Windows: latest security update is causing huge issues for some users

If you have installed the July 2024 security updates for Windows and managed to boot into the desktop after the required restart, congratulations.
Microsoft has just confirmed a new known issue that is affecting some customers.
Here are the details:
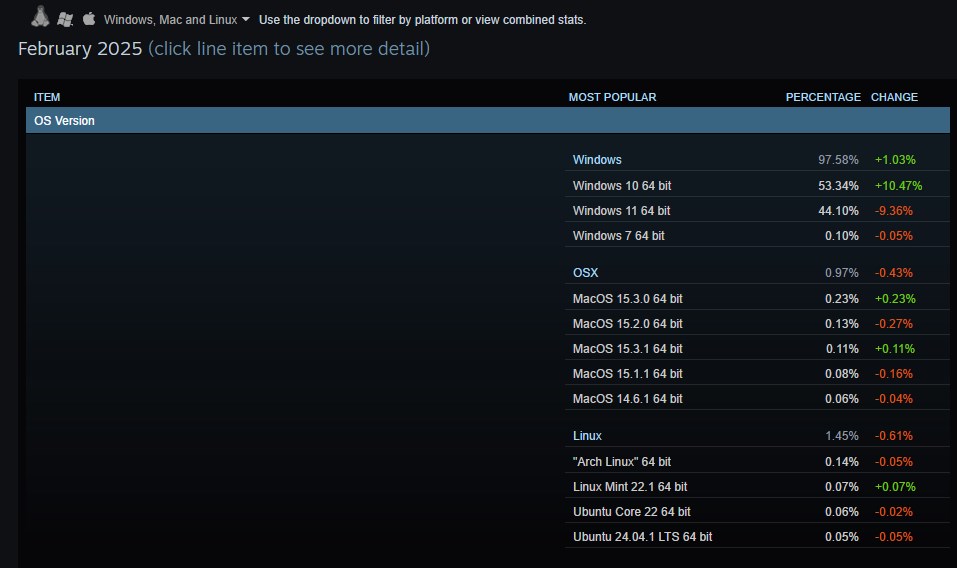
- The issue affects the security updates KB5040442 and KB5040427, which Microsoft released on July 9, 2024.
- Affected devices may boot into a BitLocker recovery screen.
- To get out, customers need to enter the device's BitLocker recovery key.
Microsoft has confirmed the issue. The company says that devices that have Device Encryption enabled are more likely to be hit by the issue. You can check whether that is the case in the following way:
- Windows 10: Open Settings > Update & security -- If you do not see Device Encryption on the page, it is not enabled.
- Windows 11: Open Settings > Privacy & security -- If you do not see Device Encryption listed on the page, it is not enabled.
It does not answer why some customers get hit by it and others do not. The workaround is simple, provided that you have access to the BitLocker recovery key.
If you do not, Microsoft advises customers to log into the BitLocker recovery screen portal to look it up.
Most home users should be able to retrieve the recovery key and type it on the recovery screen to continue.
Tip: it is a good idea to keep it save somewhere else than online. You could print it out or save it to a password manager's vault.
Microsoft revealed that it is investigating the issue and will publish an update once it has more information to share about it.
Windows users who have not installed the security updates yet on their devices may want to make sure that they have the recovery key for BitLocker at hand just in case before installing the update.
You can keep an eye on the known issues page for Windows 10 and Windows 11 if you are affected or prefer to delay the installation of the update until the issue has been fixed for good.
Do you use BitLocker encryption on your devices, or another solution, or none at all? Feel free to leave a comment down below.



















has of now windows 11 is the worst flop in the world go back to windows 10 it works great
Rather that use BitLocker, I use hardware encryption.
I set the password in the BIOS.
Every time the computer boots, I have to enter a password.
I don’t believe you can transfer the drive to another computer.
That’s a pretty bad way of doing things, unless you like that setup. Ciphershed/Veracrypt full drive encryption acts like this, but the password input stage is launched from the HDD (so HDD is theoretically transferable).
Windows: latest security update is causing huge issues for some users
no it is not it is causing huge issues with all of the pc’s around the world and ai is locking people out of ebay and amazon and the gov web pages and ss and ssi and more and now all of the makers of ai are letting people know that it is a clear danger and these companys need to be sued for spying and theft of our info
The Wiley Gates legacy… What else is new?
