New Adware method: manipulating browser shortcuts to change the home page
Whenever browser makers tighten the defense systems of the browser it does not take long usually before advertising companies and malware writers find new methods to penetrate those defense.
Some browsers display information to the user when the homepage changes while others such as Chrome may even reset settings automatically when changes are noticed.
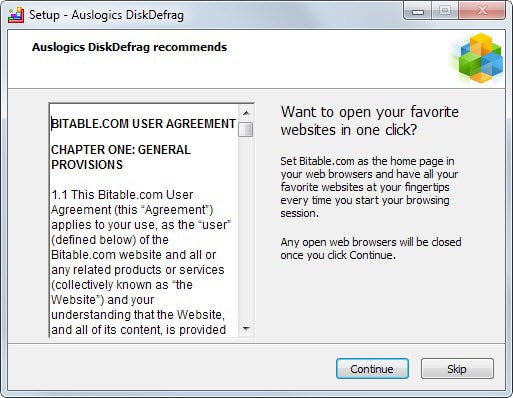
If you have installed the most recent version of Auslogics Disk Defrag, a popular disk defragmentation software for the Windows operating system, you may have noticed that it displays an offer after installation of the core program to install something that makes Bitable.com the home page in web browsers on the system.
Set Bitable.com as the home page in your web browsers and have all your favorite websites at your fingertips every time you start your browsing session.
If you open the Bitable website you will notice that it resembles contents that are opened on a browser's new tab page by default. You find a search there, thumbnail links to popular sites, date and weather information, and some other information.
If you click continue (which means give your okay so that the program makes the change) all open browsers are closed. When you restart the browser, you may notice that the home page has changed.
The change affects popular browsers such as Chrome, Internet Explorer and Firefox at the very least and maybe other browsers as well.
If you check the browser's start page settings however you will notice that it has not been modified.
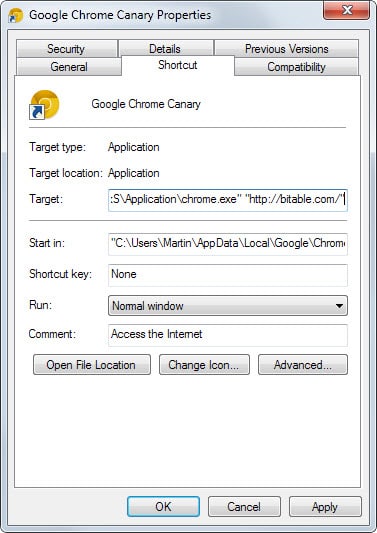
And here comes the new part and why I'm writing about it, the Bitable modification does not manipulate a browser setting, it changes only the shortcut on the system.
If you take Chrome as an example: Instead of just pointing to the chrome.exe file on the system, it adds "http://bitable.com/ at the end instructing the browser to load only this url and no other. This means no session restore and none of the usual home pages that may be loaded instead.
To find out if this is indeed the case on your computer, right-click the browser shortcut on the taskbar. Here you may find properties listed directly or after you right-click a second time on the browser name that is displayed there.
Check the target field of the properties window and if you find a url attached at the end, you are affected by this. To resolve it, remove the url at the end.
An alternative to that is to delete the shortcut with a right-click, and create a new shortcut using the start menu or a file explorer and the program directory of the browser.
Closing Words
It is likely that this method will be used by other companies as well so that this method to manipulate browser home pages will become a common issue for Internet users.
As always, it is important to read before clicks are made on buttons or links as much of this can be avoided then. If you are working in tech support or the go-to guy or girl when it comes to fixing computer problems, then this is something you may want to look in as well from now on.


















I think some adwarse are plainly annoying, like sonic train, lots of pops and make you not even look at page clearly, Chrome is the most weak, loose and vulnerable browser. Anyway anyone with any idea how i can get my hands on any raw code of any adware? a site or a link? am interested to study them further…
There is a smal tool called “unchecky” that could identify a lot of these cr@p-ware..
It’ll uncheck them, and warn you before hitting next button.
Thanks a LOT!
It should be illegal to set homepages in browsers. even subject to user approval.
Thanks :)
And the story is even getting stranger by the minute! :-)
The same company (Auslogics) that brings you all that unwanted manipulating browser shortcuts to change the home page
brings to you now the free: Auslogics Browser Care 2.0.3.0
Accoutring to ( Auslogics) there p.r. department this bring to you
This unique tool lets you take back full control of all browsers installed on your PC. Clean up, speed up and keep your web browsers well-maintained for top performance!
Remove unwanted toolbars or plugins
Change hijacked home page to the page you want
Set your preferred search engine as default
Clear cache to unclutter your drive and speed up your browser
Manage all installed browsers from one place
Version History for Auslogics Browser Care:
http://www.auslogics.com/en/software/browser-care/#details
But or this will also clean there manipulating browser shortcuts to change the home page I cant determine after reading there
(download) website
http://www.auslogics.com/en/software/browser-care/#details
Conduit and now this? Another company I won’t do business with.
