Private Internet Access rubyw.exe connections explained
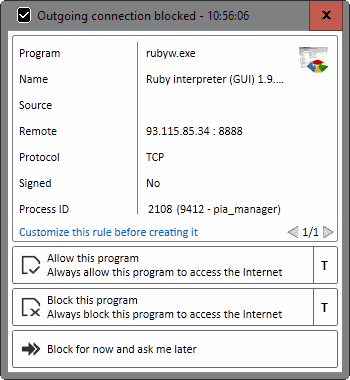
If you are using the popular VPN service Private Internet Access (PIA) and monitor outgoing network connections on your devices, you may have noticed that the program rubyw.exe attempts to connect to various Internet servers when you initiate the VPN connection to Private Internet Access.
This happens only if you are using the PIA software and not if you have configured connections to the service manually or in third-party network software.
Private Internet Access is a very popular VPN service thanks to anonymous payment options, unlimited bandwidth, impressive number of worldwide services, no traffic logging policy and advanced features such as a kill switch to drop the Internet connection when the connection to the VPN drops.
If you monitor the outgoing connections on the device you will notice that rubyw.exe connect to various remote Internet hosts under the process ID pia_manager, which is the main process of the Private Internet Access application.

The program connects to several remote hosts in a matter of seconds. Blocking the connections does not seem to have any impact on the functionality of the virtual private network connection.
First, let's talk about the connection between rubyw.exe and pia_manager.exe. Rubyw.exe is the Windows Ruby interpreter, a program that Private Internet Access uses to run its software.
Rubyw.exe is the windows ruby interpreter, and our software, runs as a packaged copy of our script + all required gems + the executable. It bootstraps from the executable, extracts a copy of ruby and all gems needed to run.
The reason why the software is initiating all these outbound connections on start is that it pings PIA servers to check availability, reliability and speed.
Since you can only select a location you want to connect to when using Private Internet Access' software, it is up to the program to find a suitable server in that region, and that is the reason why the connections are being made when you start the PIA software.
If you check the IP addresses that are contacted on start of the VPN connection, you may notice that some are apparently not owned by Private Internet Access while most are.
This is caused by rDNS (meaning remote DNS) errors according to a Private Internet Access representative.
Your application is doing a rDNS lookup, and like a phone book, rDNS has to be updated, we keep ours updated to be reasonable, and to help disguise some of the connections, if you can run this without any access to rDNS, or nameserver lookups, you'll likely see that all of these are to PIA IP addresses.
While you can block the connections from being made, you may be connected to a less-than-ideal server as the program has no way of determining a suitable server in regards to speed and reliability.
Now You: Do you monitor outbound connections on your devices?

















Much of your explanation directly quotes Alex from this page, which was posted years earlier. You should credit the source of your info. https://www.privateinternetaccess.com/forum/discussion/790/questions-regarding-the-backround-network-scans-of-rubyw-exe
https://screenshots.firefox.com/j9eQ15VNcjrReBv8/www.privateinternetaccess.com
Some might be interested in the out of country VPN services however a little warning for you. No VPN will protect you if someone really wants to find out what you are doing. As well, some of the VPN services that are out of country are run by the intelligence agencies or intelligence agencies have a back door into some of them. Really be aware that anything you do online unless you are really skilled is traceable back to you. Even if you are really skilled you can be found by someone better than you.
I agree with Olaf 100%. As well, it all depends on what kind of tin foil your hat is made out of. The majority of people will never have an issue, unless you are a really naughty person, then it really does not matter what you are doing on the net. No one cares. No one.
This is the net……..and called that for a reason…everything is captured, recorded and caught inside its own net. You are using a service and agree through them the TOS. You can try everything in the world to hide or block your existence….but unfortunately, your existence is there…..and tracks are left behind. Always!
>>> Dont forgot, pia is a US-based vpn service
I’m really not a big fan of PIA, because their IPs seem to be easily blacklisted due to the overly paranoid anonymous setting(as their VPNs only have one IP per server!!) and don’t seem to actively work to lift the blocks.
But, I don’t understand why some people believe this kind of BS.
How could you trust offshore shell companies run by those that nobody knows who are over a US-based company with an ABA-certified privacy advocate attorney as a full time member and a strong tie with privacy advocate groups like EFF.
I’m sure the Feds didn’t go further in the case John Smith mentioned because PIA were well-prepared in case this was to happen, having a full-time company attorney and building strong relationships with privacy advocate communities, which, IMO, all professional VPN providers should do.
I think many of those spreading such FUD as above and attacking major VPN providers’ LEGAL marketing efforts like the affiliate programs are VPN providers running by those who want to make easy money by just renting cheap VPS servers and installing default OpenVPN on them(Rolling out our own VPN is not so hard. So, if they don’t do things like what PIA does, what for do you pay?)!
They are doing such foul play because they can’t afford what they should do!
Yeah, the US has the Patriot Act, FISA, and Prizm, but I don’t understand why this makes you beleve offshore VPN providers are safer than US ones.
