Use Fingerprints to determine the authenticity of an Internet website
It may sometimes be useful for security purposes to make sure that you are connected to the right website, and not a spoofed copy of it. While this may be less of an issue at home, you may run into all sorts of troubles when you are using public Internet connections.
It is rather difficult on first sight to make sure that you are really connected to the right secure website and not a copy that traffic gets redirected to. This can for instance be done by spoofing a site's certificate
One of the options that you have in regards to https connections is to use fingerprints for verification, as fingerprints cannot be spoofed. So to make sure you are on the right site, you compare the fingerprint of its certificate in your browser against a trusted source that provides you with fingerprint records of its own.
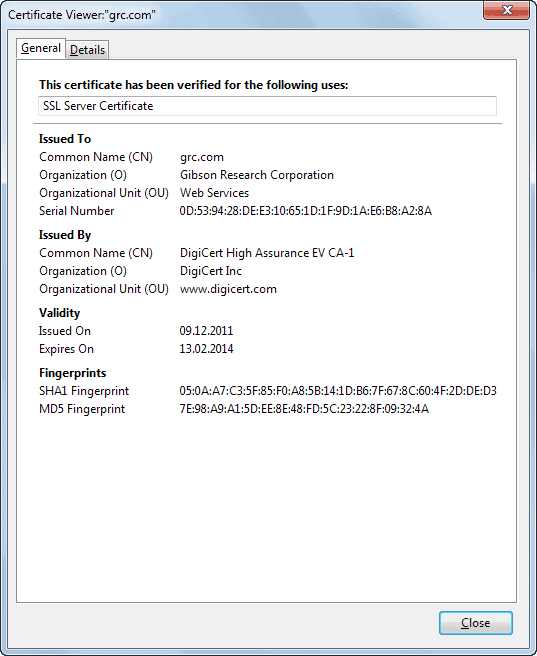
Looking up fingerprint certificates
Each web browser handles this in a different way:
Firefox
- Click on the lock icon in the browser's address bar and select more information from the menu.
- Select View Certificate on the new window that opens up.
- Locate the fingerprint section on that page.
Google Chrome
- Click on the lock icon in the browser's address bar.
- Switch to connection and on that page on certificate information.
- Switch to details on the new window and locate Thumbprint at the bottom of the listing.
Opera 15+
- Click on the secure lock icon in the address bar and select details from the menu that opens up.
- Click on the certificate link that is displayed.
- Switch to the details tab and check the Thumbprint field value here.
Internet Explorer
- Right-click on the page and select Properties from the context menu.
- Select Certificates on the properties page.
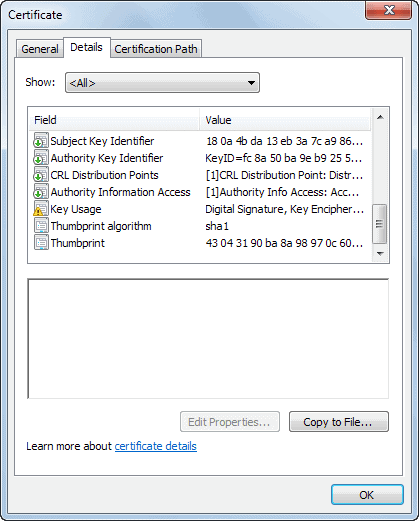
- Switch to the details tab, make sure that show is set to all, and scroll down until you find the thumbprint field.
Verifying the fingerprint of a website
Now that you know how to look up the fingerprint of a website's or server's certificate, it is time to compare the fingerprint using a second source.
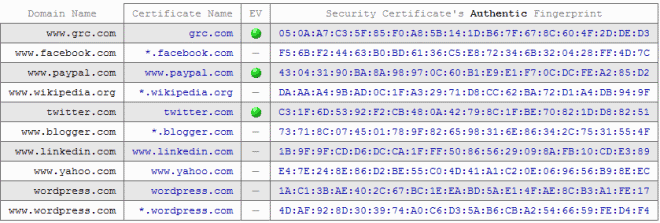
The GRC website can be used for that purpose. Just visit the fingerprint page on it and either look at one of the popular fingerprints at the top, or enter the website you want to retrieve the certificate fingerprint for below in the form.
All you have to do is compare the fingerprint displayed in the web browser to the certificate pulled by the script on the GRC website.
As a side note: Make sure the GRC website shows a green listing and lock icon in Firefox, Chrome or Opera, as this is an indicator of an authentic Extended Validation Certificate.
Once you have have compared the fingerprint that is displayed in your web browser of choice to the fingerprint that the GRC website provides you with, you know that the connection is either valid or spoofed.
Exception: Companies may use multiple certificates which all come with their unique fingerprint. Depending on which server you are connected to, it may mean that the certificate differs even if you are connected to the real website or server.
Closing Words
The technique is ideal to make sure you are connected to the right secure website. While it may not provide you with a definitive answer that a certificate is spoofed if fingerprints do not match, it still may make you more cautious because of it.
Advertisement















Use Fingerprints to determine the authenticity of an Internet website. http://www.thetechart.com/how-to-download-torrentz-file-using-idm/
Firefox addon is available to check these for you automatically.
Chrome version isn’t automatic because of API limitations,
Both available via http://www.signaturecheck.org
I agree with this invention, its really nice for everyone!
For anyone who’s interested, if using IE once you’ve identified a legitimate certificate, you can use the ‘Certificate Pinning’ feature in EMET 4.0 which will warn you if the certificate changes or expires.
@Transcontinental: I think that the reason that no add-on was created to check the fingerprints is the second part of your comment :) (it would create confusion/frustration among many users).
True, Nebulous, I agree. The fact is I thought about this but a bit too late.
Most interesting. I wonder why no add-on (as far as Firefox is concerned) has been created to automate this task (as fa as I know).
A major handicap is the exception possibility mentioned in the article. Consequently, if fingerprints checksums match, it’s ok; if they don’t it might still be ok. I admit this may lead to fruistration in the latter case.
I am sorry. Unless you are one of the few over paranoid Wed users, you are not going to go through all those hoops to verify a website. The whole purpose of the Web (now) is convenience. Those who use the Web are bombarded with more and more convenient ways to simply do what was more difficult before.
The fingerprint idea is great for the paranoid. But, for it to be of any use for the masses, it needs to be incorporated into the browsers so it is check automatically in the background and then WARN users that the site they are visiting is corrupted some way.
I have a number of add-ons I use to help steer me away from trouble, but common sense is my best weapon.
Tom I do agree that this is taking it a bit far, but the idea here is to highlight that you can verify it. So, if you suspect that someone is tapping your line or attacking you, then you may want to check your connections.
Also, it does not make sense to verify them all. While I would for instance verify my connection to PayPal, I may not do so if I want to search on Google.
Speaking of paranoia you can also verify how secure is encrypted connection to your PayPal or your Bank server..
https://www.ssllabs.com/ssltest/index.html