Android malware campaign hijacks more than 1 million Google accounts
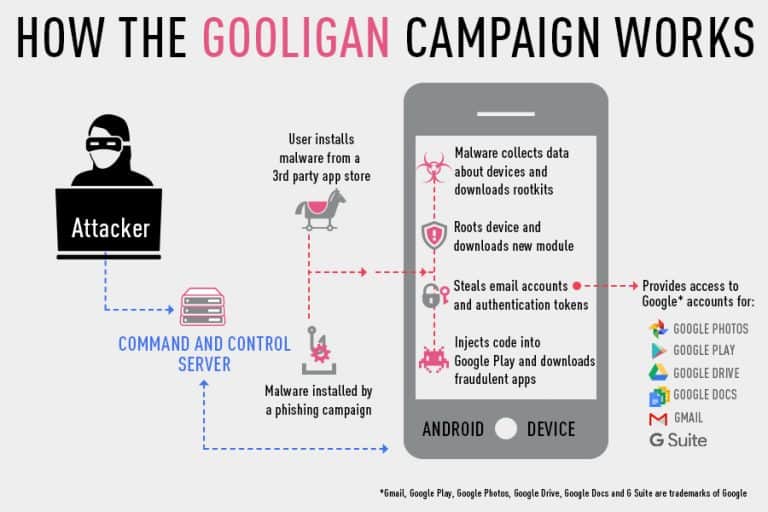
A new malware campaign, dubbed Gooligan by Check Point, has successfully breached more than 1 million Google accounts up to this point according to the company.
About 13,000 new devices are breached every day by the malware campaign. According to Check Point's research, Android 4 and 5 are the main target of the attack which account for a little bit less than 75% of all Android devices out there.
The breach starts with the download of an infected application. Apps like WiFi enhancer, Perfect Cleaner, or Memory Booster are but some of the apps that are infected by Gooligan.
These applications are usually not offered on Google Play, but on third-party application stores or direct links on websites, in emails or messages.

When an infected app is installed on the device, it tries to communicate with a command and control server. It sends data about the device to the server, and gets a rootkit from the server in return. This rootkit exploits several vulnerabilities in Android 4 and 5.
The main issue here is that while patches are available, they may not be available for all devices, or may not have been installed by the user.
The rooting, if successful, gives the attacker full control of the device. Gooligan downloads a new module from the server and installs it on the device. This module is designed to avoid detection by Google Play or Google Mobile Services.
This module, according to Check Point, allows the attacker to steal the user's Google email account and authentication token, install apps from Google Play, and rate these apps, install adware on the device to generate revenue.
One common method of earning revenue on breached phones is to get paid for application installations. Since this is not a issue if the system is under full control, this is one of the easier ways for attackers to make money.
Is your device infected?
Check Point created an online tool that you may use to find out whether your Google account has been breached.
All you need to do is visit the website linked above, enter your Google email address in the form, solve the captcha, and hit the check button afterwards.
If your account has been breached, you need to perform the following operations immediately:
- Do a clean installation of the mobile operating system on your device. How this is done varies but you may find help either on your mobile phone provider's support site, or at the device's manufacturer's site. Either way, you need to flash a clean image to the device. If you have a backup, that is probably your best option provided that it is clean.
- Once done, change your Google account password immediately. You may also want to clean up any comments or ratings left in your name. You can do so on the Google Play website.
Now You: Has your device been affected by Gooligan?





















I won’t check my e-mail. I think I’m safe though. While I keep Google’s application scaning disabled, I’m running CyanogenMod13 (Marshmallow), no shady applications installed, ever, nothing suspicious in background, no ads, no battery drain, etc.. Checking battery usage, my phone indicates that it’s always sleeping while I’m not using it, so I think I’m safe.
Sounds tricky…
How Check Point, (honestly, this is the first time I am seeing its name around) can find out whether the EMail address (wait, “EMail address can be infected?) is effected?
Sorry but I think this is something done by that “Check Point” to promote their products…:)
Because those email address/passwords are sold on the Darknet and leaked so before deleting them from website like Pastebin those companies put all emails address in a database where you can check if your email was in the one’s that have been hacked.
It exist multiple databases for other exploit where the email/password were leaked and you can check if you were attacked.
I don’t use Google account with my Android phone. In other words, my phone is not attached to any account. I have disabled all Google apps, even Play Store. I have disabled all Android system updates, all automatic updates.
I use my phone the same way as my desktop PC.
-I sideload apps. It’s obvious that most apps on the internet are fake adwares, viruses, but I always recognize them. Same as if you want to download pirated programs for PC, all download sites offer fake download buttons, fake .exe files, but I can recognize all of them too. Plus I use VirusTotal.
-I log in into my accounts ony in the Firefox for Android browser and only if I want do do something. I always log out when I don’t use it. I also have Ublock Origin.
