KeeFarce extracts KeePass information straight from memory
Password managers are the way to go when it comes to keeping accounts and information secure on virtually any system. They allow you to create secure passwords for any service, and many even improve the login process by auto-filling information or logging you in automatically.
As long as the underlying system or device is not compromised, they do offer a high level of protection.
A newly released hacking tool highlights that the protection that password managers offer becomes void when a system is compromised. While that is not a new finding, the new tool may raise awareness for the issue.
KeeFarce is a free program for Windows that enables you to extract KeePass 2.x information from memory. This includes the username, password and urls in cleartext among other things. The information is saved to a csv file in the Windows appdata folder automatically when it is run.
The program uses DLL injection "to execute code within the context of a running KeePass process". Additional information about the process are provided on the project's GitHub page.
KeeFarce needs to be run on a computer system the attacker has access to. This can be a compromised system for example, and highlights why the issue is not limited to the password manager KeePass.
Considering that local access is required for the attack, virtually any password manager running on the system is vulnerable to similar attack forms.
The owner or user of the system needs to have KeePass open for the attack to be carried out successfully. It won't work if the password database is locked as KeeFarce won't be able to extract information from it in this case.
Since most password managers are kept open all the time, it highlights why it may not be a good idea after all.
So how can you protect your data against this attack form?
Since it works only on compromised systems, making sure that yours is not compromised is enough to protect your data from the attack.
Since it affects all password managers in theory running on the system, there is little that you can do about it if your system has been compromised.
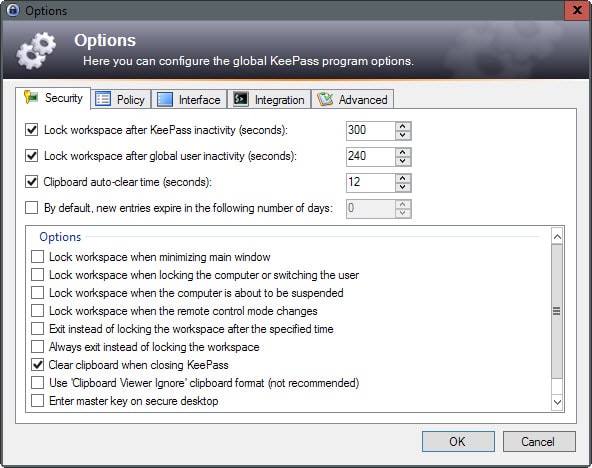
I like to lock the KeePass database automatically after a certain period in which it has not been used. While this won't prevent remote attacks from being carried out against the database if a system has been compromised, it may help prevent others from running the program locally.
You may enable the feature under Tools > Security > Lock workspace after KeePass inactivity.
Closing Words
A compromised password manager can be a catastrophic event considering that it puts a user's online presence up for grabs. An account could use the data to take over a user's online life, and it would take serious effort on part of the user to regain control over stolen account accounts again.
A compromised system without password managers is in no way better off considering that keyloggers and other malicious software can grab passwords and information from the system as well. (via Ars Technica)















Hi, I wonder if somebody can specify in what way my system has to be compromised? From what I read it looks like somebody has to locally or may be within remote session run the KeeFarce to get the passwords from KeePass and moreover the KeePass has to be unlocked!? Why would somebody needed KeeFarce when in such situation you can simply read out the passwords directly from KeePass?
Thanks for explanation…
“Or, better, start using Linux.” trusting Linux when there could be the same problem with the KeePass software
Or, better, start using Linux.
Windows machines are easy targets.
I use Keepass on Linux and life is beautiful
Yes, because Linux doesn’t store data in memory like Windows does. Really…
In his/her defense, on Linux it wouldn’t be as easy as you’d need to use a vulnerability to get to the data while in Windows it’s a feature (one that I’ve used often before).
I grow weary of seeing this response to Windows issues. Linux has a 1% market share for a reason. It’s a great OS, for sure, but it’s highly impractical for most people.
With it, you eliminate about 95% of PC games. You eliminate most Adobe products, including Photoshop (and PS Elements), Illustrator, Premiere, etc. You eliminate almost all Windows applications, save for the few that have Linux versions.
You introduce a sizable learning curve for about 95% of computer users (Linux file system is vastly different). You make it impractical to move work around from your work PC (which is about 99% likely to be a Windows PC, and probably running MS Office) and your home PC. And there are many other issues with switching.
The takeaway lesson is not: “Keepass is vulnerable!”, but “Prevent your system from being compromised”. If you have already allowed malware to run arbitrary code in Windows, then you’ve basically lost your system.
I am currently using Keepass on linux, so I am safe for now.
2-factor authentication helps. If you retain control of your e-mail account(s) for example then the repercussions could be mitigated.
Would you advise Keepass users to stop using the software? What would they use instead?
David, no I would not. The problem is not KeePass, it is that of a system that has been compromised. If your system is safe, KeePass is safe.The same is true for other locally run password managers.
Thanks. Yes, that was my gut feeling too. If your system is compromised, everything is compromised anyway regardless of Keepass