If malwarebytes fails, I turn to Adwcleaner —— in fact i give it a run every week -very quick to scan, ie 30secs
Maybe they do this to sell their other product ‘Browser-Care’ lol.
Auslog is such a joke now, I used to love their Defragger, I wish and hope a good disk defragmentation program would crop up now, to bad Piriform’s defragger sucks hard and that open source one hasn’t been touched in years. Woe is me.
This shows that it is not recommended to recklessly install software.
Some has reported that the home page on their Firefox/IE Chrome installations has changed to US-based Bitable without warning.
For those who still want to use Auslogic Disk Defrag, one redditor recommend using the Ninite installer for the program in question.
Yes, if Ninite has it, that is always the best route.
My advice is to avoid all Auslogics products these days. They’ve sold out to malware installers. ESET reports their Registry cleaner tool as being malware as well, saying it includes a variant of the ‘monetizer’ malware or some such.
Auslogics used to be reputable, but they’ve crossed over to the dark side.
It’s not adware, it’s malware as it breaks your setup system.
thanks for heads up on the shortcut change.
I wonder, as it seems they lock onto browser.exe shortcuts, would it simply be worth setting just the browser shortcut properties on taskbar to do not modify … or would permissions when installing the carrier software overwrite that? It might make browser updates more of a hassle, but better secure and all that…
Now we’ll need processes that alert us to changes to shortcuts .. idk .. i see this as a OS problem, but .. maybe .. browsers can be proactive in this >> i.e if page loaded on new session is not the homepage or a session restore, then prompt? Dunno .. sometimes my browser is not open and i click an url (in an email or RSS feed) and i don’t want to be bitched at about that.
meanwhile .. I’m still waiting for all USB connections to be sandboxed >> http://www.wired.com/2014/07/usb-security/ .. and also … where are my pants?
i don’t want to sound like the bad guy here but this is not new at all to me. I’ve been seeing this for over a year with some friends’ computers, mostly some crapware like hao123 and some crap like that. they changed the home page and the shortcut as well, even the start menu shortcut and the shortcut on the taskbar (for both chrome and firefox)
what might be new is that they just change the shortcut but not the home page, (or they possible changed it but chrome reset it,…… or something).
anyway, if i learned something from installing a lot of software,
– when there’s an option for express install and custom, NEVER go to express. the custom install will allow me to not install the toolbar, change homepage and search engine and stuff.
– when there’s an option to either accept or skip, always go to skip. don’t just accept without checking the other options. they might be in a small font, a link label and not even a button. but don’t just fall for the trap and click accept, next and…….
Good advice but there is no rule or law to say, the “Next” button only does what we think it’s suppose to do. The sneakier ones set anything and everything as a, “Yes please install your crap-ware on my computer”… including the X in the corner to close the pop-up box. Nothing works as it is suppose to and any click we do install their crap-ware on our computers. Often it is a rootkit type of installation if we tried to not install their crap-ware.
If Malwarebytes Pro (registered version) fails, I use CCleaner Pro (also registered version), but if even that fails there is only one option, “Combofix”… to be used with caution as it is a root/core capable scanner which can also destroy a system if you don’t follow the instructions before letting it run. Fully read the how-to-use Combofix link below. Make note of the /uninstall command.
http://www.bleepingcomputer.com/combofix/how-to-use-combofix
At this time ComboFix can only run on the following Windows versions:
Windows XP (32-bit only)
Windows Vista (32-bit/64-bit)
Windows 7 (32-bit/64-bit)
“- when there’s an option for express install and custom, NEVER go to express.”
+1
Agreed. I work on PC’s a lot, and I’ve seen this technique used in the past.
For years my go-to anti-virus or anti-malware software is myself. Well, I’m a human being but you got the point.
I think popular trustworthy softwares, most importantly web browsers, should make people read or watch some information regarding these kinds of things. It can be done when the user installed it and ran the browser the first time. A short and easy to understand video could be displayed or a summarized text, informing the user about the basic usage of installing softwares and malicious websites.
Because, as I said, at the end of the day, no matter what anti-X software people use, there’ll always be a new X and people will keep installing those Xs.
Recently I had similar experience when installing some free software for video compression. Shopper Pro got slipped into my system (I’m sure I didn’t accepted any additional offer). Result was that all my browsers were infected (chrome, opera, IE, FF..). It changed the home/start page and search engine to something else (*don’t remember which one).
None of the AV software could remove it (MWBytes, MSE, some specialized tools just to get rid of SP…).
I ended up reinstalling OS :)
oh…and it pulled some additional apps from net (some YT download cr*p, some kind of “security tools” bs…and so on).
Silently in the background. Until I realized that something is going on, it already pulled around 100 MB of net traffic (and I was on mobile broadband, and my FW was turned off, otherwise it would never get online)…. I wanted to kill someone :)
There should be law against those ?%#$#$”
The reason I use Uniextract. In your example with Auslogics, the bitable.com installation files are in the {tmp} folder after the extraction. The {app} folder has the real program without the possibility of accidentally installing this malware, or I would even say in this case, spyware.