What you can do against Internet Explorer's latest 0-day vulnerability (April 2014)
Microsoft released a security advisory on Saturday that informs customers about a disclosed vulnerability affecting all versions of the company's web browser Internet Explorer.
Microsoft is aware of limited attacks targeting Internet Explorer, and that a successful exploit of it allows remote code execution on the affected system.
According to the information, users need to visit a malicious website for that to happen, which usually happens when users click on links in emails, but also other websites that link to the exploit pages directly.
What's interesting in this regard is that Internet Explorer 6 to Internet Explorer 11 are affected by this, but that attacks seem to concentrate on IE9 to IE11 currently.
While that is the main target right now, the situation looks dire for Windows XP users as a patch won't be released for the operating system.
This means in effect that Internet Explorer should not be used anymore on that system.
Mitigation
It is possible to mitigate the attack, and you have several options to do so.
Different browser
Don't use Internet Explorer until it is patched. This is the most obvious choice but it may not always be possible depending on your work environment. But if you can run other browsers on your system, use them instead for the time being. Firefox is a great choice.
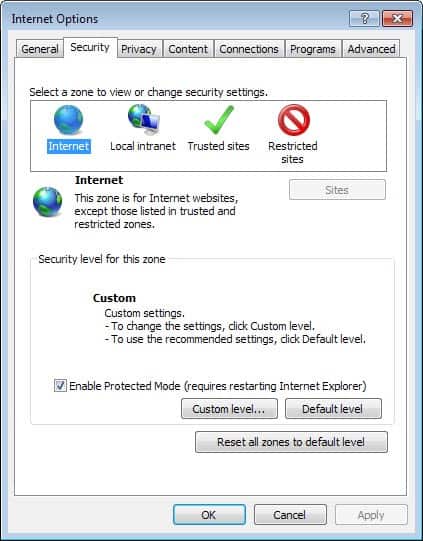
Enhanced Protected Mode
If you are using Internet Explorer 10 or 11 with Enhanced Protected Mode enabled, you are safe as it breaks the exploit. To check if it is enabled on your system do the following:
- Open Internet Explorer on your system.
- Tap on the Alt-key on your keyboard and select Tools > Internet Options.
- Switch to the Advanced tab here and make sure Enhanced Protected Mode is enabled under Security here. You find it near the bottom of the listing.
Microsoft Enhanced Mitigation Experience Toolkit
Microsoft's EMET versions 4.1 and 5.0 (currently available as a Tech Preview) break the exploit as well. Note that Emet 4.1 is compatible with Windows XP Service Pack 3 while version 5.0 is not, as it supports only Windows Vista and newer.
All you have to do is install the program on your system to protect it against the vulnerability.
Adobe Flash
According to security company Fireeye, disabling Flash in Internet Explorer will prevent the exploit from functioning as well as it appears to require Flash for its proper execution.
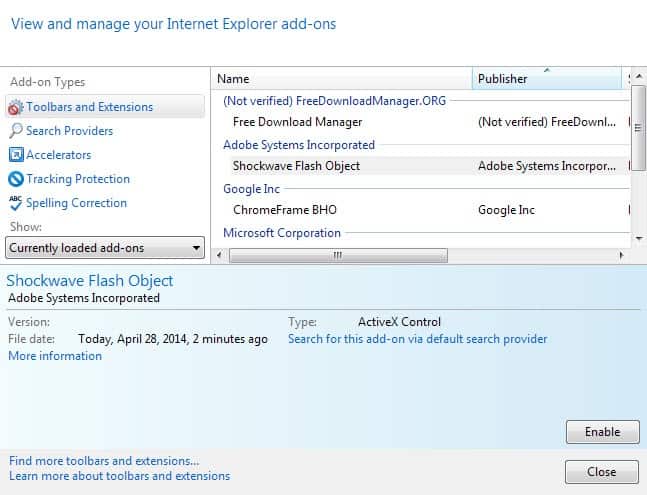
To disable Adobe Flash in Internet Explorer, do the following (this is demoed using IE11, other versions may vary)
- Open Microsoft's Internet Explorer browser.
- Tap on the Alt-key and select Tools > Manage Add-ons.
- Locate Shockwave Flash Object under Toolbars and Extensions and click on the item.
- Click on the disable button to block it from running in Internet Explorer.
Alternatively, uninstall the Internet Explorer Flash plugin using the Control Panel.

















You can disable Flash with : tools, security, select “filter activeX”
FYI: EMET 4.1 on XP requires .NET Framework version 4.0.
According to Microsoft :
…
..”attacker who successfully exploited this vulnerability could gain the same user rights as the current user” and if that user is logged on with administrative rights, the attacker could take complete control of an affected system and “install programs; view, change, or delete data; or create new accounts”….
Except for an occasional update, I haven’t used IE in years and don’t intent to use it ever again.
BTW, why does wuauclt.exe continue to run on my XP system?
I disabled “Automatic Updates”. You’ll still see wuauclt.exe in the tasklist, but it won’t actually run scans of your system files.
Though there will be no more updates for XP, the program itself will still run though it will not update anything. You can block it in your firewall to force an error to close it down. When MS ended updates for XP it didn’t dawn on them to patch, “wuauclt.exe” to desist operation, it will run but it won’t find anything. Opt for blocking it.
One word really EMET :)
http://www.wilderssecurity.com/threads/windows-8-security-deep-dive.363228/
I guess I am safe (Enhanced Protected Mode,ActiveX Filtering,new Flash version).
Solution for IE8 is to deregister the vulnerable DLL file.
http://news.softpedia.com/news/First-Post-Death-Windows-XP-Vulnerability-Already-Found-439562.shtml
A new version of Flash was just released – outside of the normal release cycle. Maybe it addresses the problems somehow.
Useful article, thanks.
Not sure about your instructions for Enhanced protected mode though.
Your screenshot and instructions just show plain old protected mode.
Enhanced protected mode is under the advanced tab and requires a computer restart.
There is also an option in there to enable 64 bit processes for EPM.
Are you sure ?
That option exists only in Windows x64.That means that IE10/IE11 in Windows x86 are vulnerable.
I am confused.
You are right, corrected it.
what to do?????
use a browser
PS: IE is not one
Very mature comment. Misconceptions like these still linger from the old days.
Actually recent versions of Internet Explorer, especially IE11 on Windows 8.1 with 64bit enhanced protected mode, smartscreen and high entropy ASLR (I bet you never heard of any of these three), are among the most secure browsers out there. On top of that Internet Explorer has the best protection against social engineering.
The worst browser in terms of security is in fact Firefox. Yet nobody knows this, because it still draws its reputation from years ago (when XP was the most recent Windows version), when browsers did not use low rights containers, sandboxed plugins and other security features. Great extensions like NoScript don’t make up for that.