The NSA and CIA are intelligence agencies and so they don’t care jurisdiction. The FBI can operate outside the US.(You guys must be familiar with Kim.com or Operation D-Elite, right?). I don’t remember
Also, most of VPN providers that betrayed our trust, which disappeared with users’ money, which monitored users’ activities without a court order, and which leaked users’ info to the police were offshore providers(XeroBank, FindNot/Procy.sh, EarthVPN).
I don’t recall any US provider that did such things. (Well,HMA? but it is UK-based…)
BTW, do you really think those offshore shell companies will protect you when they get raided? Without a lawyer? I don’t think so!
I doublt they even have an intention to keep their TOSs or PPs. Even if they break them, what can you do? Sue them? But how? How can you catch them? Where can you find them?
In any event, after ‘Panama Paper’ leaks, offshore shell companies are getting a lot of attention. So, how could you still say offshore VPN providers are safer than US providers now?
BTW, I remember the FUD was exactly what Xerobank, FindNot, Proxy.sh and EarthVPN were advertising!
Actually I do have one problem with PIA’s rubyw.exe. It is that everytime you start PIA VPN, PIA will automatically compile a brand new copy of rubyw.exe, and run this from within a newly generated and unique (randomly named) subfolder in {sysroot}:\Users\{username}\AppData\Local\Temp\.
The reasons for this behavior are not quite clear to me, but the consequence is that it’s next to impossible to whitelist rubyw.exe as a trusted program in firewalls. Because everytime it’s a “new” rubyw.exe in a different folder! So in other words, everytime I start PIA VPN, I will get firewall popup warnings about this “new instance” of rubyw.exe trying to access the internet. And because it’s about a different folder location every time, I can’t whitelist it to stop such warnings.
Also, PIA doesn’t clean up very well after its back. Right now in that Appdata\Local\Temp location on my PC I have 18 (eighteen) totally similar folders from past PIA sessions, each one containing its own rubyw.exe and a whole slew of associated files (like the inevitable ssleay32.dll). Everything looks identical in each of those 18 remaining folders. Only the different file creation dates and times give away the exact times when I started a new PIA session…
Let me tell you, if I ever were to give my students a programming course, I might very well show this as a typical example of “sloppy implementation”.
For the rest I have no complaints about PIA as a VPN service, though. It works great and fast. And as for that dubious story about the FBI, in fact those “fedz” do scare me less than Microsoft’s and Google’s data harvesting practices do scare me right now!
@Hank
” in fact those “fedz” do scare me less than Microsoft’s and Google’s data harvesting practices do scare me right now!”
Agreed. I use PIA. I’m neither a terrorist nor a pedo so I have little concern about the NSA or FBI in terms of how they may approach PIA in regards to my info (which I do NOT believe they actually log). I am much more concerned with general web privacy re: all the trackers and big corporations and their spying.
Thumbs up for PIA from me. It has been superb so far, and the speed difference is negligible if detectable at all.
I use Comodo Firewall with Custom rulset.
I think it’s depending, if I see as an provider someone would abuse my service for illegal stuff I would also start to logg him and only him, in case someone want to contact me or I should pay for him. It’s your right, but to promise to not keep any logs is always strange because this usually needs to require that you re-write the entire backend, because every backend comes with logging by default. Same as every CMS, so if everyone wants to tell me nothing will be logged how they ban such abuse user? Then it requires again time to re-write, knowledge and other fingerprint mechanism.
It’s difficut in my entire time I only know about one board which truelly never logged something, it was the old gulli.de board which banned users only via username. And the admin said many times it was written by himself. So I highly doubt no one logs not strange traffic if he/she see that there is a lot of more traffic then on every other connection. it’s more to protect yourself.
The thing is no matter if you log or not, in case someone gets problems or abuse it, if it was well coded via zero-knowledge then it would be hard to get some useful information of these logs, since no one would be able to see behind all of these.
It seems more easy, reliable and secure to just use openvpn with PIA.
Oh and by the way regarding the logging claim from the other guy:
https://torrentfreak.com/vpn-providers-no-logging-claims-tested-in-fbi-case-160312/
There’s an example of not logging when FBI asks that’s less than three months old..
pia keep logs and working with the fedz. Dont forgot, pia is a US-based vpn service
If you use a vpn service to commit crime then they will record what the user in question is doing,which is fair and i would expect no less.I doubt they work with the feds unless required by law.They are a company and like any company in the world if their government requires a particular criminals web activities that uses their product they have to do it. I don’t believe they monitor or log your web activities in normal use but if a child abuser or hacker is up to no good they will log ,as any right thinking person would expect. I don’t believe they would log for things like torrents if they say that that protocol is welcome or for the feds if they have no court order.But i may be wrong. Personally i don’t use PIA.
Please verify the claim, thanks!
I have experienced Fed shadowing of every inbound and outbound comm connecting with PIA servers. When I confronted customer service they sent back the following as a response “.” Speaks volumes IMHO.
https://www.reddit.com/r/privacy/comments/2drwdr/proof_that_private_internet_access_keeps_logs_to/
Thanks, but I would not say that this counts as proof that PIA logs.
What is the name of a progam from screenshot used in this article?
It is Windows Firewall Control: https://www.ghacks.net/2009/11/09/windows-7-firewall-control/
WFC is pretty great. Initially got it because I loved Zonealarm’s pop-ups for connection allowing. One of those must-have programs for me now.