config page as it lists all installed plugins and the name that you need to use for the feature.
When you browse the plugin related preferences on the page, you may also notice that Flash Protected Mode is disabled by default in Firefox Nightly and Aurora.
It has been the cause for Flash related issues in Firefox ever since it was introduced by Adobe and Mozilla hopes that the browser's own sandbox and disabling Protected Mode at the same time makes those issues a thing of the past.
The plug-in sandbox, just like the tab sandbox, is not as restrictive yet as Mozilla wants it to be. It is interesting to note however that the plug-in sandbox is not relying on Firefox's multi-process architecture Electrolysis e10s. (via Sören Hentzschel)





















@testuser, I dunno about average users, for the most part I agree that security conscious professionals are immune to widespread malware outbreaks. However, we have seen professionals compromised. Like how the Facebook engineers fell victim to a watering hole malware trap a while back. Also sometimes especially with writing software you need the “direct” access to fully debug program and features, thus isolation tricks like virtual machines or sandboxie aren’t always applicable.
With all these singular new functions I wonder sometimes if users are not becoming unwillingly beta-testers, and I’m referring to stable releases. I do understand that everything is done to increase speed and security but is it done or attempted?
I remain nevertheless a Firefoxer, and happy as. Perfection is not of this world.
New functions are incubated in the Nightly often for a very long time before they get anywhere near the stables. The more complicated the features is, the more likely it will stay in the test channels for polish. It isn’t perfect, you can’t completely replicate in the test channels the number and diversity of users using the stable releases, so sometimes issues pop up that don’t show up with users in the test channels, but I think its the best anyone can do.
For this feature though, it can’t show up fast enough. For example, right now there security alert with Adobe Flash, there is a dangerous zero day exploit causing all type of mischief that won’t be patched until next week by Adobe. Chrome isn’t affected b/c it sandboxes its own flash.
That’s why I’m (also) using Sandboxie under Windows. And there are also “things” like virtual machines as well, so it’s mainly a threat for the average user. Isn’t it?
This can’t be implemented soon enough into regular Firefox. I just hope that it isn’t buggy when it happens.
I’ve just discovered your blog All Things Firefox. Seems interesting.
Thank you.
Wow, sounds like they did this perfectly. Firefox FTW :-)
Just a note: e10s disables itself if you have a touch screen monitor. They are working on a fix for this.