Deploy honeypot documents to find out about unauthorized access

When it comes to important documents, be they of personal nature, business related or otherwise of importance to you, it is usually best to use encryption to protect them from prying eyes. Encryption protects documents from local and remote access and is usually the best way to make sure that their contents remain protected.
Sometimes though, you may want to know if someone else accessed your personal documents. It may be possible to tell if that is the case locally, for instance by looking at the last access stamp of important files, but that too is not a 100% surefire way of knowing, as those can be edited with the right set of tools.
As far as online storage is concerned, there are even less options to find out. While you get the same information if the files are hosted on a server that you have access to, you are more or less blind if they are hosted on third party servers.
This includes file synchronizations services likes Dropbox, email services like Gmail, and pretty much any other service that allows you to upload files to their servers.
It may be a good idea to test that service with so called honeypot documents to find out if the test documents have been opened and read.
Honeydocs
Honeydocs is a free service that does so. You are probably wondering how they are tracking access. It was one of the first things that I wanted to find out. The service uses the same "trick" that Internet marketers use to track users on the Internet or in emails: remote images.
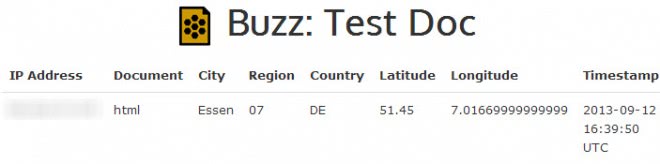
Each document that Honeydocs makes available contains a small remote image that gets loaded when the document is opened. The server records the hit, and you get information about each operation that is recorded, including the IP address used to access the contents, the user agent, city, region and country it originated from, and the timestamp.

You can create new stings right after you have signed in to the service on the overview page. Just enter a name and wait for it to be created. Note that free users can create one sting, while paying customers can create multiple.
A click on documents displays a list of specifically prepared documents that you can use for testing. It is also possible to add the tracking to your own documents, but that requires some manual work on your site. Simply add the remote image to them and you are good to go.
Now upload the document to remote hosts or place it on your computer. Whenever someone accesses it, you are informed about that.
Note: The hit will only be recorded if an Internet connection is available. If the program that opens the file, e.g. Word, is blocked from Internet access or if no Internet access is available at the time, the access won't be recorded.
It is interesting to note that Dropbox appears to open those documents when they get uploaded.
Verdict
Honeydocs' method of tracking document access is not perfect, as it requires Internet access to record the hit, but it is better than no solution at all. It is ideal to test online services that store documents for you, to find out if they read the contents of the documents, or if they do not. While you do not get a 100% guarantee that they do not, it may be reassuring nevertheless.
Advertisement

















