Browser history spam from view.atdmt.com and other networks
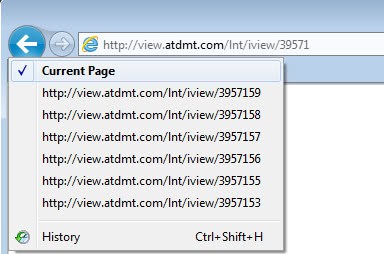
Browser history spam refers to scripts messing up the current tabs history by polluting it with script related entries so that the web pages that have been visited before are moved down the queue or even completely removed from the history when the limit is reached. It is not really clear if that is done on purpose, or if those scripts have a programming flaw that is causing the behavior. As far as I know, this is only happening in Microsoft's Internet Explorer and not in other web browsers at all.
A few advertising services are mentioned regularly when it comes to this kind of spam: http://view.atdmt.com/ belonging to Atlas Solutions which is part of Microsoft, Â http://apr.lijit.com which is part of Federated Media, and http://googleads.g.doubleclick.net which is Google's advertising network. All three are legit networks, which suggests that individual apps are causing the issue.

It should be a temporary issue, as these kind of ads should get reported quickly to the advertising networks and then removed as a consequence from the network's inventory.
So how can you overcome the issue in the meantime? There are several options:
- Switch to a different web browser, e.g. Firefox, Google Chrome or Opera
- Use an ad blocker like Adblock IE
- Block the ad networks using the hosts file
- Try reloading the page with F5. Users have reported that this removes the ad entries from the history
- Add the networks to the list of restricted sites in Internet Explorer. This is done with a click on the settings button and the selection of Internet Options from the menu (in IE9, may be different in previous versions of Internet Explorer). Switch to the security tab, click on restricted sites, then the sites button, and add the networks that are causing the issue to the list there.
I'd probably start with the reloading option and keep using it unless you run into history spam fairly frequently.
Advertisement











Ha, I already had those blocked with the hosts file and through my router.
Thanks for the heads-up though.