Thanks for the heads-up, Martin. It’s reassuring to see Microsoft acknowledging and addressing these issues promptly. For those affected, having that BitLocker recovery key handy is crucial. Here’s hoping for a swift resolution from Microsoft! Stay informed, folks!
It’s a good reminder of the importance of keeping backups and recovery options readily accessible. While updates are essential for security, occasional hiccups like these underscore the need for preparedness. Let’s hope Microsoft resolves this quickly for everyone’s peace of mind.
I have no issue with it on Win 11 Pro and Win 10 Pro.
I do not use bitlocker.
If Microsoft, a convicted monopoly,[1] really had a rootkit scanner worth using, it would detect Windows as a major threat and remove it, apologize to you for having such malware installed, wipe the drive, and install Linux for you.
[1] https://en.wikipedia.org/wiki/United_States_v._Microsoft_Corp.
I went to the BitLocker site mentioned above and was told “You don’t have any BitLocker recovery keys uploaded to your Microsoft account,” which is true because I don’t use BitLocker. So, if I’m an exception and this thing hits me, what am I supposed to do?
You don’t have to give MS a copy of your key.
I use and recommend Bitlocker. Full-disk encryption – especially of the boot dive – is not risk-free, and this is a case where I want the most stable and well-supported option possible.
If your threat model is such that you can’t trust Bitlock, then you shouldn’t be using Windows.
Bitlocker is KNOWN to be vulnerable. If you have to use Windows by any means and want cryptographic security, then use Veracrypt.
Tachy has it right. That’s why I recommend using VeraCrypt full disk encryption rather than Bitlocker. The only way to use Bitlocker on Windows is entrust a copy of your key to Microsoft, who’s in bed with three letter agencies and has proven track record of violating user privacy and selling us out to third parties. Microsoft has given anyone paying attention every reason to distrust their competence, integrity, and motivations.
“If you have installed the June 2024 security updates for Windows and managed to boot into the desktop after the required restart, congratulations.”
I think you mean July 2024.
Jason, that is exactly what I meant. Thanks for letting me know!
I don’t know much about bitlocker so let’s see if I got this right.
You encrypt all the data on your PC with a key, for security reasons.
Then you give a copy of your key to M.$?
/dogheadtilt
The key to open bitlocker can be stored in a USB stick. Don’t be dramatic, please.
Furthermore, there is an overhead. It reduces SSDS performance by half. I immediately disable this trash. I’m not a major corporation. I don’t need this junk on my personal devices.
Are you sure you don’t need encryption ?
Without it, everybody who has physical access to your computer can read all the data on the system.. Most trivial method is a USB-boot stick. If you prevent this, 2nd easiest way is to simply physically remove the drive and plant it as a non-OS-disk into a different running system.
The only thing that stands between an attacker with physical access and your data is FDE (given, it may better not be from MS).
@Anonymous,
The average joe does not need encryption, I’m sorry. If you are a primarily laptop user and do *everything* on a laptop, and that laptop ever leaves the house, then yeah, maybe. But not everybody needs encryption especially not desktop people.
Regardless of what encryption you use, it slows everything down, why would you put yourself through that?
Anecdotal remark: I worked at an IT MSP for a few years where we encrypted everything and recommended encryption to everybody. The amount of times a device with potentially sensitive data was stolen/lost and we said “thank god for encryption” was negligible, in fact, I never remember it happening, but the number of times that encryption itself caused a problem for the people that actually needed to use the computers, that was high.
We used bitlocker on anything with a TPM and Ciphershed/Veracrypt for anything that didn’t have a TPM. What a pain in the ass… We never misplaced decryption keys or anything, but one thing you never have to worry about with an unencrypted device is forgetting that “password”.
I just don’t need that stress in my life, so on my homebound PCs, I’ll never use it. if you’re really worried about sensitive things you can always schedule tidy ups such as history deletion, local cache/tmp file deletion (minimise risk), and you can always encrypt individual files or folders – these are all things i’d consider before full drive encryption!
I keep sensitive stuff on an external hard drive (EHD). If I have that plugged in for more than a minute or two I unplug the modem so that I’m not connected to the internet, thus the data on the EHD is not available to hackers. Maybe something is left behind in RAM, but that’s a cosmic-sized stretch and don’t know that I can do anything about it anyway.