The bloatwares waste the battery lifespan and flash memory lifespan. Because I disabled all bloatwares (Google apps and most stock apps), my phone has better battery life and better gaming performance. I hate when my phone or my PC is working pointlessly because a program is running in the background without my will or command.
I’m not an expert on Android, but I understand it’s based on Linux. So I can’t understand why updates seem to be so problematic. I certainly think we’re entitled to be cynical about manufacturers who cram our devices with rubbish we don’t want but claim that something we do want like regular updating is unviable. Suggestions that we all replace perfectly workable hardware make me even more cynical.
I own an 8″ Lenovo tablet, barely a year old – still on Lollipop and no update on the horizon.
My wife owns an almost identical 10″ model which – with Nougat just out – has only within the last couple of weeks been updated to … Marshmallow!
My son runs a 2-year old Asus tablet – no update at all since Kitkat!
I asked around my neighbours about which Android version they’re running – most had not the slightest idea.
When I do come to replacing my devices, I’ll be thinking hard about Android in general and which brand names I’ll be considering in particular. Never have cared for Apple stuff, so I might just find that the latest thing to become incompatible with portable devices is – me!
I would have suggested that manufacturers start thinking hard about well know phrases like ‘goose’ and ‘golden egg’ – but then again why should they when there are such huge numbers of people daft enough to queue outside shops whenever someone produces a device half a millimeter thinner than the last one.
Don’t shoot me but wouldn’t it make sense to have a Win8 or Win10 phone from MS ? I know there are not too many apps but looking at Google’s store and all of its childish, colorful junk it may make sense if you are not a gamer, etc and just use the phone for basic stuff like email, texting or a little browsing (not watching movies). Thank you all for allowing me to stay alive.
A couple of years back I read somewhere about two Chinese companies that were working on linux smartphones.
Not any update after that… And when I ask at a shop, they stare at me like a cow at spanish clover. They only know that android.
As that android is said to basically be linux with a lot of that google dirt thrown upon it, and linux is said to be relatively safe, why is it so difficult to find a clean linux-only phone without all that extra dirt… ?
Why are all these developers (both hardware and software developers) so brainwashed that they only follow the google path and don’t even see options and needs (facilities, safety) to the side of that ?
fena: FDroid, Aptoide. ** Usual precautions apply**, have Malwarebytes installed, and an AV doesn’t hurt. Only ever had 1 problem, and Malwarebytes picked it up immediately after update, so I deleted it. (Scan afterwards was clean). RA Blocker is a very good app. (Remote Access Blocker) for blocking camera and microphone, also check out SMS blockers, etc. FDroid is an open source repository. Best is to have a few, trusted, well known apps with Android, anyway. (Not lots), eg, no ‘cleaners’, ‘memory enhancers’, etc. Also, games. (Paranoid?). :)
Some of us have android but do not have google or amazon accounts so we do not use the “stores”. Out alternative is to get from other sources. I use apkmirror. Is there a safe alternative to the “stores” ?
@fena : I am one of those. For the few apps that I wanted and that were only on that dreaded Google Play, I emailed to the developer, and they were so kind to send me the apk by email. One even followed my suggestion and put them on his own website for direct download.
On Android, one is only moderately safe if one buys the latest flagship EVERY YEAR. Even then you’re not even sure to get the latest Android version. Stay away from the midrange models, the manufacturers blatantly and shamelessly lie about future updates for them. Samsung is the biggest liar of them all. Since Lenovo bought Motorola, they come in as second master liars. Android is a big mess, security-wise.
If you try out some good custom roms for your phone, then you do not need to switch to a better model.
@Rocky:
Yes, the privacy/security risks with normal consumer Android devices seem intolerable.
Even clean, reputable apps are very intrusive. The app “permissions” problem, for example — apps routinely harvesting your personal data … ID, phone numbers, photos, contacts, etc.
Of course, getting OS updates (especially security updates) is a huge problem.
Wonder why some enterprising company has not come up with a basic Android device without the usual non-removable adware/junkware/spyware… one with full user control of app permissions… and one with a reliable OS update cycle ??
The more I read about the updating problems in Android the more I would wonder about its future ?
Needs to be noted that most people don’t install random or unknown apps on a whim. Most use Google’s Play Store, some use Amazon’s app store. Side-loading of apps is generally frowned upon, and best left for those who are more smartphone savvy. There are some markets where the Play Store is not allowed but those are also areas where something piracy and exploits are the norm, and something like Gooligan is just a drop in a bucket.
The tech media frenzy on this is more click-bait, less substance. It’s a nasty exploit but it affects only a specific group of people, those who ignore the warnings that pop up on their phones when they intentionally try to bypass stated safety measures. As for the number of allegedly infected phones, when the real stats come out, by independent sources, the real numbers and facts will just be old news.