First look at Spideroak's password manager Encryptr
Password managers serve many purposes: from securely storing important data such as account passwords to password generation and usability features such as automatically entering login information on websites.
But similarities end there. Some password managers run locally as programs, others are integrated into browsers and other programs, and a third-kind uses the cloud to sync the data across devices.
There is no perfect password manager that fits the bill for all users. My favorite, KeePass is an excellent program, but if you require cloud syncing you are out of luck as it does not support the feature. While I don't want my data to be stored in the cloud, other users may want that feature.
LastPass, another popular program supports that and more, but some users may not want data saved in the cloud.
Encryptr is a new password manager by Spideroak that does not reinvent the wheel. If you visit the main project page you will notice that device support is quite good for a new product. You get versions for Android, Windows, Linux and Mac OS X currently with an iOS version on its way as well. It is also open source, the client that is.
Basically, what it does, is encrypt and decrypt data locally so that it can only be accessed by authorized users. The encrypted data is stored in the cloud and synchronized between all devices the user installs the application on.
Encryptr Setup and usage
This is the setup of the Windows version. Other versions should have a similar setup procedure.
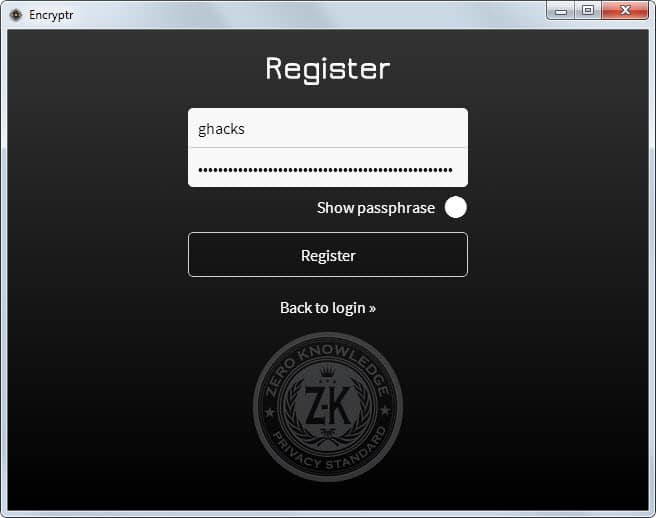
After you have installed the program on your Windows machine and started it up, you are asked to log in or create an account. The account is created locally and all you need to enter to create it is a username and passphrase.
It is synced to the server however so that it can be used on different devices. While that is comfortable, it means that anyone with knowledge of the username and passphrase can access your data. Choose a very secure password because of that reason.
Once you have created the account and signed in, you get to the account list. Here you find all entries that you have created in the past using the application.
You can create new entries easily with a click on the plus icon in the upper right corner. The program supports three different types currently: credit card, general and password.
- Credit Card: Enter a label, type, name on card, card number cvv, expiry date and notes.
- General: Enter a label, text and notes.
- Password: Enter label, username, password, site url and notes.
The label is shown on the frontpage along with the data type.
You can access any entry with a click on it, and copy any information by pressing and holding the left mouse button for a short while on a field.
And that is about it. It is simple and easy to use, but because of that, lacks features that some users require. For instance, there is no real password generator included. While a random password is displayed in the password field when you create a new entry, there is no option to change the password's strength at all.
There is also no search which makes the program unusable for users who work with dozens or even hundreds of accounts.
Verdict
Encryptr is a basic password manager that supports cloud synchronization and is open source. That's all there is to say about it right now. If you compare it to established password managers it is not fairing too well in that comparison. While it may be a bit too harsh to compare a relatively new product to established programs that have had years to grow, it makes sense to do so from a user perspective.


















I have been using SpiderOak for about a year and Encryptr for a few weeks. Both products are well designed, easy to use, and have been very reliable (so far). I prefer these products over many pf their competitors simply because of the “zero knowledge” policy. Even the SpiderOak employees reportedly cannot see my data.
If you’re too lazy to use a password manager and store your passwords on a plain text file on your computer (you know you really shouldn’t do it that way, but…) then consider Steganos LockNote. (https://www.steganos.com/us/products/for-free/locknote/overview/)
Portable program à nd your (AES 256bit encrypted) text in just one exe file. A real little gem for the lazy ones among us.
Martin spend an article on it almost 8 years ago: https://www.ghacks.net/2007/01/08/steganos-locknote-standalone-text-encrypter/.
PasswordSafe is another old gem , stored in your computer and you export the DB is required.
I just watched a 30 minute interview with edward snowdon. smart guy for sure. one of the things he said about security was to stop using dropbox. that it was just not secure at all. i always thought of the “cloud” as a warehouse in Queens that was full of servers and guarded by a 68 year old security guard..hahh. anyway, i prefer to keep my “valuables” on my computer, not someone elses. but each to his own. here is a link to that interview with snowdon.
http://techcrunch.com/2014/10/11/edward-snowden-new-yorker-festival/
once again, thanks for the article…always a first read for me.
Assuming that a classified data be protected by an encryption key of 256-bit entropy and the program to manage the system be protected by a manager’s password such as P@$$WoRd1234, the chances may well be that the system will have been taken over by the criminals who broke the password rather than those who tried to attack the 256-bit encryption key. It could be emphasized that sufficiently strong passwords are the key for the safe deployment of cryptography..
ID federations (single-sign-on services and password managers) create a single point of failure, not unlike putting all the eggs in a basket. It remembers all my passwords when un-hacked and loses all my passwords to criminals when hacked. It should be operated in a decentralized formation or should be considered mainly for low-security accounts, not for high-security business which should desirably be protected by all different strong passwords unique to each account.  Needless to say, the strength of the master-password is crucially important.
Using a strong password does help a lot even against the attack of cracking the stolen hashed passwords back to the original passwords. The problem is that few of us can firmly remember many such strong passwords.  We cannot run as fast and far as horses however strongly urged we may be. We are not built like horses.
At the root of the password problem is the cognitive phenomena called “interference of memoryâ€, by which we cannot firmly remember more than 5 text passwords on average. What worries us is not the password, but the textual password. The textual memory is only a small part of what we remember. We could think of making use of the larger part of our memory that is less subject to interference of memory. More attention could be paid to the efforts of expanding the password system to include images, particularly KNOWN images, as well as conventional texts.
Why 2 stars
this is better than Norton Identity Safe (my opinion)
and securesafe (password manager)
It lacks functionality when compared to applications such as KeePass or LastPass.
SpiderOak has been the best cloud store so far… this should end up being a well done tool.
Keepass does support syncing. You store the database in dropbox or google drive or whatever, same as 1password.
http://keepass.info/help/v2/sync.html
http://keepass.info/plugins.html#keecloud
I too have been using Keepass with dropbox. The ability to have a local copy of the DB when the cloud is not available is mission critical for me, and I don’t have to trust anyone with my passwords.
Yep. I’ve been syncing KP for awhile on a privately shared drive. It’s pretty awesome.